The NIST Cyber Security Framework

The National Institute of Standards and Technology (NIST) Cybersecurity Framework provides a proven, adaptable approach for managing and reducing cybersecurity risk. Built around five core functions, the framework helps organizations of all sizes strengthen security posture, align with regulatory standards and communicate risk clearly across technical and business teams.
In this guide, you’ll learn what the NIST Cybersecurity Framework (CSF) is, why it matters and how Cymulate helps organizations apply and validate it effectively.
Key highlights:
- The NIST Cybersecurity Framework (CSF) provides a structured, adaptable model for managing and reducing cybersecurity risk across any organization.
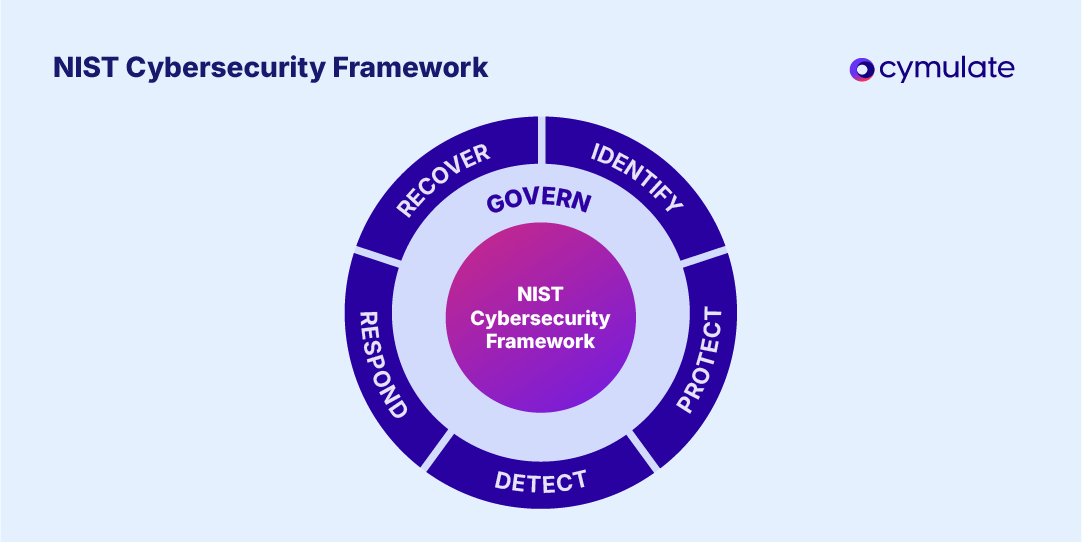
- The framework’s five core functions — Identify, Protect, Detect, Respond, Recover and Govern — serve as the foundation for building and maintaining a resilient cybersecurity posture.
- Implementing the framework enables measurable maturity, improved governance and stronger alignment between technical and executive teams.
- Cymulate strengthens NIST CSF adoption through continuous validation, automated assessments and actionable insights that keep defenses effective over time.
What is the NIST Cybersecurity Framework (CSF)?
The NIST Cybersecurity Framework is a set of guidelines designed to help organizations strengthen their cybersecurity posture through clear, outcome-based practices. It provides a common language for identifying, protecting against, detecting, responding to and recovering from cyber threats.
At its core, the NIST security framework focuses on what organizations should do, rather than prescribing how to do it, making it flexible and accessible for teams across industries, regardless of size or regulatory environment. As a whole, it provides a comprehensive view of how organizations can manage risk, covering everything from prevention to incident response and recovery.
How the NIST CSF framework helps enterprises
The NIST security framework provides organizations with a practical way to embed cybersecurity into daily operations. It avoids dense regulatory language and focuses on what matters — creating a shared understanding of security across teams. Instead of enforcing strict rules, it lays out clear outcomes that Sec teams can adapt to different industries, risk levels and business goals.
Key reasons why the NIST CSF is so widely implemented:
- Accessible language: The framework is written in plain English, making it easy for both technical and non-technical stakeholders to understand.
- Adaptable structure: It can be customized to align with any organization’s risk profile, regulatory requirements or maturity level.
