Cloud Security Posture Management (CSPM): A Guide
Cloud misconfigurations remain one of the leading causes of cloud data breaches. As organizations expand across AWS, Azure, and Google Cloud, maintaining consistent visibility and control becomes increasingly difficult. Cloud Security Posture Management (CSPM) addresses this challenge by continuously monitoring configurations, enforcing compliance and automating remediation across multi-cloud environments.
This guide explains what CSPM is, why it matters, how it works and how validation through Cymulate strengthens its effectiveness.
Key highlights:
- Cymulate extends the value of CSPM by turning posture management into measurable assurance, validating that cloud defenses are resilient against real-world threats.
- Cloud Security Posture Management (CSPM) is a continuous process that identifies, assesses and remediates cloud misconfigurations and compliance risks to maintain a secure and compliant posture.
- CSPM helps organizations prevent breaches caused by human error and configuration drift while simplifying governance across providers.
- Modern CSPM solutions combine posture management with workload and container protection for broader coverage.
What is CSPM?
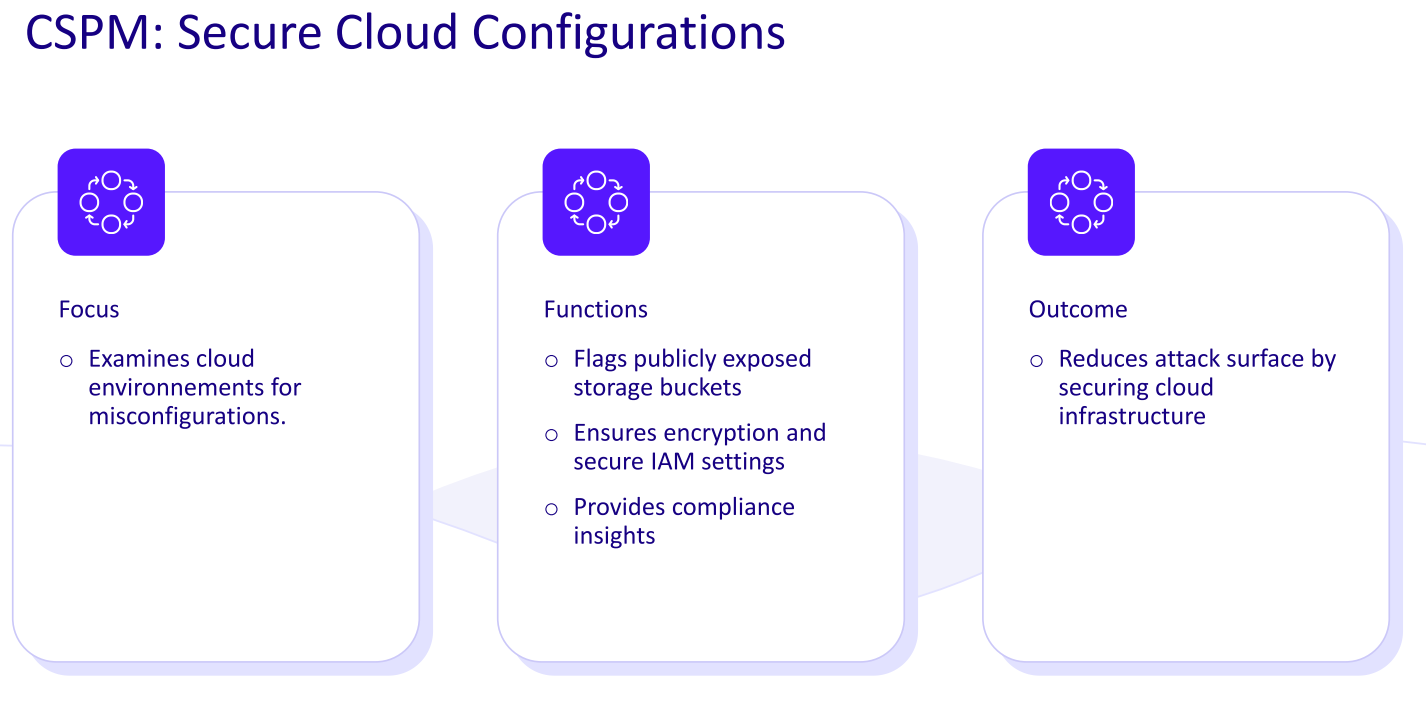
Cloud Security Posture Management (CSPM) is the continuous process of identifying, monitoring and remediating misconfigurations and compliance risks across cloud environments to prevent data breaches and policy violations.
