Making SIEM Alerts Smarter: Best Practices for Real-World Detection
SIEM alerts are mission-critical, but also a minefield. For every high-value alert that catches a real threat in progress, security teams must sift through hundreds of false positives, noise and duplicated signals.
Alert fatigue is real. So is the risk of missing actual intrusions.
Security Information and Event Management (SIEM) platforms are only as useful as their signal-to-noise ratio. Without careful engineering, validation and tuning, even the most advanced SIEM solution becomes a liability. That’s where smarter detection practices enter the picture.
What Is a SIEM Alert?
A SIEM alert is a security signal automatically generated by correlation rules within a SIEM system. These alerts are triggered when specific patterns or events occur across log data collected from endpoints, firewalls, cloud environments, identity providers and other sources.
SIEM alerts are more than simple notifications. They’re data-driven decisions, indicating that something matches predefined threat logic or suspicious behavior.
How SIEM Alerts Are Generated:
- Log sources feed the SIEM with telemetry.
- Correlation rules analyze those logs for patterns.
- If a rule’s conditions are met, an alert fires, ideally one that’s actionable.
Done right, each alert is a high-fidelity signal. Done wrong, these alerts just become more background noise.
Types of SIEM Alerts with Real-World Examples
While SIEM rules can be tailored to any environment, most alerts fall into several core categories:
Authentication Anomalies
These are some of the top SIEM alerts and often the first sign of lateral movement or credential abuse.
- Example: Multiple failed login attempts followed by a successful one from a new geography.
Malware or IOC Triggers
Triggered when SIEM detects indicators of compromise from threat intel feeds or endpoint detection tools.
- Example: Beaconing to a known C2 domain or hash matches from threat feeds.
Suspicious Privilege Use
These alerts highlight potential abuse of high-value accounts or unauthorized access escalation.
- Example: A standard user suddenly running PowerShell scripts or creating new admin accounts.
Policy Violations
Noncompliant behavior, whether intentional or accidental.
- Example: Use of unauthorized USB devices, data exfiltration attempts or disabled antivirus.
For detection engineers, understanding these categories enables smarter correlation logic and SIEM alert best practices around tuning and triage.
Why SIEM Alert Fatigue Happens
SIEM alert fatigue isn’t just a buzzword. It’s one of the most persistent operational issues in modern SOCs. Here’s why:
- Overly Broad Correlation Rules: Rules that are too generic catch benign activity, drowning analysts in alerts with no investigative value.
- Redundant Alerts from Multiple Tools: With XDR, EDR, cloud and on-prem feeds, the same event may trigger alerts across several platforms unless deduplicated or normalized.
- Lack of Contextual Enrichment: Alerts that lack context (like asset value, user role, or risk score) force analysts to hunt for clarity, slowing triage.
- No Proactive Validation or Feedback Loops: Without testing whether alerts work in real-world scenarios, organizations can’t know if detection logic holds up.
These challenges directly impact SOC efficiency, analyst burnout and missed threats. But they also represent an opportunity: alert quality can be improved.
Best Practices for Effective SIEM Alerts
To make alerts smarter and more actionable, security teams should adopt a proactive, data-driven approach. Below is a series of best practices for your organization to consider.

Continuously Tune Correlation Rules
SIEM alerts hinge on accurate correlation logic. However, rule effectiveness degrades over time as environments change:
- Automate validation & tuning
Tools like Cymulate automatically extract and simulate real-world attack scenarios to test existing SIEM rules. This identifies whether rules fire as expected, reveals gaps in data collection, and delivers actionable, SIEM-native remediation steps. - Filter redundancies
Large SIEM deployments may contain redundant or overlapping rules resulting in false alerts and wasted effort. Emerging LLM‑based tools like RuleGenie help identify and remove such rules using semantic clustering. - Use detection-as-code
Store rules and tuning workflows in Git with version control and CI/CD pipelines. Maintain a regular review cycle to archive outdated rules and prevent alert fatigue.
