What is Continuous Threat Exposure Management (CTEM)?
Continuous Threat Exposure Management (CTEM) is a proactive security program that continuously identifies, validates, prioritizes, and remediates cyber exposure across an organization’s entire attack surface. In other words, CTEM is not a single tool or technology, it’s an ongoing framework and set of processes for systematically reducing your risk.
The rationale behind CTEM is straightforward: by continually scoping your attack surface, discovering vulnerabilities and weaknesses, prioritizing which exposures matter most, validating security controls against real threats, and mobilizing the right fixes, you can stay ahead of attackers and strengthen your security posture over time.
Gartner analysts introduced CTEM as a top strategic approach for cybersecurity, predicting that organizations adopting CTEM to guide their security investments will experience dramatically fewer breaches (as much as a two-thirds reduction by 2026).
CTEM is rapidly gaining traction, a recent Gartner survey found 71% of organizations could benefit from a CTEM approach, with 60% already pursuing or considering a CTEM program.
Key highlights:
- Holistic CTEM framework: Continuous Threat Exposure Management is a five-phase model (Scope, Discover, Prioritize, Validate, Mobilize) that moves beyond traditional vulnerability management. It aligns security efforts with business priorities and evolving threats across on-premises and cloud environments.
- From reactive to continuous defense: CTEM replaces periodic fixes with continuous, proactive exposure management. Ongoing monitoring and validation help organizations remediate faster and stay ahead of attackers. Gartner projects that companies adopting CTEM will be 3x less likely to suffer a breach in coming years.
- Tangible security and business benefits: CTEM strengthens the link between security and business goals, automates validation, and delivers actionable risk insights.
- Cymulate’s end-to-end CTEM platform: Cymulate provides a unified Exposure Management Platform covering the full CTEM lifecycle: continuous attack-surface discovery, automated validation, risk-based prioritization, and guided remediation. Customers have reported over 50% reduction in critical exposures using Cymulate.
The 5 stages of the Continuous Threat Exposure Management lifecycle
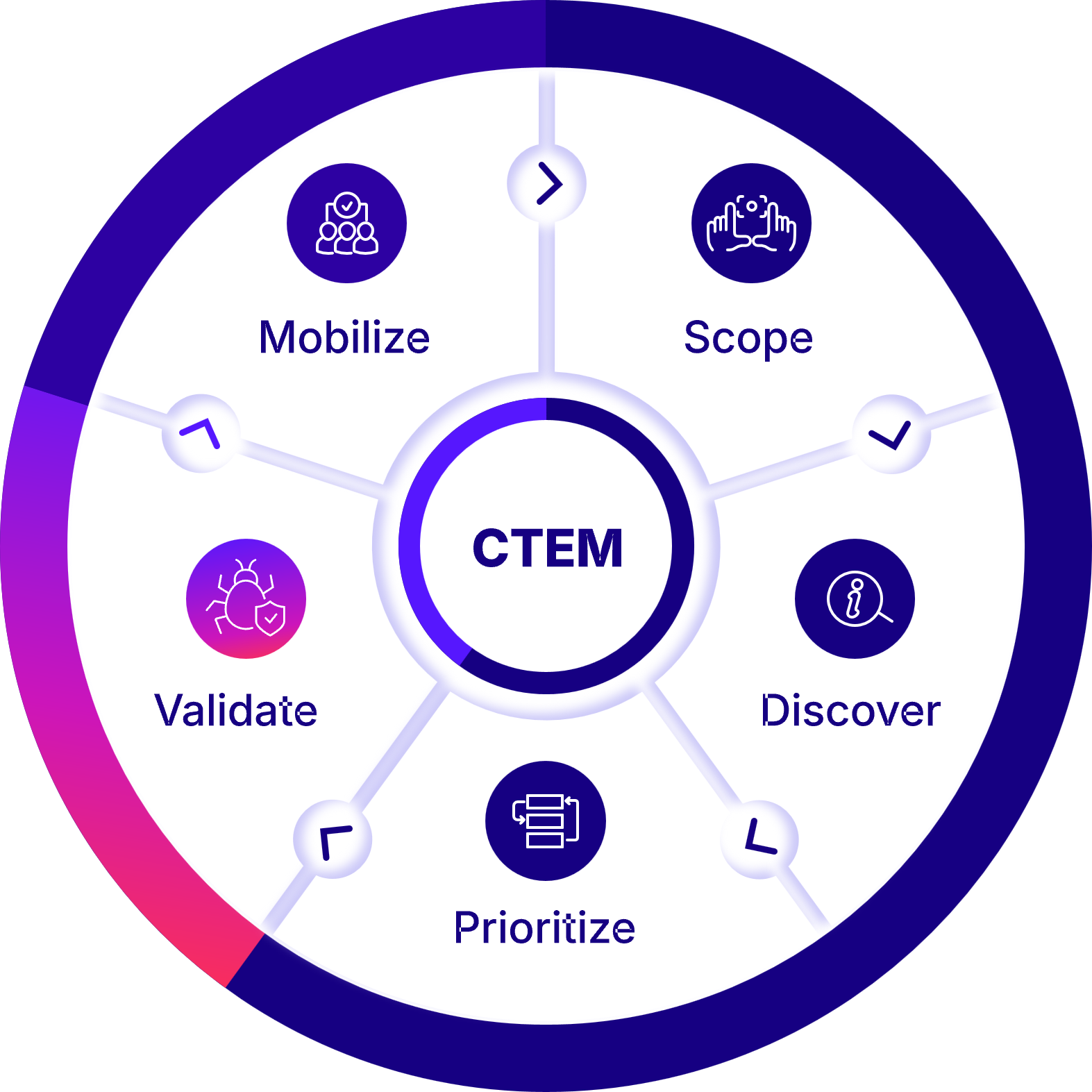
The five stages of the Continuous Threat Exposure Management (CTEM) program offer a comprehensive approach to managing security risks:
1. Scoping
The first step in an exposure management program is, naturally, scoping the exposure. This is done by mapping the external attack surface and the risks associated with SaaS and software supply-chain. It requires a collaboration between the business and the security functions to define (or refine, in later iterations) what is mission-critical, high value, or sensitive, and the business objectives to support it.
2. Discovery
Discovery consists of mapping the infrastructure, network, applications, and sensitive data assets, to find misconfigurations, vulnerabilities, and other tech/logic/process flaws and classify their respective risk.
