Cloud Security Management
Managing security in cloud environments is increasingly complex due to shared responsibility models, rapidly changing configurations and the scale of modern cloud deployments. As organizations adopt multi-cloud architectures and support new analytics and AI workloads, maintaining visibility, control and trust becomes more challenging.
In this article, we’ll explore what cloud security management is, the risks organizations face and how to implement effective strategies and best practices to protect cloud environments at scale.
Key highlights:
- Cloud security management is the practice of securing cloud-based data, applications and infrastructure through coordinated policies, controls and continuous oversight.
- Cloud environments introduce distinct security challenges such as misconfigurations, identity misuse and limited visibility that require approaches beyond traditional IT security models.
- An effective strategy for managing cloud security combines governance, automation and continuous validation to ensure controls remain effective as cloud environments evolve.
- Cymulate helps organizations validate cloud security controls continuously, enabling teams to identify gaps, reduce risk and strengthen trust across AWS, Azure and GCP.
What is cloud security management?
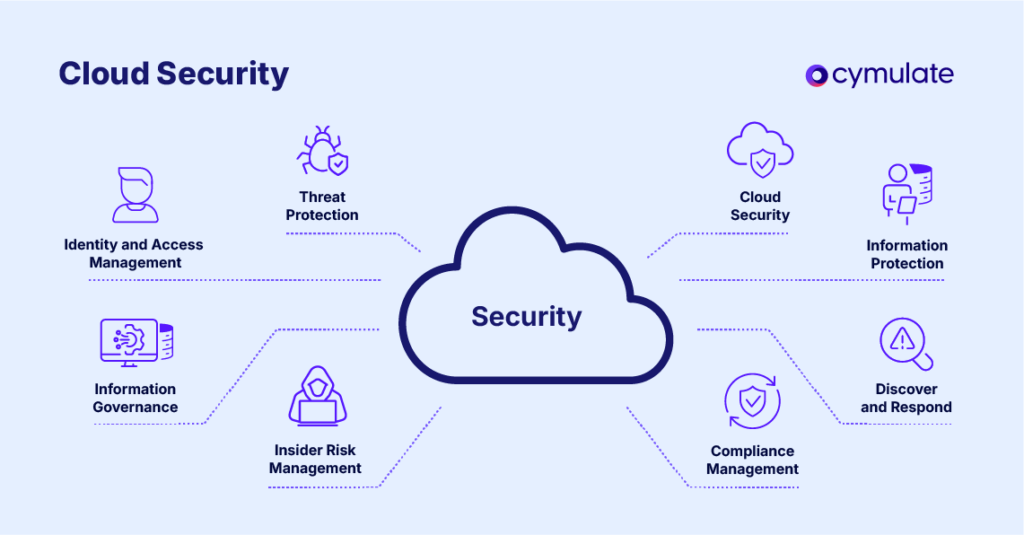
Cloud security management is a cybersecurity practice that encompasses the strategies, policies, procedures and technologies required to protect data, applications and infrastructure in cloud computing environments. It addresses the unique challenges presented by the cloud's dynamic and distributed nature, going beyond perimeter security to secure:
- Workloads
- Data
- Access within the cloud
The purpose of cloud security management tools is to protect cloud-based data, applications and infrastructure by maintaining confidentiality, integrity and availability across multi and hybrid-cloud environments such as AWS, Azure and GCP.
The high stakes of security management in cloud computing
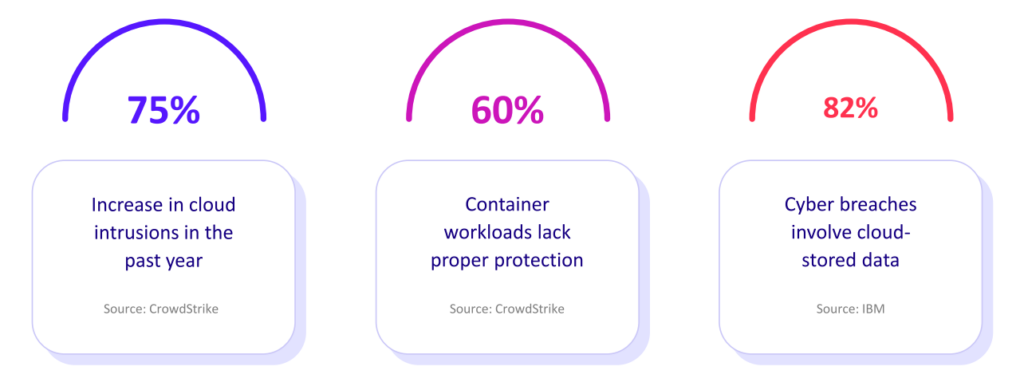
A cloud data breach can have devastating consequences, including financial losses, reputational damage, legal liabilities and operational disruptions. In fact, as IBM reported, 82% of breaches in 2024 involved data stored in the cloud and cost enterprises an average of $4.88 million.
