Stopping Attackers in Their Tracks: Mitigating Lateral Movement with IAM and Network Segmentation

When attackers gain an initial foothold, their next step is propagating in the network toward the organization’s crown jewels. To move laterally, the attacker must gain privileges and leverage network connectivity.
Attackers apply a number of proven techniques to achieve that goal of lateral movement. This blog highlights a few common techniques for lateral movement as well as recommendations to prevent attackers from using them to achieve their goals.
Access Token Manipulation
Windows uses access tokens to determine the ownership of a running process. A user can manipulate access tokens to make a running process appear to belong to someone other than the user who started the process. When this occurs, the process also takes on the security context associated with the new token. For Example, Microsoft promotes using access tokens as a security best practice. Administrators should log in as a standard user but run their tools with administrator privileges using the built-in access token manipulation command “runas”.
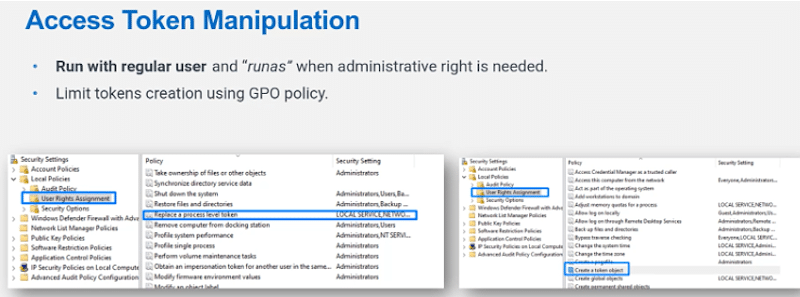
For more information, see https://attack.mitre.org/techniques/T1134/
Pass the Hash
Adversaries may “pass the hash” using stolen password hashes to move laterally within an environment, bypassing normal system access controls. Pass the hash (PtH) is a method of authenticating as a user without having access to the user’s cleartext password. This method bypasses standard authentication steps that require a cleartext password, moving directly into the authentication segment that uses the password hash.
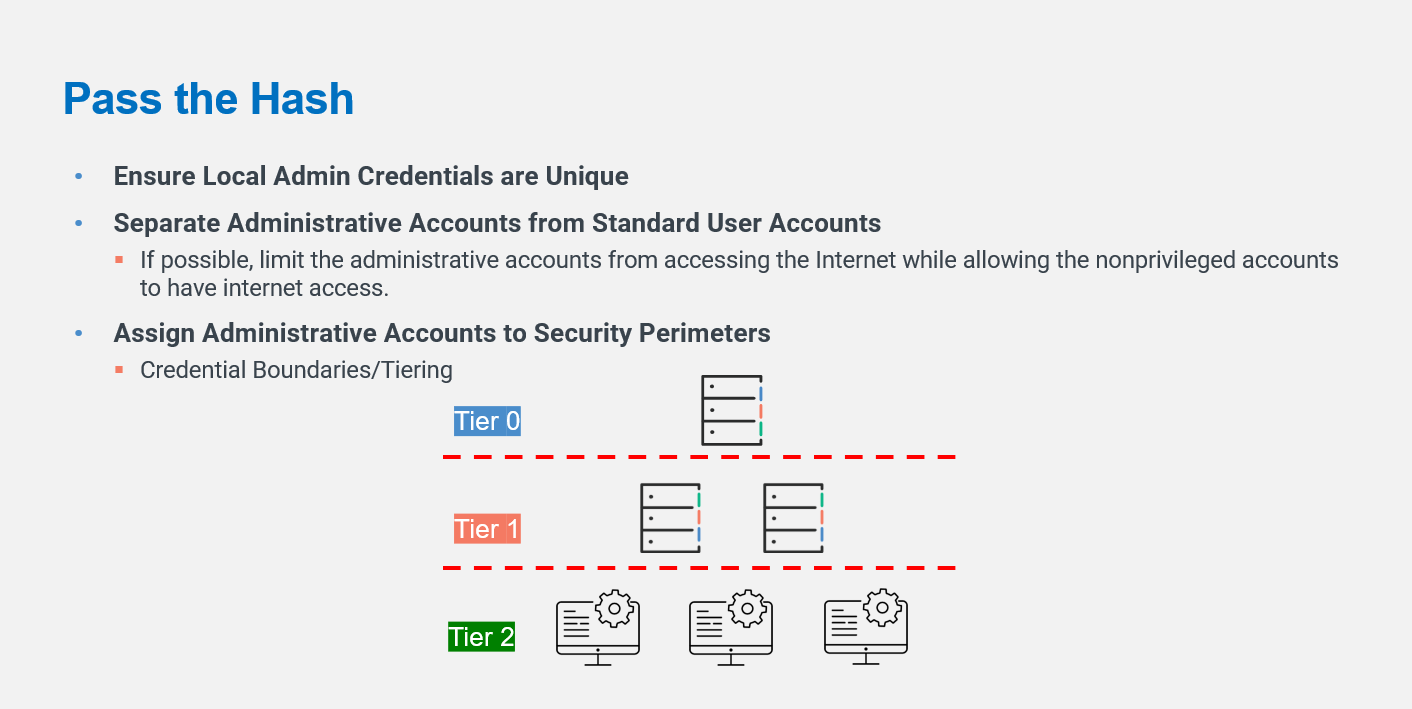
For more information, see https://attack.mitre.org/techniques/T1550/002/
Kerberoasting
Adversaries may abuse a valid Kerberos ticket-granting ticket (TGT) or sniff network traffic to obtain a ticket-granting service (TGS) ticket that may be vulnerable to Brute Force.
