Exposure Management
Find and fix what matters most by taking an attacker’s view of what can actually be exploited.
Legacy approaches to SecOps don’t provide a true picture of an organization’s cyber resilience.
Security executives manually compile data
Source: Osterman Research
CISOs feel at risk of material cyber attack
Source: Proofpoint
Breaches involve unpatched vulnerabilities
Source: Ponemon Institute
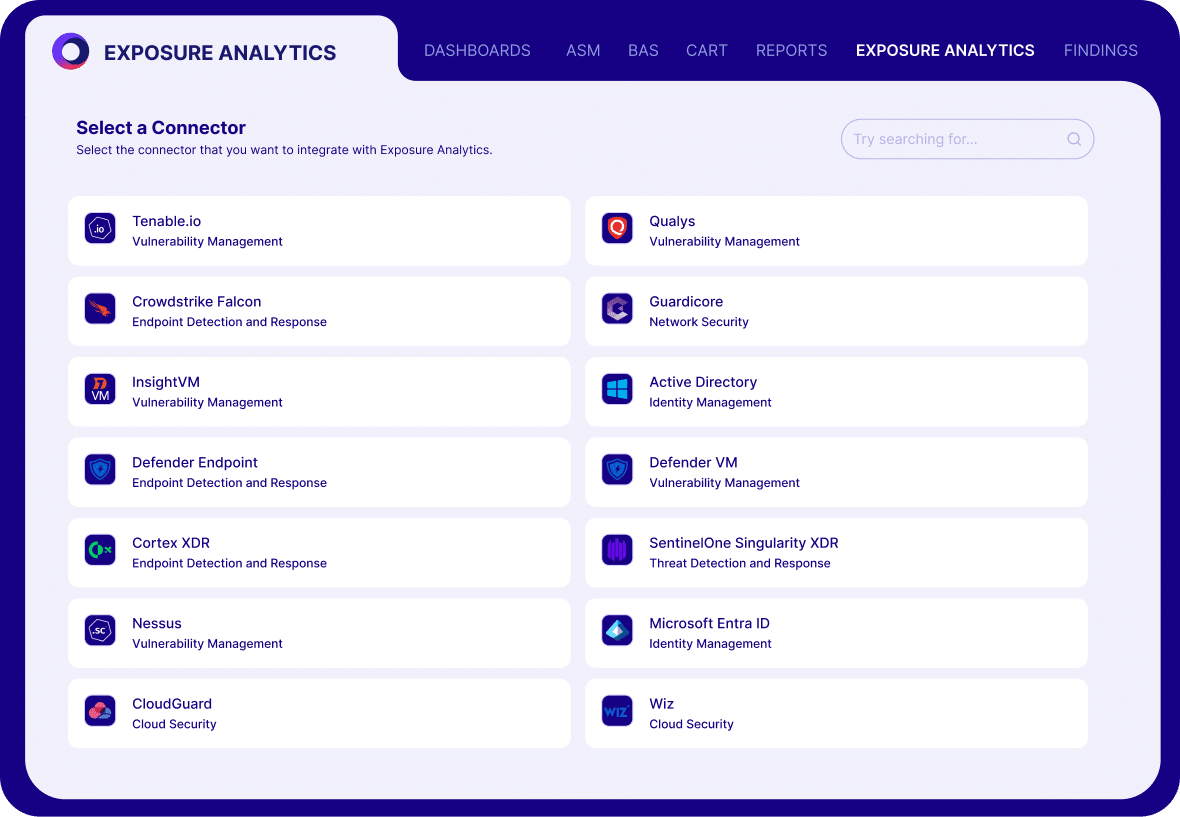
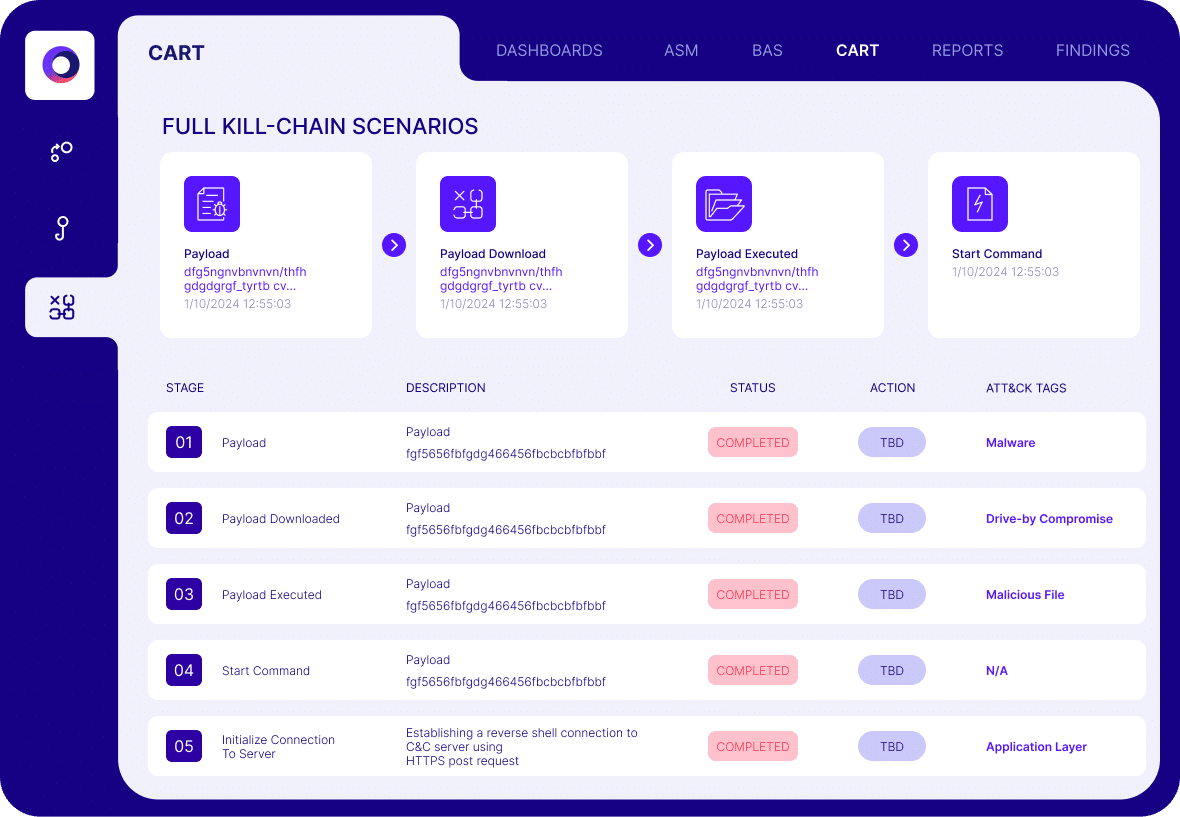
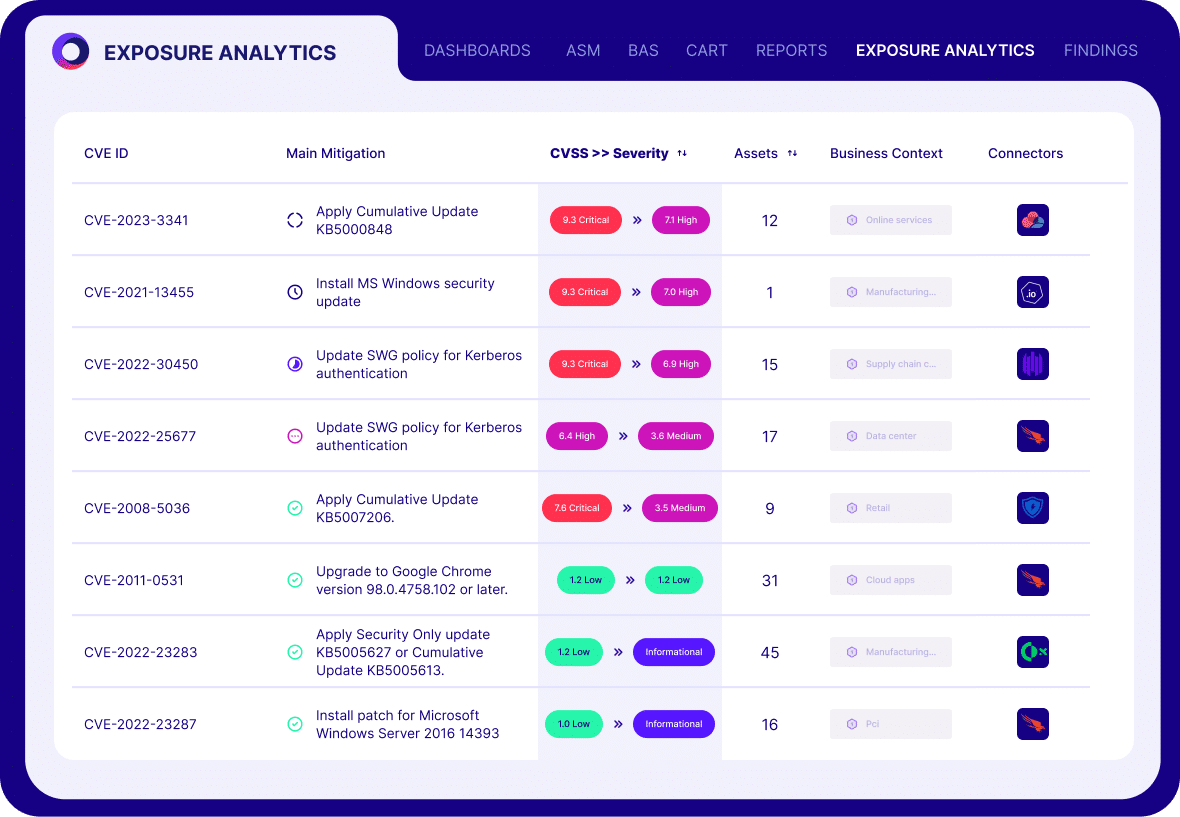
Focus on True Exposures
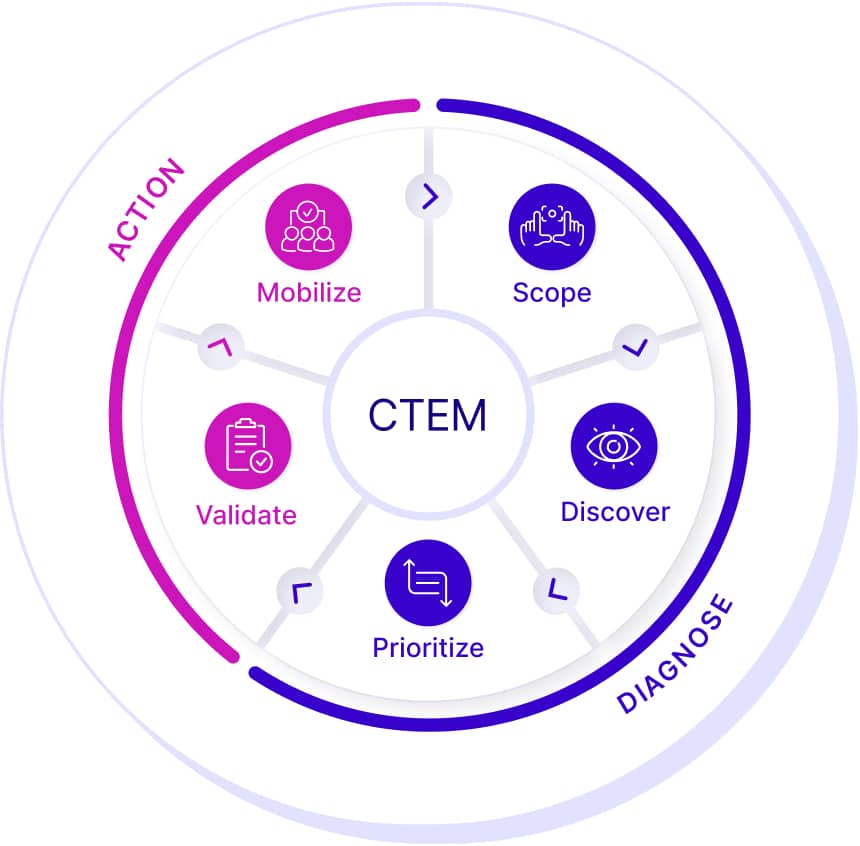
Cymulate brings best-in-class security validation to the heart of exposure analysis in a unified and open platform, which includes integrations and analysis to support every stage in the continuous threat exposure management (CTEM) process.
Solution Benefits
Results & Outcomes
81%
Improvement in risk score in 4 months
Global Transportation
168
Exploits prevented from 1 policy change
Healthcare Company
60%
Increase in efficiency patching vulnerabilities
FINANCE COMPANY
What our customers say about us
Organizations across all industries choose Cymulate to drive their exposure management programs and prioritize validated threat exposure.