Specialized CSPM security tools scan your cloud infrastructure (such as AWS, Azure and Google Cloud) for risky misconfigurations, gaps and compliance violations. If something’s off, for example, a storage bucket is public when it shouldn’t be, it flags it and often helps fix it before it becomes a real problem.
This solution gives teams visibility across IaaS, PaaS and SaaS environments, continuously comparing your setup against best practices and benchmarks. This reduces your attack surface by eliminating unsafe defaults and human error.
Why strong cloud posture management matters
According to Gartner, the CSPM market is on track to hit $3.3 billion by 2027. It’s clear that more organizations than ever are cloud-first chasing agility, speed and scale. But with that shift comes risk.
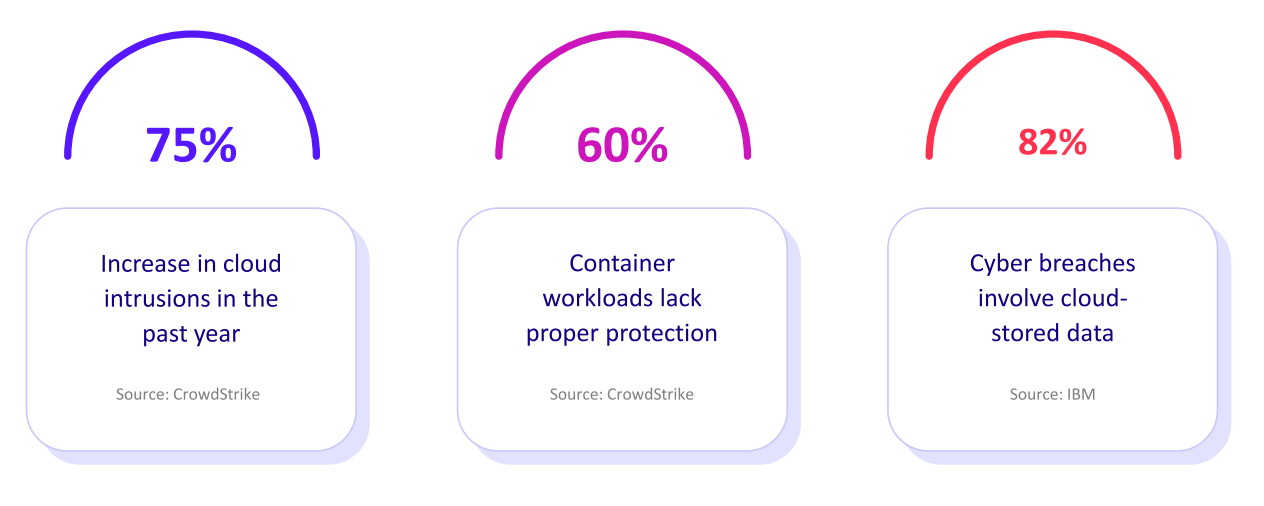
Misconfigurations, excessive permissions and blind spots in cloud setups are leading causes of data breaches. Traditional security tools weren’t built for this environment and the numbers prove it: cloud misconfigurations account for the vast majority of cloud incidents, with over 82% of breaches involving cloud-stored data.
That’s why cloud security posture management matters. It brings structure to cloud sprawl, helping security teams continuously detect, prioritize and fix risks before they’re exploited.
The biggest risks to cloud security include:
Keeping track of accounts and misconfigured access
Cloud environments depend heavily on Identity and Access Management (IAM). While IAM provides flexibility through fine-grained roles and policies, it often becomes overly complex. Many organizations accumulate unused or overly permissive accounts, leading to identity sprawl. This raises the risk of privilege misuse or accidental public access.
