Types of Penetration Testing
In a world where cyber threats grow more sophisticated every day, having a strong security posture is critical. It's what keeps you safe from bad actors intent on stealing your data, disrupting your operations or causing financial harm. Penetration testing is a key component of a robust security strategy. By simulating attacks, these tests offer insights into how well your defenses hold up (or don’t).
What Is Penetration Testing?
Penetration testing, or "pen testing," simulates cyberattacks to expose vulnerabilities in a computer, system or network. It’s about finding the gaps before real attackers do.
Pen tests can be done manually by ethical hackers who use real-world hacking techniques, or automatically through specialized software. But whether it’s a person or a program running the test, the goal is the same: expose the vulnerabilities that could be exploited and fix them before it’s too late.
For example, a company might hire a penetration testing firm to assess their web application's security. Pen testers would then try to exploit vulnerabilities, such as SQL injection or cross-site scripting. These attacks involve injecting malicious code to manipulate the database or execute scripts on the user's browser. If successful, they can gain unauthorized access or control of the application. Armed with this information, the company can improve the application's security and prevent real-world attacks.
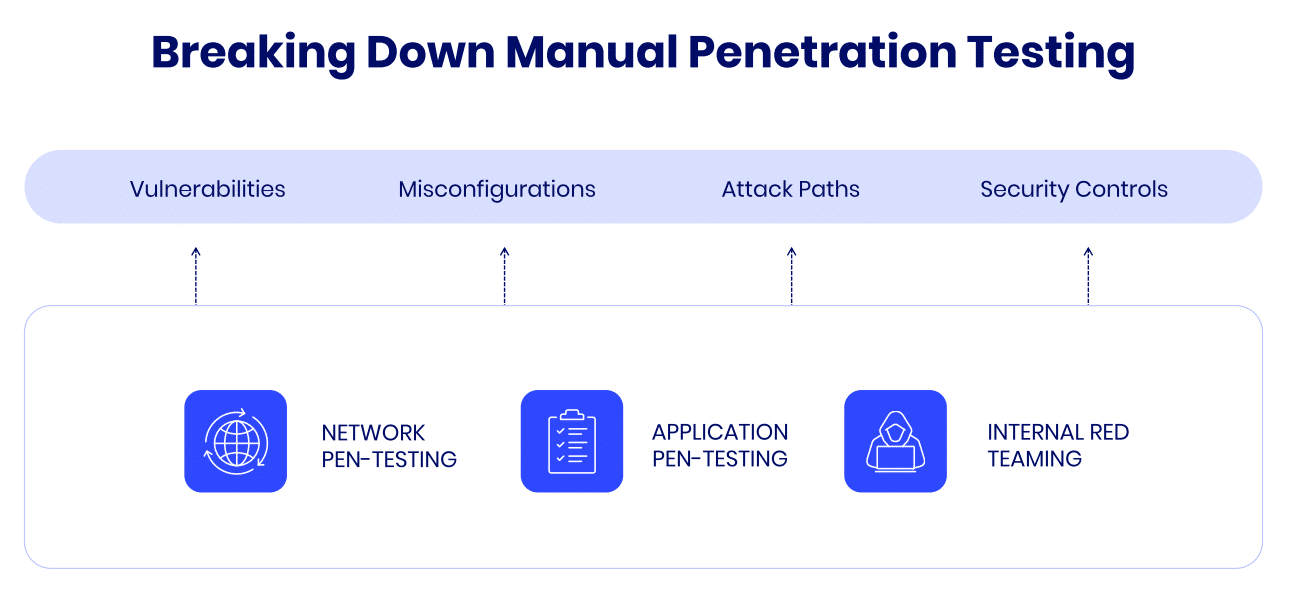
The Three Penetration Testing Methodologies
There are three primary ethical hacking methodologies, and they vary based on how much information the tester has about the system they're trying to breach.
1. White box penetration testing
White box penetration testing, sometimes called "clear" or "glass" box testing, gives the tester full access to internal information. This means everything including source code, credentials and system architecture maps. Because the tester has access to every layer of the system, they can identify weaknesses in logic, code structure or configuration that might not be visible in other types of tests.
Typically, organizations opt for white-box testing when security is critical, and every potential flaw needs to be uncovered and fixed. For example, finance firms and healthcare providers often conduct white-box testing to ensure sensitive data is protected and compliant with regulations.
2. Black box testing
Black box penetration testing is essentially the opposite of white box testing - the tester has no information at all. They approach it like an outsider, using real-world hacking techniques to find and exploit vulnerabilities. This method tests how well a system can defend against external threats, showing how it would perform against a real-world attack.