Service principal names (SPNs) are used to identify each instance of a Windows service. To enable authentication, Kerberos requires SPNs to be associated with at least one service logon account (an account specifically tasked with running a service). Adversaries possessing a valid Kerberos ticket-granting ticket (TGT) may request one or more Kerberos ticket-granting service (TGS) service tickets for any SPN from a domain controller (DC).
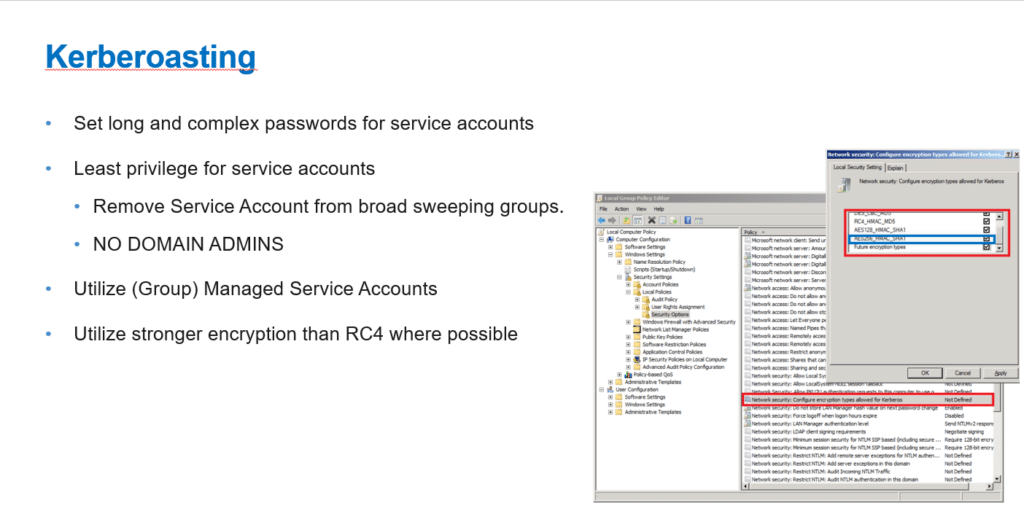
More information, see https://attack.mitre.org/techniques/T1558/003/.
LLMNR Poisoning
By responding to LLMNR/NBT-NS network traffic, adversaries may spoof an authoritative source for name resolution to force communication with an adversary-controlled system. This activity may be used to collect or relay authentication materials.
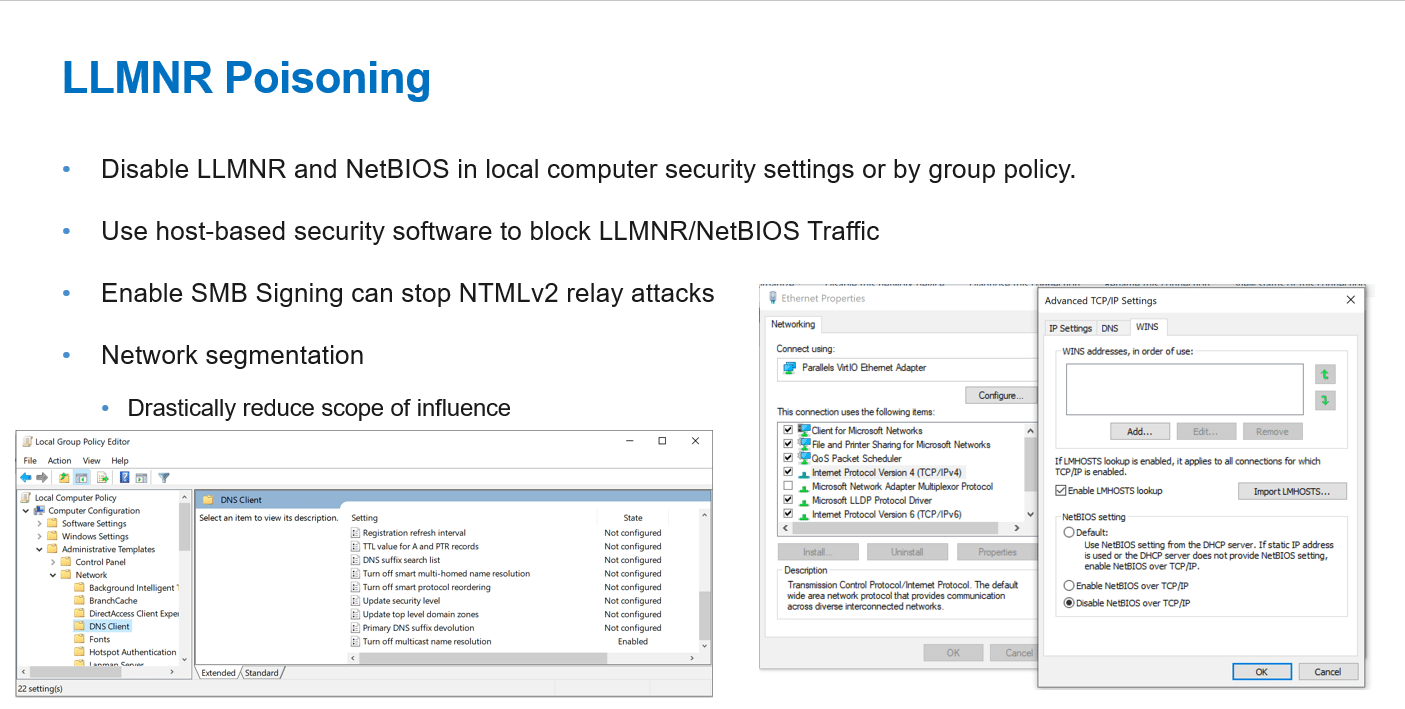
For more information, see https://attack.mitre.org/techniques/T1557/001/
Robust IAM programs Management) programs, specifically PAM (Privileges Access Management) and network segmentation, are the foundations of lateral movement defense.
Here are some foundational recommendations for privileged access management (PAM) and identity and access management (IAM) programs in a large-scale enterprise:
- Define the scope of the program: Determine the specific systems, applications, and data that the PAM and IAM programs will cover. Identify the critical assets that require the highest level of protection.
- Establish policies and procedures: Develop policies and procedures that address access control, password management, authentication, and authorization. These policies should align with industry best practices and regulatory requirements.
- Conduct a risk assessment: Conduct a comprehensive risk assessment to identify vulnerabilities and risks associated with privileged access and user access to enterprise systems and data.
- Implement least privilege: Enforce the principle of least privilege by restricting access to only what is necessary for each user and application. Implement role-based access control (RBAC) to ensure users can access only the resources they need to perform their job functions.
- Use multi-factor authentication (MFA): Implement MFA to provide an additional layer of security to protect against unauthorized access. MFA should be used for privileged users as well as regular users.
- Implement monitoring and reporting: Implement real-time monitoring and reporting to detect and respond to suspicious activities. This includes monitoring user activity logs, access attempts, and system changes.
- Conduct regular training and awareness: Educate employees on the importance of PAM and IAM and their role in ensuring the security of enterprise systems and data. Conduct regular training and awareness programs to ensure employees understand their responsibilities and are aware of the latest threats and vulnerabilities.
