Web Gateway Validation
Test and optimize your secure web gateway against the latest
web-based threats.
Most malware is delivered via the web and email, making secure gateways essential protection.
Web URLs link to
malicious sites
Source: Cloudflare
Web traffic
originates from bots
Source: Cloudflare
Malware distributed
via the web
Source: Expert Insights
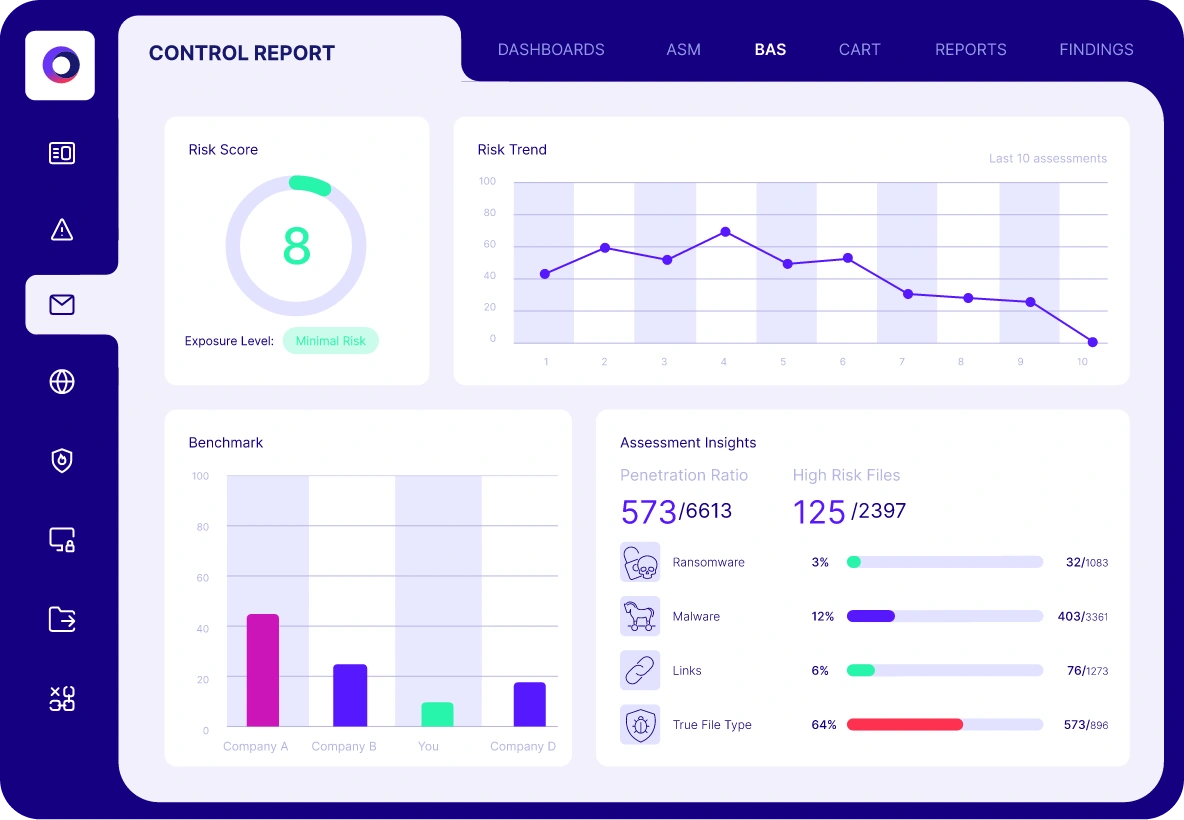
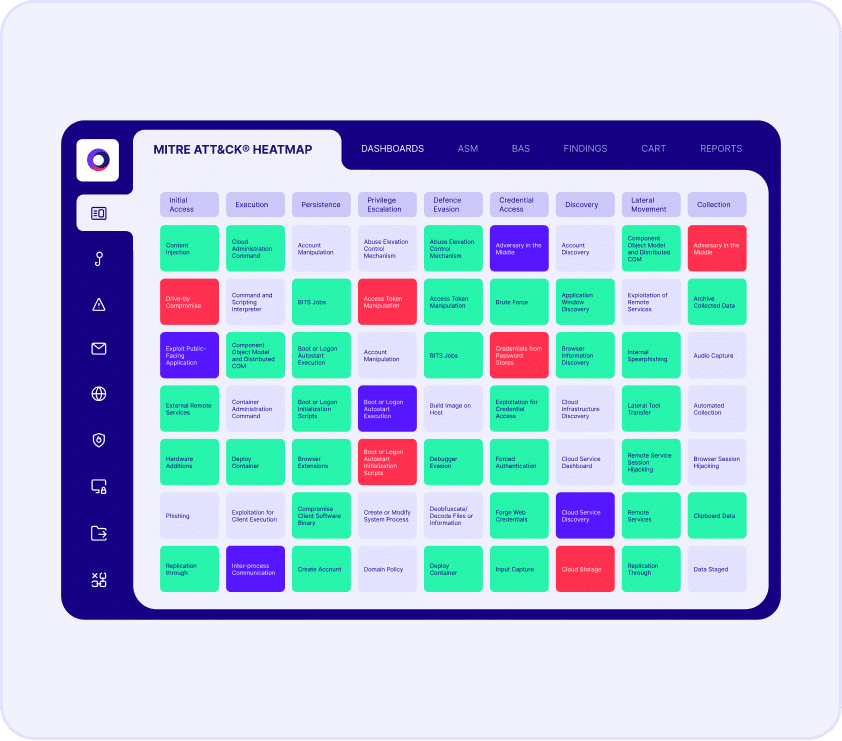
Web Gateway Assessment
Cymulate uses breach and attack simulations to assess the efficacy of your web defenses. The automated security validation simulates different types of web-based threats and malicious content to validate the effectiveness of your secure web gateway, including:
Inbound validation
- Malicious payloads (files)
- File policies
Outbound validation
- Malicious links
- URL category policies
Solution Results
81%
Improvement in malicious
file detection
91%
Improvement in malicious file
detection post mitigation
50%
Prevention of known exploit techniques from a single policy change
Solution Benefits
What our customers say about us
Organizations across all industries choose Cymulate for automated security validation, proactively confirming that defenses are robust and reliable-before an attack occurs.