thre
validated
Reducing threat exposure doesn't have to be complicated. Just focus on the exploitable.
Book a DemoOutcome-Driven Threat Exposure Validation
Proactive security to filter out noise and guide immediate action
Prove anything.
Harden defense.
Focus on the exploitable.
Prove anything.
Harden defense.
Focus on the exploitable.
One AI-powered platform.
Better efficiency. Stronger cyber resilience.
Cymulate Named Leader in 7 categories on G2
Discover how Cymulate empowers security professionals to validate and strengthen their cyber resilience.

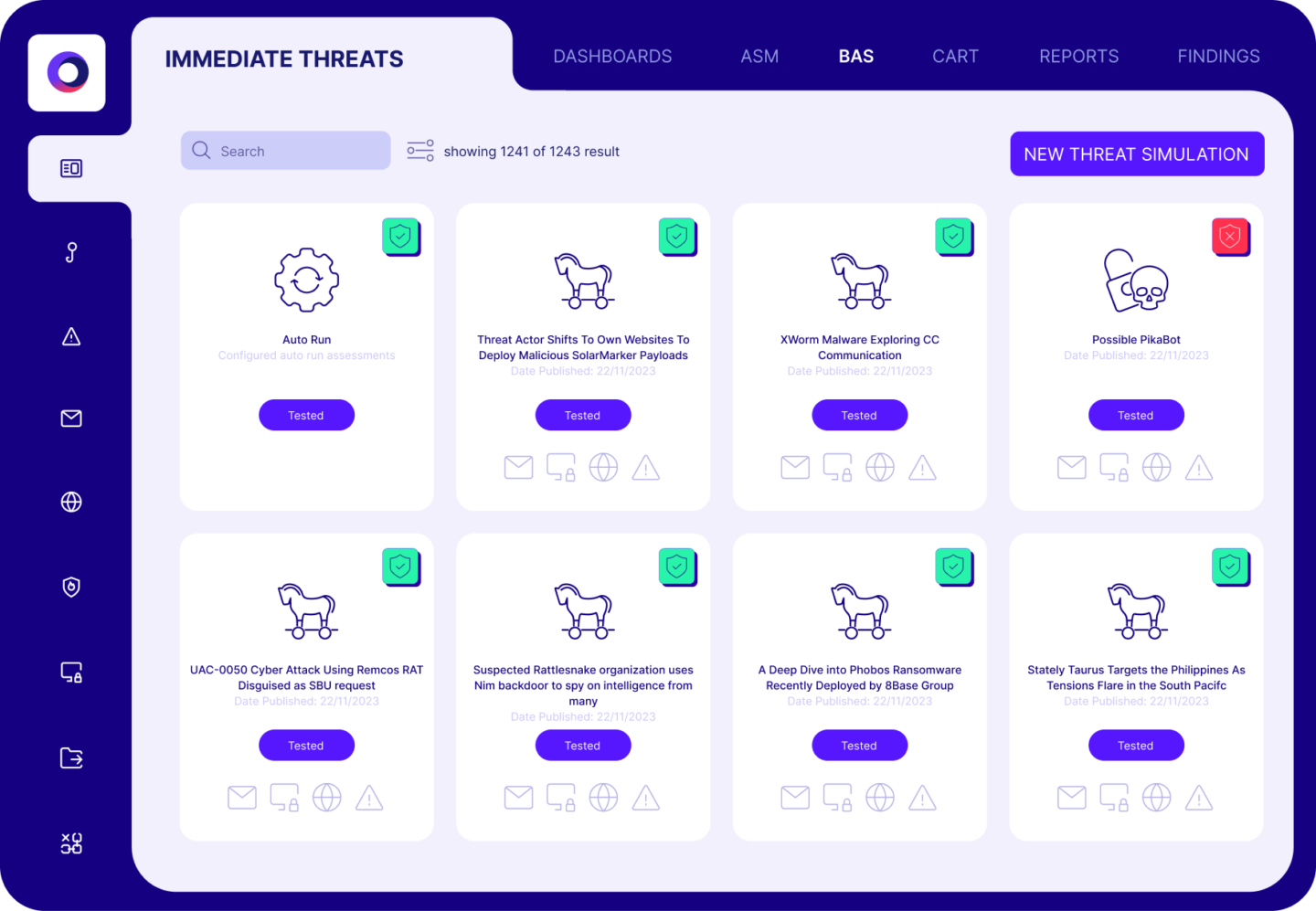
Validate Security Controls
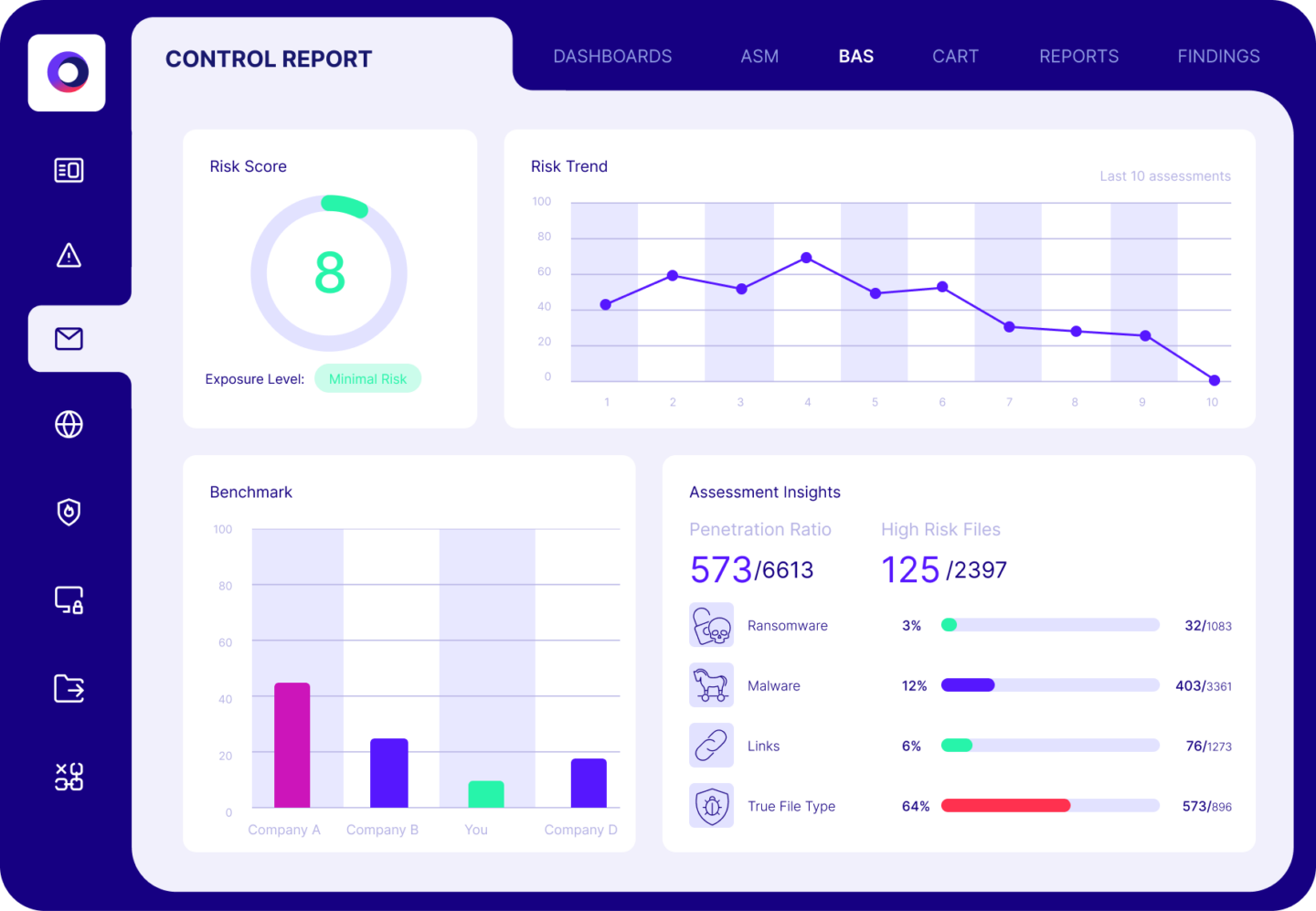
