Third-Party Risk Management (TPRM)
Third-Party Risk Management (TPRM): Strategies, Tools, and Best Practices
Third-party risk management (TPRM) is becoming a top priority in today’s cloud-driven business ecosystems. Organizations rely on countless software-as-a-service (SaaS) providers, cloud platforms and external vendors – expanding the cyber attack surface far beyond the traditional network perimeter.
This interconnected environment brings great agility but also significant cyber risk from vendors. Recent data shows 41% of companies that suffered a major security incident in 2023 attributed it to a third-party cause. High-profile supply chain attacks like SolarWinds and MOVEit underscore how a single compromised vendor can impact risk exposure for hundreds of downstream organizations.
Amid these trends, robust third-party risk management is essential. TPRM is the practice of identifying and mitigating risks stemming from external business partners, suppliers, service providers and other third parties.
A TPRM program helps organizations ensure that vendors maintain strong security controls, comply with regulations and don’t inadvertently introduce vulnerabilities into the business.
What Is Third-Party Risk Management?
Third-party risk management is the process of an organization’s identification, assessment, and control of risks that arise from working with external entities – including vendors, partners, suppliers, contractors or service providers.
In other words, it extends your internal risk management practices to cover the entire vendor ecosystem and supply chain. TPRM is sometimes used interchangeably with terms like vendor risk management or supply chain risk management, reflecting its broad scope.
A formal third-party risk management framework provides increased visibility into potential threats from outside parties to help reduce risk and prevent security incidents. This involves establishing policies and procedures to evaluate third parties at every stage - from initial due diligence and vendor onboarding, through ongoing monitoring and eventual offboarding.
TPRM includes more than cybersecurity alone; it also considers any vulnerabilities that could harm the organization, such as legal compliance gaps, operational failures or reputational damage.
Objectives of Third-Party Risk Management
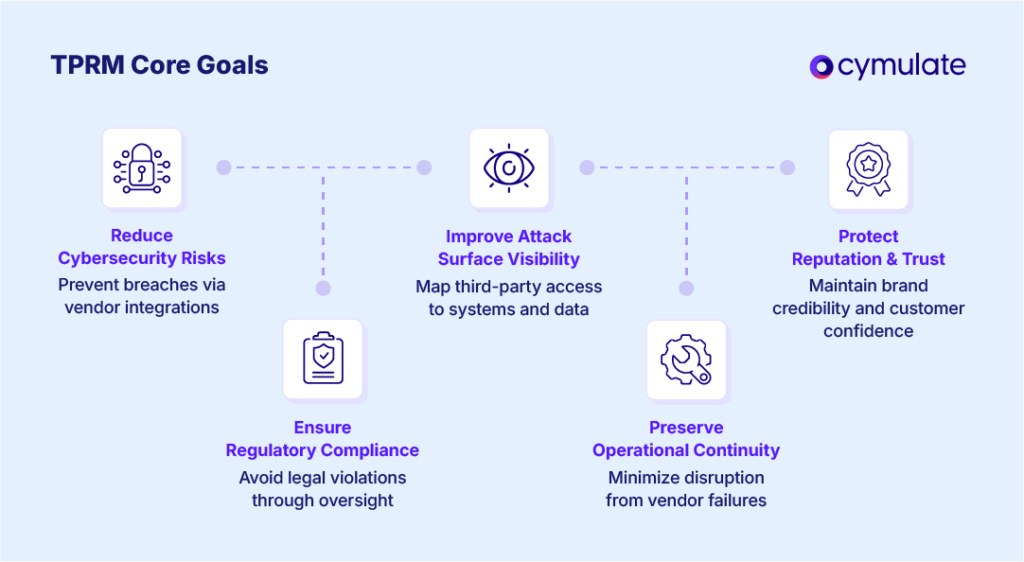
A robust TPRM program pursues several core goals to protect the organization’s interests. Key objectives of third-party risk management include:
- Reducing cybersecurity risks from vendors: Minimizing the likelihood of breaches, malware infections, or unauthorized access via third-party systems and integrations. This includes plugging security gaps that attackers could exploit in the supply chain.
- Ensuring regulatory compliance: Verifying that third parties handle data and processes in compliance with laws, standards, and industry regulations. Effective TPRM helps avoid violations (e.g. privacy breaches or data handling non-compliance) that could result in legal penalties.
- Improving attack surface visibility: Gaining a clear view of the organization’s extended attack surface by mapping all vendors, connections and data flows. This visibility helps identify vulnerable points introduced by third parties and improves overall risk assessment of the supply chain.
