Security Posture Assessment
Every year, thousands of organizations fall victim to cyber attacks. Why? Often, it's due to vulnerabilities that, if caught early, could have been easily patched or prevented. A security posture assessment can help find these vulnerabilities, allowing you to take action before they become a serious problem.
What is Cyber Security Posture?
Security posture describes an organization’s ability to defend against and respond to cyber threats. It's a snapshot of a company's overall state of cybersecurity readiness, and includes having clear policies, the right technology, and fast response plans.
Having a strong security posture is now more important than ever. In 2024, the average data breach cost hit $4.88 million, the highest totalt ever. What's more, it now takes an average of 194 days to find a breach. During these almost 200 days, threat actors harvest data and wreak havoc on systems.
What is a Security Posture Assessment?
A cyber security posture assessment evaluates an organization’s security strategies, policies, and controls to identify vulnerabilities and gaps in its defenses.
In short, the goal of a security posture assessment is to provide a comprehensive understanding of an organization's security health. This includes identifying vulnerabilities, assessing risks and recommending improvements to enhance cyber resilience and protect against potential threats.
The assessment may reveal a well-established security posture that requires only minor adjustments or expose critical gaps and high-risk vulnerabilities that demand immediate attention. Either way, by identifying vulnerabilities and understanding your risks, you can take proactive steps to protect your assets.
We only have to look to recent history for a real-world example of how having outdated software can have dire consequences. The WannaCry ransomware attack infected hundreds of thousands of computers in over 150 countries, estimated to have cost nearly $4 billion in damages. This malware exploited a known vulnerability that Microsoft had already patched. In other words, this attack was only made possible because users were running older, unsupported software.
How a Security Posture Assessments Work
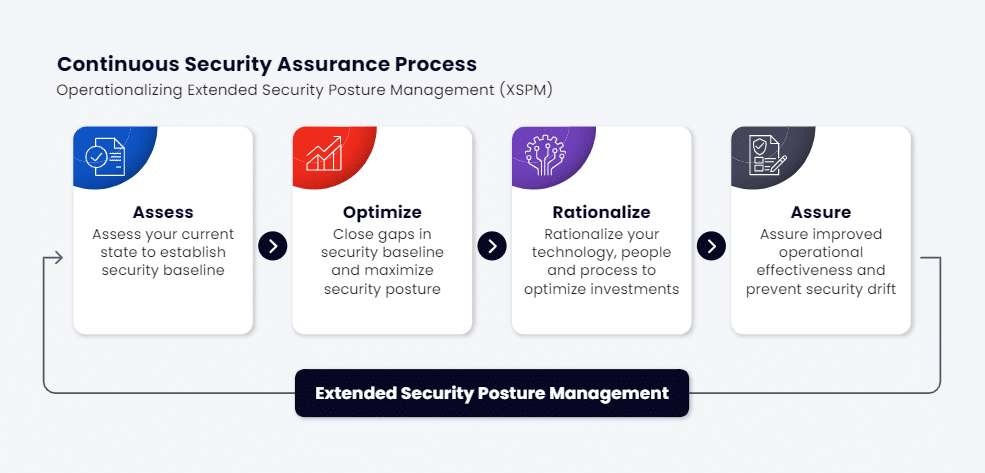
Security posture assessments typically involve four key steps: risk assessment, optimization, rationalization and assurance.
In risk evaluation, the organization’s assets and potential threats are analyzed. This step is critical for many reasons, but one of the most significant ones is shadow IT - the term for IT assets that the IT team doesn't know about. According to one study, 42% of the average company's applications fall under shadow IT. And research by Gartner found that shadow IT accounts for 30 to 40% of IT spending[4]. You can't defend what you can't see.
Next, vulnerabilities are identified through testing, scanning and reviewing security controls, looking for weaknesses in systems, networks, and policies. This step looks at all possible ways an organization may be breached.
Once vulnerabilities are identified, the assessment concludes with remediation recommendations, providing steps to strengthen defenses and mitigate risks.
For example, an assessment might reveal outdated software and unpatched systems. The recommended fix could include patching the software, updating firewalls, and implementing stronger access controls.
Why Security Posture Assessments Are Essential
Security posture assessments are essential because they reduce the risk of attackers infiltrating your system and vastly reduce the potential damage in the case of a successful attack. This is especially critical in an environment where cyber threats are rapidly evolving and compliance requirements are stringent. The consequences of a successful attack or a compliance breach can be significant.