3. Gray box penetration testing
Gray-box testing falls between black and white box methods - the tester has some information about the system, but not full access. This limited knowledge might include login credentials, partial architecture details or system documentation.
The pen tester simulates an attacker with some level of insider access, such as a compromised employee account or a hacker who has already breached a weak point. Gray-box testing offers a balanced approach, combining the real-world attack scenarios of black-box testing with the targeted precision of white-box testing. It’s ideal for assessing how well a system can handle both internal and external threats.
Different Types of Penetration Testing
Different types of penetration testing cover different areas. The type you choose depends on the specific systems and vulnerabilities you need to assess.
Web application penetration testing
Web application penetration testing focuses on identifying vulnerabilities within web-based applications. Testers examine areas like authentication, data validation, session management and input/output handling. These tests aim to find weaknesses that could allow attackers to compromise user data, manipulate application behavior, or gain unauthorized access. Common vulnerabilities include cross-site scripting (XSS), SQL injection and insecure direct object references. With the widespread use of web applications, this type of testing is crucial for protecting sensitive user data and ensuring the integrity of online services.
Network penetration testing
Network penetration testing assesses the security of an organization's internal and external networks. Testers simulate attacks to identify weaknesses such as open ports, misconfigured firewalls or unpatched vulnerabilities that could allow unauthorized access to sensitive data or systems. The goal is to evaluate how well the network can withstand attacks, detect intrusions and prevent unauthorized access.
For example, a tester might scan the network for open ports that are listening for incoming connections. If they find an open port that is running a vulnerable service, they could attempt to exploit the vulnerability to gain unauthorized access to the system. For instance, if the port is running an FTP server with a weak or default password, the tester could try to log in and access sensitive files.
Testers might also look for cleartext traffic being transmitted over the network. This could include passwords or other sensitive data.
Mobile application penetration testing
Mobile app penetration testing identifies vulnerabilities in apps for smartphones and tablets. Testers analyze functionality, encryption, authentication and data storage. They seek risks like insecure data storage, weak encryption or improper session handling that attackers could exploit. For example, a tester might attempt to reverse engineer the app to extract sensitive data or bypass authentication mechanisms.
Social engineering penetration testing
Social engineering penetration testing evaluates an organization's susceptibility to human-based attacks. Testers use techniques like phishing, baiting and pretexting to manipulate individuals into divulging sensitive information or granting unauthorized access. This identifies weaknesses in employee behavior or processes that attackers could exploit.
For example, the tester might send a phishing email impersonating a software vendor the company uses. The email could include a fake link designed to trick employees into entering their login credentials. If successful, the tester can gain unauthorized access to sensitive information or systems.
Social engineering attacks are particularly effective because they exploit human psychology and trust. By understanding how employees are likely to respond to social engineering tactics, organizations can develop targeted training programs and security policies to mitigate the risk of such attacks.
Cloud penetration testing
Cloud penetration testing identifies vulnerabilities in cloud-based environments (public, private or hybrid). Testers assess configurations, user access controls, data encryption and API security. Given the critical nature of cloud services, testing ensures sensitive data remains secure and the cloud environment is resilient against threats. As more organizations adopt cloud services, cloud penetration testing becomes increasingly essential.
IoT penetration testing
IoT penetration testing identifies vulnerabilities in Internet of Things (IoT) devices and their ecosystems. These include things like industrial sensors and warehouse sensors. Testers evaluate device firmware, communication protocols, user interfaces and data flows.
IoT devices often have weak security practices because they are designed for specific functions rather than general-purpose computing. This means that security is often an afterthought, and devices may lack the necessary features to protect against common cyber threats. Second, the focus on functionality over security can lead to devices being shipped with default passwords or other security vulnerabilities that many companies don't think to address.
External penetration testing
External penetration testing simulates real-world attacks on a company's publicly accessible systems like websites, servers and IP addresses. Testers attempt to exploit vulnerabilities to gain unauthorized access or steal sensitive data. This helps organizations understand the effectiveness of their perimeter defenses and identify gaps in their security posture.
For example, a tester might attempt to brute force login credentials on a company's website. External penetration testing is crucial for protecting publicly accessible systems from cyber attacks.
Wireless penetration testing
Wireless penetration testing evaluates the security of an organization's wireless networks, including Wi-Fi and Bluetooth. Testers attempt to exploit vulnerabilities in wireless protocols, weak encryption methods, and unauthorized access points. This ensures the wireless network is protected from attacks like eavesdropping, man-in-the-middle attacks, or unauthorized access.