CSPM solutions help surface these issues by flagging misconfigured roles and unused admin rights, although deeper identity governance often falls under CIEM tools. Without continuous review, permissions can become a serious liability.
Constantly monitoring ephemeral infrastructure
Cloud resources are dynamic and short-lived. Servers, containers and services can spin up and vanish in minutes, making it nearly impossible for manual processes to maintain consistent security.
Traditional audits quickly become outdated. Cloud posture management addresses this by continuously monitoring the environment, ensuring even short-lived resources are assessed for misconfigurations. In cloud security, automation is essential because threats can appear and disappear faster than human teams can respond.
Dealing with Complicated Multi-Cloud and Hybrid Setups
Many organizations operate across multiple cloud providers, each with its own configuration standards and tooling. This makes unified visibility and policy enforcement difficult. Native tools often don't communicate across platforms, creating silos and blind spots.
CSPM solves this by providing a centralized view across AWS, Azure, GCP and more, applying consistent security checks and highlighting gaps in each environment. CSPM simplifies oversight in what is otherwise a fragmented and error-prone landscape.
Handling shadow IT and policy violations
Cloud agility allows teams to spin up resources independently, but this decentralization often leads to shadow IT and policy violations. Enforcing rules like mandatory encryption or restricted network access becomes difficult without central control.
CSPM cloud security acts as a safety net, catching misconfigurations regardless of how or where resources are created. It enforces security policy adherence across teams, reducing the chances of overlooked risks, even when teams bypass standard processes.
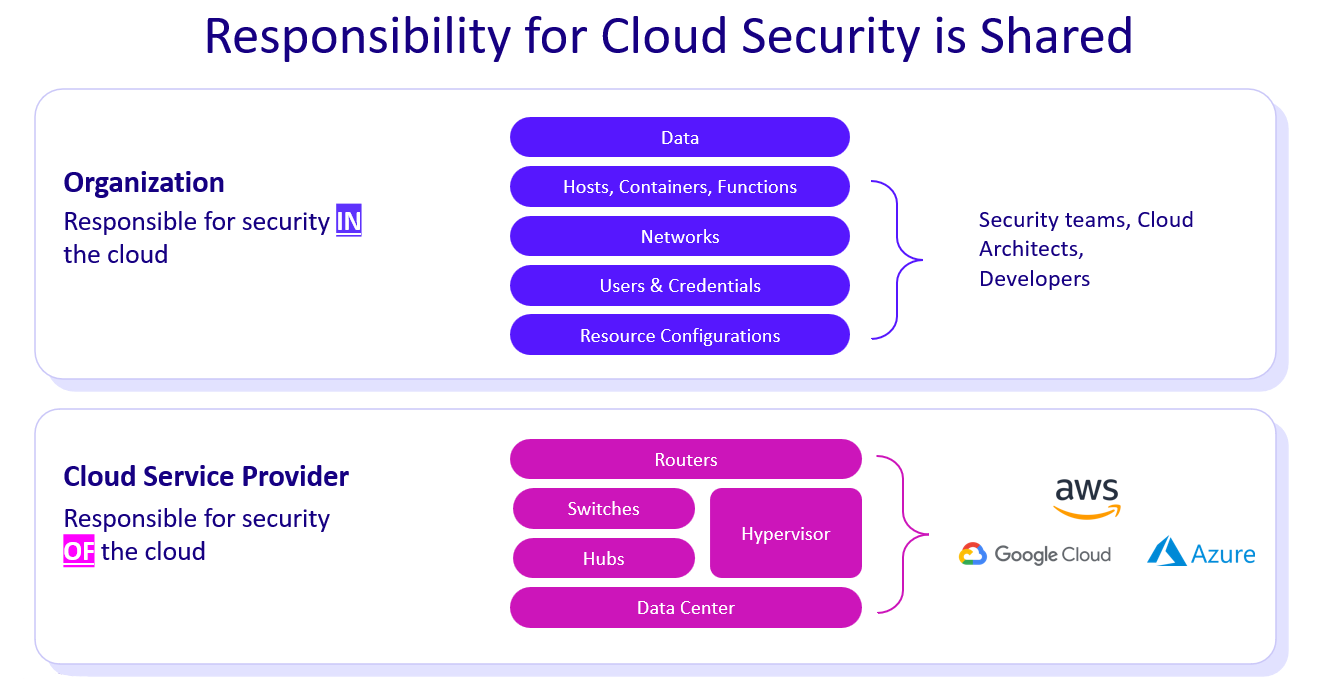
Managing the shared responsibility model
In the cloud, providers secure the infrastructure, but customers are responsible for securing their configurations, data and service usage.
