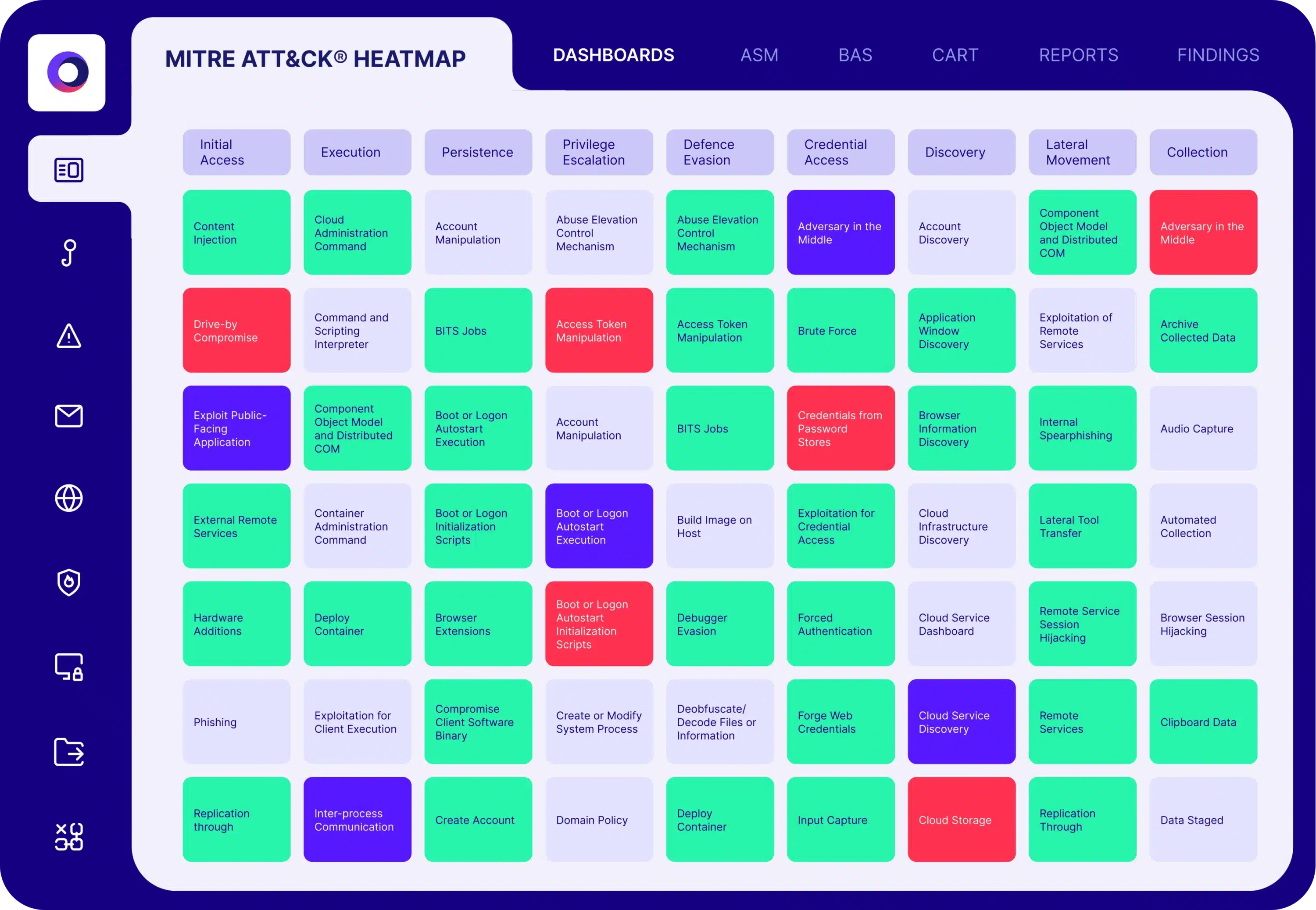
Email Gateway Validation
Test and optimize your secure email gateway against
the latest email-borne threats.
Email remains the number-one attack vector and the most frequently used delivery method for cyber attacks.