Use Severity Levels & Align with Business Context
Not all alerts are created equal. Aligning alerts with business impact is key:
- Assign dynamic severity with context
Attach asset value, user roles, or system criticality to alerts. Machine learning and threat intelligence feeds enable contextualized alert enrichment and prioritization. - Embed business context in filtering
A “90% actionable threshold” filter can be applied at ingestion, discarding low-value events from environments or identities outside business relevance. - Integrate threat intelligence mapping
Each detection should be mapped to MITRE ATT&CK tactics and known IOCs. The Cymulate validation engine auto-aligns SIEM rule mapping to TTPs, helping to surface where rules capture or miss behavior.
Align Alerts with MITRE ATT&CK Framework
- Map and visualize coverage
A visual MITRE ATT&CK heatmap found in Cymulate shows which tactics/techniques are detected, partially covered or invisible. This highlights coverage gaps and risk areas. - Leverage AI mapping tools
LLM-driven frameworks like Rule-ATT&CK Mapper automate mapping SIEM rules to MITRE techniques, which speeds classification and reduces manual errors. - Prioritize based on adversary activity
Detection engineering should target high-risk techniques aligned with industry-specific threats. Coverage decisions should be informed by threat intel and MITRE-informed strategy.
Automate Triage & Alert Suppression
- LLM-powered triage
Generative AI can filter, summarize and contextualize alerts, flagging only high-impact incidents. Tools such as Cortex XSIAM or custom AI modules automate triage—distinguishing noise from meaningful incidents. - Feedback loops for suppression
Use SOAR playbooks to auto-suppress false positives. For example, during breach simulation runs, create transient suppression rules for expected alerts and apply consistent tuning to production rules. - Adaptive aggregation
AI correlation groups related alerts into higher‑level incidents based on behavioral patterns, reducing noise and improving focus.
Regular Testing & Detection Rule Validation
- Scheduled simulation assessments
Weekly attack simulations against real-world TTPs ensure detection logic evolves alongside threats. Cymulate orchestrates automated tests and provides mitigation guidance. - Integrate into SOC playbooks
Include simulation drills as part of detection toolchain. They not only validate log collection and detection logic, but also test alert-to-response handoffs via SOAR. - Validation post-tuning
Every tuning iteration should be re-tested. A cycle from Cymulate (integrate → correlate → validate → tune → re‑test) ensures continuous effectiveness.
Monitor Key KPIs: TPR, FPR, MTTR & MITRE Coverage
To ensure your SIEM delivers meaningful alerts and supports SOC efficiency, it’s critical to monitor performance metrics that reflect both rule quality and operational outcomes. Focus on these core KPIs:
- True Positive Rate (TPR)
A high TPR indicates that detection rules are accurately identifying real threats. Regular simulations after tuning should confirm improvements in TPR. Tools like Cymulate enable continuous validation by running known attack sequences against your SIEM to verify rule effectiveness. - False Positive Rate (FPR)
High false positive volumes lead to analyst fatigue and slower response times. You can reduce FPR through suppression rules, contextual filters and iterative tuning especially when guided by simulation-based feedback. AI/ML enrichment can further improve signal-to-noise ratios by understanding behavioral context. - Mean Time to Detect and Respond (MTTD/MTTR)
These metrics show how quickly your SOC identifies and reacts to real threats. Automating triage and leveraging AI-assisted correlation can significantly reduce both, helping the team stay ahead of fast-moving attacks. Integrating detection with SOAR workflows streamlines response and containment. - MITRE ATT&CK Coverage Percentage
A strong SIEM strategy ensures broad visibility across the threat landscape. By mapping your detection rules to MITRE ATT&CK techniques, you can visualize your overall coverage and prioritize gaps. ATT&CK heatmaps from Cymulate and validation tools are particularly useful for measuring and improving this metric over time.
Effective SIEM alerting isn’t a “set-and-forget” task, it’s a continuous cycle. To summarize the main points:
- Tune rules automatically and weed out redundancies.