3. Prioritization
CTEM advocates evaluating the likelihood of exploitability – with or without regard to compensating controls – as the basis to grade their relative importance. Where the exploitability likelihood is low, the security gap is scored as a low priority and could be postponed if sufficient remediation resources are unavailable.
4. Validation
“Validation ensures that identified threats are actionable and that security controls can mitigate them effectively”.
Launch simulated or emulated attacks on the previously identified exposures to evaluate the efficacy of existing defenses, and validate that the immediate response and remediation are adequate, making sure to leverage initial foothold gains to test the attacker’s ability to exploit lateral movement routes to the critical assets. This stage requires using a large variety of techniques to assess the efficacy of both security controls and procedures.
5. Mobilization
Taking corrective measures and actions deriving from business implications of the validation’s outcomes. It is usually done manually and within the local context. As CTEM depends much on collaboration, the remediation operationalization is expected to be near-frictionless and generate comprehensive information formatted to optimize rescoping for the subsequent cycle.
By following these five stages of the CTEM program, organizations can better manage their security risks and reduce their exposure to threats. It's important for businesses to be proactive in their approach, continually assessing, monitoring, validating, remediating.
Core components of the CTEM framework
While the five stages describe what a CTEM program does, it’s also useful to understand the key components and capabilities that make CTEM possible.
Successful CTEM programs typically integrate several core components (people, processes, and technologies) to support the continuous exposure management cycle. When building or evaluating a CTEM framework, make sure the following elements are in place:
1: Comprehensive asset visibility
You can’t manage exposures you don’t know about. A core component of CTEM is having tools for continuous asset discovery and attack surface management, including external attack surface management (EASM) to map internet-facing assets and shadow IT.
This provides a living inventory of your on-premises and cloud assets, applications, data, and users. Given that only a small minority of organizations (17%) can currently identify most of their assets, having this visibility is foundational.
2: Threat intelligence & context
CTEM solutions incorporate threat intelligence and business context to enrich the raw findings. This means mapping discovered vulnerabilities or weaknesses to real-world threat activity, for example, knowing which vulnerabilities are actively being exploited by attackers, or which assets are being targeted in your industry.
It also means understanding the criticality of assets (as determined in scoping) so that a vulnerability on a crown jewel server is treated with greater urgency than one on a low-tier system.