Security management in cloud computing is becoming a top concern for most organizations, which is understandable given the 75% increase in incidents in the past year alone, according to CrowdStrike.
With the growing amount of cloud threats and rising data breach costs, organizations that take cloud security seriously gain a critical advantage. A well-structured cloud security program allows you to:
- Protect sensitive data: Cloud security helps ensure unauthorized access is prevented, and theft of company and customer information is deterred. Strong encryption, access controls and regular data backups are essential components for this defense.
- Prevent disruptions to critical business operations: Robust cloud security keeps essential business applications and services consistently available, supporting business continuity during potential disruptions.
- Ensure compliance: In the complex regulatory landscape, staying in compliance with data privacy laws and relevant industry regulations is paramount.
- Maintain customer trust and confidence: Demonstrating a steadfast commitment to robust data protection is vital for sustaining customer loyalty.
Clearly articulating and demonstrating stringent measures for managing cloud security, including transparency regarding data handling practices and robust protection against breaches, establishes a reliable and dependable cloud environment, instilling confidence in customers and solidifying trust in the services provided.
Challenges in cloud security and trust management
As organizations adopt cloud-first and multi-cloud architectures, managing security and trust becomes significantly more complex. Unlike traditional environments, cloud platforms introduce unique operational and security challenges that make consistent protection harder to achieve.
Key challenges include:
- Fragmented security controls across cloud providers: AWS, Azure and Google Cloud each offer different security services, configuration models and identity frameworks, making it difficult to apply consistent policies across environments.
- Increased risk of misconfigurations: The scale and flexibility of cloud environments increase the likelihood of exposed storage, overly permissive access policies and unsecured services, which remain leading causes of cloud breaches.
- Limited visibility across dynamic environments: Rapid deployments, ephemeral workloads and constant configuration changes can obscure security gaps and make it difficult to maintain an accurate view of cloud risk.
- Complex trust management: Establishing and maintaining trust requires proving that security controls are correctly configured, continuously enforced and effective over time — not just defined on paper.
- Specialized expertise requirements: Managing security across multiple cloud platforms often demands deep provider-specific knowledge, increasing operational overhead and leaving room for human error.
Without a unified approach to visibility, governance and continuous validation, these challenges can weaken security posture and erode confidence in cloud environments.
Core security objectives in cloud environments
The core objectives of cloud security management are interconnected and crucial for establishing a fortified security posture. They should not be treated as isolated elements; instead, a comprehensive strategy integrates them to create a robust and resilient posture.
Here are the three core objectives of security management in cloud environments:
1. Prevent threats
Establishing a robust defense mechanism involves proactively securing cloud workloads like virtual machines, containers and serverless functions against diverse cyber threats. This entails implementing intrusion detection systems (IDS/IPS), conducting regular vulnerability scanning and reinforcing security hardening measures to counter potential intrusions effectively.
2. Detect and respond to risk
Continuously monitoring cloud activities for anomalies or indicators of malicious behavior in real-time ensures prompt detection and efficient incident response. This approach entails using Security Information and Event Management (SIEM) systems and well-defined incident response plans to swiftly mitigate incidents.
3. Maintain compliance
Ensuring adherence to relevant industry regulations and established security frameworks like the NIST Cybersecurity Framework and ISO 27001 is critical. Compliance frameworks provide structured guidance for safeguarding data and maintaining a robust cloud security posture.
Traditional IT vs cloud security: Main differences
Traditional IT security was built for static, on-premises environments with clearly defined network perimeters and physical infrastructure. Cloud security management solutions operate under different conditions, including virtualized resources, continuously changing environments, and access beyond a single network boundary.
Here’s a closer look at the main differences:
| Core aspects | IT practices | Cloud security practices |
| Security model | Rely on perimeter-based defenses, such as firewalls, to protect the internal network | Verify user and device identities and protect data itself, regardless of location |
| Change velocity | Remain relatively static, with fewer changes and updates happening | Dynamic, with frequent updates, new deployments and configuration changes |
| Infrastructure abstraction | Focus on protecting physical servers and network devices | Focus on protecting virtualized resources |
Understanding the shared responsibility model
A fundamental concept in cloud security is the shared responsibility model that defines the responsibilities of the cloud service providers and customers. The cloud provider is responsible for the security of the cloud itself, which includes the physical infrastructure, the underlying network and the physical security of their data centers.