For example, a pentester might set up a rogue access point to lure employees into connecting to an unauthorized network. Once connected, the tester could intercept data transmitted over the network or gain access to the employee's device. Given the prevalence of wireless networks in corporate environments, wireless penetration testing is essential to safeguarding sensitive data and preventing attackers from exploiting network weaknesses.
Where Pen Testing Falls Short and What To Do Instead
While penetration testing is undoubtedly useful, it has its limitations. , It only provides a point-in-time snapshot of vulnerabilities, and pen tests are often only conducted once or twice a year.
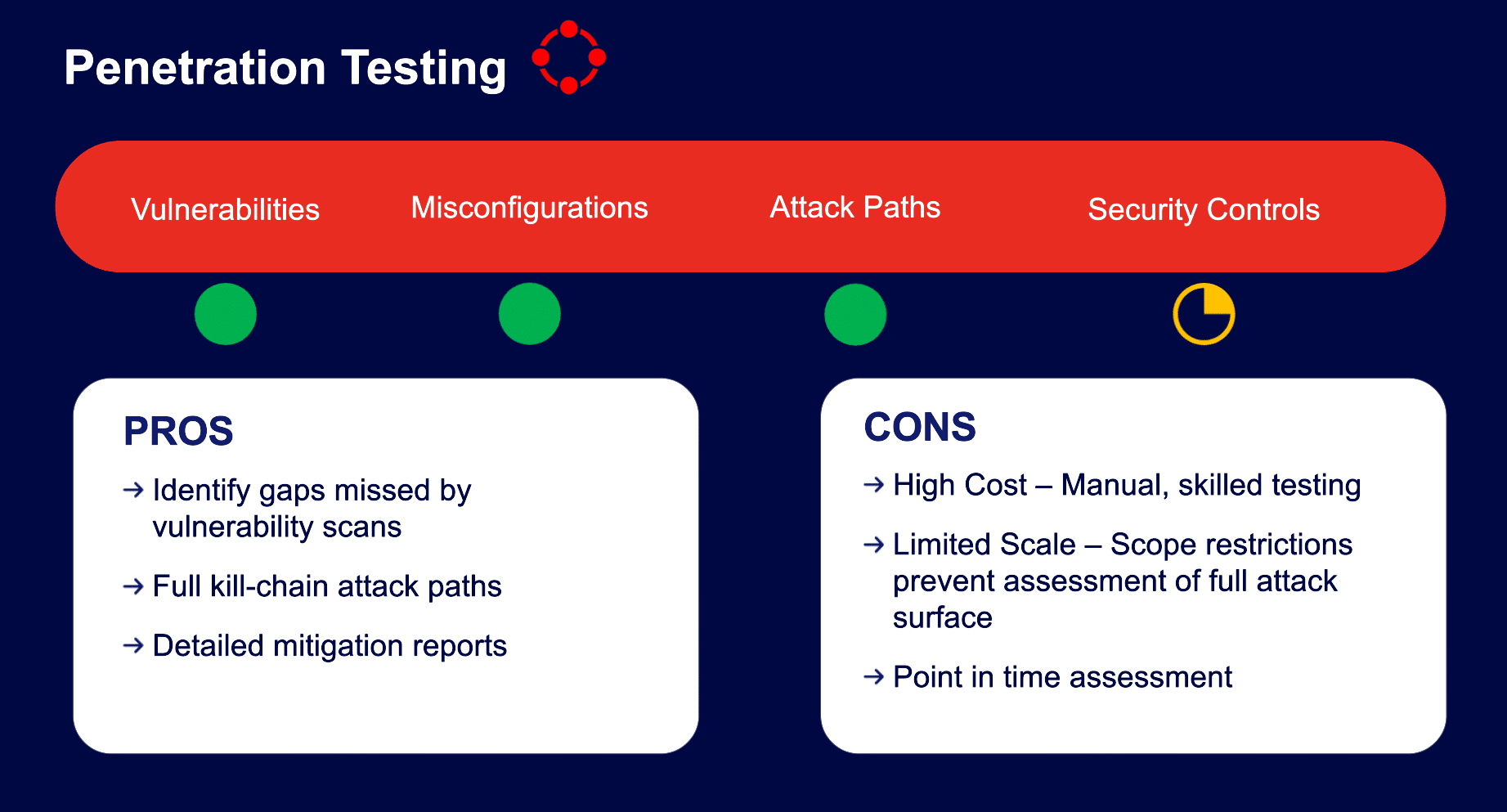
A better approach is security control validation. Unlike penetration testing, security control validation is continuous, automatically validating your security measures against real-world threats. Security control validation automatically checks your defenses across the entire environment, ensuring they are effective against the latest attack techniques. This provides ongoing visibility into your security posture, enabling you to adapt swiftly to emerging risks.
