Operationalizing
the MITRE ATT&CK® Framework
The MITRE ATT&CK® framework is a globally accessible knowledge base of adversary tactics and techniques based on real-world observations. Cymulate uses this framework to create realistic attack scenarios, allowing customers to assess and improve their security controls in production environments.
14 Tactics of the ATT&CK Framework
The ATT&CK Matrix for Enterprise describes the cyber kill chain in 14 tactics, each with numerous techniques and sub-techniques. Implementing a single technique can have thousands of variations. For example, validating email security against spear phishing requires thousands of unique emails to identify those that bypass security controls undetected.
Reconnaissance
Techniques that involve adversaries actively or passively gathering information that can be used to support targeting.
Resource Development
Techniques that involve adversaries creating, purchasing, or compromising/ stealing resources that can be used to support targeting.
Initial Access
Techniques that use various entry vectors to gain their initial foothold within a network.
Execution
Techniques that result in adversary-controlled code running on a local or remote system.
Persistence
Techniques that adversaries use to keep access to systems across restarts, changed credentials, and other interruptions that could cut off their access.
Privilege Escalation
Techniques that adversaries use to gain higher-level permissions on a system or network.
Defense Evasion
Techniques that adversaries use to avoid detection throughout their compromise.
Credential Access
Techniques for stealing credentials like account names and passwords.
Discovery
Techniques an adversary may use to gain knowledge about the system and internal network.
Lateral Movement
Techniques that adversaries use to enter and control remote systems on a network.
Collection
Techniques adversaries may use to gather information and the sources information is collected from that are relevant to following through on the adversary’s objectives.
Command and Control
Techniques that adversaries may use to communicate with systems under their control within a victim network.
Exfiltration
Techniques that adversaries may use to steal data from your network.
Impact
Techniques that adversaries use to disrupt availability or compromise
integrity by manipulating business and operational processes.
Mapping Vectors to MITRE ATT&CK Tactics
Cymulate maps ATT&CK tactics to attack vectors to assess security layers against real-world scenarios. Each attack vector implements multiple tactics, and the same tactics are used across different vectors, simulating actual attacks. For instance, the Recon vector includes techniques from both Reconnaissance and Resource Development, while Lateral Movement techniques are tested in both Endpoint and Lateral Movement vectors. This approach allows customers to independently assess and optimize each security layer against techniques used by threat actors.
| ATTACK Tactics | Cymulate Attack Vectors and Modules | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
| Recon | Web Gateway | Email Gateway | Web Application Firewall | Phishing Awareness | Endpoint Security | Lateral Movement | Data Exfiltration | Full Kill Chain APT | Immediate Threats Intelligence | Purple Team | |
| Reconnaissance | |||||||||||
| Resource Development | |||||||||||
| Initial Access | |||||||||||
| Execution | |||||||||||
| Persistence | |||||||||||
| Privilege Escalation | |||||||||||
| Defense Evasion | |||||||||||
| Credential Access | |||||||||||
| Discovery | |||||||||||
| Lateral Movement | |||||||||||
| Collection | |||||||||||
| Command and Control | |||||||||||
| Exfiltration | |||||||||||
| Impact | |||||||||||
Operationalize threat intelligence
& the MITRE ATT&CK framework
To continuously challenge, assess and optimize security operations.
Security Infrastructure
SOAR
via API
Queries
IoCs and IoBs
Guidance
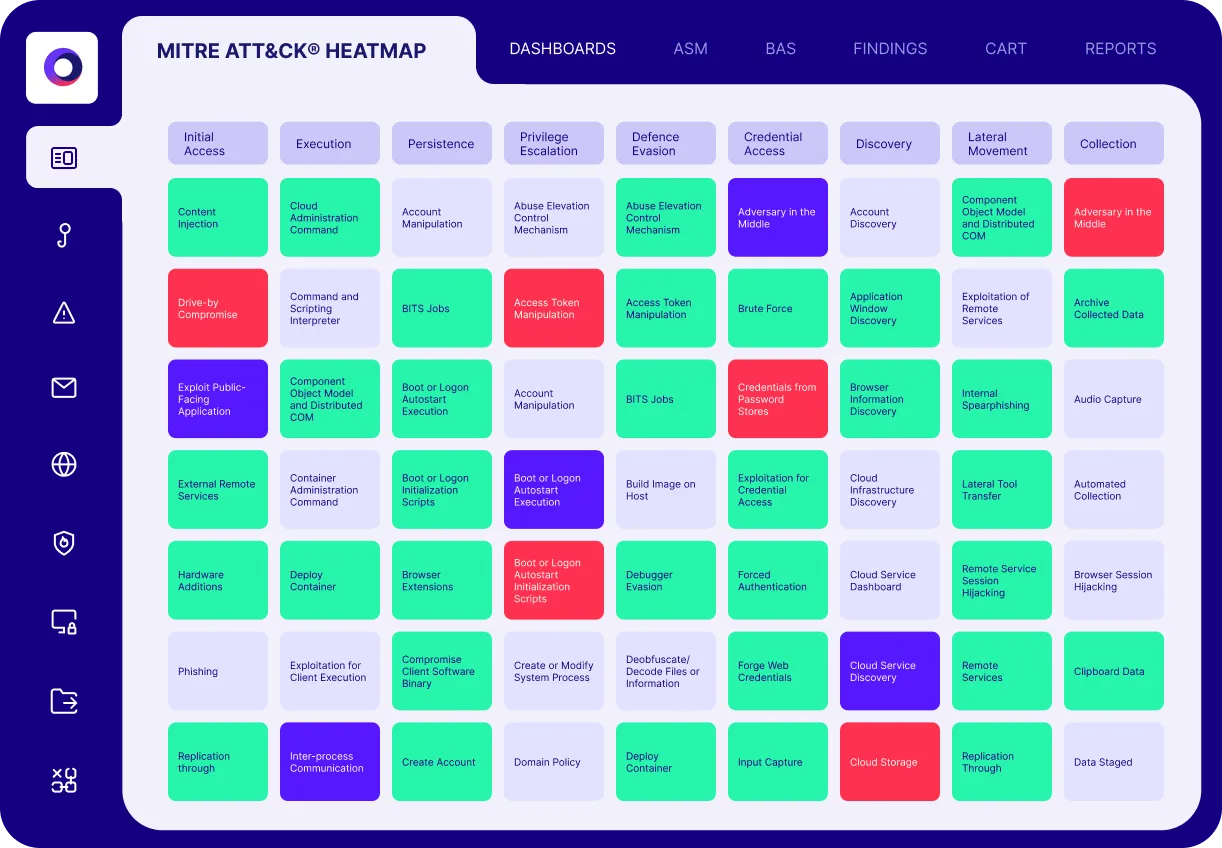
Mapping the Results
The MITRE ATT&CK® framework provides a comprehensive knowledge base and common taxonomy for the cyber-attack kill chain, allowing security professionals to use a shared language when describing attacks and vulnerabilities. Cymulate aligns with this framework, mapping assessments and results to it, and providing a heat map that highlights strengths and weaknesses in security architecture.