Many breaches occur because this responsibility is misunderstood. CSPM reinforces this boundary by constantly monitoring what’s under the customer’s control, flagging default settings that haven’t been hardened.
What are the benefits of cloud security posture management?
Security posture management solutions in the cloud give organizations continuous oversight of their environments. It transforms complex, multi-provider infrastructures into manageable, measurable systems. By combining visibility, automation and compliance alignment, CSPM helps security and DevOps teams reduce breach risk, control costs and maintain confidence in their defenses.
Here are the main benefits:
- Visibility: Cloud security posture management tools continuously discover and inventory all cloud assets across providers, exposing hidden or misconfigured resources that create blind spots.
- Risk Reduction: Automated assessments flag and prioritize misconfigurations and policy violations that are most likely to cause breaches, enabling fast and targeted remediation.
- Compliance: Built-in mappings to frameworks such as CIS, NIST and GDPR let teams monitor adherence and generate audit-ready reports with minimal manual effort.
- Operational Efficiency: Centralized dashboards and automated workflows replace manual reviews and streamline collaboration between security and DevOps teams.
- Scalability: As environments expand, CSPM maintains consistent governance and protection across multiple accounts, regions and cloud services without added overhead.
How to prevent data breaches with CSPM
Small errors in how cloud resources are set up, like public storage buckets, open ports or permissive IAM roles, can lead to serious security gaps. These aren’t rare occurrences. According to the 2025 Verizon Data Breach Investigations Report, human error is involved in about 60% of all breaches, including mistakes like misconfiguration and incorrect access permissions.
Cloud posture security management helps reduce these gaps and prevent data breaches by addressing:
Compliance pressures in the cloud
CSPM isn’t just about avoiding breaches; it’s also about staying compliant. Cloud infrastructure must meet standards like GDPR, HIPAA and PCI DSS, along with frameworks such as CIS benchmarks.
A single oversight, like an exposed database, can break compliance, potentially triggering fines and reputation damage. Cloud security posture management solutions continuously scan for drift from these requirements, making it easier to catch and correct issues early, before they show up in an audit or cause a breach.
Visibility issues across cloud assets
Traditional data centers offered clear visibility. Cloud environments? Not so much. Assets are spread across multiple providers, accounts and services, making it difficult to see what’s running, where it’s located and who has access.
This lack of visibility is a severe liability. CSPM gives security teams a centralized, real-time view of their cloud footprint, closing blind spots and surfacing unknown risks. In short, it brings structure and insight to what can otherwise feel like a cloud-free-for-all.
Gaps that lead to losses
One misconfigured permission could lead to privilege escalation. One open bucket could lead to a breach. Cloud security posture management also plays a critical role in preventing costly incident responses. The average cost of a cloud-related breach is now $4.4 million, according to a 2025 report by IBM, and that doesn’t include the damage to customer trust.
By detecting vulnerabilities early, organizations can avoid worst-case scenarios. It's not just a security tool; it’s a safeguard against disruption and loss. Cloud complexity and human error go hand in hand. Without a solution in place, even a small mistake can lead to significant consequences.
By continuously auditing your cloud for misconfigurations, policy violations and compliance gaps, CSPM security acts as a critical early warning system. It helps organizations stay secure, compliant and in control even as their cloud environments evolve.
Key components of cloud security posture
Enterprise CSPM solutions typically offer a range of functions to improve your cloud security baseline. The key capabilities include:
Comprehensive visibility across cloud assets
One of cloud posture security management’s foundational functions is inventory and visibility. By connecting directly to your cloud accounts, CSPM automatically maps all assets, virtual machines, storage buckets, serverless functions, containers, databases and more.