The Cymulate Comprehensive Platform for Security Testing
The Cymulate platform empowers organizations to prioritize critical risks through continuous exposure validation. By simulating real-world attacks, it strengthens defenses against the most dangerous threats.
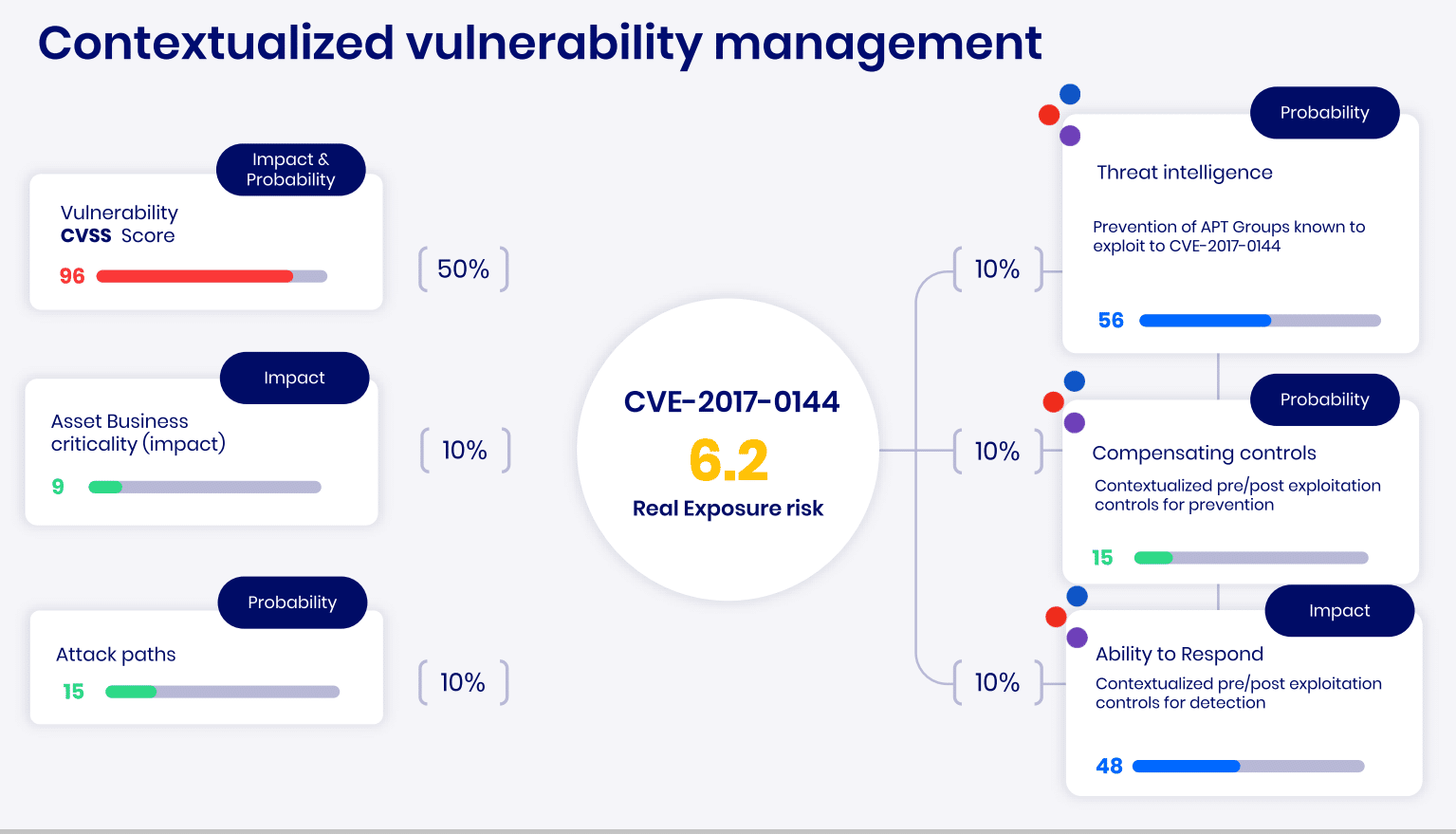
Our platform provides ongoing security resilience validation and optimization, helping you focus on the most pressing gaps. With clear metrics to measure and baseline your cyber performance, you can ensure your defenses remain robust against emerging threats.


