Proactive Security in Action: What Real-World Gaps Reveal About Cyber Resilience

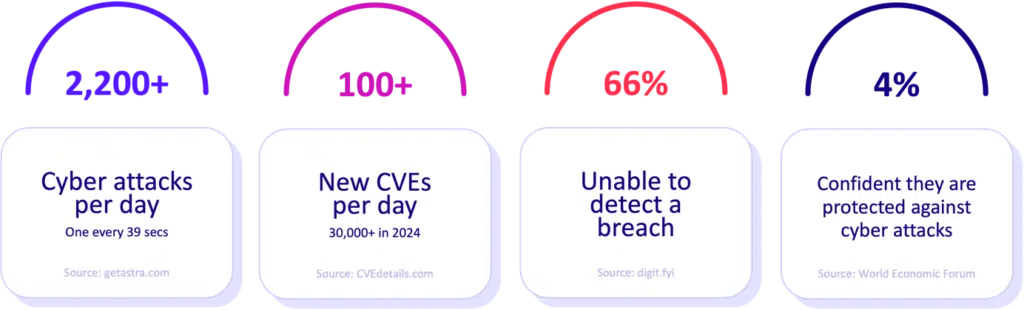
Today’s threat actors move fast, and reactive security is no longer enough. Most breaches have a common root cause: a security control that didn’t perform as expected. Even the most well-funded programs remain vulnerable when defenses go untested. According to the IBM Cost of a Data Breach Report 2024, only 42% of data breaches were detected by an organization's security teams or tools.
Organizations that adopt a proactive security mindset will consistently validate their defenses, identify exposures before attackers do and build the resilience needed to stay ahead of evolving threats. One of the most effective ways to operationalize this mindset is through exposure validation.
Security teams are often overwhelmed by the large number of potential exposures found in their organizations. Exposure validation ensures your controls are working as intended against real-world threats and helps focus remediation on what’s actually exploitable, not just theoretically risky.
What Is Proactive Security?
Proactive security is the practice of identifying and mitigating cyber exposures before they can be exploited. It stands in contrast to reactive approaches, which focus on responding to breaches and managing damage after an incident has occurred.
To support this proactive approach, organizations leverage a variety of tools, including:
- Breach and attack simulation (BAS) - Simulates real-world cyberattacks in a controlled manner to test whether your existing defenses (like firewalls, EDR, email security, etc.) detect, block, or allow them through.
- Continuous automated red teaming (CART) - Automates red team tactics at scale, delivering continuous, realistic attack simulations to assess an organization’s security posture.
These techniques also support exposure validation by giving security teams a clear, prioritized view of risk, equipping them to act where it matters most.
The Cost of Assumption: What Organizations Miss
According to Gartner, cybersecurity leaders report using an average of 43 tools in their security stack, with 5% managing over 100 (Gartner, Reduce Threat Exposure With Security Controls Optimization, 3 April 2025, Evegny Mirolyubov, Eric Ahlm). Too many organizations fall into the trap of believing that simply having security controls in place means they’re secure. But cyber defense isn’t about how many tools you own, it’s about whether the tools will actually protect you when it matters most.
At Cymulate, we’re proud that our customers demonstrate what’s possible with a proactive cybersecurity strategy; one that validates controls continuously, rather than relying on assumptions. Here are just a few real-world discoveries made by these proactive security teams:
- Servers believed to be isolated were actually exposed to the internet.
- Hardcoded passwords were found scattered across multiple environments.
- Email gateways failed to block malicious scripts embedded in attachments.
Each of these issues was discovered and remediated before it could be exploited, which is a testament to the power of exposure validation.
Proactive Security Starts with Mindset
You can’t automate your way to cyber resilience with tools alone. The most secure organizations succeed because they operate with a proactive mindset. These teams don’t wait for alerts to signal that something went wrong; they continuously validate and remediate before attackers get the chance to exploit a weakness.
A proactive mindset treats continuous validation as a discipline, not a checkbox. It’s about embedding cyber resilience into the fabric of your operations, not just into your incident response plan.
Want Proof? These 10 Companies Found Exposures Before Attackers Did
Real Cymulate customers are using proactive security strategies to uncover risks that could have otherwise led to major breaches. Instead of waiting for the worst-case scenario, they validate their assumptions early to avoid disaster.
From unpatched systems to credential exposures, these organizations represent a new breed of defenders: those who treat security not as a reaction, but as a practice in foresight and resilience.
Download the eBook “10 Cybersecurity Exposures You Can’t Afford to Ignore” to see what proactive security looks like in action.