- Outcome-driven approach: Rather than focusing on specific tools or methods, the NIST framework for cybersecurity emphasizes results and measurable improvements.
- Improved communication: Creates a shared language between operations, compliance and executive leadership.
- Continuous improvement: Encourages an iterative approach to assessing, improving and validating cybersecurity posture over time.
- Cross-framework alignment: Works seamlessly with existing standards such as ISO 27001, PCI DSS and NIST 800-53.
These qualities make the CSF not just a framework for compliance but a foundation for continuous improvement and measurable resilience.
Core functions of the NIST Cybersecurity Framework
The NIST CSF framework is organized around six key functions: Identify, Protect, Detect, Respond, Recover and Govern — added in NIST CSF 2.0. Each function is further divided into categories (such as access control, incident response or data protection) and subcategories that describe specific outcomes or activities organizations should achieve.
In its security framework, NIST details 23 categories and 108 subcategories in total, representing the “what” of a cybersecurity program, while leaving the “how” flexible for organizations to adapt to their size, industry and risk profile.
These five core functions work together to provide a continuous cycle of improvement, helping organizations understand their risk exposure, strengthen defenses and validate resilience across their entire environment.
1. Identify
The Identify function focuses on understanding what needs protection by mapping critical assets, systems, data and capabilities. It lays the foundation for effective risk management, helping organizations define what’s essential, identify vulnerabilities and determine who is accountable for protecting them.
Outcomes:
- Clear visibility into digital assets, dependencies and data flows
- Defined governance and accountability for cybersecurity oversight
- Informed risk prioritization across business functions
How Cymulate helps:
The Cymulate Exposure Management Platform identifies and assesses weaknesses across on-prem, cloud and hybrid environments — helping organizations understand where the most significant risks lie before bad actors can exploit them.
2. Protect
The Protect function ensures that safeguards are in place to maintain the security of critical assets and limit the impact of potential incidents. It includes controls related to access management, network segmentation, data security and user awareness.
Outcomes:
- Strong access control and least-privilege enforcement
- Verified network segmentation and endpoint protection
- Enhanced policy adherence and employee security hygiene
How Cymulate helps:
Cymulate validates key preventive controls — testing identity and access mechanisms, segmentation, endpoint and email security configurations — to confirm that your protection measures are effective and aligned with business needs.
3. Detect
The Detect function focuses on identifying cybersecurity events as quickly as possible to minimize damage. It addresses monitoring, anomaly detection and alerting to ensure timely awareness of malicious or suspicious activity.
Outcomes:
- Continuous monitoring for anomalous behavior or indicators of compromise
- Defined processes for detection, escalation and triage
- Reduced dwell time through faster threat recognition
How Cymulate helps:
Cymulate Breach and Attack Simulation (BAS) capabilities continuously test detection capabilities by emulating real-world attack chains, measuring how effectively your monitoring and SIEM tools respond and highlighting visibility gaps that need improvement.
4. Respond
The Respond function enables organizations to contain and mitigate the impact of cybersecurity incidents once detected. It focuses on structured planning, communication and coordinated action between teams.
Outcomes:
- Documented and tested incident response playbooks
- Clear communication protocols during active incidents
- Continuous process improvement through lessons learned
How Cymulate helps:
Through attack-scenario testing and response drills, Cymulate helps evaluate your cybersecurity posture by simulating realistic threats, enabling teams to measure and refine their response effectiveness in controlled conditions.
5. Recover
The Recover function ensures that teams restore affected systems, data and services swiftly and securely following an incident. It emphasizes resilience, business continuity and learning from prior disruptions.
Outcomes:
- Validated backup and recovery processes
- Improved operational resilience through tested recovery strategies
- Transparent stakeholder communication during restoration
How Cymulate helps:
Cymulate Security Control Validation confirms that recovery mechanisms — such as backups, redundancy and failover procedures — operate as intended, enabling your organization to restore normal operations quickly with minimal disruption.
6. Govern
The Govern function, introduced in version 2.0, establishes how cybersecurity is managed and overseen across the organization. It ensures that leadership defines clear policies, roles and accountability structures — embedding cybersecurity into the overall governance and risk management framework rather than treating it as a standalone IT issue.
