What is VAPT (Vulnerability Assessment and Penetration Testing)?
Vulnerability Assessment and Penetration Testing (VAPT) provides security professionals with the tools to identify, evaluate and mitigate potential risks that could lead to security breaches, forming a critical component to your organization’s cybersecurity strategy. With cyberattacks growing increasingly sophisticated, VAPT enables your organization to defend systems and sensitive data proactively.
The combination of vulnerability assessments and penetration tests gives organizations a clearer, more comprehensive understanding of their security posture. While this process not only helps businesses find weaknesses but also simulates the actions of real-world attackers to validate risk exposure, it operates best when part of a larger continuous threat exposure management (CTEM) strategy.
Key highlights
- VAPT combines two critical practices: vulnerability assessments and penetration testing.
- It provides a comprehensive view of an organization’s risk by combining both broad vulnerability scanning and in-depth exploitation.
- VAPT helps prioritize remediation efforts by identifying the most critical risks that need immediate attention.
- Cymulate enhances the VAPT process by offering continuous threat exposure management (CTEM) with automated security validation that keeps your organization ready to address new threats.
What is VAPT?
VAPT is the security evaluation process designed to identify, assess and mitigate potential vulnerabilities in your organization’s environment. VAPT combines two distinct but complementary practices: vulnerability assessments and penetration tests.
- A vulnerability assessment is the process of identifying and categorizing vulnerabilities within a system, network or application. It aims to find potential weaknesses that could be exploited by attackers.
- Penetration testing simulates an actual attack on the system to exploit the vulnerabilities found during the assessment phase, validating their real-world impact.
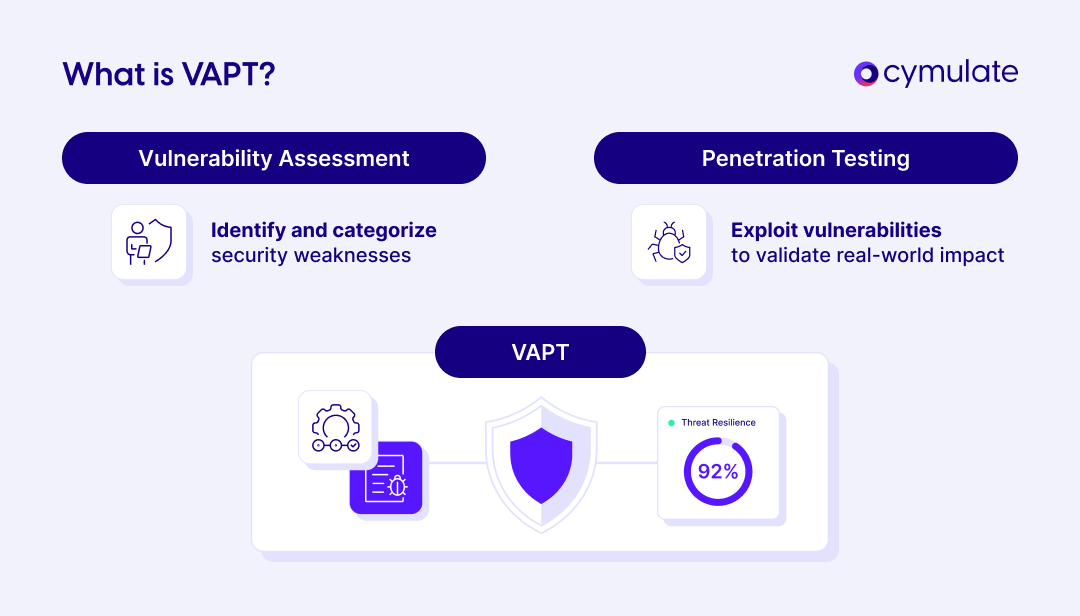
VAPT provides both visibility (through assessments) and validation (through penetration testing). The combined result is an actionable report that helps your organization understand true risk, not just theoretical exposure.
The purpose of VAPT is to assess the security posture of an organization, identify weaknesses and proactively eliminate or mitigate those risks before they can be exploited. By combining the results of vulnerability assessments and penetration tests, VAPT can help your organization adopt a proactive defense strategy and reduce the likelihood of successful cyberattacks.
What is a vulnerability assessment?