This unified view helps security teams monitor their entire cloud footprint from a single dashboard. More importantly, it helps answer a critical question: What do we have running, and where are the risks?
Misconfiguration detection and alerts
Cloud posture management tools constantly scan your cloud environment for misconfigurations, like unencrypted databases, publicly exposed buckets or insecure network settings.
It compares configurations against best practices and policies, flagging anything that drifts from safe baselines. This type of exposure management acts as an automated safety net, alerting teams to the kind of configuration mistakes that are easy to miss but often lead to breaches.
Continuous compliance assurance
Maintaining compliance in the cloud is difficult due to the sheer pace of change. CSPM helps simplify this by evaluating cloud configurations against industry standards like CIS, NIST, ISO 27001, GDPR and more.
CSPM alerts teams when anything falls out of alignment and can even generate compliance reports on demand. This constant monitoring makes it easier to stay audit-ready and avoid regulatory penalties.
Smart risk prioritization
Not all misconfigurations are equally urgent. That’s why CSPM platforms include risk prioritization, ranking findings based on severity and potential business impact. Using scores and visualizations like posture ratings or attack path analysis, teams can quickly identify which issues need attention first.
This prevents alert overload and ensures critical risks are addressed before they can be exploited.
Remediation and automation
CSPM tools go beyond just detection; they help teams fix problems fast. Many offer remediation guidance and some support automated fixes for specific issues. For example, if a storage bucket is found open, the solution can suggest or even auto-apply a policy to secure it. Integration with Infrastructure-as-Code and CI/CD pipelines also enables tools to catch risky configurations before they impact your software supply chain.
Continuous monitoring and real-time alerts
At the heart of CSPM is continuous monitoring. These tools operate around the clock, tracking every configuration change or newly deployed resource.
As soon as something changes, your cloud posture management tool checks it for risk and sends alerts via dashboards, email, or integrations with SIEM/SOAR tools. This always-on vigilance means security teams can respond in real time, far faster than traditional manual audits.
How does cloud security posture management work?
Current CSPM solutions are generally agentless and API-driven, designed to integrate directly with cloud provider platforms. They monitor cloud environments to detect and fix misconfigurations before they can be exploited. It connects directly to provider APIs to deliver real-time visibility into resources, assess them against security and compliance benchmarks, and automate remediation where possible.
Here’s an overview of how CSPM typically works:
1. Connecting to cloud platforms
CSPM tools are agentless and typically connect to cloud environments via APIs. This setup requires read-only access through native roles or credentials, such as AWS IAM roles or Azure service principals. Since no agents are deployed on workloads, CSPMs operate through the cloud control plane, offering fast deployment with no performance impact on systems.
2. Asset discovery and inventory
After integration, the CSPM begins mapping out your cloud environment. It automatically discovers compute instances, containers, storage, databases, IAM settings and network configurations. This produces a live, centralized inventory that continuously updates with every change.
Visual diagrams often accompany the inventory, helping teams identify overlooked or unknown assets.
3. Configuration analysis
Once resources are inventoried, the CSPM evaluates their security posture. It compares current configurations against industry standards like CIS or NIST and any custom organizational policies. Misconfigured permissions, unencrypted databases, or open ports are flagged as violations. This analysis helps close the gap between your current state and a secure, compliant state.
4. Risk scoring and prioritization
CSPM does more than list issues. It assigns risk scores based on severity and context.
For instance, a publicly exposed database with sensitive data ranks higher than a misconfigured development instance. Advanced CSPMs may identify potential attack paths by correlating misconfigurations. The result is a prioritized list that helps teams focus on high-impact threats first.
5. Alerting and reporting
When issues are detected, CSPM platforms generate alerts and send them through multiple channels. Security teams can view them in dashboards, email, messaging tools like Slack or forward them to SIEM platforms. Reports summarizing security posture over time are also available, providing insights for compliance audits and executive review.
6. Remediation and automation
Beyond alerts, CSPM assists in resolving issues. Basic platforms may only display findings, while advanced ones provide remediation guidance or enable auto-remediation. For example, the tool might automatically restrict access to a public bucket. Integration with SOAR systems and CI/CD pipelines helps enforce policy during development and respond to security incidents quickly and consistently.