Outcomes:
- Defined cybersecurity roles, responsibilities and decision-making authority
- Integration of cybersecurity into enterprise risk management
- Policies and oversight that align with business priorities and compliance requirements
How Cymulate helps:
Cymulate provides continuous validation and measurement to support governance oversight. By translating technical results into executive-level insights and trend data, it helps leadership monitor posture, measure control effectiveness and align investments with strategic risk priorities.
Benefits of NIST CSF for enterprises
Implementing the NIST framework for cybersecurity enables organizations to turn complex programs into a transparent, repeatable process for managing risk. The framework’s structure promotes visibility, accountability and continuous improvement across every layer of the business.
Key benefits of NIST CSF implementation include:
| Benefits of NIST CSF | How the NIST benefits impact security teams |
| Unified risk visibility | Builds a complete picture of assets, vulnerabilities and threats, allowing teams to identify where risk truly resides. |
| Stronger governance and accountability | Defines clear ownership of cybersecurity responsibilities and ensures alignment between technical and executive stakeholders. |
| Continuous improvement and maturity tracking | Establishes a cycle of measurement and progress using NIST’s Implementation Tiers to benchmark organizational growth. |
| Streamlined compliance and framework alignment | Simplifies alignment with other standards, reducing redundancy and audit complexity. |
| Clear communication and collaboration | Provides a common language for cybersecurity, enabling consistent reporting and collaboration across teams and leadership levels. |
How to implement the NIST CSF
Implementing the NIST Cybersecurity Framework helps organizations move from reactive defense toward structured, measurable risk management. Each phase below represents a standalone pillar of a mature cybersecurity program.
Here is how to implement NIST CSF in five steps:
1. Assess your current state
Every cybersecurity strategy begins with visibility. Organizations must understand which assets, systems and processes are critical to operations and how well they’re currently protected. A comprehensive assessment provides the baseline needed to manage risk strategically rather than reactively.
Here’s how to assess your current posture:
- Map existing controls and policies to the CSF’s five functions and 23 categories
- Review audits, incidents and vulnerability reports to uncover recurring weaknesses
- Involve both business and IT stakeholders to capture the full operational context
- Document your current profile to establish a clear, evidence-based starting point
2. Define your target profile
Defining a target profile sets direction for your cybersecurity program. It outlines the outcomes your organization aims to achieve based on business goals, risk appetite and compliance requirements. The target profile serves as a vision statement for your future state of cybersecurity maturity.
Here’s how to define your target profile:
- Translate organizational objectives into measurable security outcomes.
- Determine which CSF subcategories best align with your industry and regulatory landscape.
- Establish performance indicators, such as detection time or incident containment speed.
- Identify the desired NIST Implementation Tier that represents your maturity goal.
3. Prioritize and plan improvements
Effective cybersecurity improvement depends on focus. After establishing clear goals, organizations must decide which initiatives offer the most significant risk reduction and the best return on effort (and investment). Prioritization ensures that security investments directly support mission-critical outcomes.
Here’s how to plan your improvements:
- Rank identified gaps by risk severity, exploitability and potential business impact.
- Sequence initiatives in a logical roadmap, balancing short-term wins with long-term goals.
- Define resource requirements, budgets and ownership for each improvement effort.
- Communicate the plan across stakeholders to ensure alignment and accountability.
4. Implement and integrate controls
Implementation turns strategy into operational reality. Deploying and integrating controls solidifies cybersecurity into everyday business processes. Success depends on ensuring that safeguards, policies and training coexist seamlessly with existing systems and workflows.
Here’s how to implement effectively:
- Deploy prioritized technical and procedural controls according to the roadmap.
- Update documentation, policies and awareness programs to reflect new measures.
- Integrate monitoring, alerting and response capabilities into enterprise operations.
- Measure adoption and performance to confirm that security objectives meet defined standards.
5. Validate and continuously improve
Validation closes the loop between strategy and effectiveness. Regular evaluation ensures that security controls perform as intended, that risks remain within tolerance and that the organization adapts to new threats. Continuous improvement is the hallmark of a resilient cybersecurity program.
Here’s how to validate your posture:
- Conduct recurring control assessments and attack simulations to test defenses.