3: Risk-based prioritization mechanism
At the heart of CTEM is a risk scoring or prioritization engine that can analyze all identified exposures and score/rank them based on likelihood and impact. This component could be a dedicated exposure management platform or part of a vulnerability management tool that uses algorithms (often leveraging CVSS scores, threat intel, asset value tagging, etc.) to sort the critical few from the trivial many.
The prioritization capability should be dynamic updating as new threats emerge or as environments change, and it should produce clear outputs like risk ratings or tiered lists of what to fix now vs later. In essence, this is the “brain” of CTEM that ensures the program is always risk-driven rather than volume-driven.
4: Continuous security validation
Another core element is the ability to continuously test and validate your security controls against threats. This includes technologies like breach and attack simulation (BAS), automated red teaming tools, adversary emulation scripts, and other security testing tools that can validate exposures from an attacker’s point of view.
Incorporating a validation component means that CTEM doesn’t rely on theoretical risk alone, it actively checks if a vulnerability can be exploited and if your systems detect and stop it. Gartner notes that CTEM programs expand traditional assessments by including the attacker’s perspective and testing the effectiveness of security controls and incident response processes.
Essentially, this component answers “prove it” for each high-priority exposure. Without continuous validation, you might fix things that don’t actually pose a real threat or miss gaps in your detection/response; with validation, CTEM stays grounded in real-world security effectiveness.
5: Orchestrated remediation & collaboration
CTEM requires strong processes (and often tools) for orchestrating remediation and facilitating collaboration across teams. This component can include integration with IT service management or ticketing systems to create remediation tickets, workflows to assign tasks to the right owners, and tracking mechanisms to ensure fixes are implemented.
It also involves reporting and dashboarding capabilities to communicate progress and results to both technical staff and executives. A CTEM program should output easily digestible reports (e.g. an executive dashboard of exposure trends and risk metrics, as well as detailed technical reports for the ops teams). Executive leadership and cross-team buy‐in are critical for CTEM success, so this component ensures there is transparency and alignment.
Think of it this way: CTEM isn’t just a process to follow, but also an ecosystem of capabilities, asset discovery to know what you have, analytics to know what’s risky, validation to know what’s real, and collaboration to actually get things fixed. When evaluating CTEM solutions or building out your program, ensure you have strength in each of these areas so that the five CTEM stages can run effectively and continuously.
6 benefits of implementing CTEM solutions
Security and business leaders that successfully implement CTEM increase the maturity and effectiveness of their cyber programs with technical, business, and operational benefits that combine into reduced exposure risk and improved security posture.
Here are six ways CTEM enables organizations to move from primarily reactive to primarily proactive security, continuously improving defenses in alignment with business needs:
1. Business alignment
CTEM translates technical findings into business insights, enabling data-driven decisions aligned to business objectives and improved communication between security and executive teams.
2. Continuous validation
Ongoing CTEM activities like breach simulations and red team exercises validate security controls and posture continuously versus point-in-time audits.
3. Efficiency at scale
Automating CTEM steps like discovery, validation, and data correlation allows assessments at higher frequency and comprehensiveness while efficiently scaling across the environment.
4. Actionable insights
CTEM not only reveals gaps and weaknesses but also provides clear prioritized guidance and integrated workflows to accelerate remediation.
5. Measurable resilience
CTEM metrics and trend reports provide tangible visibility into reduced risk exposure, creating objective measures of security posture improvements over time.
6. Consolidated visibility
Rather than introducing more siloed tools, platforms which integrate multiple CTEM processes streamline and connect workflows across capabilities for greater efficiency.
Learn more about validation and mobilization.

The ultimate goal of CTEM
Ultimately, CTEM is about security posture optimization. Its continuous nature allows quick remediation and the application of lessons learned from each cycle. Success depends on agility, accelerated by both automation and rapid mobilization. This way, organizations can meet risk requirements aligned with business priorities and executive expectations.
Continuous improvement is a core principle of CTEM. It is not a one-time project but an ongoing process that requires constant evaluation, adaptation, and refinement to keep pace with evolving threats and changing business needs.
The urgency for this approach is clear. Despite millions invested in scanners and defensive controls, most organizations cannot prove resilience against threats or react fast enough when exposures are identified. Security teams face:
- Noisy exposure discovery that overwhelms analysts with false positives.
