Frequently Asked Questions
Product Overview & Purpose
What is Cymulate Endpoint Security Validation?
Cymulate Endpoint Security Validation is a solution that uses automated breach and attack simulation to test and optimize your endpoint defenses against malicious files and behaviors. It helps organizations proactively identify weaknesses in endpoint security controls, including antivirus (AV) and endpoint detection and response (EDR) solutions, by simulating real-world attack techniques such as ransomware, worms, trojans, rootkits, DLL side-loading, and code injection.
What is the primary purpose of Cymulate Endpoint Security Validation?
The primary purpose is to help organizations proactively validate the effectiveness of their endpoint security controls, identify vulnerabilities, and optimize their security posture. By simulating a wide range of attacks, Cymulate enables security teams to stay ahead of emerging threats and improve overall resilience.
How does Cymulate Endpoint Security Validation work?
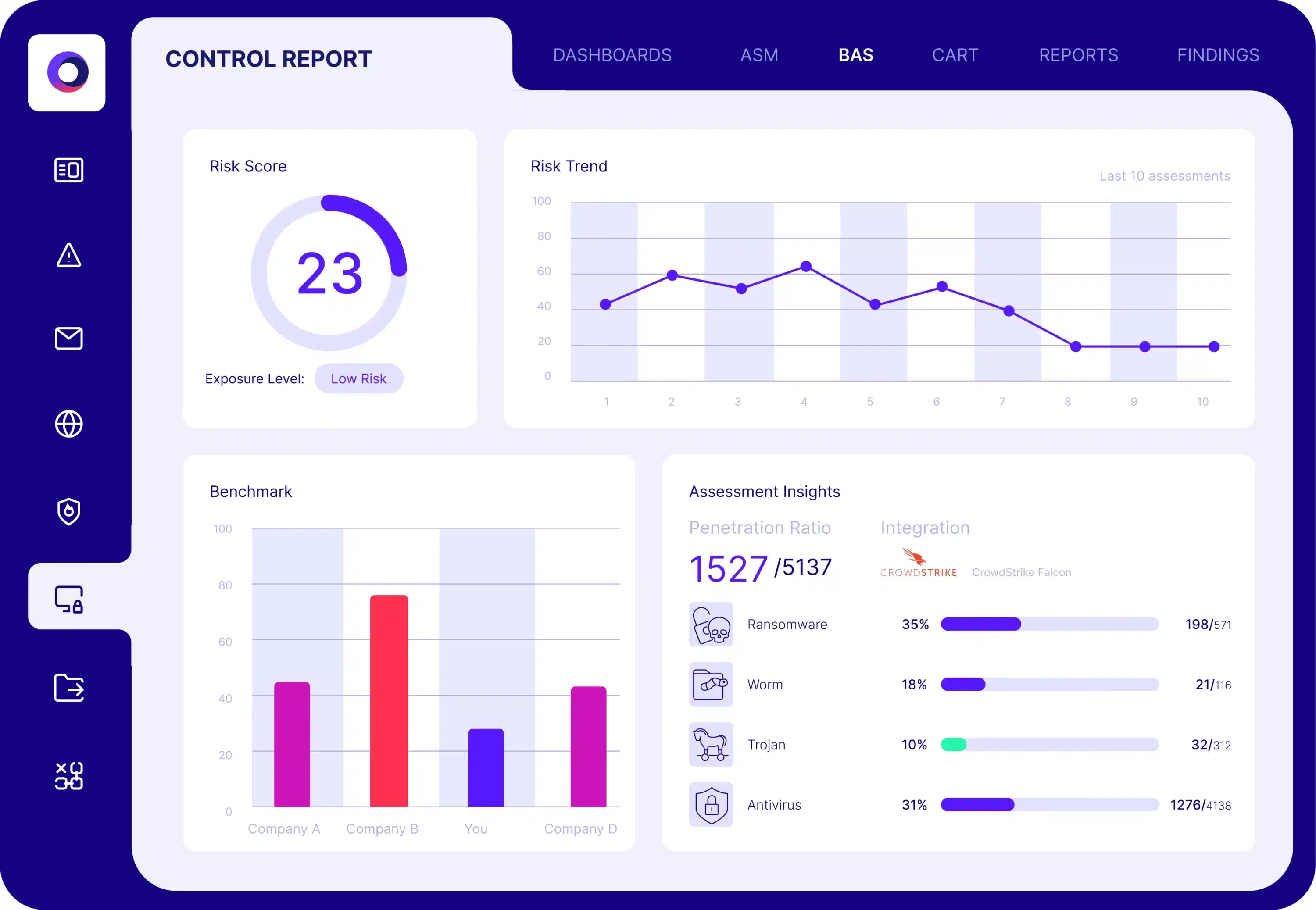
Cymulate automates the testing of endpoint security controls by simulating thousands of known malicious file samples and advanced attack behaviors. It executes over 490 attack simulations from the threat actor's playbook, providing detailed findings, risk scores, penetration ratios, and actionable mitigation guidance to optimize endpoint security.