- Regularly review and update the program: Conduct regular reviews of the PAM and IAM program to ensure it remains effective and aligns with the evolving threat landscape and changing business requirements.
By implementing these foundational recommendations, a large-scale enterprise can establish a strong PAM and IAM program to protect its critical assets and ensure the security of its systems and data.
A robust network segmentation plan can help protect your organization’s critical assets from potential security threats by following these recommendations:
- Identify Critical Assets: The first step in any network segmentation project is identifying the critical assets that need protection. This can include data centers, servers, applications, and other sensitive resources. Once you have identified these assets, you can create policies limiting access exclusively to authorized users.
- Design a Segmentation Plan: After identifying the critical assets, the next step is to design a segmentation plan. This plan should divide the network into smaller, more manageable segments. Each segment should have its own security policies and controls, and access should be limited based on business needs.
- Implement Access Controls: Once the segmentation plan is in place, it’s essential to implement access controls to ensure that only authorized personnel can access each segment. This can include using firewalls, VLANs, and other security technologies to control access and enforce policies.
- Monitor and Maintain Segmentation: Network segmentation is not a one-time project. Monitoring and maintaining segmentation regularly is essential to ensure that segmentation is still effective and up-to-date. This can include regular security audits, vulnerability scans, and penetration testing.
- Use Security Information and Event Management (SIEM): SIEM tools can provide visibility into network activity, helping to detect potential security threats. Integrating SIEM into your network segmentation plan lets you quickly detect and respond to security incidents.
- Train Employees: Lastly, it’s crucial to train employees on network security best practices, including how to follow access control policies, avoid phishing attacks, and report any suspicious activity. Regular training can help ensure that everyone in the organization is on the same page when it comes to network security.
Validating the efficacy of those pre-emptive measures can be done by using automated lateral movement technologies such as Cymulate Continuous Automated Red Teaming (CART) with its Hopper module that simulates an attacker that has gained an initial foothold and moves laterally in search of any additional assets that can be compromised.
To learn more about testing for lateral movement, watch the webinar Building a Real Worm For Good.
Watch the webinarFeatured Resources
Subscribe to Our Blog
Subscribe now to get the latest insights, expert tips and updates on threat exposure validation.