Vulnerability Scanning
Vulnerability scanning is the automated process of identifying, analyzing and assessing security weaknesses in computer systems, networks, and applications. Organizations use it to detect potential threats before attackers can exploit them, reducing risks and improving security.
The goal of conducting a vulnerability scan is to proactively detect security flaws and weaknesses before they can be exploited by a threat actor. By identifying these vulnerabilities early, organizations can take the necessary steps to mitigate risks, strengthen their security posture and prevent a potentially costly data breach or attack.
Regular scans can help meet compliance requirements, such as PCI DSS, ISO 27001, and Health Insurance Portability and Accountability Act (HIPAA), ensuring businesses follow industry security standards.
How Does Vulnerability Scanning Work?
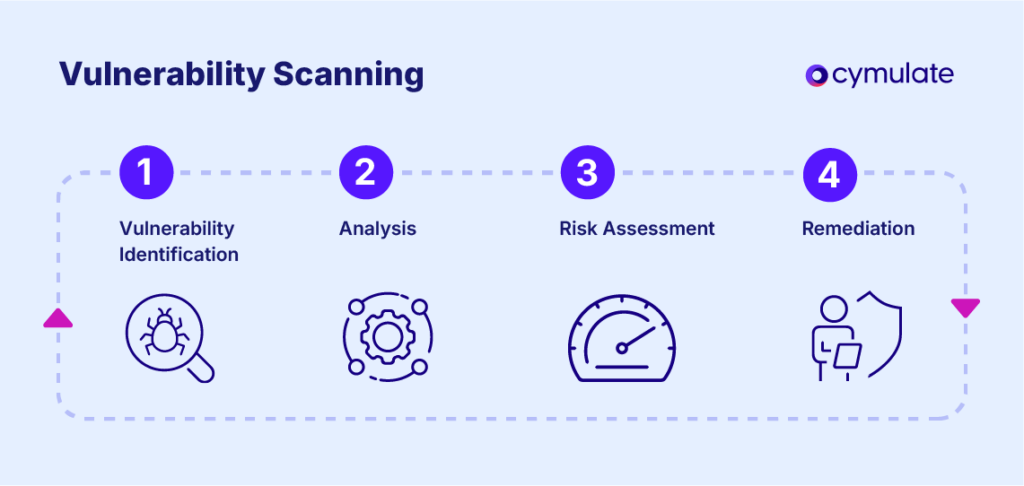
Vulnerability scanning follows a structured process to detect security risks and provide actionable solutions. The process consists of several key steps:
1. Planning and Scope Definition
- Identify the assets to be scanned (e.g., networks, applications, cloud environments).
- Define the scope of the scan (internal, external, cloud, containerized environments, etc.).
- Determine the frequency and compliance requirements for scanning.
2. Scanning and Discovery
- Use automated vulnerability scanners to probe systems for known vulnerabilities.
- Identify active devices, open ports, operating systems, and installed software.
- Map the network and assess potential attack vectors.
3. Vulnerability Detection and Analysis
- Compare identified assets against known vulnerabilities in databases like CVE (Common Vulnerabilities and Exposures) and NVD (National Vulnerability Database).
- Categorize vulnerabilities based on severity (e.g., CVSS score).
- Identify false positives and eliminate redundant findings.
4. Risk Prioritization
- Prioritize vulnerabilities based on risk factors, such as exploitability, impact, and criticality of the affected systems.
- Use context-aware analysis to focus on exploitable vulnerabilities rather than theoretical risks.
5. Reporting and Documentation
- Generate detailed reports with findings, risk levels, and remediation recommendations.
- Customize reports based on the audience (e.g., executive summaries for management, technical details for security teams).
- Maintain records for compliance with regulations (e.g., PCI DSS, HIPAA, ISO 27001).
6. Remediation and Mitigation
- Work with security teams to patch or mitigate vulnerabilities.
- Apply security controls, such as network segmentation, application whitelisting, or disabling vulnerable services.
- Implement compensating controls if patches are unavailable.
7. Rescanning and Continuous Monitoring
- Perform a follow-up scan to ensure vulnerabilities have been mitigated.
- Establish a regular scanning schedule to detect new vulnerabilities.
Integrate continuous security validation through tools like Breach and Attack Simulation (BAS) to ensure protection against evolving threats.
Types of Vulnerability Scanning
There are two primary types of vulnerability scanning:
- Authenticated scans: These scans use valid login credentials to access systems. It allows a deeper inspection of security settings, installed software, and misconfigurations that an attacker with access might exploit.
- Unauthenticated scans: These scans simulate an external attack by assessing systems without login credentials. They help identify vulnerabilities visible to outsiders, such as exposed ports, weak encryption, or publicly accessible services.
Both scanning methods are essential for a comprehensive security strategy. By regularly conducting vulnerability scans, organizations can proactively detect and fix weaknesses before attackers exploit them.
Different types of scans focus on specific areas, ensuring comprehensive security coverage.
