Cyber Risk Quantification
The Ultimate Guide to Cyber Risk Quantification: Measuring and Managing Cybersecurity Risks Effectively
Cyber risk quantification (CRQ) is the process of measuring and assigning numerical values to cybersecurity risks. It often translates technical risks into financial terms. This helps organizations understand how cyber threats could impact business operations.
CRQ helps organizations answer key questions about how much a cyberattack could cost, high-risk areas that could be vulnerable to attack and how much investment should be made in cybersecurity.
As cyber threats grow more complex, businesses need clear, actionable insights. CRQ turns vague risks into concrete numbers. That clarity leads to smarter strategies, better budgeting and stronger resilience.
Benefits of Cyber Risk Quantification
CRQ brings real value to organizations by turning cybersecurity into a business conversation, helping teams move from guesswork to clear, data-backed decisions:
- Financial insight: CRQ shows the potential financial impact of cyber threats. Instead of vague risk scores, it provides dollar-value estimates. This helps leaders understand the true cost of a breach or incident, allocate budgets more effectively and prioritize resources where they matter most.
- Enhanced decision-making: CRQ gives your organization clear, data-driven insights to make faster, smarter decisions. You can compare the cost of a risk to the cost of fixing it, helping avoid waste or being unprotected from specific kinds of attacks or breaches. It also helps justify security investments with real numbers and guides whether to accept, reduce or transfer risk—leading to more efficient risk management.
- Regulatory compliance: CRQ helps prove you’re managing cyber risks responsibly. It shows due diligence, replaces vague assessments with measurable data and supports audit and reporting needs. With clear metrics, it’s easier to meet compliance requirements and demonstrate control.
- Stakeholder communication: Executives and boards care about business risk—not technical jargon. CRQ translates cybersecurity into business language. This helps build trust with non-technical stakeholders, get buy-in for security initiatives and align cybersecurity with strategic goals.
How to Quantify Cyber Risk
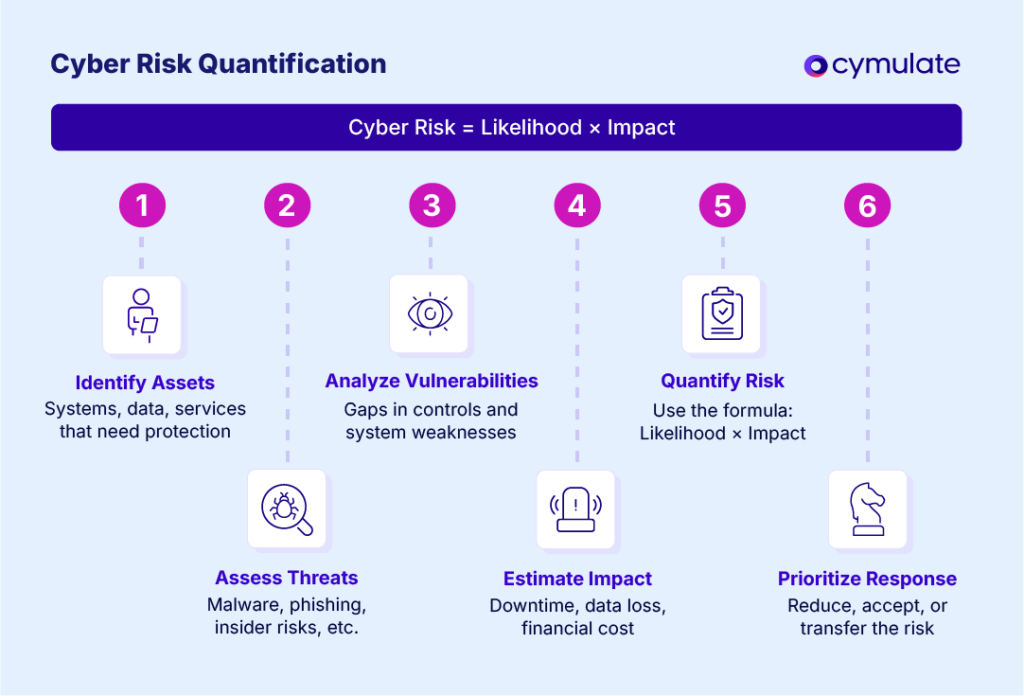
Quantifying cyber risk means calculating the potential financial impact of a cyber event. Here is how to measure cyber risk:
Cyber risk = Likelihood × Impact
This simple equation helps estimate how much a specific cyber threat could cost your business over time. To use it effectively, follow these key steps:
- Asset identification: Start by identifying what you’re protecting. Catalog your critical assets—these could be systems, data, applications, or services. Assign each asset a business value. Your organization needs to consider the following questions:
How important is this asset to operations?
