Exposure Validation
Critical Reasons Why Exposure Validation Matters
Exposure validation is a vital component in any cybersecurity strategy to help ensure the protection of sensitive information and maintenance of a strong security posture. The ability to understand and validate an exposure to cyber threats positions an organization to be able to make informed decision, enhance their compliance and ultimately safeguard their assets and reputation.
Here are some ways in which exposure validation can be a major asset to a cybersecurity strategy:
- Risk Assessment – Identifying vulnerabilities early through exposure validation helps organizations assess their weaknesses and potential attack surfaces before a threat actor can exploit them. Doing this allows for informed decision-making throughout the security organization and allocation of proper resources.
- Compliance and Regulatory Requirements – Meeting industry regulatory requirements for data protection (i.e., GDPR, HIPAA) measures ensures that sensitive information is secured as well as organizations can avoid costly fines, legal and reputational repercussions.
- Enhancing Security Posture – With real-time monitoring and continuous improvement, organizations can quickly adapt and respond to evolving threats.
- Building Trust – Organizations that prioritize exposure validation and can demonstrate robust cybersecurity practices can easily build trust with customers, partners and stakeholders, which is a vital part of maintaining business relationships and reputation.
- Cost-Effectiveness - Being able to allocate resources more efficiently means organizations can identify where to invest in cybersecurity measures more effectively, leading to long-term cost savings.

How does Exposure Validation work?
Exposure validation involves several systematic steps to help ensure that exposure data is accurate, reliable and relevant. Below are the eight defined steps:
Step 1: Define the Objectives
Determine why exposure validation is needed, for example, regulatory compliance, health or financial risk assessment is the first step. Then clarify what type of exposure is being assessed (what industry).
Step 2: Develop a Validation Plan
Select the appropriate methods for data collection and validation, whether that be direct measurement, modeling or statistical analysis. Define the set criteria for validation, such as acceptable levels of accuracy, precision and completeness.
Step 3: Collect Exposure Data
Gather data and use selected methods to collect exposure data. This could involve sampling, including air, water or biological samples, surveys or existing databases. An important part of this step is ensuring quality control by implementing quality control measures during data collection to minimize errors and biases.
Step 4: Analyze the Data
It’s crucial for data processing to be kept clean and organized for the purposes of collecting data for analysis, removing any anomalies or irrelevant data points. Applying statistical analysis methods to assess data reliability, variability and distribution could include calculating confidence intervals, performing regression analysis or conducting sensitivity analysis.
Step 5: Compare with Standards or Benchmarks
By referencing data points, you can compare the collected exposure data against established benchmarks, guidelines or regulatory standards relevant to the context. During this comparison stage, you can identify discrepancies and note any significant differences between the collected data and reference values and assess their implications.
Step 6: Review and Validate
During the review and validate step, use peer reviews involving field experts to review the methodology, data collection and analysis for credibility. If discrepancies are found, conduct a reassessment or consider re-evaluating the data collection methods or repeating measurements to improve accuracy.
Step 7: Document Findings
In preparation to report results, a comprehensive report detailing the methods used, findings, comparisons with standards and any limitations should be represented. It’s important to be fully transparent in the documentation of the validation process to help ensure visibility and reproducibility for future assessments.
Step 8: Implement Findings
Apply validated exposure data to make data-informed decisions, whether they involve regulatory actions, public health interventions or financial or security strategies. Feedback is key to improvements and monitoring – incorporate findings into ongoing validation and monitoring processes to continually improve data accuracy and relevance.