1. Network-based vulnerability scanning
Identifies security weaknesses in internal and external networks by detecting unpatched systems, open ports, outdated protocols, and misconfigurations in firewalls and network devices.
2. Host-based vulnerability scanning
Assesses individual devices like servers and endpoints to find missing patches, outdated software, insecure configurations, and local privilege escalation risks.
3. Web application vulnerability scanning
Identifies web application threats such as SQL injection, cross-site scripting (XSS), and weak authentication while ensuring protection against OWASP Top 10 vulnerabilities.
4. Database vulnerability scanning
Detects misconfigurations, weak encryption, and insecure permissions in databases to prevent unauthorized access and ensure compliance with security standards.
5. Cloud vulnerability scanning
Finds misconfigurations, weak IAM settings, and exposed resources in cloud environments while assessing security controls for AWS, Azure, and Google Cloud.
Each type of vulnerability scanning plays a crucial role in securing an organization’s digital assets. By using a combination of these scans, businesses can strengthen their cybersecurity posture, minimize risks, and comply with industry standards.
The Ideal Outcome of a Vulnerability Scan
A successful vulnerability scan provides organizations with clear insights into their security risks and actionable steps to improve protection. The key outcomes include:
- A prioritized list of vulnerabilities: The scan generates a detailed report ranking vulnerabilities by severity, helping organizations focus on the most critical threats first. High-risk issues, such as exploitable weaknesses or unpatched software, receive immediate attention.
- Actionable remediation steps: The report includes specific recommendations to fix vulnerabilities, such as applying security patches, updating configurations, or disabling unnecessary services. These steps ensure a proactive approach to reducing risk.
- Compliance alignment: The scan helps organizations meet industry security standards, such as PCI DSS, ISO 27001, and HIPAA, by identifying gaps that need to be addressed for regulatory compliance.
- Continuous monitoring recommendations: A vulnerability scan is not a one-time fix. The report often suggests continuous vulnerability assessment and security best practices, such as automated patch management and regular security assessments, to maintain a strong security posture.
By taking steps to act on the results of a vulnerability scan, organizations can strengthen their defenses, reduce the risk of cyber threats, and maintain compliance with industry regulations.
The Limitations of Vulnerability Scanning
Relying on scanning alone is not enough to maintain a strong security posture. Organizations should understand these challenges to strengthen their overall cybersecurity strategy.
False positives and false negatives
Vulnerability scanners sometimes generate false positives, flagging non-critical issues that don’t pose real threats. Security teams may waste time investigating harmless findings instead of addressing actual risks.
On the other hand, false negatives occur when scanners fail to detect advanced threats, leaving organizations exposed to hidden vulnerabilities.
Lack of context
Scanners identify vulnerabilities but do not assess their exploitability. A flagged issue might not be a real threat if it requires complex attack conditions. Without proper risk analysis, organizations may prioritize low-risk vulnerabilities while overlooking more significant security gaps.
No validation of security controls
Vulnerability scans detect weaknesses but do not test whether security defenses are effective. For example, a scanner may report an open port as a risk, but if a firewall or intrusion prevention system (IPS) effectively blocks attacks, the real-world impact is minimal.
Limited scope
Vulnerability scanning tools primarily focus on known vulnerabilities, meaning they may overlook zero-day threats or lateral movement risks, where attackers exploit multiple weak points within a network.
Additionally, some security testing tools may struggle with complex or custom-built applications.
To strengthen security, organizations should go beyond scanning and incorporate security control validation and breach simulation. Security validation tests whether defenses work against threats, while breach simulations mimic real-world attacks to identify exploitable weaknesses.
Combining these approaches with vulnerability scanning provides a more comprehensive and proactive cybersecurity strategy.
How Cymulate Enhances Vulnerability Scanning
Traditional vulnerability scanning helps identify weaknesses, but it does not test whether these vulnerabilities can be exploited or if security controls effectively block real-world attacks. Cymulate Breach and Attack Simulation (BAS) goes beyond scanning by continuously validating an organization’s defenses against real cyber threats.
| Key areas | Traditional vulnerability scanning | Cymulate BAS |
| Validating exploitability | Traditional scanners detect vulnerabilities but do not determine if they can actually be exploited. | Cymulate simulates real attack scenarios, allowing security teams to see which vulnerabilities pose a real risk and require immediate action. |
| Testing security controls | Scanners flag potential weaknesses, but they don’t test how well-existing security measures mitigate threats. | Cymulate validates security controls by running full kill-chain attack simulations, ensuring firewalls, endpoint protection, and detection systems are working as intended. |
| Exposure-based risk assessments | Instead of relying solely on theoretical risk scores, Cymulate analyzes exposure in real time, providing actionable insights on security gaps. | Organizations can prioritize remediation based on actual attack outcomes, rather than just scanner-generated severity ratings. |
| Continuous security validation | Cyber threats evolve daily, and a one-time vulnerability scan is not enough to maintain security. | Cymulate enables ongoing, automated vulnerability scanning and attack simulations, helping security teams stay ahead of emerging threats. |