- Contextualize alerts based on business criticality and severity.
- Align every detection to MITRE tactics with visual validation.
- Automate triage and suppress irrelevant noise.
- Test detection logic regularly using simulated attacks.
- Measure impact through KPIs like TPR, MTTR and coverage.
Prioritizing Alerts: What Deserves Attention?
Not all alerts are created equal. A meaningful triage process is key to SOC effectiveness.
Here’s how to prioritize SIEM alerts:
| Priority | Description | Example |
| High | Direct evidence of compromise or high-value target risk | Lateral movement to Domain Controller |
| Medium | Suspicious behavior, but context-dependent | Multiple failed logins on dev machines |
| Low | Policy or hygiene issue | Outdated software or log source misconfigurations |
Best Practices:
- Leverage risk scoring to stack alerts by potential impact.
- Focus on alerts tied to realistic attack paths, not hypothetical scenarios.
Cymulate maps alerts to adversary behavior and environment-specific risk, helping teams focus where it counts.
Cymulate Takes SIEM Alerts Further
Traditional SIEM setups often rely on manual rule tuning, static threat models and after-the-fact detection reviews. Cymulate transforms that reactive model into a proactive, AI-driven cycle of continuous improvement, empowering security teams to validate, optimize and enrich their detection posture in real time.
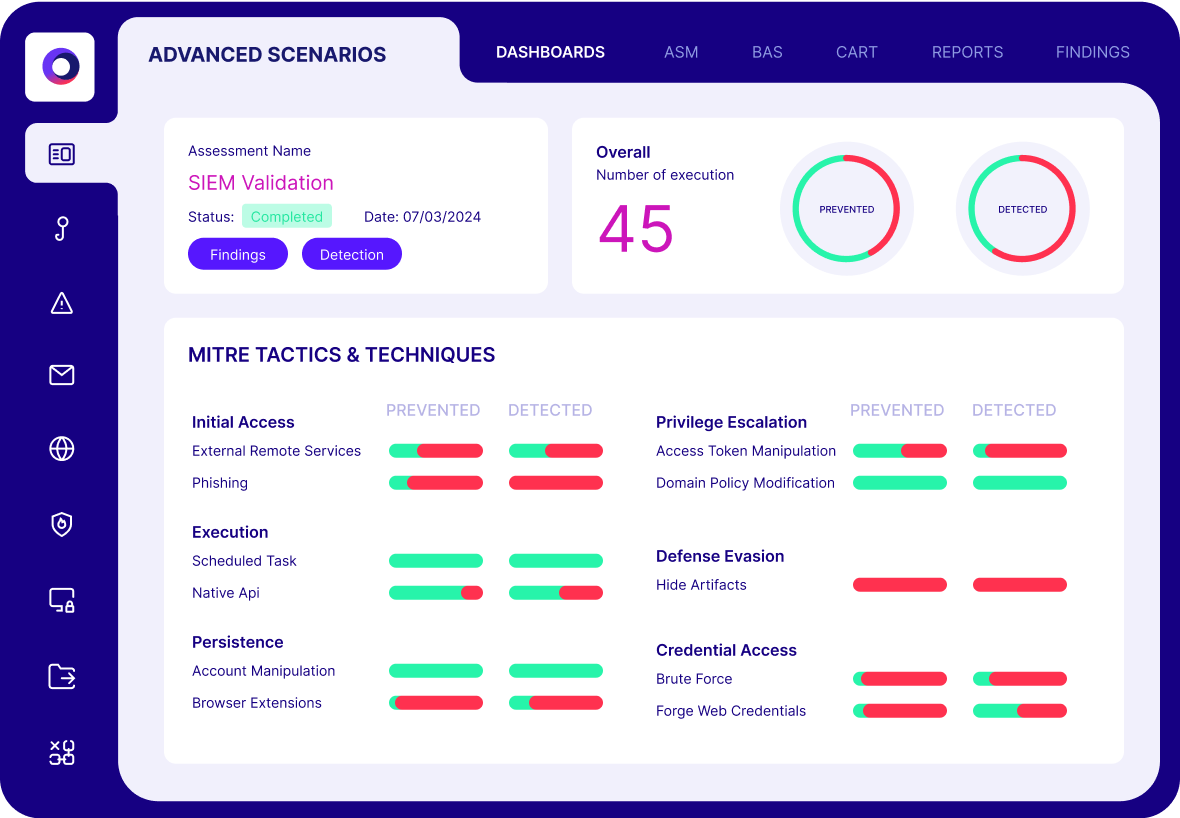
Validate Detection Logic in Real Time
Cymulate enables organizations to test whether their SIEM rules are working as intended before a real incident occurs. By simulating real-world threats aligned with the MITRE ATT&CK framework, security teams can confirm that correlation rules fire correctly, telemetry is complete, and detections are actionable.