What types of attacks does Cymulate Endpoint Security Validation simulate?
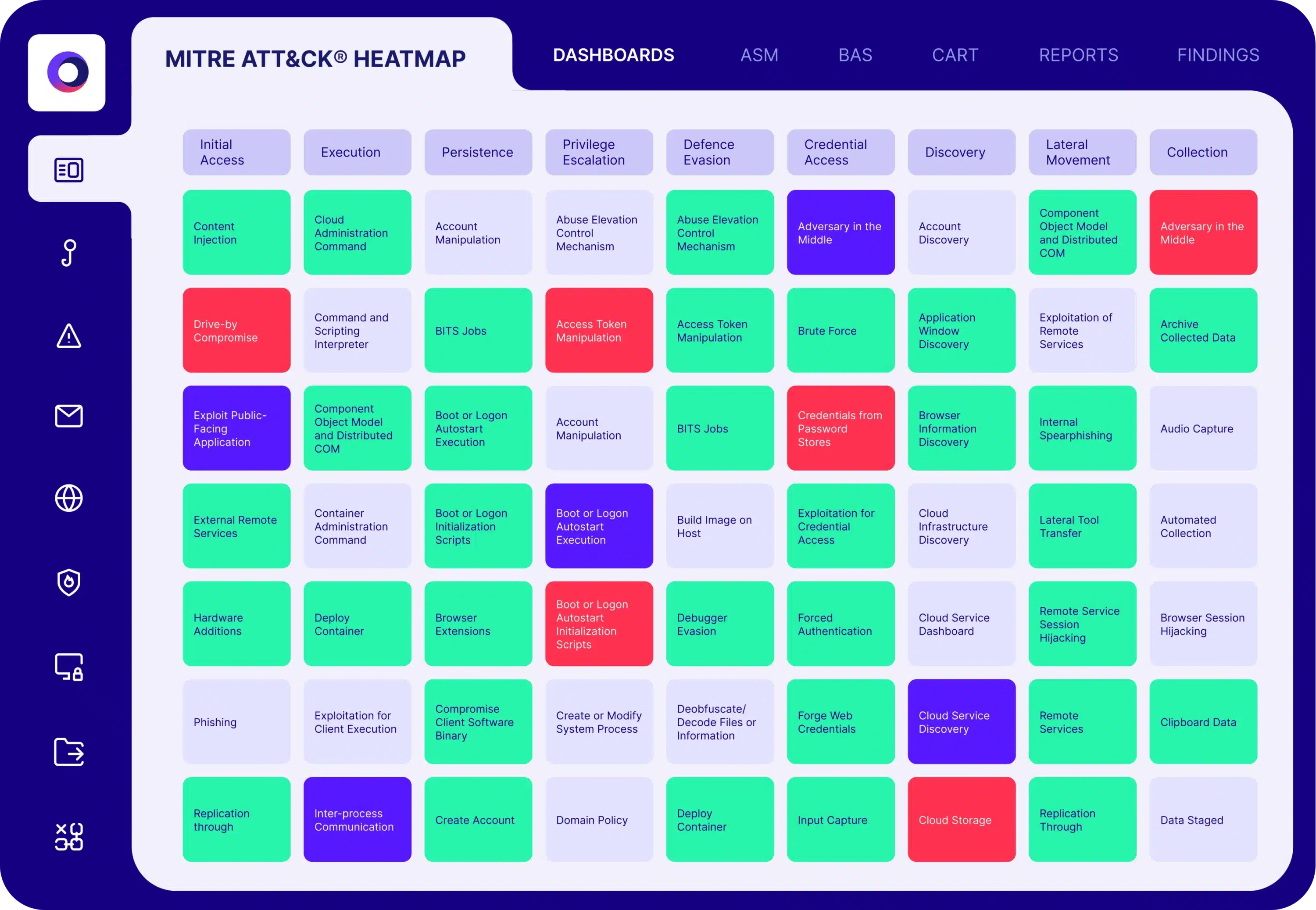
The solution simulates a wide range of attacks, including ransomware, worms, trojans, rootkits, DLL side-loading, code injection, and other malicious behaviors. It also tests AV and EDR controls against thousands of known malicious file samples updated daily.