The customer is responsible for the security in the cloud, which includes their data, applications, configurations and the management of access to their cloud resources. The specific division of responsibilities varies depending on which of the following cloud service models is being used:
- Infrastructure as a Service (IaaS): The customer has the most responsibility, managing the operating system, applications, data, access management and configurations.
- Platform as a Service (PaaS): The customer manages the applications, data, access management and configurations. The cloud provider manages the infrastructure, operating systems and platform services.
- Software as a Service (SaaS): The customer has the least responsibility, managing only the data, user access policies and configurations. The cloud provider manages the infrastructure, operating systems, platform services and applications.
Misunderstanding the shared responsibility model is a common cause of security gaps in cloud deployments.
Key threats to cloud security
Cloud environments face a distinct set of security threats driven by their scale, accessibility and reliance on identity and configuration. Understanding how these threats manifest is essential for protecting cloud workloads and preventing breaches.
Here are the three most prevalent threats to cloud security that organizations currently face:
1. Misconfigurations and poor access control
Misconfigurations in cloud resources are a leading cause of data breaches. Common misconfigurations include publicly accessible storage buckets, improperly configured security groups and overly permissive Identity and Access Management (IAM) policies.
2. Insider threats and unauthorized access
Insider threats, whether intentional or unintentional, pose a significant risk to cloud security. The broad access to sensitive data and the inherent remote accessibility of cloud environments can amplify the potential impact of insider actions.
Even compromised insider accounts, where external attackers gain control of legitimate user credentials, can be leveraged for malicious activities. Robust monitoring and rigorous access controls are essential for mitigating these threats.
3. API-based attacks, ransomware and lateral movement
APIs are essential for integrating and enabling cloud services, but they also create a significant attack vector. Insecurely implemented APIs can provide attackers with entry points to gain unauthorized access to cloud services and the valuable data they contain.
Main cloud security frameworks
A good cloud security structure requires adherence to industry-recognized frameworks and relevant compliance regulations. These standards provide a structured approach to managing risks and ensuring data protection.
These are the key frameworks used to maximize cloud security:
NIST cybersecurity framework (CSF)
The CSF offers a flexible, risk-based approach to managing cybersecurity risks. Organized around five core functions – identify, protect, detect, respond and recover – the CSF provides a structured methodology for organizations to:
- Identify their critical assets and the cybersecurity risks they face.
- Implement appropriate security controls to protect those assets.
- Detect security incidents in a timely manner.
- Respond effectively to mitigate the impact of incidents.
- Recover quickly to restore normal operations.
ISO 27001/27017
ISO 27001 is a globally recognized standard for Information Security Management Systems (ISMS). Achieving ISO 27001 certification demonstrates a strong commitment to data security and provides a framework for establishing, implementing, maintaining and continuously improving an ISMS.
CIS controls for cloud security
The CIS Controls for Cloud Security offer a set of prescriptive, prioritized and simplified best practices designed to strengthen an organization's cybersecurity posture across all environments, including the cloud.
Managing regulatory compliance in the cloud
Managing regulatory compliance in the cloud introduces added complexity due to shared responsibility models, distributed data storage and continuously changing cloud configurations. Organizations must ensure that sensitive data remains protected and auditable across cloud services while meeting industry and regional regulatory requirements.
Achieving compliance in the cloud requires not only implementing the right controls, but also continuously validating that those controls remain effective as environments evolve. Regulations that need to be considered are:
- General Data Protection Regulation (GDPR): Safeguards the personal data and privacy of individuals within the European Union, necessitating specific technical and organizational measures for data protection and accountability.
- Health Insurance Portability and Accountability Act (HIPAA): Mandates the safeguarding of Protected Health Information (PHI) for healthcare organizations, necessitating Business Associate Agreements (BAAs) with cloud providers and specific security controls.
- Payment Card Industry Data Security Standard (PCI DSS): Outlines security standards for organizations handling credit card data, mandating the implementation of technical and procedural controls for protecting cardholder data.
Adherence to these industry-specific regulations is essential, and it’s crucial to validate the effectiveness of implemented security controls to maintain compliance. Through rigorous testing and simulation, using solutions like Cymulate Threat Validation, enterprises can prevent and detect real-world attacks that threaten data.