This eliminates guesswork and makes SIEM validation empirical rather than speculative. Check out our SIEM Validation Guide. The platform offers native support for leading SIEMs like Splunk, Microsoft Sentinel and QRadar, making integration and feedback seamless.
Tune Based on Red/Purple Team Findings
Instead of siloing offensive testing, Cymulate allows teams to bridge the gap between red/purple team results and defensive rule tuning. Attack simulations generate telemetry and alert outcomes that can be directly fed into detection engineering processes.
Cymulate also supports detection-as-code workflows, enabling teams to codify findings, refine rule logic and re-test after updates. This creates a virtuous cycle of proactive defense that mirrors adversary behavior.
Cut False Positives and Alert Fatigue
One of the most valuable capabilities Cymulate offers is its impact on false positive reduction. By continuously testing detection logic and correlating alerts with expected threat behavior, Cymulate helps refine SIEM rules to reduce noise without losing visibility.
It also enables SOCs to validate whether enrichment strategies (such as threat intelligence or asset tagging) are being applied effectively to reduce non-actionable alerts. As detailed in their AI/ML blog, this optimization supports measurable reductions in MTTD and MTTR, making SOCs more responsive and resilient.
Continuously Assess Coverage Against MITRE ATT&CK
Cymulate maps simulated threats and alerting outcomes to the MITRE ATT&CK matrix, allowing organizations to visually track detection coverage across all tactics and techniques.
Security leaders can identify high-risk gaps, determine which MITRE techniques have weak or no alert coverage, and prioritize remediation efforts accordingly. This real-time visibility improves threat readiness and helps organizations align detection priorities with evolving attacker behaviors.
Use AI to Enhance Rule Engineering and Tuning
Cymulate provides an AI-powered rule analysis engine augments human efforts by analyzing rule structures, context, telemetry and outcome data. It offers automated suggestions for rule optimization, identifies redundancy and flags blind spots in detection logic.
This capability accelerates tuning cycles and supports detection engineers by reducing manual rule reviews. Whether you’re onboarding new threat content or refining legacy logic, this tool helps you achieve higher fidelity and efficiency in your SIEM environment.
Real-World Impact: RBI’s SIEM Optimization
Raiffeisen Bank International (RBI) used Cymulate to proactively validate and optimize their SIEM alerts. Key benefits included:
- Enhanced coverage across critical MITRE techniques
- Identification of non-functional or overly noisy rules
- Fast validation of new detection rules
- Improved alert quality and SOC efficiency
By incorporating Cymulate into their workflow, RBI moved from a reactive SIEM posture to a proactive, data-driven model, resulting in better threat visibility and reduced alert fatigue.
Make Every SIEM Alert Count
SIEM alerts only matter if they reflect reality. That means tuning detection logic, testing regularly and continuously validating your assumptions.
Cymulate empowers security teams to move from reactive to proactive. Every alert becomes a true signal, not just another distraction.
Ready to validate your SIEM alerting strategy? Explore the SIEM Observability Validation solution brief and request a demo today.