- Safeguarding operational continuity: Reducing the chance that a vendor issue disrupts business operations. TPRM aims to prevent scenarios like critical service outages or supply chain failures by evaluating vendors’ resiliency and contingency plans.
- Protecting reputation and customer trust: Avoiding negative publicity or loss of trust stemming from third-party incidents. By managing vendor risks, organizations can prevent headline-grabbing breaches or compliance failures that would damage their brand image.
Third-party risk management seeks to reduce risk exposure, ensure business continuity and enforce accountability across all external relationships. It gives security and risk teams greater control over factors outside the organization’s direct boundaries.
Core Risk Categories in Third-Party Relationships
Working with third parties introduces a variety of risk types. A comprehensive TPRM program considers and addresses multiple categories of vendor-related risk, often overlapping, including:
Cybersecurity risk
The danger of cyber attacks or data breaches originating from a vendor’s systems or services. This is exemplified by supply chain attacks such as the SolarWinds breach, where attackers inserted malware into a third-party software update - compromising thousands of organizations including U.S. government agencies.
Similarly, the 2023 MOVEit file transfer hack exploited a vulnerability in a widely used third-party platform, affecting dozens of companies (British Airways, BBC, and more) and exposing millions of individuals’ data. These incidents show how a security weakness at one vendor can cascade into a major breach for its clients.
Compliance and legal risk
Third-party actions that lead to regulatory violations or legal liabilities for your organization. For example, if a vendor fails to meet data protection laws or contractual security requirements, the company could face fines or lawsuits.
A lack of vendor security controls might result in non-compliance with standards like GDPR, HIPAA or industry-specific regulations, placing the business in legal jeopardy.
Operational risk
A vendor failure could disrupt your business operations or supply chain. This could arise if a critical supplier has an outage, a cloud service provider goes down, or a vendor lacks adequate disaster recovery.
Operational risk also covers scenarios like a third party’s poor processes or staffing issues causing service delays. If an outside provider can’t deliver as expected, it may halt your dependent processes.
Reputational risk
Damage to your organization’s reputation stemming from a third party’s actions or incidents. A breach at a vendor that handles your customer data, for instance, can generate negative public opinion and erode trust in your brand. Similarly, if a vendor engages in unethical practices or suffers a highly public outage, the association can tarnish your image. Because stakeholders often blame the primary company for its vendors’ failures, reputational harm can be a severe fallout.
Each of these risk types is important to manage. Often a single incident will span multiple categories – for example, a vendor data breach can create cybersecurity, compliance, operational and reputational impacts all at once. TPRM therefore takes a holistic approach to evaluate how third-party relationships could threaten the organization across various dimensions.
Critical Threat Signals in Your Vendor Ecosystem
Effective third-party risk management requires recognizing warning signs and risk indicators early. Security and risk teams should be vigilant about common red flags in vendor relationships, such as:
- Poor vendor security hygiene: Indicators that a vendor lacks strong security controls or policies – for example, no recent penetration tests, absent certifications (like SOC 2), delayed patching practices, or a history of frequent incidents. If a vendor cannot demonstrate a mature security program, they present higher risk.
- Shadow IT and unsanctioned tools: The use of third-party apps or cloud services outside of the organization’s approved procurement process. Shadow IT can introduce unknown SaaS vendors handling sensitive data without oversight, bypassing security vetting. This makes it hard to gauge risk and ensure consistent protections. Unvetted integrations or plugins also fall into this category of hidden risk.
- High-risk integrations and privileged access: Third parties that have deep access into your systems or data pose greater risk if compromised. Watch out for vendors integrated into core workflows (finance systems, HR data, etc.) or those with VPN access into your network. These connections increase the potential blast radius of a breach. Ensure such vendors are thoroughly assessed and monitored.
- Lack of transparency or incident reporting: Vendors who are unwilling to share security information or notify you of incidents promptly can be risky. A partner that won’t disclose its security posture, subcontractors or past breaches may be hiding critical issues. Similarly, if a vendor doesn’t agree to contract clauses about breach notification, that’s a red flag.
- Rapid vendor ecosystem changes: Significant changes like mergers/acquisitions involving a vendor, sudden growth or downsizing, or financial instability can introduce new risks. For instance, if a critical service provider is acquired by a foreign company or faces bankruptcy, it could impact their security or reliability. Monitoring the health of key third parties helps catch these developments.
Implementing Third-Party Risk Management
Implementing an effective third-party risk management program involves a systematic, step-by-step approach. Whether starting a new TPRM initiative or enhancing an existing one, organizations should consider the following key steps:
Inventory all third parties and dependencies
Begin by cataloguing your third-party vendors, suppliers, service providers, and partner software. Include SaaS applications, cloud platforms, consultants – any external entity with access to your data, systems, or processes.