7. Continuous posture management
CSPM is built for continuous operation. It identifies trends, tracks recurring issues and helps teams measure progress over time. With ongoing scans and posture reports, organizations can refine policies, train specific teams and stay ahead of new risks. This cycle of detection, remediation and validation forms the foundation of cloud security hygiene.
CSPM tools and integrations explained
The CSPM ecosystem has expanded. Organizations now choose between native tools, third-party platforms, and open-source options.
| Type of tool | What it does | Examples |
| Cloud-Native CSPM Tools | Built by cloud providers for their own platforms. Offer posture management, compliance checks and risk alerts specific to that environment. Deeply integrated but limited to single-cloud visibility. | AWS Security Hub, Microsoft Defender for Cloud, Google Security Command Center |
| Third-Party CSPM Platforms | Provide unified visibility across multi-cloud environments with advanced analytics and broader rule coverage. Many are evolving into Cloud-Native Application Protection Platform (CNAPPs) by combining CSPM with workload and container security. | Orca Security, Wiz, Prisma Cloud, Trend Micro, Lacework |
| Open-Source CSPM Tools | Offer lightweight configuration scanning and policy enforcement. Useful for smaller environments or as supplemental tools but lack the depth and automation of enterprise-grade solutions. | ScoutSuite, Cloud Custodian |
When evaluating options, it’s important to look at deployment simplicity, rule coverage, integration capabilities and whether the CSPM fits into a broader cloud security strategy.
Integration capabilities to consider
A strong CSPM tool fits into the broader security ecosystem through integrations that streamline detection, investigation and remediation.
Keep the following in mind when evaluating cloud security management solutions:
- SIEM integrations allow CSPM alerts to be forwarded to platforms like Splunk, QRadar, or Azure Sentinel. This correlation with identity and network events helps security teams understand the full context of an issue.
- SOAR and ticketing integrations enable automation. A CSPM alert can trigger a playbook in Cortex XSOAR or create a ticket in ServiceNow or Jira, reducing manual workload and speeding up response times.
- DevOps and CI/CD pipelines benefit from CSPM capabilities during development. CSPMs can scan Infrastructure-as-Code templates before deployment, blocking insecure configurations from entering production. Dashboards can also be shared with DevOps teams for self-service remediation.
- Cloud-native workflow integration is invaluable for DevSecOps. CSPMs can work with services like AWS Lambda or Azure Functions for remediation and use real-time cloud events (like AWS CloudTrail) to detect changes as they happen. Alerts can be pushed to collaboration platforms like Slack or Microsoft Teams for faster response.
- Identity integrations are emerging as CSPMs begin to overlap with CIEM. Some tools can analyze IAM configurations and flag accounts with excessive or unused privileges, helping security teams catch misconfigured access settings that violate policy.
Limitations of relying on a CSPM platform alone
While CSPM is a vital component of security posture management in the cloud, it’s not a silver bullet. It’s important to understand what traditional CSPM tools cannot do, or where they need supplementation:
Visibility limited to the control plane
CSPM focuses on cloud configurations, not workloads. It monitors control plane data like resource settings and IAM policies, but doesn’t inspect the runtime layer, such as operating systems, containers or application code. This approach means tools won’t detect malware, software vulnerabilities, or leaked secrets inside VMs.
If an instance is compromised but still correctly configured, cloud posture management tools may miss it entirely. To close this gap, they must be complemented by Cloud Workload Protection Platforms (CWPP) and Cloud Detection and Response (CDR) tools.
Alert fatigue without prioritization
A basic CSPM may surface hundreds of alerts on day one, many of which lack risk context. Without proper tuning, teams can become overwhelmed by noise, especially when low-risk or intentional configurations are flagged as issues. This leads to alert fatigue and the potential to overlook real threats.
More advanced CSPMs address this by adding risk scoring, correlating alerts with workload and identity data, and visualizing exploit paths. Still, without customization and integration, traditional tools can struggle to separate signal from noise.