A vulnerability assessment is a systematic process for identifying and evaluating vulnerabilities within an environment. The goal of a vulnerability assessment is to discover weaknesses in your organization’s infrastructure that cybercriminals could potentially exploit.
Process of a vulnerability assessment
- Discovery: Scanning the entire environment to identify all assets and systems.
- Scanning: Automated tools scan the environment for known vulnerabilities, misconfigurations and missing patches
- Classification: Identified vulnerabilities are categorized based on severity (critical, high, medium, low).
- Reporting: Vulnerabilities are documented, including descriptions, severity ratings and suggested remediations.
What a vulnerability assessment does not do
A vulnerability assessment is not designed to exploit vulnerabilities to see if they can be used in an attack. It focuses purely on detection and classification of weaknesses. It does not attempt to exploit or test vulnerabilities under real-world conditions.
Use cases, advantages and limitations
- Use cases: vulnerability assessments are typically performed periodically to maintain an up-to-date inventory of vulnerabilities in an environment.
- Advantages: Provides an automated and broad overview of an organization’s risk surface, helping identify gaps that might be overlooked.
- Limitations: While a vulnerability assessment highlights vulnerabilities, it doesn’t validate whether they can be exploited in a real-world attack scenario.
What is a penetration test?
A penetration test (or pen test) is a simulated, controlled attack designed to validate the presence of vulnerabilities identified during a vulnerability assessment. It involves actively attempting to exploit the vulnerabilities within a system to understand the extent of the risk they pose.
Penetration testing methodology
- Reconnaissance: Gathering information about the target system (e.g., public information, system architecture).
- Exploitation: Attempting to exploit vulnerabilities to determine how they can be used by attackers.
- Pivoting: After gaining access, tester attempt to move laterally within the environment to gain deeper access.
- Privilege escalation: Testers try to elevate privileges once inside the system, simulating how attackers can escalate their control.
- Reporting: Results are documented with a focus on exploited vulnerabilities, the attack path and recommendations for remediation.
Penetration testing focus
Unlike vulnerability assessments, which look at breadth (many systems, many vulnerabilities), penetration testing focuses on depth. Different types of penenetrations tests are can be more time-consuming but offer more insight into how vulnerabilities can be exploited by an attacker.
Typical pen test scopes
- Network: Examining internal and external network infrastructures.
- Application: Assessing web and mobile applications for flaws like SQL injection or cross-site scripting.
- Cloud: Testing cloud-based systems and infrastructure.
- Social engineering: Simulating phishing attacks or other social engineering tactics to exploit human weaknesses.
Why combine vulnerability assessment and penetration testing?
While both vulnerability assessments and penetration tests have value on their own, combining them in a VAPT approach can yield benefits.
Broader visibility and validated risk
Vulnerability assessments provide broad visibility into an organization’s weaknesses, while penetration testing offers validation of whether those weaknesses can be exploited. Together, they offer a comprehensive view of the organization’s security landscape, enabling more effective prioritization of remediation efforts.
Improved remediation prioritization
By combining VAs and PTs, security teams can focus on vulnerabilities that pose the most immediate risk, rather than addressing vulnerabilities in isolation.
Better understanding of attacker pathways
The VAPT process helps your organization understand the attacker’s journey from the initial compromise to potential escalation, giving security teams valuable insights into defending against real-world attacks.
Stronger compliance posture
Many compliance frameworks require organizations to conduct vulnerability assessments and penetration tests as part of their security controls. VAPT helps your organization meet compliance requirements while improving security posture.