This inventory forms the foundation for managing vendor risk. To understand your attack surface, map out what data or systems each third party can access.
Classify and tier vendors by risk criticality
Not all third parties carry equal risk. Segment your vendor list based on factors like the sensitivity of data they handle, their access privileges, and the criticality of the service they provide.
For example, a payroll processor or core infrastructure provider is high-risk, whereas a low-access marketing tool might be lower risk. Tiering vendors (e.g. high, medium, low risk) helps focus resources on the most critical third parties.
Conduct due diligence and risk assessments
For each vendor (with rigor proportional to their tier), perform thorough risk assessments before onboarding and periodically thereafter.
This typically includes questionnaires or standardized assessments (such as the SIG or CAIQ), security audits, reviewing the vendor’s policies and certifications and evaluating any vendor due diligence documentation. The goal is to identify control gaps or compliance issues. Streamlined due diligence processes help assess vendors efficiently.
Define security requirements and policies
Establish clear policies for third-party risk management and embed security requirements into vendor contracts.
This may involve requiring certain security measures (encryption, access controls, etc.), service level agreements for security incident response, right-to-audit clauses and obligations for vendors to notify you of any breach. A formal TPRM policy aligned to frameworks (like NIST or ISO) can guide consistent enforcement.
Continuous monitoring and risk mitigation
Managing third-party risk is not a one-time activity – it requires ongoing oversight. Implement continuous monitoring to track vendors’ security postures in real time, such as using security ratings services or automated scans for new vulnerabilities. Stay alert to changes (financial, operational, or security-related) in your third parties.
Throughout these steps, organizations should leverage industry frameworks and standards to shape their program. Guidelines like NIST SP 800-161 (for supply chain cybersecurity) and ISO 27036 (supplier security) provide best practices and control recommendations for TPRM.
Aligning your process with such frameworks helps cover all bases and meet regulatory expectations. Ultimately, implementing third-party risk management is about integrating vendor oversight into your overall risk management lifecycle – from onboarding to offboarding – to continuously keep external risks in check.
Third-Party Risk Management Best Practices
Maturing a TPRM program involves adopting proven best practices to efficiently manage vendor risks at scale. Security leaders and vendor risk managers should consider the following practices to strengthen third-party risk management:
1. Use a risk-based tiering approach
Focus effort where it matters most by categorizing vendors into tiers (critical, high, medium, low) based on inherent risk. Apply more intense scrutiny and more frequent assessments to high-risk third parties.
This ensures limited resources are allocated to reduce risk where a third party could truly impact your business. Lower-risk vendors can be managed with lighter touch controls.
2. Leverage standardized assessments
Utilize established questionnaires and frameworks to evaluate vendors in a consistent way. For example, the Shared Assessments SIG (Standardized Information Gathering) questionnaire and the Cloud Security Alliance CAIQ are widely used to collect vendor security information mapped to industry standards. Standardizing your assessment process saves time and allows easier comparison of vendors’ controls.
3. Embed security in procurement and contracts
Make TPRM an integral part of vendor procurement and onboarding. Security and compliance requirements should be defined up front during vendor selection.
Include contractual clauses that mandate security controls, data handling practices, breach notification timelines, and audit rights. By building these into contracts, vendors are obligated to uphold your security and compliance expectations.
4. Continuously validate and test controls
Don’t just trust vendor attestations – verify that their security measures work. This can include requesting evidence (like pen test results) and employing tools to continuously test the security of integrations.
Some organizations perform periodic attack simulations or technical validation on vendor connections to ensure that controls remain effective. Continuous security validation, as a best practice, helps catch any lapses in third-party defenses in real time.
5. Implement ongoing monitoring and threat intelligence
Supplement periodic assessments with continuous monitoring services and threat intel feeds. Automated third-party risk management tools can watch for changes in a vendor’s external security posture (such as new vulnerabilities, leaked credentials, or cyber incidents) and send alerts.
Monitoring financial health and news about critical suppliers is also wise. Early warning allows you to take preventative action before a vendor issue becomes your issue.
6. Foster cross-functional collaboration
Third-party risk touches many parts of the organization – security, compliance, legal, procurement, IT and business units. Create channels for these stakeholders to collaborate on vendor evaluations and share information.
For example, ensure procurement involves the security team in any high-risk vendor purchase. An interdisciplinary TPRM committee or workflow can help break down silos so that everyone works together to manage vendor risks holistically.
The program should become ingrained in business processes (like onboarding and vendor review cycles) and adapt as new risks emerge. Consistency, automation, and collaboration are key themes among successful TPRM programs.