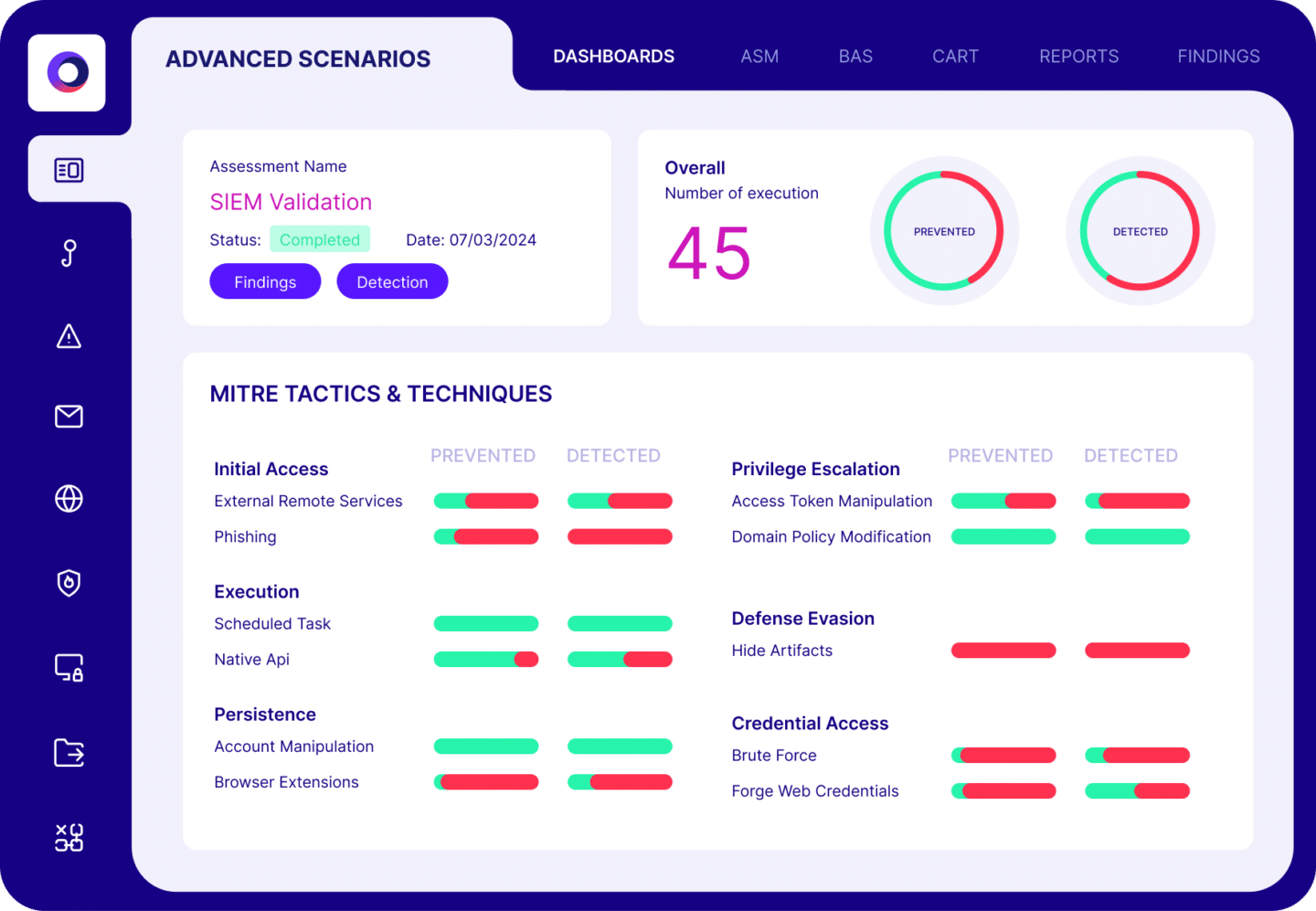
Cymulate validates security controls and hardens defenses with real-world attack simulations that identify control weaknesses. Our platform includes policy tuning guidance, automated control updates and custom mitigation rules that can be directly applied to your controls.