- Misguided prioritization that diverts attention from truly critical risks.
- Suboptimal defensive controls that fail to perform as expected under attack conditions.
- And as a result, 88% of organizations still suffer incidents despite significant security investments according to Logicalis 2025 CIO Report.
CTEM directly addresses these shortcomings by providing validated, prioritized, and business-aligned guidance. Instead of chasing noise, organizations gain valuable insights, intelligence, and context that enhance the effectiveness of the Security Operations Center (SOC).
With a continuous exposure management solution in place, businesses can adopt a forward-looking approach to cybersecurity. This enables faster response to incidents, resilience against advanced threats, and a security posture that can be demonstrated—not just assumed.
How to choose the right CTEM vendor
With the growing popularity of continuous exposure management, many security vendors now claim to offer “CTEM solutions” or related capabilities. It can be challenging to sort through the marketing and determine which solution is the best fit for your organization’s needs.
When evaluating CTEM vendors, keep in mind that true CTEM platforms should cover the end-to-end program (not just a single slice of it) and enable the practices described above. Here are some key criteria and features to look for when choosing the right CTEM solution:
1: Comprehensive exposure coverage
The solution should provide full coverage of your attack surface, including both external and internal assets. This means it likely should include or integrate with external attack surface management (EASM) to handle internet-facing asset discovery, as well as internal network scanning and cloud security posture capabilities.
The best CTEM solutions ensure you have no blind spots, they can continuously discover shadow IT, cloud instances, rogue servers, and more, keeping your asset inventory complete.
2: Continuous validation and threat simulation
A distinguishing feature of CTEM tools is the ability to validate exposures through simulated attacks. When evaluating vendors, check that they offer capabilities like breach and attack simulation (BAS), automated or guided penetration testing, or integration with red teaming tools. This ensures the platform can actually test and confirm which findings are exploitable and whether your controls work.
For example, does the vendor provide a library of attack scenarios or allow you to emulate tactics from frameworks like MITRE ATT&CK? Can it test both preventive controls (by attempting exploits) and detective controls (by seeing if your SOC alerts on the simulated breach)? Continuous validation is critical for a CTEM solution to deliver value beyond what a basic scanner would, so a top CTEM platform will have strong features in this area (or seamless integration with third-party BAS, etc.).
3: Risk-based prioritization and analytics
The vendor should employ intelligent prioritization algorithms and provide clear risk scoring. This means the solution should automatically correlate findings with threat intelligence (for example, flag if a critical vuln has active exploits or if a certain misconfiguration is being used by ransomware groups).
It should factor in asset criticality (allowing you to tag or categorize importance) and ideally even suggest the potential impact of an exploit (e.g., “this vulnerability could lead to data theft of customer records”).
Look for a platform that presents results in a prioritized way by default, e.g. a dashboard of “top 10 exposures to address”, rather than just dumping raw scan results on you. The ability to customize risk criteria to your environment is a plus. Ultimately, the best CTEM solutions will surface what most threatens your business, saving you from analysis paralysis.
Ask vendors how their product ensures you’re not overwhelmed with false positives or low-value findings, and how it helps you focus on the critical few issues.
4: Integration and automation
A CTEM solution needs to fit into your existing security and IT ecosystem. Prioritize vendors that offer strong integrations with your current tools, for example, does it integrate with popular vulnerability scanners (to import existing scan data), with SIEM/SOAR platforms (to enrich findings or handle response), with cloud platforms and containers, with ticketing systems like Jira or ServiceNow for remediation workflow, etc.?
The more interconnected the platform, the easier it will be to operationalize CTEM without heavy manual effort. Automation is equally important: look for features like scheduling of regular scans/attack simulations, automated ticket creation for high-risk findings, and even automated remediations (like pushing a firewall rule or disabling a compromised account automatically if policy allows).
These capabilities are what enable continuous management at scale. If a vendor’s solution requires a lot of manual driving or doesn’t play well with other tools, it may hinder the efficiency of your CTEM program.
5: Reporting and executive metrics
Since one of CTEM’s goals is to improve communication and visibility, choose a vendor that offers robust reporting and dashboarding functionality. You’ll want both granular technical reports (for analysts to drill into details) and high-level summaries for leadership. Features to look for include: trend charts of your exposure level over time, risk reduction metrics, benchmarks against industry standards, and customizable reports that map to your organization’s KPIs.