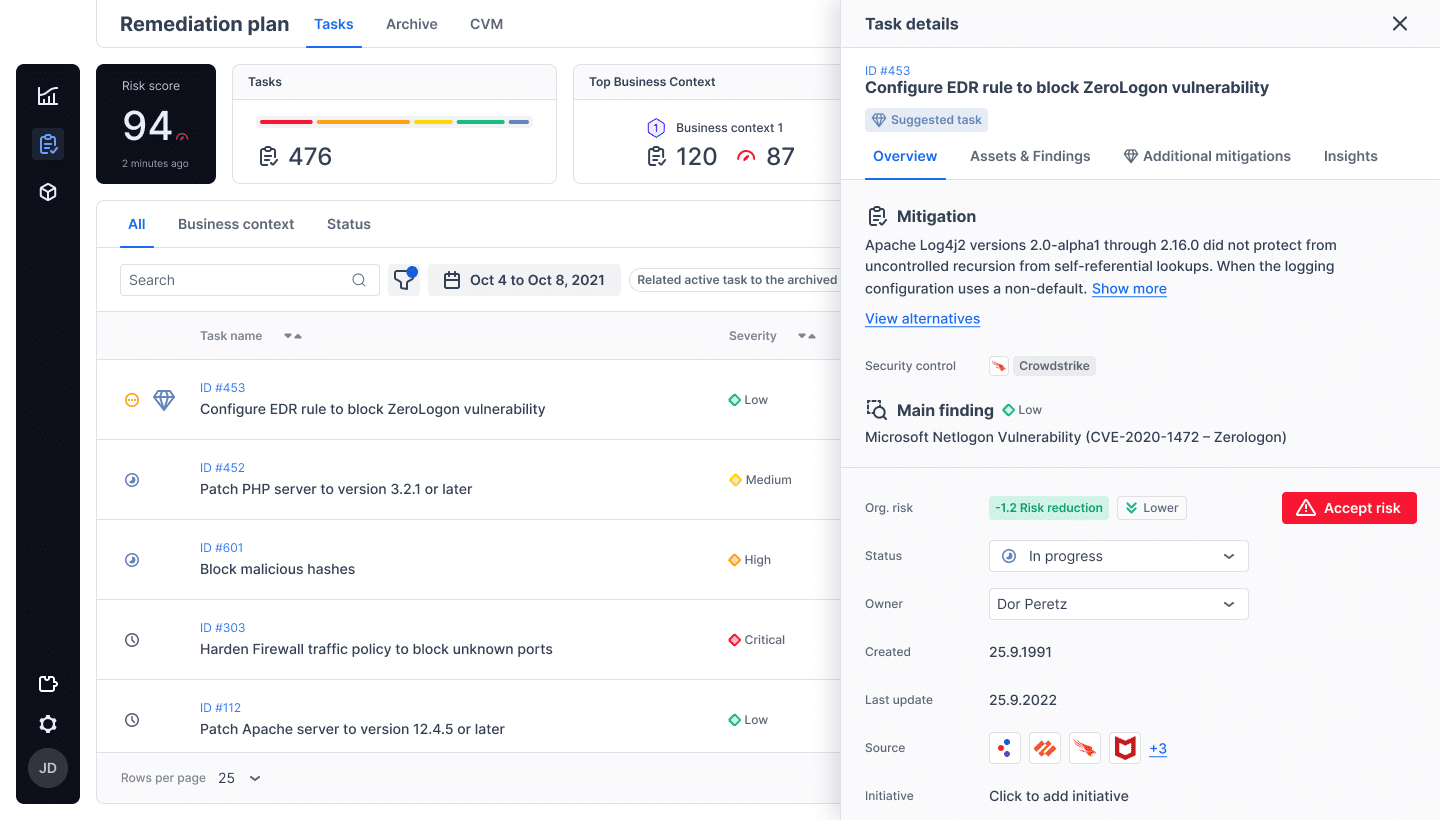
How Cymulate Does Exposure Validation
To strengthen your defenses against the riskiest exposures and threats, validation is the best prevention with continuous attack simulation. Through a simulation platform, Cymulate can automatically test and validate the security controls across an entire IT environment to expose risky threats, dangerous attack paths and unknown gaps. And then tell you how to fix them before the impacts of a breach occur.
Key Takeaways
Exposure validation is a fundamental aspect of decision-making in various fields, ensuring that the data guiding our actions is trustworthy and robust. Whether we’re protecting public health, ensuring workplace safety, or managing financial risks, the importance of accurate exposure data cannot be overstated. By investing in thorough validation processes, we can make informed decisions that safeguard our health, environment, and economic stability.
Understanding and implementing exposure validation is essential for creating a safer and more sustainable future. So, the next time you hear about exposure data in any context, remember the critical role that validation plays in shaping our responses and policies.