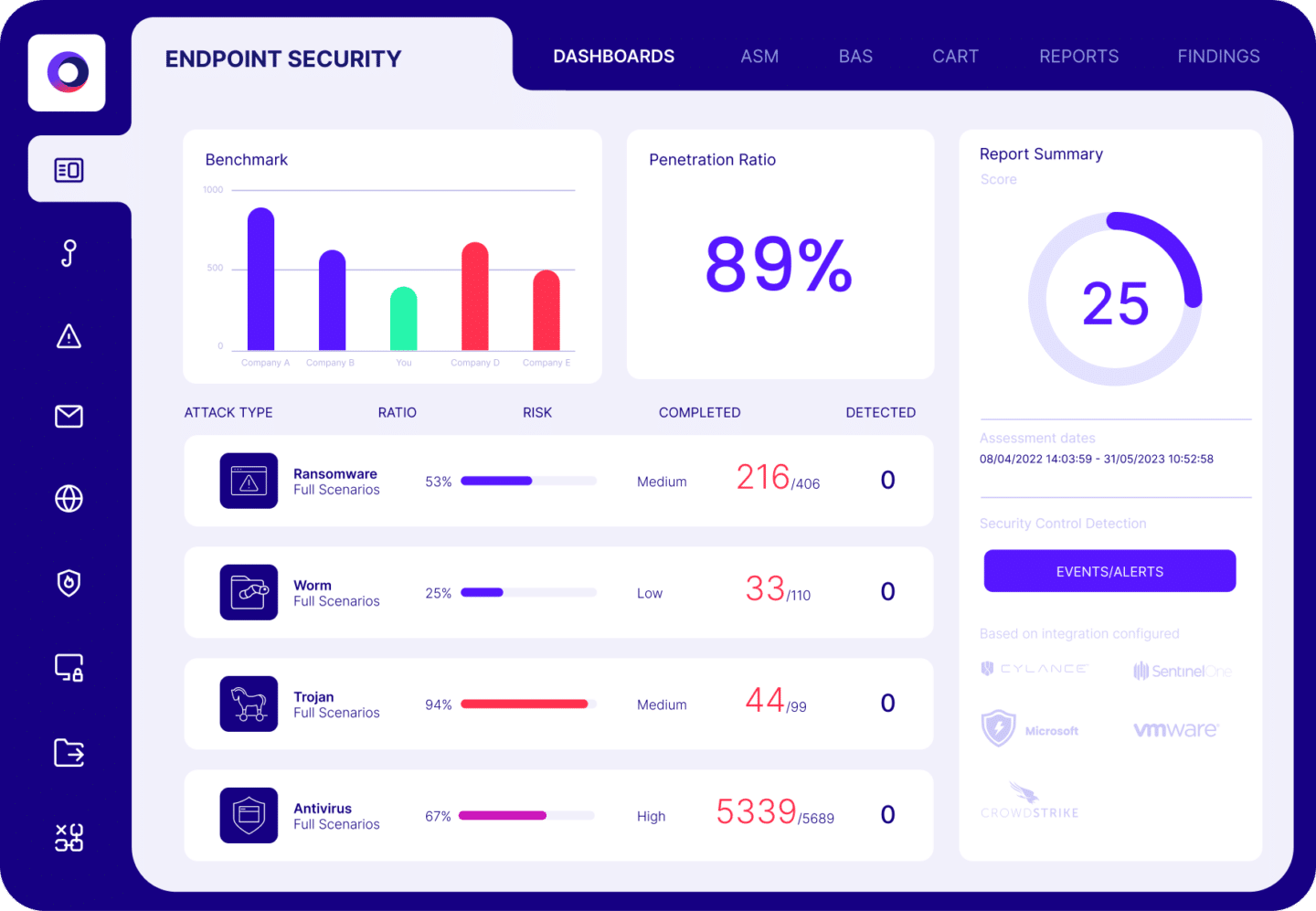
Join the gold standard for 1000+ security leaders worldwide
Test, tune and optimize your
|
Cymulate integrates with top security vendors to test and optimize the controls you already have in place. Maximize your controls. Minimize your gaps.
GET A PERSONALIZED DEMO
Ready to see Cymulate in action?
“With Cymulate, we can present quantifiable data to the board and show a direct correlation between investments and the reduction in risk.“
- Avinash Dharmadhikari, CISO, Persistent