Organizations suffered
email security incidents
Source: Egress Software
Cyber attacks started
with a phishing email
Source: Egress Software
Ransomware attacks
began with an email
Source: Barracuda Networks
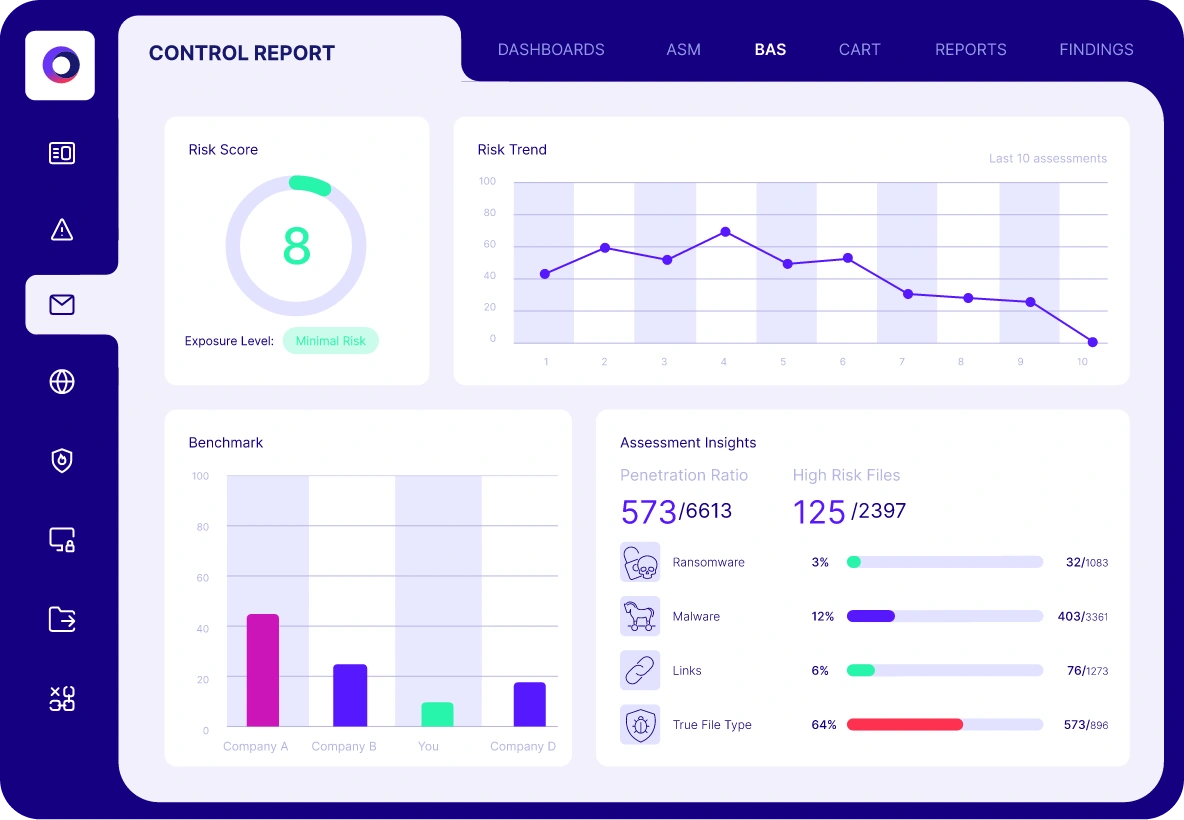
Email Gateway Assessment
Cymulate uses breach and attack simulations to assess the efficacy of your email defenses. The automated security validation simulates different types of email-borne threats and malicious content to validate the effectiveness of your secure email gateway including:
- Malicious links and attachments
- Executable payloads
- Dummy code execution
- True file type detection
- Email attachment policies
Solution Results
91%
Improvement in malicious file detection post mitigation
89%
Reduction in email gateway risk score within two weeks
50%
Improvement in the prevention of known attack techniques
Solution Benefits
Automated security validation
gateway controls and policies against the latest
email-borne threats.
Identify gaps and weaknesses
Optimize security controls
Reduce exposure risk
What our customers say about us
Organizations across all industries choose Cymulate for automated cybersecurity validation, proactively confirming that defenses are robust and reliable-before an attack occurs.