CISA Alert – Is Your Organization Exposed?
Cybersecurity is no longer a luxury, it’s a necessity with new threats emerging every day. Every day the Cybersecurity and Infrastructure Security Agency (CISA) issues new CISA alerts warning people of the latest cyber threat activity. But how do you know if your organization is exposed to these new threats? And equally as important, how confident are you that your cybersecurity defenses can withstand these latest attacks? It’s important not to guess whether your business has is fully prepared to handle an attack but rather to simulate real-world attacks and validate.
The Challenges of Emerging Threats
With cybercriminals becoming just as sophisticated as the technology used today, the threats adversaries deploy become more targeted and invasive. Organizations must be more adaptable than ever to keep pace with the growing number of threats, from ransomware to zero-day vulnerabilities. There are three top reasons emerging threats pose such a challenge:
- Speed of evolution: Cybercriminals are moving at the same pace as the cybersecurity industry, if not faster of refining their tactics to discover new weaknesses. This means organizations are likely and often behind and unable to patch or defend against them in real-time.
- Advanced attack techniques: With today’s attacks being more advanced, involving multi-layered, including phishing, social engineering and supply chain compromises, it makes traditional defense methods like firewalls and antivirus software easily penetrable.
- Resource constraints: Cybersecurity budgets and resources are consistently fought for, which leaves small and mid-sized businesses often lacking the resources and technical experts they need to stay ahead of new threats. As a result, they may find themselves inadequately prepared for emerging risks and exposed to an attack.
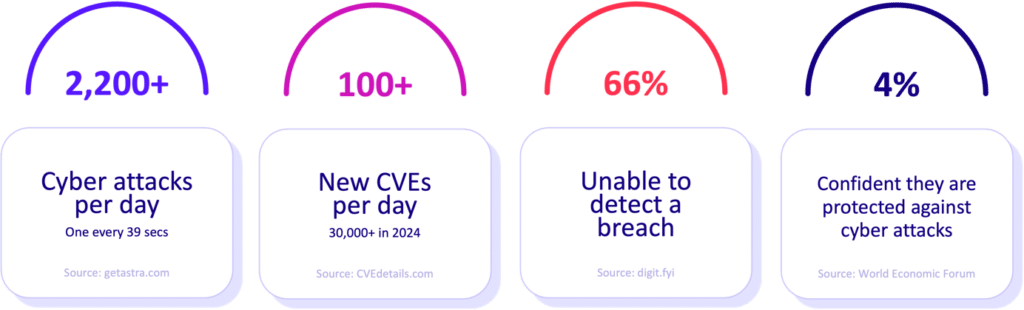
Recent Notable Threat Activity Reported by CISA
Alerts about imminent risks are provided by CISA, who continuously monitors the cyber threat landscape. There have been several high-profile attacks recently, that have highlighted the urgency for organizations to take steps quickly and decisively. These include:
Iranian Cyber Threat Compromises Critical Infrastructure Organizations:
- Alert code: AA24-290A, release date: October 16, 2024
- This alert focused on a nation-state threat actor targeted critical infrastructure using espionage for political gains.
Akira Ransomware:
- Alert code: AA24-109A, release date: April 18, 2024
- This alert focused on an eCrime threat group (aka Punk Spider) that used data exfiltration and double extortion tactics to gain access to 250 organizations and extort $42 million in ransom payments.
Respond to CISA Alerts with Confidence
The best way to answer CISA’s alerts with confidence is to proactively assess your organization's exposure to the latest threats. But how can you truly know whether your defenses are up to the task?
Move beyond theoretical assessments and take a more practical approach. Rather than relying solely on speculative analysis of threat intelligence, organizations should adopt a simulation-driven defense strategy.
The Solution: Don’t Speculate, Simulate
A simulation-driven approach involves testing your organization’s defenses under realistic attack scenarios, allowing you to gain a real-world understanding of how your security measures would hold up in the face of emerging threats. Rather than guessing whether your organization is vulnerable, simulate actual cyberattacks, testing both your technical defenses and your incident response capabilities.
Here are some key advantages of using simulations:
- Realistic threat scenarios: By simulating attacks based on the most recent threat intelligence, you can test how your organization would respond to specific, real-world attack methods. For example, simulating a ransomware attack that exploits a recently disclosed vulnerability can show you if your patch management processes are effective.
- Identifying weaknesses: Simulations reveal the blind spots in your cybersecurity strategy. Perhaps your incident response plan needs refinement, or your team isn’t aware of the latest tactics used by threat actors. Attack simulations provide the visibility necessary to close these gaps.
- Improving team readiness: A well-conducted simulation exercise can help your security team practice and hone their skills in a controlled environment. This builds muscle memory for dealing with real attacks, improving response times and decision-making under pressure.
Validate Exposure to Immediate Threats
To effectively validate your exposure to the most immediate threats, organizations should incorporate threat simulation exercises as part of their regular security protocols. This means:
- Tracking CISA alerts: Stay informed about the latest alerts and threat advisories from CISA. These provide crucial information about the most urgent risks and vulnerabilities currently affecting the cybersecurity landscape.
- Conduct regular risk assessments: Assess the impact of the vulnerabilities identified in the latest CISA reports. Do you have these vulnerabilities in your environment? Are they being actively exploited in the wild?
- Perform penetration testing: Work with cybersecurity experts to simulate attacks specific to the threats identified in recent CISA advisories. This will help you understand if attackers could exploit those vulnerabilities in your network.
Create Attack Simulations for Emerging Threats
To create effective attack simulations that mirror emerging threats, follow these best practices:
- Leverage threat intelligence: Ensure that your simulations are based on the most up-to-date threat intelligence. This includes understanding the tactics, techniques, and procedures (TTPs) used by the latest threat actors, as outlined in CISA’s alerts.
- Incorporate real-world scenarios: Build simulations that mirror the methods being used in actual cyberattacks. If CISA issues an alert about a new ransomware campaign, simulate that specific type of attack, focusing on the attack vector, encryption methods, and lateral movement techniques used by attackers.
- Test across the entire organization: Don't limit simulations to just the IT team. Involve other stakeholders, including your C-suite, human resources, and legal teams. Cybersecurity is an organization-wide responsibility, and preparing all departments for potential breaches ensures a coordinated response when an actual incident occurs.
- Repeat and improve: After each simulation, debrief your team, identify weaknesses, and refine your security measures. These exercises are not one-time events but part of a continuous improvement cycle.
Key Takeaways
With the increasing frequency of cyberattacks and the rise of new threat vectors, the time for speculation has passed. To truly assess your organization’s exposure to emerging threats, you must simulate real-world attacks. By regularly testing your defenses, validating your vulnerability management strategies, and ensuring that your response teams are prepared, you can face the latest cyber threats with confidence.
CISA alerts provide valuable early warnings, but it’s up to your organization to take those alerts seriously and act decisively. Don’t wait for a breach to reveal your vulnerabilities. By simulating the threats you face today, you’ll be ready for whatever tomorrow’s cybersecurity challenges may bring.
To learn more about how to be alert ready, watch our latest webinar here.



