CISO
Automate security validation to increase resilience against cyber attacks and minimize the risk of a breach.
CISOs struggle to make confident, informed decisions because they lack validated insights into the true state of their security posture.
CISOs believe they are at risk of a material cybersecurity attack
Source: Proofpoint
CISOs suspect defenses won’t withstand a sophisticated attack
Source: Cymulate TEV Impact Report
Security leaders say threat exposure validation is essential
Source: Cymulate TEV Impact Report
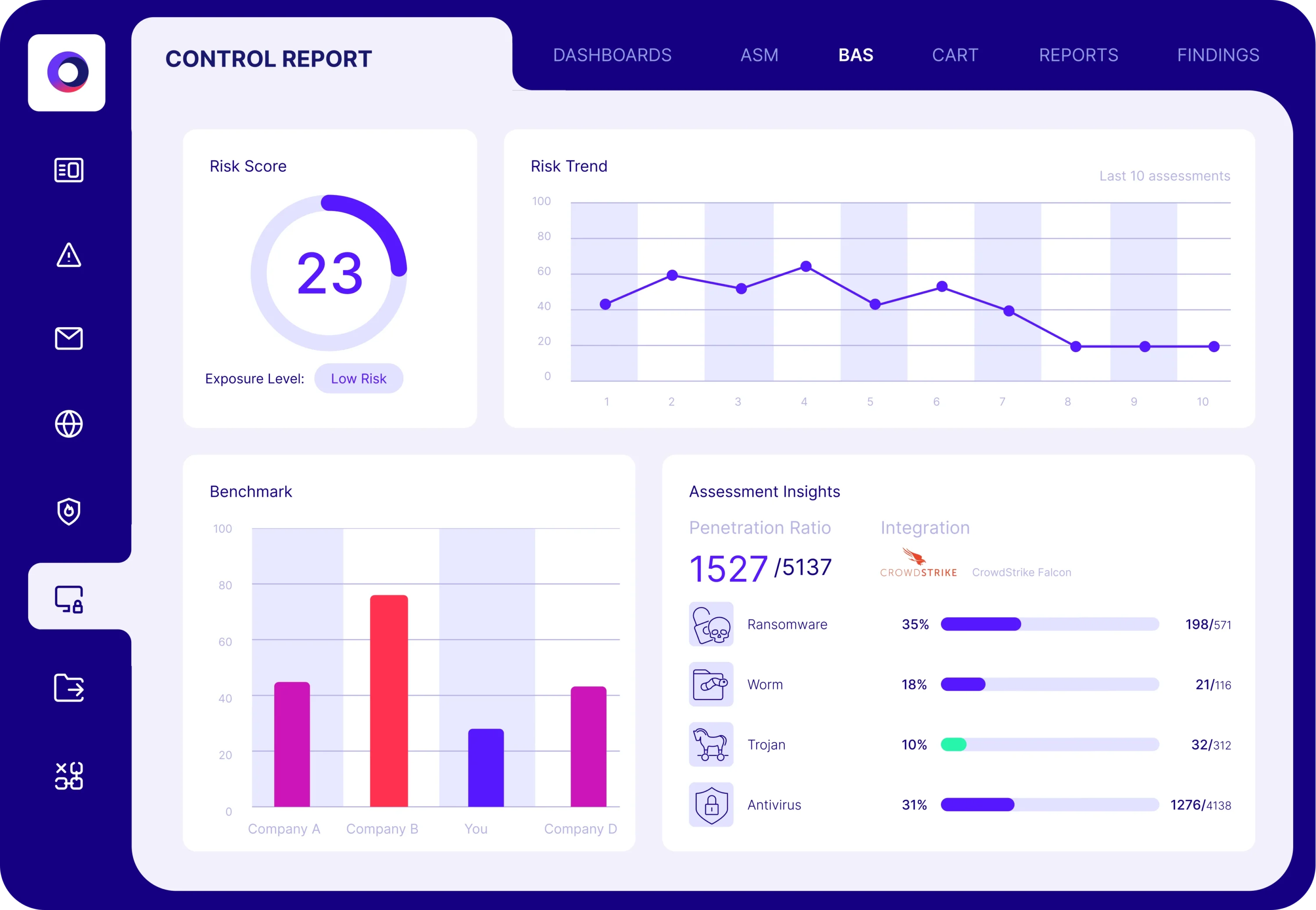
Safeguard Your Organization from Cyber Threats
The Cymulate Exposure Validation platform enables CISOs to continuously validate the state of their security program with metrics and insights to understand where they have critical exposure risk that could result in a material cyber breach.
Solution Results
81%
Improvement in security risk score in 4 months
transportation
60%
Increase in team efficiency addressing vulnerabilities
Finance
17
subsidiaries using
the same cyber metrics
manufacturing company
Solution Benefits
What our customers say about us
Organizations across all industries choose Cymulate for exposure validation, proactively confirming that defenses are robust and reliable-before an attack occurs.
CISOs FAQs
Cymulate continuously assesses an organization’s security posture using real-world attack simulations. This proactive approach identifies gaps before attacks do, so CISOs can ensure their teams optimize defenses and close gaps to enhance overall cyber resilience.
Yes. Cymulate provides measurable risk reduction metrics and control effectiveness insights over time. CISOs can use these metrics to show how their investments translate into stronger security, reduced risk and better business outcomes.
CISOs use Cymulate to track cyber resilience, return on security investments, MITRE ATT&CK and NIST coverage, industry benchmarking and more.
Yes. Cymulate compliance evidence report templates provide evidence-based validation of security controls, helping CISOs demonstrate their cybersecurity posture and alignment with key industry standards and regulatory frameworks. Each report is tailored to support compliance efforts by verifying that implemented controls are effective in preventing and detecting threats relevant to specific requirements.