Features & Capabilities
What are the key features of Cymulate Endpoint Security Validation?
Key features include automated breach and attack simulation, continuous control validation, simulation of known malicious file samples and behaviors, detailed reporting with risk scores and penetration ratios, and mitigation guidance for optimizing endpoint security controls.
How does Cymulate validate endpoint security controls?
Cymulate validates endpoint security controls by simulating both known malicious file samples (for AV) and advanced malicious behaviors (for EDR). It automates the execution of these simulations and provides detailed findings to help organizations identify and remediate gaps in their endpoint defenses.
What reporting and analytics does Cymulate provide?
Cymulate provides detailed findings and reports, including risk scores, penetration ratios, insights into the most and least protected threat categories, and actionable mitigation recommendations. These reports help organizations measure and optimize their endpoint security effectiveness.
How often are attack simulations and threat libraries updated?
Cymulate's threat library is updated daily, ensuring that simulations reflect the latest attack techniques and threat intelligence. This helps organizations stay ahead of emerging threats and continuously validate their defenses.
Does Cymulate support both AV and EDR validation?
Yes, Cymulate supports validation for both antivirus (AV) and endpoint detection and response (EDR) controls. It simulates thousands of known malicious file samples for AV and automates the testing of EDR controls by simulating advanced malicious behaviors.
How many attack simulations does Cymulate Endpoint Security Validation offer?
Cymulate Endpoint Security Validation offers over 490 attack simulations from the threat actor's playbook, covering a broad range of techniques and tactics used in real-world attacks.
Use Cases & Benefits
Who can benefit from Cymulate Endpoint Security Validation?
Organizations of all sizes and industries can benefit, including finance, healthcare, retail, media, transportation, and manufacturing. The solution is designed for CISOs, security leaders, SecOps teams, red teams, and vulnerability management teams seeking to proactively validate and optimize endpoint security.
What are the main benefits of using Cymulate Endpoint Security Validation?
Main benefits include a 60% increase in team efficiency, 25% reduction in manual SecOps tasks, and 70% reduction in vulnerabilities between pen tests. The solution enables continuous control validation, identifies gaps and weaknesses, optimizes security controls, and reduces exposure risk.
How does Cymulate help reduce the risk of endpoint data breaches?
By continuously measuring and improving endpoint security posture, Cymulate helps organizations reduce the risk of cyber attacks and data breaches. Automated simulations identify and remediate weaknesses before attackers can exploit them, minimizing the likelihood and impact of breaches.
Can Cymulate be used to compare different endpoint security solutions?
Yes, Cymulate can be used to evaluate and compare the effectiveness of different endpoint security solutions, including AV and EDR products. Customers have used Cymulate to compare endpoint solutions, DNS filtering services, and email security, benefiting from its wide range of attack simulations.
What customer results have been achieved with Cymulate Endpoint Security Validation?
Customers have reported a 60% increase in team efficiency, 25% reduction in manual SecOps tasks, and 70% reduction in vulnerabilities between pen tests. These results demonstrate the platform's effectiveness in improving operational efficiency and reducing risk. (Source: Cymulate Solution Results)
Are there real customer testimonials for Cymulate Endpoint Security Validation?
Yes, customers from various industries have praised Cymulate for its ease of use, effectiveness, and breadth of attack simulations. For example, an Information Risk Officer in the banking industry highlighted the tool's ability to measure malware attack risks and verify cyber defense effectiveness, while an IT Operations Manager in financial services noted its impressive attack range and usefulness in evaluating security controls. (See full testimonials on the Cymulate website.)
Implementation & Ease of Use
How easy is it to implement Cymulate Endpoint Security Validation?
Cymulate is designed for quick and easy implementation. It operates in agentless mode, requiring no additional hardware or complex configurations. Customers can start running simulations almost immediately after deployment, with minimal resources required.
What support resources are available for Cymulate Endpoint Security Validation?
Cymulate provides comprehensive support, including email support ([email protected]), real-time chat support, a knowledge base with technical articles and videos, webinars, e-books, and an AI chatbot for quick answers and guidance.
Is Cymulate Endpoint Security Validation suitable for organizations with limited security resources?
Yes, Cymulate is designed to be intuitive and user-friendly, making it accessible for organizations with limited security resources. Its automation and ease of use help teams maximize effectiveness without requiring extensive expertise or manual effort.
How do customers rate the ease of use of Cymulate Endpoint Security Validation?
Customers consistently praise Cymulate for its intuitive interface and ease of use. Testimonials highlight the platform's user-friendly dashboard, quick implementation, and accessible support, making it easy for teams to understand and act on security insights. (See customer reviews on the Cymulate website.)