What would it cost to lose or restore it? - Threat assessment: Next, identify the threats that could target these assets. Common threats include malware, phishing, insider threats or system failures. For each one, estimate how likely it is to happen and consider how often it occurs in your industry.
- Vulnerability analysis: Now, assess how exposed your assets are. Look for weaknesses in systems, software or processes. Use tools like Cymulate for vulnerability scanning or audit reports—the more vulnerable an asset, the higher the chance a threat will succeed.
- Impact analysis: Finally, conduct an impact analysis on the consequences. Focus on the financial impact—downtime, data loss, recovery costs, fines and reputational damage. Estimate both direct and indirect losses.
By combining these steps, you get a clear, data-driven view of your cyber risks. It turns security into measurable business risk—making it easier to prioritize and act.
Methodologies and Frameworks
To quantify cyber risk effectively, you need structured methods. Several proven frameworks can guide your process. Each offers tools to measure risk in a practical, business-focused way.
FAIR framework (factor analysis of information risk)
FAIR is one of the most widely used models for cyber risk quantification. It breaks risk into measurable components and focuses on the financial impact of cyber risk.
With FAIR, you assess:
- The probable frequency of a threat event.
- The likely loss magnitude if it happens.
This helps you answer: How much could this risk cost us? FAIR is ideal for organizations that want a repeatable, data-driven approach to cyber risk.
NIST Cybersecurity Framework
Developed by the National Institute of Standards and Technology (NIST), this framework provides guidelines for identifying, assessing, and managing cyber risk.
NIST focuses on five core functions:
- Identify
- Protect
- Detect
- Respond
- Recover
While not strictly a quantification model, the NIST cybersecurity framework helps you build a strong foundation for a cybersecurity risk assessment. It aligns well with regulatory standards and supports risk-informed decisions.
Monte Carlo simulations
Monte Carlo simulations use probability to model thousands of possible threat scenarios. In cyber risk, they help make uncertainty more manageable. They show how different attacks could play out and estimate financial losses and risk levels more accurately.
This method validates your assumptions and gives a clearer, more reliable view of your exposure—making CRQ results more accurate and useful.
Challenges in Implementing CRQ
While CRQ offers clear benefits, implementing it can be challenging. Understanding these hurdles helps teams plan better and avoid common pitfalls.
Data quality
CRQ needs accurate, complete data to deliver useful results. Without it, risk estimates can be off. Common issues include outdated asset inventories, missing incident data and unreliable threat or loss estimates based on assumptions.
Fix this by improving data collection and security control validation. Keep inventories current, log incidents regularly and use real-world data where possible.
Better data means better risk insights—and smarter decisions.
Resource intensity
CRQ takes time, tools, and skilled people. You’ll need experts who understand both cybersecurity and business risk, time to gather data, run models and review results and budget for tools or external support, if needed.
Smaller teams may need to scale efforts or take a phased approach.
Complexity
Modeling cyber risks isn’t always straightforward. Challenges include estimating likelihoods with limited data, translating technical risks into financial terms and choosing the right frameworks and methods.
Start simple. Focus on high-impact risks first, then expand.
Despite these challenges, CRQ is worth the effort. With the right planning and tools, it becomes a powerful asset for managing cyber risk.
Best Practices for Effective Cyber Risk Quantification
To get the most value from cyber risk quantification, it’s important to follow a few best practices. These steps help ensure your results are accurate, relevant and useful for decision-making.
Cross-functional collaboration
Cyber risk is a business issue, not just an IT problem. Managing cyber risk well takes teamwork.
You’ll be best served on this journey by starting with IT and cybersecurity for technical insights. Then, add finance to assign real dollar values to risks. Include cyber risk management to apply structure and proven frameworks. Finally, bring in legal and compliance when regulations are involved.