Tools and Platforms for TPRM
Managing dozens or even thousands of vendor relationships manually is a daunting task. Thankfully, a variety of third-party risk management solutions and tools are available to streamline and automate TPRM activities. Key types of TPRM tools and platforms include:
Vendor risk management platforms
Dedicated TPRM software platforms allow centralized tracking of all third parties, digital questionnaires, risk scoring and workflow automation.
These platforms (often cloud-based) serve as a single source of truth for vendor information, documents and assessment results. They provide dashboards to visualize risk across your vendor portfolio and often include reminder systems for periodic reviews. By automating assessments and consolidating data, third-party risk management platforms greatly improve efficiency and consistency.
Continuous monitoring services
These tools continuously scan and analyze vendors’ external cyber risk indicators to provide real-time alerts. Solutions like security ratings services will monitor factors such as exposed ports, security certificate status, data breaches and malware signals for your third parties.
Continuous monitoring offers an independent, outside-in view of a vendor’s security posture on an ongoing basis. If a supplier’s score degrades or a new vulnerability is detected, you can be notified immediately. This complements point-in-time assessments with ongoing vigilance.
Risk quantification and scoring tools
Some platforms provide capabilities to quantify third-party risk in financial or business impact terms. By leveraging analytics and data, they translate technical findings into risk scores or dollar-value impacts.
This helps in prioritizing mitigation efforts and reporting risk levels to executives in understandable ways. Quantitative risk tools can also model fourth-party risk (your suppliers’ suppliers) to highlight concentration risks and systemic issues.
Security validation and testing tools
Another emerging category includes breach and attack simulation (BAS) and attack surface management tools (often part of broader exposure management platforms). These allow you to actively test the security controls surrounding third-party connections or software.
You might simulate an attack from a compromised vendor account to see if your defenses detect and block it. Security validation tools provide assurance that both your organization’s and the vendor’s controls work as expected against real-world threats. They add a layer of technical verification on top of questionnaires and reviews, ensuring no blind spots.
Deploying the right combination of third-party risk management tools can significantly enhance your program. Automation and dashboards reduce the manual workload on risk teams while ensuring no vendor falls through the cracks.
Real-time data and continuous testing mean you aren’t operating on stale information. Ultimately, TPRM platforms and tools enable organizations to scale vendor risk oversight to meet the demands of an ever-expanding digital supply chain.
How Cymulate Supports Third-Party Risk Management
Cymulate is a cybersecurity threat exposure validation platform that enhances Third-Party Risk Management (TPRM) by offering continuous security validation and breach and attack simulation (BAS). With supply chain threats on the rise, Cymulate enables organizations to realistically and safely test the security postures of their vendors and third-party connections.
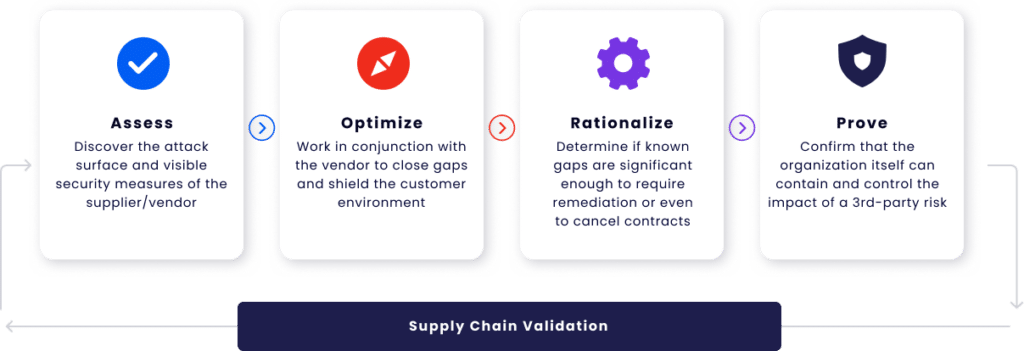
One of Cymulate’s key offerings is its Supply Chain Validation capability. With the vendor’s consent, Cymulate can:
- Scan publicly exposed assets
- Simulate real-world attacks
- Identify weaknesses and misconfigurations
This gives organizations a direct, evidence-based view of a supplier’s security defenses—something static questionnaires can’t achieve.
Cymulate promotes ongoing vendor risk assessment by allowing organizations to:
- Request regular validation assessments from key suppliers
- Use continuous testing to monitor for new vulnerabilities
- Set minimum security score thresholds in SLAs
Vendors can run safe simulations in their own environments and share insights, supporting a collaborative and proactive approach to TPRM.