To get more into the details, continuous security assessment is more vital than ever before. Today, organizations manage hundreds or even thousands of assets, leading to a significantly expanded attack surface—the various ways attackers can exploit systems and data. Attackers have more entry routes into systems, more unique exploitation methods, and can often go undetected for long periods.
At the same time, attack methods advance so quickly that updating policies and educating employees on security best practices can be difficult. Adding to this complexity is the sheer number of cybersecurity frameworks like MITRE Att&ck Framework, NIST, OWASP and ISO 27001.
Methods
There are several approaches to conducting a security posture assessment, each with its own strengths and weaknesses.
Manual Assessments
Manual assessments rely on humans to do the work. These assessments typically involve:
Interviews with key personnel can gauge understanding of security protocols and identify potential gaps. Interviews can help determine both the security posture and how well-understood the security policies are across the organization. For example, do employees know what to do if they receive a suspicious email?
- Policy reviews ensure alignment with industry best practices and legal requirements.
- Audits determine whether security policies are being implemented, and how effectively.
- While highly customized, manual assessments can be time-consuming and require significant resources.
Automated Tools
Automated cybersecurity posture assessment tools use software to scan for vulnerabilities and misconfigurations. They can identify outdated software, unpatched systems, weak encryption, or improper access control. For example, they might find that an employee who works in human resources has administrative access to the company's financial systems. This could allow employees to access sensitive financial data or manipulate payroll records.
Automated tools can also generate reports highlighting risks and suggesting fixes. Moreover, some tools are especially powerful, allowing continuous monitoring for proactive threat detection. For instance, they may detect unusual patterns of network traffic or login attempts that may indicate a potential attack. This allows organizations to respond quickly to threats before they can cause significant damage.
Breach and Attack Simulation
Breach and attack simulations test an organization's defenses against real-world cyber attacks. These tools simulate specific attack scenarios like phishing, malware, DDoS attacks, and more. The goal is to Identify weaknesses in defenses, incident response protocols, and strategies through hands-on testing.
Security Posture Assessment vs. Penetration Testing
A security posture assessment provides a holistic view of the organization’s overall cybersecurity health and readiness. In contrast, penetration testing is a point-in-time assessment focused on simulating specific attacks to find vulnerabilities in particular systems or networks.
While penetration testing offers deep insights into specific weaknesses, it is narrower in scope and does not provide the continuous, broader evaluation that a security posture assessment does. Both are important but serve different roles in maintaining cybersecurity.
Key Components of a Strong Security Posture
Strong cybersecurity posture has many key tenets:
Clear and Updated Security Policies
Policies guide access to systems, data, and security measures. Regular updates ensure policies remain relevant to evolving threats.
Robust Technical Controls
- Use controls such as firewalls, intrusion detection and prevention systems (IDS/IPS), and encryption to protect systems and data from attacks.
- Implement network segmentation to isolate assets and limit the potential damage of breaches.
Effective employee training
- Equip staff to recognize phishing, social engineering and other threats, reducing the risk of human error. According to a joint research by Stanford University and Tessian, 88% of data breaches are caused by an employee mistakes.
- Regular training ensures employees can recognize and respond to threats like phishing and social engineering attacks.
Zero-Trust Model
- Adopt a Zero-Trust Model where no user or device is automatically trusted, wether inside or outside the network. Every point of access should require strict verification and authorization.
Enhanced Threat Detection and Response
- Strengthen detection and response capabilities by using SIEM solutions to centralize security data and identify suspicious activity in real time.
- Maintain a comprehensive incident response plan to minimize damage and support fast recovery from breaches.
Patch Management and Automation
- Regularly update and patch systems to close security gaps and prevent vulnerabilities from being exploited.
- Invest in automation tools for continuous monitoring and real-time threat detection, ensuring prompt management of vulnerabilities.
Challenges and Common Gaps
Some security gaps are more common than others. For example, weaknesses like outdated software, insufficient staff training, and inadequate visibility across their networks are common.
Unpatched software creates vulnerabilities that attackers can exploit, while untrained employees may fall victim to phishing or other social engineering tactics. Limited visibility into network activity can make it difficult to detect breaches early, which is exactly why it takes an average of 194 to detect a breach.
These gaps can be easily filled with continuous monitoring, regular software updates, and ongoing employee training. The key is being proactive. Without a proactive approach, organizations risk falling behind on evolving threats, leaving them vulnerable to cyber attacks that could have been prevented.
