Digital Operational Resiliency Act (DORA)
Increasing Resiliency Against Cyber Attacks
The Digital Operational Resilience Act (DORA) was created by the European Union (EU) to ensure that the banking and financial systems that keep our economies running and the Information and Communication Technologies (ICT) that underly them, are resilient to the risks and digital threats facing the financial sector.
Cyber attacks represent the largest area of risk for financial systems, making the testing and validation of ICT security controls for a financial institution and their third-party service providers a critical component in achieving DORA compliance.
Digital Operational Resiliency Testing
Financial institutions and their third-party providers operating within the EU are now required to develop and integrate a detailed ICT risk management framework and conduct operational resilience testing of critical ICT systems and controls to comply with the DORA regulation.
The Cymulate platform enables DORA compliance by delivering digital operational resilience testing using real-world breach and attack simulations and continuous automated red teaming for:
- ICT Security Controls
- Immediate & Emergent Cyber Threats
- Security Operational (SecOps) Response
Through frequent testing and validation of ICT security controls, immediate threats and operational response, financial institutions and providers can implement a common process of continuous testing and improvement which measures risk and exposure to cyber threats and enables the organization to achieve an acceptable level of risk given their business profile.
Security operations teams can monitor the risk and exposure level for drift based on the latest immediate threats updated daily in the Cymulate platform by our threat research team, as well as when changes are applied to the IT environment and security controls.
The findings and reports generated by the Cymulate platform provide the proof and evidence needed to show the commitment towards continuous improvement and to meet the digital operational resilience testing needs of the DORA regulation.
Digital Operational Resiliency Act (DORA) Solution Brief
Learn how the Cymulate platform provides the proof and evidence you need to achieve DORA compliance against cyber attacks.

ICT Security Control Testing and Validation
The Cymulate platform delivers production-safe testing and validation of your ICT security controls using a wide range of automated test scenarios and templates. These best practice templates can be scheduled to run on a weekly / monthly basis to perform assessments of key ICT security controls and processes including:
- Email and Web Gateways
- Web Application Firewalls
- Antivirus & Endpoint Security
- Cloud Workload & Container Security
- Lateral Movement & Data Loss Prevention
- Advanced Persistent Threat Scenarios
- Phishing
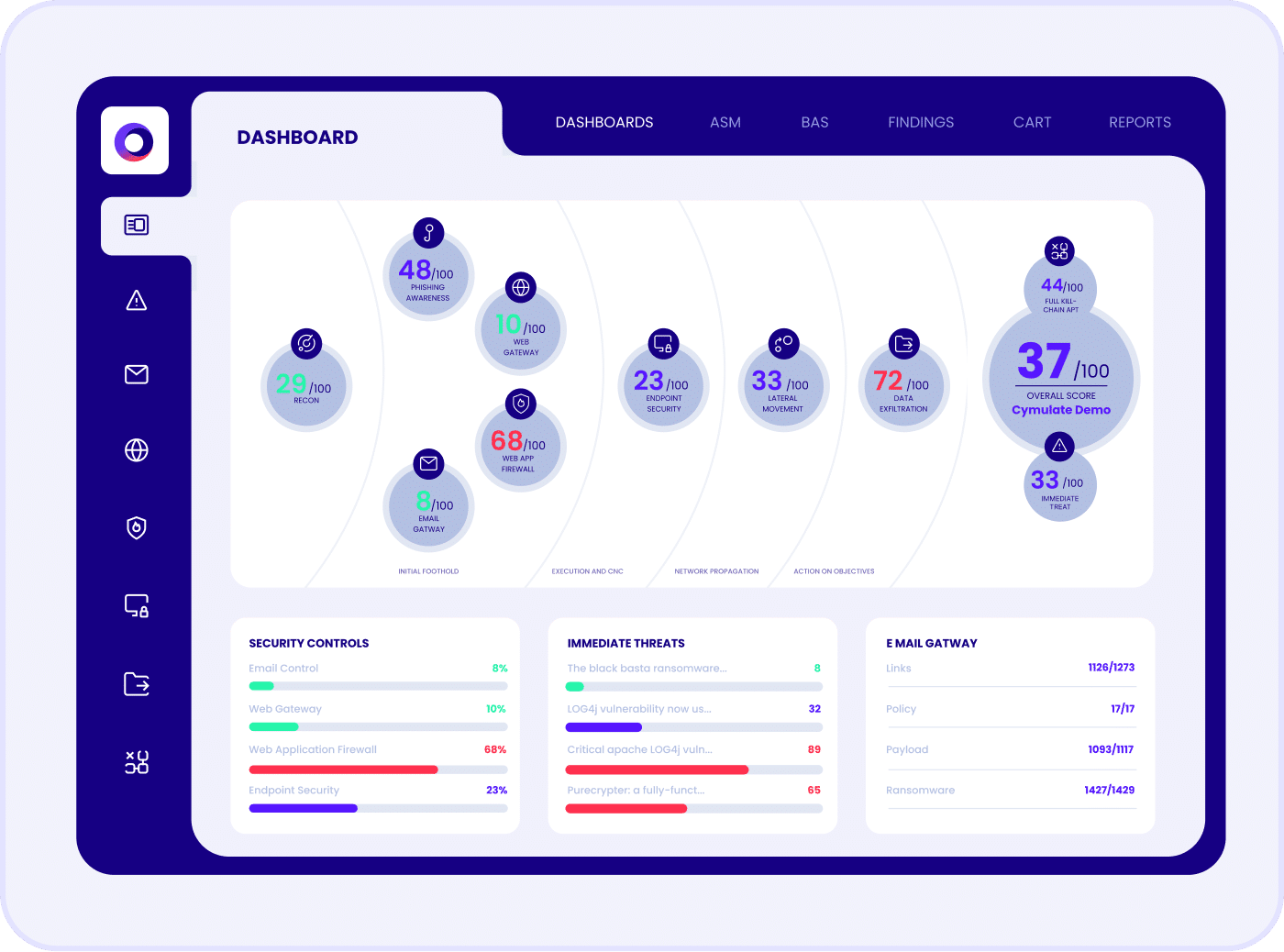
The dashboards and findings from the assessments highlight areas of risk, identifying gaps and weaknesses that could be exploited by threat actors to disrupt financial operations. The detailed findings offer mitigation guidance to configure and tune your ICT security controls to increase resiliency and lower the risk of a cyber breach. The reports provide the proof you need to achieve DORA compliance with evidence of the effectiveness of your ICT security controls to prevent and detect the latest cyber attacks.
Why Choose Cymulate?
Depth of attack simulations
Our assessments challenge every aspect of your ICT security controls with comprehensive test executions that simulate thousands of attack tactics and techniques used by today’s threat actors.
Production safe
The full suite of attack simulations and automated test executions is completely production-safe with no malicious execution that could impact financial systems in your production environment.
Automated testing
The Cymulate best practice assessments are fully automated, enabling frequent testing, validation, and optimization of your ICT security control effectiveness to improve your digital operational resilience.