A good CTEM platform should be able to show the before and after impact of your remediation efforts in each cycle, and produce proof of improvement (e.g. “we have 30% fewer critical exposures this quarter than last”). Also, consider whether the vendor provides out-of-the-box executive reports or even integrations to business risk dashboards.
The ability to translate technical risk to business terms (like potential financial impact or compliance risk) is a differentiator. Essentially, the solution should help you answer “How secure are we now, and how is that improving?” in a quantifiable way.
6: Vendor expertise and support
Don’t overlook the importance of the vendor’s experience and support structure. CTEM is a relatively new approach, so it can be valuable to choose a provider who has a strong track record in this space or related disciplines (like breach simulation, exposure management, etc.).
Consider whether the vendor is recognized by analysts (for instance, being noted in Gartner reports or Forrester studies) and whether they have reference customers who have successfully implemented CTEM using their product.
Since CTEM spans people and process as much as technology, having a supportive vendor can accelerate maturity. Ensure that the solution’s complexity matches your team’s capabilities, some platforms may be very advanced but require specialized expertise to use effectively, so gauge the learning curve and available help (documentation, community, etc.).
Remember that CTEM is not achieved by a single tool alone, but the right platform can greatly simplify and unify your continuous threat exposure management efforts. Look for a vendor that checks the boxes across discovery, validation, prioritization, and integration, this will set you up for success in implementing the CTEM framework.
Why Cymulate leads in Continuous Threat Exposure Management
Cymulate accelerates achieving CTEM by providing a platform that supports the entire lifecycle across all five phases. Cymulate Exposure Management Platform allows for seamless integrations to discover assets and exposures, runs attack tests to validate existing security prevention and detection capabilities, contextually scores and prioritizes exposures and delivers automated remediations.
1. Continuous threat Validation in one platform
Most exposure management solutions stop at discovery. Cymulate goes further by putting the “T” in CTEM — continuously validating exposures against real-world threats to prove which ones are truly exploitable.
With one multifunctional platform, Cymulate unifies:
- Attack Path Discovery
- Automated Red Teaming (CART)
- Breach and Attack Simulation (BAS)
- Exposure Prioritization and Remediation
All of this consolidation in one platform means security teams can cut through noisy scan results and focus on validated, evidence-backed threats.
For example, if Cymulate’s BAS scenarios show that a critical vulnerability on Server X can indeed be exploited to achieve domain admin privileges (while dozens of other vulnerabilities could not lead anywhere significant), you know exactly where to direct your effort. This integrated approach streamlines workflows that used to be spread across multiple siloed tools. The end result is a demonstrably stronger security posture,Cymulate customers have reported materially improved outcomes from this approach.
Proof Point: Customers report a 52% reduction in critical exposures and a 30% increase in threat prevention after using Cymulate’s continuous validation platform, as it allowed them to prioritize and fix the most impactful weaknesses first. In short, Cymulate delivers proven resilience against the attacks that matter most by combining all core CTEM functions into a unified, easy-to-use solution.
2. Automate testing across teams and processes
CTEM is as much about people and process as it is about technology. Cymulate recognizes this by making it easier to operationalize CTEM across various security teams (SecOps, incident response, vulnerability management, etc.) through extensive automation and easy workflows.
Advanced security testing techniques that once required expert red teams can now be run by a small SecOps team on a continuous basis using Cymulate’s platform. The solution provides automation and even AI-driven assistance for tasks like:
- Continuously test SOAR playbooks, SOC workflows, and incident response procedures.
- Automate breach and attack simulations using the latest intelligence.
- Provide ready-to-use Sigma detection rules and mitigation guidance for seamless remediation.
This automation helps teams operationalize CTEM at scale, ensuring every cycle of scoping, discovery, validation, and mobilization is faster, smarter, and less resource-intensive.
3. Translate technical findings into business outcomes
One of Cymulate’s strengths is helping bridge the gap between technical cybersecurity details and high-level business risk and performance metrics, a crucial aspect of CTEM.
The platform is built with extensive analytics and reporting features that turn raw findings into meaningful business-oriented insights. With Cymulate, organizations can transform technical data into:
- Validated exposure scores
- Clear resilience metrics
- Performance benchmarks and ROI tracking
This focus on translating findings to business outcomes means security leaders can prove the organization’s resilience in tangible terms, and communicate to non-technical stakeholders in a language they understand. Cymulate aligns its output with the CTEM objective of executive visibility and straightforward reporting.