How Cymulate Plays a Role in Security Posture Assessment
By leveraging breach and attack simulation, automated red teaming, and security control validation, Cymulate provides organizations with real-time insights into their security posture. This enables you to proactively identify and prioritize vulnerabilities, measure your resilience, and prioritize closing the gaps to significantly enhance your overall security posture.
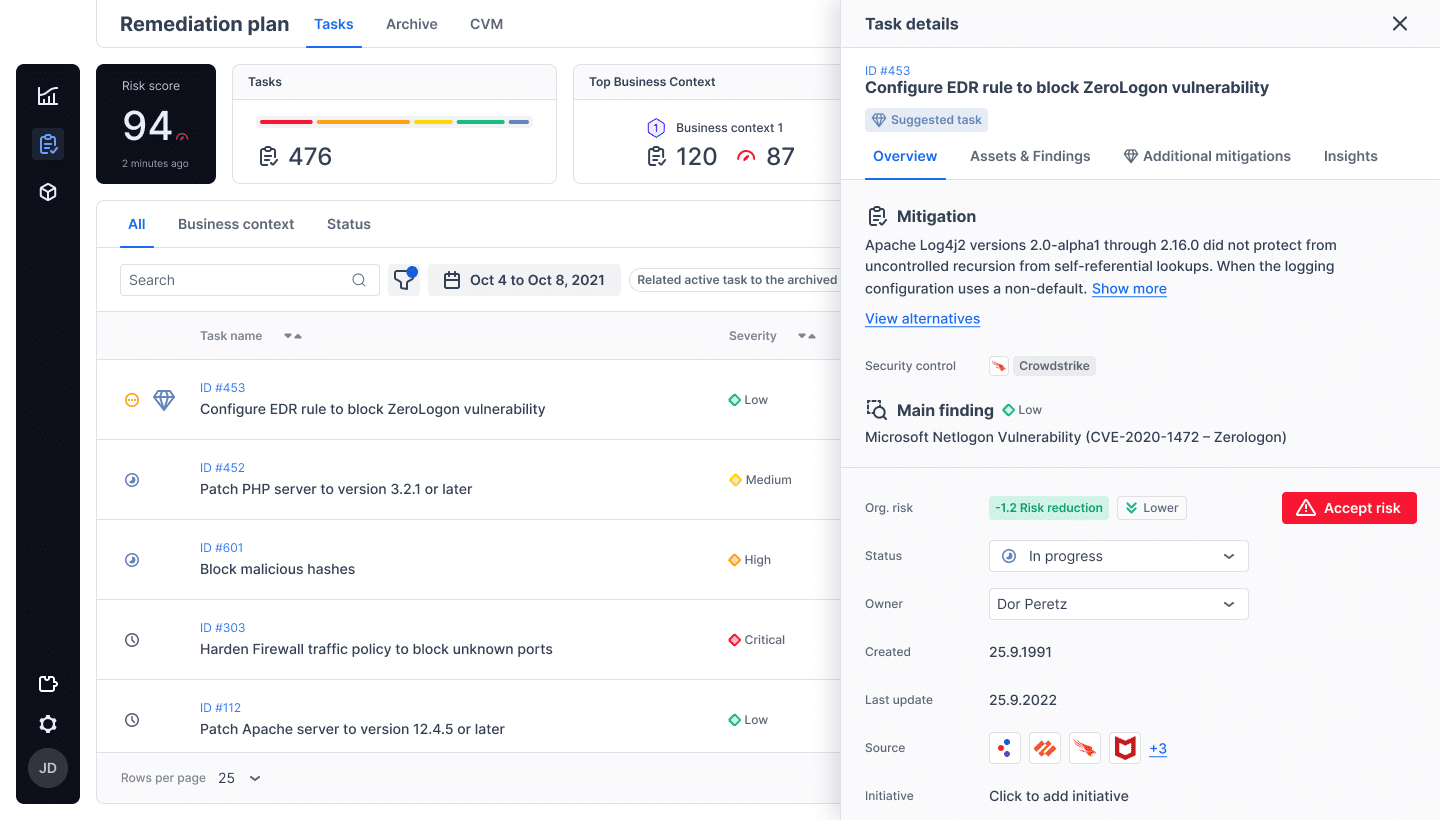
Amid increasing ransomware attacks, a strong, continuously monitored security posture is essential for maintaining a solid security posture. The Cymulate platform offers a comprehensive solution for real-time security posture assessment, empowering you with the information and tools you need to safeguard your systems. By leveraging Cymulate, you can take control of your security journey and ensure you are well-equipped to face the challenges of the future.