- Measure results against established performance indicators and NIST maturity tiers.
Analyze lessons learned from incidents and audits to refine processes. - Refresh the framework annually to align with evolving technologies and business changes.
For a complete list of categories and subcategories, refer to the official NIST CSF 2.0 documentation.
Best practices for meeting NIST cybersecurity standards
Maintaining alignment with NIST computer security standards is an ongoing process that requires consistency, measurement and adaptability. Organizations that approach the framework as a living program, rather than a one-time exercise, are better equipped to manage emerging risks and demonstrate continuous improvement.
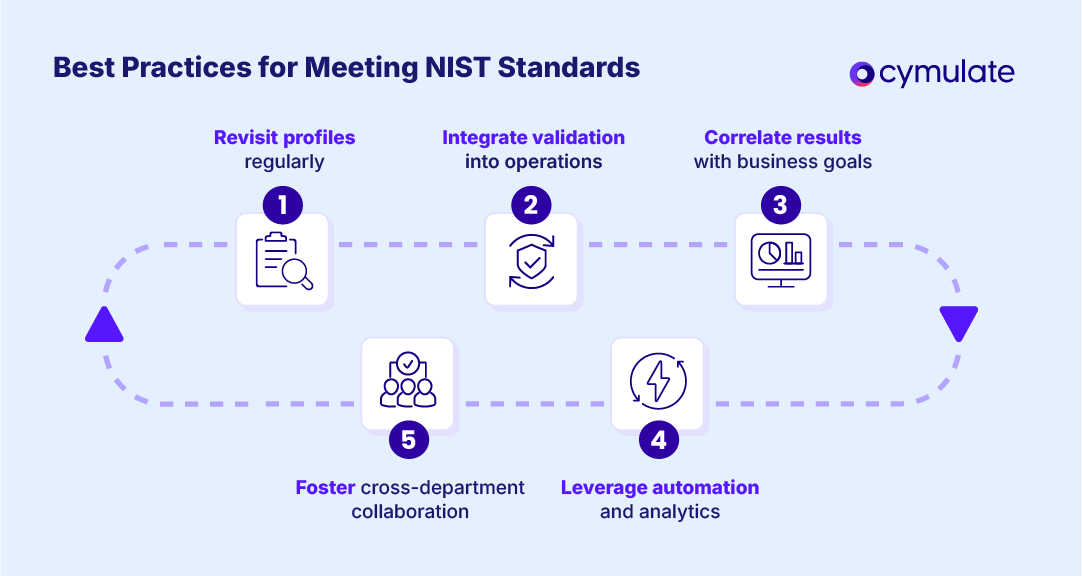
Follow these five best practices for maintaining NIST cybersecurity standards:
- Revisit profiles regularly to ensure current and target states reflect evolving business goals and threat landscapes.
- Integrate validation into routine operations by testing controls and response capabilities on a recurring schedule.
- Correlate results with business objectives to show how cybersecurity improvements support organizational outcomes.
- Leverage automation and analytics to reduce manual workload and gain data-driven insights into control effectiveness.
- Foster cross-department collaboration to align technical, compliance and executive teams on risk priorities.
Following these best practices helps organizations sustain CSF alignment as their environments, technologies and regulatory requirements evolve.
Cymulate enhances NIST CSF implementation
Cymulate strengthens the implementation of the NIST Cybersecurity Framework by transforming strategy into measurable action. Our continuous security validation platform empowers you to test and verify controls across all five CSF functions, while automating assessment, reporting and improvement over time.
Here’s how Cymulate helps organizations bring the NIST CSF to life:
- Comprehensive mapping and validation across roughly 60 of the framework’s 108 subcategories to assess control effectiveness and track maturity.
- Continuous automated risk assessment through real-world simulations that quantify readiness and prioritize remediation.
- Audit-ready reporting and executive visibility with dashboards and documentation mapped directly to CSF controls and implementation tiers.
- Unified exposure management that centralizes risk insights across on-premises, cloud and hybrid environments.
- Operational efficiency and scalability through automation that reduces manual testing workload and accelerates improvement cycles.
Book a demo today to see how Cymulate transforms NIST CSF implementation into a measurable, automated and continuously improving process.