Prove threat resilience
Integrate exposure discovery
Focus on the exploitable
Build threat resilience
Put CTEM into action with Cymulate
Moving from a reactive approach to a proactive approach against cybersecurity threats with programs like Continuous Threat Exposure Management can help organizations better prioritize their efforts and build greater resilience over time against these types of attacks.
With the rise of cyber-attacks and data breaches, companies should take a proactive approach towards cybersecurity and risk management by gaining a deeper understanding of their cyber estate on an ongoing basis.
This will enable organizations to take prompt action based on a thorough, contextual analysis, thereby facilitating a more proactive approach to addressing cyber risks through advanced strategies like continuous threat exposure management in their security operations led by security leaders.
Cymulate’s platform helps you with better and faster decision-making for a successful Continuous Threat Exposure Management program and its ultimate KPI. If security posture is tested in advance, preemptive measures are taken, risks remain low, and adversaries are likely to move on to the next target.
Request a demo to see how Cymulate can help you with exposure management.
Frequently asked questions
CTEM is a continuous program that cycles through scoping, discovery, prioritization, validation and mobilization. Red team exercises are one-off simulations of attacker behavior, often used once or twice a year. In CTEM, red teaming becomes part of the validation phase, but CTEM goes further by ensuring findings are prioritized, remediated and re-tested in every cycle.
Penetration testing is a point-in-time check, typically limited in scope, producing a static report. CTEM is on the other hand is ongoing, it not only identifies exposures but also validates which ones can be exploited, prioritizes by business impact, and drives remediation into workflows. Pen testing is tactical; CTEM is programmatic and strategic. Both complement each other, but CTEM ensures pen test results are acted on and continuously revisited.
Continuous Threat Exposure Management (CTEM) is a strategic framework designed to help organizations continuously identify, prioritize, validate, and remediate security exposures. Its strength lies in providing a business risk–aligned roadmap for reducing the most impactful vulnerabilities, misconfigurations, and attack paths across the environment. CTEM takes a holistic approach, considering not just the technical side but also how exposures translate into real business risk to make sure that remediation efforts are focused on what matters most.
Breach and Attack Simulation (BAS), on the other hand, is a tactical technology that tests whether defenses can detect, block, or respond to real-world attack techniques. BAS delivers hands-on validation by simulating adversarial behaviors in a safe environment, providing technical evidence of how well existing controls perform. While CTEM is the ongoing program that drives exposure management, BAS acts as one of its key tools during the validation phase. In practice, CTEM provides the big-picture strategy, and BAS ensures that the defenses supporting that strategy are working as intended.
IAM and ITDR are tools for identity management and detecting compromised accounts. CTEM is broader: it manages exposures across identities, infrastructure, applications, cloud and supply chain.
Identity issues may surface during CTEM discovery and prioritization, but CTEM also includes validating if attackers can abuse them and ensuring fixes are applied. IAM/ITDR handle identity; CTEM orchestrates everything, including identity, in a continuous cycle.
EASM (external attack surface management) tools only map and monitor internet-facing assets, like domains or exposed servers. CTEM platforms cover internal and external assets, validate whether exposures are exploitable, prioritize them by risk, and integrate remediation workflows. If a solution stops at external discovery, it’s EASM. If it runs the full lifecycle, it’s a CTEM platform.
No, Managed Detection and Response (MDR) and Continuous Threat Exposure Management (CTEM) are not the same. MDR focues on detecting and responding to active threats in real time, while CTEM focuses on identifying, validating, and prioritizing potential attack paths before they can be expolited by malicious threat actors.
While different, MDR and CTEM are complementary. Simply put, CTEM reduces the number of exploitable weaknesses, while MDR catches what slips through.
CSPM (cloud security posture management) focuses on cloud misconfigurations like open storage buckets or weak IAM roles. CTEM spans all environments cloud, on-prem and SaaS and adds prioritization and validation to ensure the riskiest issues are addressed. The two work best together: CSPM feeds cloud findings into CTEM’s broader program.
Yes. CTEM is environment-agnostic. It scopes and discovers assets across on-prem data centers, hybrid networks, cloud platforms and SaaS applications. Validation and remediation apply equally across these environments, creating a unified, continuous view of exposures. This ensures attackers cannot exploit the weakest link, wherever it resides.