How to implement a cloud security strategy
Effectively protecting and defending cloud assets requires a well-defined and diligently implemented cloud security process. Here are the four key steps for developing such a strategy, from conducting risk assessments to integrating automation and continuous validation:
Step 1: Conduct a risk assessment for cloud environments
The first step in implementing a cloud security strategy is to conduct a thorough risk assessment specifically tailored to the cloud environment. This assessment should identify potential threats and vulnerabilities, assess the likelihood and impact of each risk and prioritize risks based on their severity and potential business impact.
Step 2: Align security measures with business and compliance needs
Security measures should be aligned with both business objectives and compliance requirements. Ensure that security controls not only meet regulatory mandates but also support the organization's overarching business goals. This requires a careful balancing act to maintain robust security without hindering operational efficiency or usability.
Step 3: Integrate security automation and continuous validation
Automating routine security tasks, such as vulnerability scanning, patching and configuration management, reduces manual effort and the potential for human error. Implementing continuous security validation ensures that security controls are functioning as intended and can effectively defend against current and emerging threats.
Step 4: Perform ongoing threat monitoring, attack simulation and remediation
An effective cloud security strategy requires ongoing threat monitoring to detect suspicious activities and emerging threats. Regular attack simulations, using tools like Breach and Attack Simulation (BAS), validate the effectiveness of defenses against the latest threats and identify areas for improvement. A well-defined incident response plan is essential for quickly and effectively remediating any security incidents that may occur.
Best practices for cloud security
By adopting effective strategies, organizations can improve their posture, reduce the risk of data breaches and maintain customer trust. Mitigating threats and strengthening defenses requires implementing and consistently monitoring the following four best practices for cloud security:
1. Apply effective identity and access management
Effective IAM is fundamental to cloud security. Robust controls around identity and access prevent unauthorized users from accessing cloud resources and performing malicious activities.
To ensure a strong IAM, you need to apply:
- Zero trust: Employ ongoing authentication and authorization for every user and device attempting to access cloud resources.
- Least privilege access: Grant only the minimum permissions needed for users and systems to do their jobs, helping prevent damage or breaches and aligning with the principle of least privilege.
2. Apply comprehensive data protection
A strategy that incorporates policies and technologies designed to safeguard sensitive information both in transit and when stored in the cloud is at the heart of data protection.
A solid data protection strategy should include:
- Encryption: Ensure data remains confidential and appears unreadable in the event of interception. This data protection method should be applied when data is at rest and in transit.
- Tokenization: Exchange sensitive data for non-sensitive surrogates, also called tokens. This approach enables better privacy protection during storage or while conducting processing in less secure settings.
- Data Loss Prevention (DLP): Secure private data by flagging and managing it as well as minimizing leakage, regardless of whether the leaks came from incidents or intentional disclosures from inside their cloud networks.
3. Ensure consistent network and application security
Robust measures that shield the network and applications create an impregnable barrier against potential breaches and unauthorized activity, and fall within network and application security.
Your strategy should include:
- Web Application Firewalls (WAFs): Sift through all potentially malicious activity to mitigate attacks that exploit SQL injection or cross-site scripting.
- Container Security: Protect containerized platforms from image design through runtime, given the ubiquity of these containers in the cloud.
4. Automate threat detection and response
Quickly identifying and addressing security threats is vital to reducing harm and limiting damage to infrastructure, operations and data. Using processes that actively identify threats in the cloud enables security experts or those managing operations to respond as efficiently as possible to real and looming breaches.
- Breach and Attack Simulation: Regular simulations of real-world scenarios conducted by companies help security staff proactively identify shortcomings in protective technologies before malicious actors expose them.
- Cloud Security Posture Management (CSPM): Automate the detection of misconfigurations, identify security gaps and ensure compliance with industry standards and best practices within cloud environments.
Enhance cloud security posture with validation from Cymulate
Cymulate offers a robust and comprehensive platform that significantly enhances cloud security through its validation capabilities. Cloud security validation enables you to optimize your security controls and better protect the systems and data hosted in your environments.
The platform offers nearly 8,000 cloud attack scenarios to test high-privilege actions with an “assume breach” mindset, identifying exploitable vulnerabilities across AWS, Azure and GCP.
These production-safe tests emulate real-world attacks, such as:
- Identity-based attacks
- API vulnerabilities
- Lateral movement attempts
Book a demo today and see how Cymulate cloud security management solutions can help your organization validate the effectiveness of its existing controls. vironment.