Each team offers a unique view. Together, they create stronger, more informed decisions.
Continuous monitoring
Cyber risk changes quickly. New threats, systems and business shifts can all impact your risk profile. That’s why cyber risk quantification shouldn’t be a one-time effort.
Make CRQ a living process. Keep it current so it stays useful for decisions. Regularly update your data and assumptions, review the latest threat intelligence and refresh your models based on recent events.
This keeps your analysis relevant, accurate and ready when you need it.
Standardized metrics
Use consistent metrics and terms across teams to avoid confusion. This keeps everyone—IT, finance, and leadership—on the same page. For example, use Annualized Loss Expectancy (ALE) to show financial impact. Clearly define terms like threat event frequency, including how you calculate them. Standardized metrics improve communication, reporting and decision-making. This will make it easier to compare risks and align your teams.
Scenario analysis
Go beyond the numbers. Create realistic scenarios to model potential attacks. Ask questions such as: “What if ransomware hits our core systems?” and “What’s the impact of a major data breach?” Scenario planning helps you prepare, prioritize and respond more effectively.
Future Trends in Cyber Risk Quantification
CRQ is evolving fast. As threats grow more complex, organizations need smarter, faster ways to assess and manage risk. Two key trends are shaping the future of CRQ are automation with AI and integration into enterprise risk management.
Automation and AI
Manual risk assessments take time and often rely on assumptions. Automation and artificial intelligence are changing that.
AI-powered tools like Cymulate AI Copilot can:
- Analyze large volumes of threat and incident data
- Spot patterns and predict future risks
- Generate real-time risk scores based on live inputs
Automation speeds up data collection and model updates. It also reduces human error and helps teams scale CRQ without extra workload. As cyber risk quantification tools improve, CRQ will become more accurate, efficient and provide real-time benefits.
Integration with enterprise risk management (ERM)
Cyber risk is no longer separate from other business risks. It affects operations, finance, reputation, and compliance. Leading organizations are embedding CRQ into their broader ERM programs.
This shift allows companies to:
- View cyber risk alongside financial, operational, and strategic risks.
- Align risk responses across the business.
- Report to executives and boards in a unified, consistent way.
CRQ becomes a key part of business planning—not just a cybersecurity task.
The Cymulate Approach to Cyber Risk Quantification
Cymulate helps organizations improve cyber risk quantification by using real-world data instead of guesswork. It identifies gaps, simulates attacks, and shows exactly where to focus your security efforts.
Here’s how Cymulate boosts CRQ:
- Continuous exposure management: Cymulate runs ongoing tests across your environment—email, endpoint, network and more. This shows what’s exposed and helps estimate the likelihood of an attack.
- Automated attack simulations: Simulate real threats like ransomware or phishing. See how they spread and what impact they could have. Use these results to feed directly into your CRQ model.
- Actionable remediation insights: Get clear, prioritized recommendations based on real exposures. Focus on the highest risks, assign financial impact and track how fixes reduce your overall risk.
By combining continuous testing, real-world attack simulations and clear remediation priorities, Cymulate gives you a more accurate and useful view of your cyber risk.
It helps you measure, manage, and reduce risk—fast.
Key Takeaways
Cyber risk quantification gives organizations a smarter way to understand and manage cybersecurity. Instead of vague scores, CRQ puts risks into financial terms. This makes it easier to prioritize, plan and communicate with stakeholders. This translates into the following key outcomes:
- CRQ turns cybersecurity into a business tool. Measuring risk in dollars helps teams make smarter, aligned decisions.
- Traditional CRQ often relies on estimates, which can miss the mark in fast-changing threat environments.
- Cymulate improves this by using real-world data. The platform runs automated attack simulations and continuous testing to show actual exposures.
To get the most from CRQ:
- Automate simulations to find weaknesses early.
- Continuously test security controls.
- Prioritize fixes based on real, measurable risk.
By combining traditional frameworks with real-time validation tools like Cymulate, companies can build a more accurate and actionable view of cyber risk.
The result? Better protection, smarter spending and stronger alignment between cybersecurity and the business.