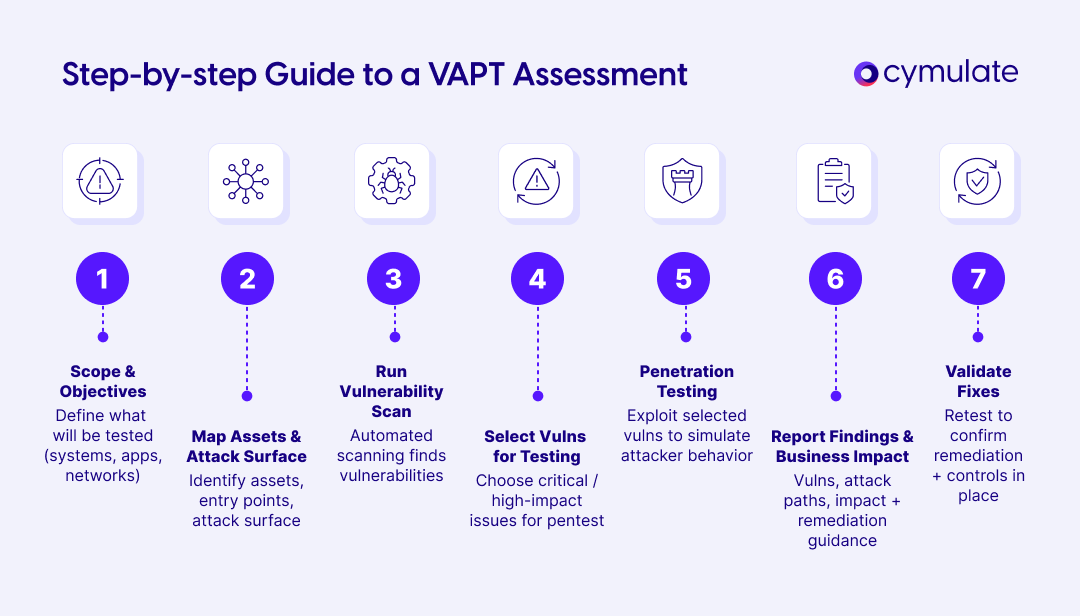
Step-by-step guide to VAPT assessment
A typical VAPT assessment follows several critical stages. Here’s a breakdown of each phase:
- Scoping and defining objectives: Establishing the scope of the engagement, including which systems, networks and applications will be tested.
- Mapping assets and attack surfaces: Identifying assets, networks and attack surfaces for testing.
- Running vulnerability assessments: Using automated tools to scan for vulnerabilities.
- Selecting vulnerabilities for testing: Based on severity, a select group of vulnerabilities is chosen for penetration testing.
- Penetration testing: Attempting to exploit the selected vulnerabilities, simulating an attacker’s actions.
- Documenting findings and business impact: Generating detailed reports that outline vulnerabilities, attack paths and business impact.
- Validating fixes: Ensuring that vulnerabilities are effectively remediated and that controls are in place to prevent future exploitation.
Cymulate automated validation capabilities
The Cymulate platform can automatically validate the effectiveness of remediation efforts and continuously assess your organization’s defenses, making it easier to track and fix vulnerabilities over time.
What’s the difference between VAPT and penetration testing alone?
Comparison between VAPT and penetration testing
| Aspect | VAPT | Penetration Testing |
| Scope | Comprehensive: includes broad vulnerability scanning and deep penetration testing. | Focuses only on exploiting vulnerabilities identified. |
| Goals | Provide a full picture of vulnerabilities and exploitable risks. | Simulate real-world attack scenarios and validate exploitability. |
| Methodology | Combines vulnerability scanning and active exploitation. | Exploits vulnerabilities in real-time to gain access. |
| Tools | Uses automated scanning tools for assessments, combined with manual testing. | Manual and automated penetration testing used for exploiting vulnerabilities. |
| Deliverables | Broad risk profile with identified vulnerabilities and their risk levels. | Detailed exploitation path and severity of the impact. |
| Frequency | Typically done periodically. | Often performed at scheduled intervals or during critical changes. |
VAPT vs. Continuous security validation
Traditional VAPT assessments are periodic and limited in frequency, making them less effective in today’s fast-based threat landscape, where vulnerabilities can arise at any time. To stay ahead of emerging threats, organizations need continuous validation.
Why continuous validation matters
Typically, VAPT is conducted just once or twice a year within an organization. On the other hand, continuous validation (through exposure management solutions) enables organizations to constantly assess their security posture.
Where Cymulate fits in
The Cymulate platform offers continuous, automated security exposure validation that goes beyond traditional VAPT. By simulating real-world attacks continuously and providing real-time visibility into vulnerabilities, Cymulate ensures your organization is always ready for the next threat.
The Cymulate platform’s role in VAPT
While the VAPT process can be helpful for your organization, VAPT alone does not meet the needs of your modern environment. The attack surface is bigger than ever, leading to more potential points of vulnerability in your organization. Running assessments and tests a few times a year is no longer sufficient.
