Security Controls
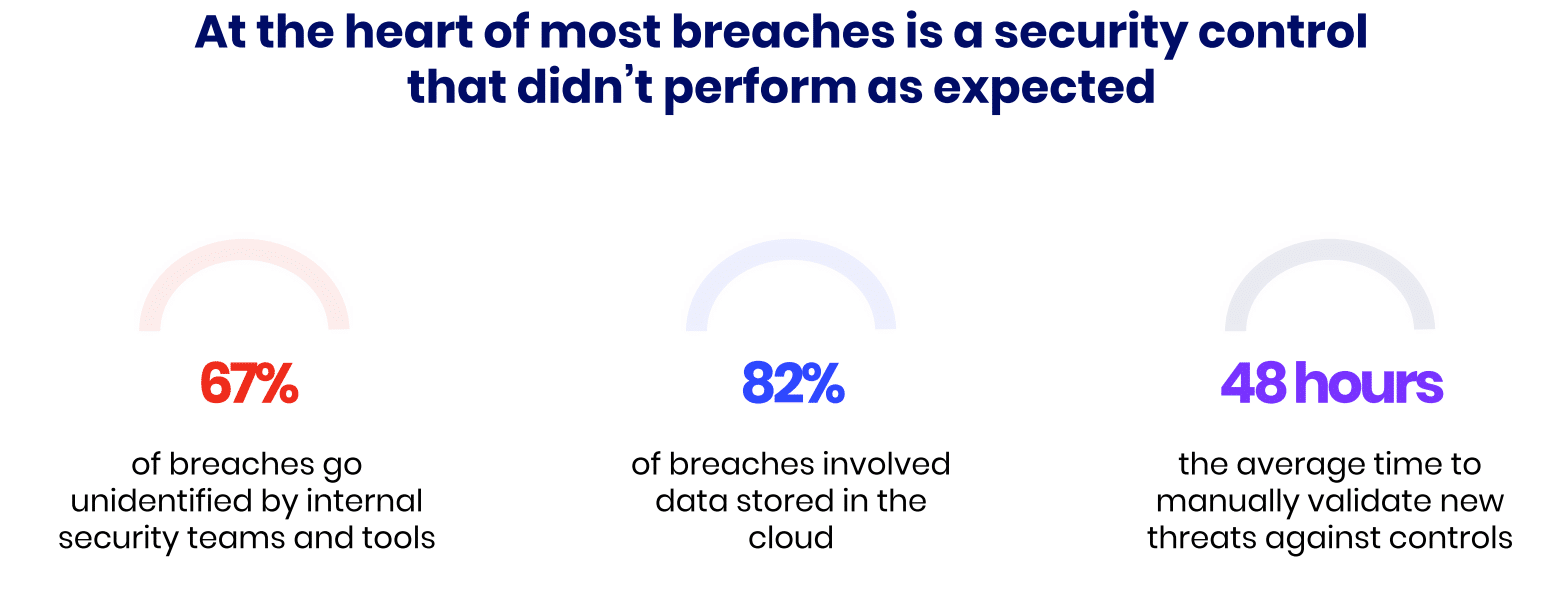
Security controls are essential measures for helping organizations reduce the risk of potential breaches that could lead to sensitive data and information being exposed. Behind most successful breaches, there was a security control that didn’t perform as expected. This is why continuously validating the effectiveness of security controls is just as important as having them in place.
What are security controls?
Security controls refer to any measure an organization puts in place to reduce the risk of breaches to information, systems, data and other infrastructure. They are designed to protect the confidentiality, integrity and accessibility to information by preventing, detecting and responding to a constantly evolving number of security threats.
Security controls can be anything from physical controls such as access cards to an office environment, to cyber security controls such as email and web gateways, firewalls, intrusion prevention and data loss prevention. Each control serves a different purpose in the organization's security strategy.