No real-time blocking or active defense
CSPM is primarily a detective control. It identifies and remediates misconfigurations, but it doesn’t block attacks in progress. For example, it might alert you that a database is exposed, but it won’t stop an attacker from accessing it before the fix is applied.
Tools lack real-time protection, inline traffic analysis or behavioral monitoring. For that, organizations must rely on tools like web application firewalls, IDS/IPS or runtime protection agents to actively prevent threats.
Incomplete IAM oversight
While CSPM can identify apparent IAM misconfigurations, like wildcard access, it lacks the depth needed to manage permission usage over time. It does not track how access is actually being used, nor can it enforce least privilege or rotate access credentials.
These responsibilities fall under Cloud Infrastructure Entitlement Management (CIEM). Without CIEM, excessive permissions and unused accounts may persist undetected, leaving an open path for insider threats or account misuse.
Compliance without real-world validation
Passing CSPM compliance checks doesn’t guarantee safety. Configurations may be secure, yet attackers can still exploit logic flaws in applications or steal credentials to gain access.
Relying solely on CSPM reports may create a false sense of security. Organizations must go beyond checklist-based compliance and validate defenses through simulated attacks, penetration testing or breach and attack simulation. These help test whether your environment can withstand real-world tactics, not just pass a scan.
Get better cloud posture management security validation with Cymulate
CSPM ensures your cloud is configured correctly, but it doesn’t prove whether those configurations actually stop real attacks. Cymulate’s Cloud Security Validation fills that gap by safely simulating real-world cloud threats to test if your defenses detect and respond effectively.
While CSPM finds misconfigurations, Cymulate tests resilience. It mimics tactics like:
- Privilege escalation using stolen credentials
- Data exfiltration from storage buckets
- Container escape and malware in cloud workloads
These simulations validate that tools like CloudTrail, SIEMs or WAFs are working as intended.
Cymulate complements CSPM by:
- Highlighting missed alerts or ineffective controls
- Prioritizing risks based on real-world exploitability
- Covering gaps CSPM can’t see, like runtime issues or failed detection rules
It also integrates with security operations, making remediation fast and actionable. Over time, it strengthens your cloud’s security posture by continuously validating, fixing and improving defenses.
CSPM helps you build a secure cloud, while Cymulate ensures it actually holds up under attack. Want to see our solution in action? Book a demo today.
Frequently asked questions
Cloud security posture management solutions improve an organization’s posture by continuously scanning configurations, permissions and compliance settings to detect misconfigurations and policy drift.
It prioritizes risks and automates remediation, giving organizations real-time visibility and control. This continuous monitoring strengthens resilience, ensures compliance and reduces exposure to breaches across multi-cloud environments.
Cloud security posture management (CSPM) secures cloud configurations, while cloud infrastructure entitlement management (CIEM) manages identity and access privileges. CSPM focuses on misconfigured assets and compliance and CIEM enforces least-privilege access by identifying unused or excessive permissions. Used together, they provide comprehensive protection across infrastructure, users, and services in cloud environments.
| Capabilities | CSPM | CIEM |
| Focus | Configuration and compliance | Identity and access control |
| Objective | Fix misconfigurations | Enforce least privilege |
| Scope | Assets and workloads | Users, roles, service accounts |
| Risk Coverage | Misconfigured or exposed resources | Privilege misuse, excessive permissions |
CSPM tools reduce breach risk by detecting exposed assets, insecure settings and excessive permissions before attackers exploit them. By correlating findings across configurations, identities and networks, it prioritizes critical vulnerabilities for fast remediation. This proactive approach limits exposure and strengthens defenses across complex cloud ecosystems.
CSPM forms the baseline of a multi-layered security strategy. It provides visibility, compliance assurance, and governance across all cloud resources, complementing tools like CWPP and CNAPP. With consistent baselines and automated checks, CSPM ensures other security layers operate within a secure, compliant framework.
Cymulate validates CSPM effectiveness by simulating real-world attacks to confirm that detected risks are truly mitigated. It tests cloud controls, configurations and policies against evolving threats. Together, Cymulate and CSPM turn posture management into continuous, measurable assurance of cloud resilience and breach prevention.