Integrations & Compatibility
What endpoint security solutions does Cymulate integrate with?
Cymulate integrates with a wide range of endpoint security solutions, including BlackBerry Cylance OPTICS, Carbon Black EDR, Cisco Secure Endpoint, CrowdStrike Falcon, SentinelOne, and Cybereason. For a full list of integrations, visit the Cymulate Partnerships and Integrations page.
How does Cymulate enhance existing endpoint security solutions?
Cymulate enhances existing endpoint security solutions by automating validation and providing actionable insights into their effectiveness. It identifies gaps and weaknesses, enabling organizations to optimize configurations and improve overall endpoint protection.
Where can I find more information about Cymulate's integrations?
You can find a complete list of Cymulate's technology partners and integrations, including endpoint security, cloud security, and vulnerability management solutions, on the Cymulate Partnerships and Integrations page.
Security, Compliance & Certifications
What security and compliance certifications does Cymulate hold?
Cymulate holds several key certifications, including SOC2 Type II (covering security, availability, confidentiality, and privacy), ISO 27001:2013 (Information Security Management), ISO 27701 (Privacy Information Management), ISO 27017 (Cloud Services Security Controls), and CSA STAR Level 1. These certifications demonstrate Cymulate's commitment to industry-leading security and compliance standards. Learn more.
How does Cymulate ensure data security and privacy?
Cymulate ensures data security through encryption for data in transit (TLS 1.2+) and at rest (AES-256), secure AWS-hosted data centers, a tested disaster recovery plan, and a strict Secure Development Lifecycle (SDLC). The platform also includes mandatory 2-Factor Authentication (2FA), Role-Based Access Controls (RBAC), and IP address restrictions.
Is Cymulate Endpoint Security Validation compliant with GDPR?
Yes, Cymulate incorporates data protection by design and has a dedicated privacy and security team, including a Data Protection Officer (DPO) and Chief Information Security Officer (CISO), ensuring GDPR compliance.
What application security practices does Cymulate follow?
The platform is developed using a strict Secure Development Lifecycle (SDLC), including secure code training, continuous vulnerability scanning, and annual third-party penetration tests. Employees also undergo ongoing security awareness training and phishing tests.
Pricing & Plans
What is Cymulate's pricing model for Endpoint Security Validation?
Cymulate operates on a subscription-based pricing model tailored to each organization's requirements. The subscription fee depends on the chosen package, number of assets, and scenarios selected for testing and validation. For a detailed quote, you can schedule a demo with the Cymulate team.
How can I get a quote for Cymulate Endpoint Security Validation?
To receive a personalized quote, visit the Cymulate website and schedule a demo. The Cymulate team will assess your organization's needs and provide a tailored pricing proposal.
Competition & Differentiation
How does Cymulate Endpoint Security Validation differ from traditional penetration testing?
Unlike traditional penetration testing, which is typically point-in-time and manual, Cymulate Endpoint Security Validation offers continuous, automated attack simulations. This enables organizations to validate their defenses in real-time, identify gaps more efficiently, and respond to emerging threats faster.
What makes Cymulate Endpoint Security Validation unique compared to other BAS tools?
Cymulate stands out with its unified platform, daily updated threat library, agentless deployment, ease of use, and comprehensive reporting. It offers over 490 attack simulations and integrates with leading endpoint security solutions, providing actionable insights and measurable improvements in security posture.
How does Cymulate Endpoint Security Validation help different user roles?
Cymulate provides tailored benefits for CISOs (quantifiable metrics and risk prioritization), SecOps teams (automation and operational efficiency), red teams (automated offensive testing), and vulnerability management teams (continuous validation and prioritization). Each role can leverage the platform to address their specific security challenges.
Resources & Further Information
Where can I find the solution brief for Cymulate Endpoint Security Validation?
You can download the solution brief for Endpoint Security Validation at this link for more details on features and benefits.
Are there best practices for endpoint security validation available?
Yes, Cymulate provides best practices for endpoint security validation in its blog and e-book resources. You can read about security validation best practices for endpoint AV and EDR solutions on the Cymulate blog and download the e-book on security validation principles.
How can I schedule a demo of Cymulate Endpoint Security Validation?
You can schedule a personalized demo by visiting the Cymulate website and clicking on the 'Book a Demo' link. The Cymulate team will walk you through the platform and answer any questions you may have.
Where can I find customer case studies for Cymulate Endpoint Security Validation?
You can find customer case studies, including those from the financial services industry and other sectors, on the Cymulate Customers page. These case studies showcase real-world results and use cases.