Different types of security controls
In the cyber realm, security controls are categorized based on their functions, the stage where they are implemented, and their main purpose. The primary types are:
| Preventative | Detective | Corrective | Compensating | Deterrent | Administrative | Physical |
| Email filtering, secure email gateway (SEG) | Security information & event management (SIEM) | Security orchestration, automation, and response (SOAR) | Multi-factor authentication (MFA) | Warning banners | Employee training | Building access control |
| Secure web gateway (SWG) | Intrusion detection system (IDS) | Patch management | Virtual private network (VPN) | Disclaimers | Phishing testing | CCTV |
| Web application firewalls (WAF) | Log management | Vulnerability management | Legal contracts and policies | |||
| Antivirus (AV) | Honeypots | Secured, encrypted, and tested backups | ||||
| Endpoint detection and response (EDR) | Incident response plans and playbooks | |||||
| Cloud workload protection (CWPP) | ||||||
| Encryption and system hardening | ||||||
| Data loss prevention (DLP) | ||||||
| Identity / privileged access management (IAM/PAM) |
Preventative controls
- Main objective: Preventing security breaches from occurring
- Examples: Email and web gateways, firewalls, anti-malware software, encryption, endpoint and cloud workload protection
Detective controls
- Main objective: Identify and detect lurking security breaches or anomalies
- Examples: Intrusion detection systems, security information and event management systems (SIEM), audits
Corrective controls
- Main objective: Mitigate damage and restore systems after a breach
- Examples: Incident response plans, system backups, patch management
Deterrent controls:
- Main objective: Discourage attacks
- Examples: Security policies, displayed warnings, legal disclaimers
Compensating controls
- Main objective: Provide an extra layer of protection in addition to other controls
- Examples: 2-step verification processes such as password + authenticator application, VPNs, network segmentations
Additionally, physical controls such as server rooms and surveillance cameras are forms of security measures that organizations can implement to reduce the risk of a breach. Employee cyber security training and awareness, so-called administrative controls, are also an important part of maintaining a strong security posture.
What are the main objectives of security controls?
The overall goal of any security measure is to prevent breaches that could lead to data loss, financial damage, reputational harm, or disruption of services. Security controls are put in place to ensure the following:
- Confidentiality: Ensuring that sensitive information is accessible only to those authorized to access it, preventing unauthorized disclosure of data.
- Integrity: Maintaining the accuracy and reliability of data by protecting it from unauthorized modifications or tampering.
- Availability: Ensuring that information, systems, and services are accessible to authorized users when needed, preventing disruptions due to attacks like Denial of Service (DoS).
- Accountability: Ensuring that actions within the system can be traced back to the responsible party. This is achieved through logging, monitoring, and audit trails, which help detect and respond to unauthorized activities.
- Compliance: Ensuring that the organization meets all regulatory and legal requirements related to security and privacy. This involves implementing controls that align with standards and frameworks such as GDPR, HIPAA, PCI DSS, DORA or ISO 27001.
- Risk Management: Reducing the overall risk to the organization by identifying potential threats and vulnerabilities and implementing controls to mitigate them. The objective is to lower the likelihood and impact of security incidents.
- Resilience: Building the capacity to respond to and recover from security incidents. This includes having incident response plans, disaster recovery plans, and business continuity measures in place to ensure that the organization can continue to operate in the face of disruptions.
The importance of testing the effectiveness of security controls
Having security controls in place doesn’t mean your cyber security is under control. Many major breaches occurred even after organizations invested heavily in security measures, only to find out that those controls failed when needed most.
To ensure that the security measures put in place are performing as intended, it's crucial to test and validate their effectiveness on an ongoing basis. The most common methods for testing security controls include:
- Penetration Testing: A simulated attack by ethical hackers to see if malicious threat actors can penetrate the security controls that are in place. Penetration testing mimics the tactics, techniques, and procedures (TTPs) of real-world attackers, and are usually performed at a set point in time or related to a specific known threat.
- Red Teaming: This method goes beyond standard penetration testing by simulating a full-scale attack, often over an extended period, to test how well an organization’s security posture can detect, mitigate, and recover from an attack.
- Vulnerability Scanning: Regularly scanning systems for vulnerabilities helps ensure that security controls are up-to-date and effective against current threats.
- Automated Security Validation: Tools like breach and attack simulation (BAS) platforms continuously test and validate the effectiveness of security controls by simulating attacks in real-time. These platforms provide ongoing assessments, allowing organizations to quickly identify and address potential weaknesses with their security controls
Offensive testing
Security control validation is quickly becoming the preferred method for testing the effectiveness of security controls, as it provides a comprehensive and continuous approach, unlike traditional methods such as penetration testing that might only offer a snapshot of your security posture at a single point in time pertaining to a specific threat.
With security control validation, organizations can test that their defenses are consistently effective against a rapidly evolving threat landscape. This method doesn’t only identify potential weaknesses, but also provides actionable insights that can be used to improve the overall security posture.
By validating security controls regularly, organizations can proactively detect vulnerabilities before they are exploited rather than reacting to breaches after the fact. Automated security validation tools like Breach and Attack Simulation can simulate a wide range of attack scenarios, offering a more thorough and dynamic security assessment than manual testing methods.
Key takeaways
Effective security controls are the backbone of an organization’s defenses against the ever-expanding number of cyber threats. These controls, ranging from firewalls and VPNs to physical measures like surveillance cameras, protect the confidentiality, integrity, and availability of critical information and systems.
However, simply having security controls in place is not enough; they must be continuously tested and validated to verify they function as intended to avoid a potential breach. This proactive approach helps organizations stay ahead of potential threats and adapt to the ever-changing cybersecurity landscape.