Cymulate enhances the traditional VAPT process. With the Cymulate platform, you’ll automate threat validation and integrate exposure data to prove risk and optimize resilience. By using AI, you can make offensive testing easy, scalable and continuous. This way, you’ll know your defenses are continuously validated and can provide security against real threats.
With Cymulate, you’ll get:
- Continuous security validation to keep your organization constantly prepared.
- Real-visibility into exploitable areas so you can stop drowning in vulnerabilities. Correlate proof of threat resilience with aggregated data from scanners and discovery tools.
- Exposure prioritization so you can focus your resources exposures that pose real, validated risk.
- Comprehensive coverage across email, web gateways, endpoints, networks, cloud and even human layers.
- Actionable insights and prioritized remediation guidance to reduce the most critical risks, validating security posture specific to frameworks like NIST 800-52, CIS Critical Security Controls and MITRE ATT&CK for clear benchmarking and visibility.
- Validation of security controls on demand, ensuring fixes are effective and continuous. Improve threat resilience with custom detection rules and automated mitigation to update security controls for continuously stronger defense.
By integrating automated security validation from Cymulate, your organization can extend the value of traditional VAPT and maintain ongoing readiness to address security gaps.
Frequently asked questions
VAPT should be performed at least annually, but many organizations benefit from conducting it quarterly or whenever significant changes occur in the environment.
The frequency depends on the organization’s risk profile, regulatory requirements and rate of infrastructure change. High-velocity environments (such as those adopting DevOps, cloud-native architectures or continuous deployment) often generate new risks faster than traditional yearly testing can uncover. Because attackers operate continuously, organizations with sensitive data, high compliance obligations or large attack surfaces typically adopt more frequent testing cycles.
In addition, any major system upgrade, network reconfiguration, new application rollout or merger/acquisition event should trigger a new VAPT engagement. The goal is to ensure that vulnerabilities are discovered and addressed before attackers find them, keeping the security posture aligned with real-world threats.
Yes, VAPT covers cloud environments, including SaaS, IaaS and PaaS deployments, as well as hybrid and multi-cloud architectures. Cloud VAPT typically evaluates access controls, identity and permission configurations, exposed services, API endpoints, storage buckets, workload protections and network segmentation.
Because cloud environments are highly dynamic and often misconfigured, cloud VAPT helps identify risks that traditional network tests may overlook. Many organizations also use cloud-specific controls such as CSPM or CIEM, but these do not replace manual testing. Cloud penetration testing validates whether misconfigurations or vulnerabilities can actually be exploited.
As cloud providers follow shared-responsibility models, VAPT helps organizations understand which risks they own and validates that security measures are functioning correctly across distributed systems.
VAPT uses a combination of automated scanners, manual testing frameworks and specialized exploitation tools to identify and validate vulnerabilities. Common tools include commercial vulnerability scanners, open-source exploitation frameworks, credential-testing tools, web application analysis suites and automated reconnaissance platforms.
While vulnerability assessments rely heavily on automated scanning to achieve broad coverage, penetration testers use a mix of custom scripts, attack automation tools and manual techniques to simulate real-world adversaries. Increasingly, organizations augment traditional tools with BAS platforms and exposure management solutions that continuously validate security controls and deliver context-rich insights.
This tooling combination ensures both comprehensive discovery and accurate validation of exploitable weaknesses.
Yes, many regulatory frameworks (including PCI-DSS, HIPAA, SOC 2, ISO 27001 and various regional data protection laws) require periodic vulnerability assessments and penetration testing.
Compliance-driven VAPT ensures organizations meet mandated security controls, validate the effectiveness of defenses and demonstrate that known vulnerabilities are remediated within required timeframes. In industries such as finance, healthcare, retail and critical infrastructure, VAPT is often audited regularly to verify adherence to security standards.
Beyond meeting regulatory checkboxes, compliance-aligned VAPT also helps organizations improve their risk posture by identifying exploitable gaps before auditors or attackers uncover them. While compliance requirements vary, most frameworks emphasize ongoing testing, not one-time engagements, reinforcing the need for continuous validation alongside periodic VAPT.