How to Take an Attacker’s View of Cybersecurity

It might be a cliché to say that attackers only need one successful attempt, while defenders must be right every time, but reality supports this – with some exceptions. Defenders must do at least one right thing every time, with layered defenses and compensating controls. To deal with this, defenders need to shift their focus and think like attackers to better identify exposure and counter potential threats.
Adopting a proactive security approach that automates various aspects of attack simulations identifies exposure risks such as software vulnerabilities, policy misconfigurations, unmonitored assets, and more – before attackers attempt to exploit them.
This blog post looks into four approaches designed to take an attacker’s view of an organization’s security posture and cyber resilience:
- Attack surface management (ASM)
- Breach and attack simulation (BAS)
- Continuous automated red teaming (CART)
- Exposure analytics
What are the Four Approaches to Take an Attacker’s View?
ASM scans organizations' assets to identify potentially exploitable systems, platforms, and configurations.
It involves the systematic review of risks associated with an organization's digital presence, including Internet-facing systems, cloud services, and other digital assets. ASM is divided into two main categories:
- External Attack Surface Management (EASM) - EASM emulates an attacker's reconnaissance phase by scanning domains, subdomains, IPs, ports, and more using Open-Source and commercial intelligence to discover exploitable Internet-facing assets.
- Internal Attack surface Mangement (IASM) - IASM is a non-intrusive scan that identifies assets, domains, cloud configurations, and other possible points of attack within a controlled on-prem, cloud, or hybrid infrastructure. This is indispensable in ensuring that no asset is unmonitored or holds the potential for being used as an intrusion point or a stepping stone to propagate one.
BAS safely simulates cyber-attacks on systems and networks to identify weaknesses in an organization’s security controls and protocols. BAS helps organizations proactively identify security gaps before an attack occurs so they can be better prepared to defend against real-world threats by closing those gaps and/or preparing to deal with a potential incursion.
CART automates direct attack testing to identify potential attack paths from an initial attack point through actions on objectives against critical systems and data. When optimally set, it is the closest approximation of having an in-house pen tester capable of working on demand.
Exposure analytics aggregates data from across enterprise IT, clouds, and the tools within a security stack to create risk-profiled asset inventories, measure and baseline cyber resilience, focus on the biggest risks, and accelerate mitigations. By identifying risk as it applies to business contexts, both the technology and business stakeholders can work together to overcome discovered issues.
BAS, CART, ASM, and Exposure Analytics: Contributions to a Cybersecurity Strategy
ASM, BAS, CART, and exposure analytics can be used individually to meet technical use cases like asset discovery, control validation, SIEM optimization, purple teaming, and vulnerability prioritization. Collectively, they provide the attacker’s view of an organization’s security posture.
This is particularly relevant when looking to implement methodologies such as the Gartner Continuous Threat Exposure Management (CTEM) approach, defined as “an integrated, iterative approach to prioritizing potential treatments and continually refining security posture improvements.” (Gartner, 21 July 2022, Implement a Continuous Threat Exposure Management (CTEM) Program)
CTEM is a cyclical 5-stage program intended to help organizations monitor, evaluate and reduce their level of exploitability, and validate that their analysis and remediation processes are optimal.
Building a CTEM program requires using tools such as ASM, BAS, and CART to inventory and categorize assets and vulnerabilities, simulate and test attack scenarios and other forms of posture assessment processes and technologies. Tools like Exposure Analytics tie together the results of the data collected, correlate it with business contexts, and provide a remediation schedule recommendation optimized to factor in both technical and business priorities.
Exposure Management Maturity
Adopting these methodologies to comprehensively implement a CTEM approach can be achieved by gradually scaling cybersecurity, progressing from initial exposure assessment to sophisticated threat management.
The maturity scaling model can be broken down into three stages:
- Baselining
- Optimizing
- Automating
Baselining is necessary to evaluate the current exposure position and should be done using a combination of ASM to ensure all assets are accounted for. BAS identifies security gaps and tests the effectiveness of controls as they exist today.
Starting from that baseline, organizations can move into optimization to begin closing gaps and dealing with discovered issues.
Optimizing gradually introduces automated pen testing and red teaming capabilities, such as those of a CART tool. This stage should be dedicated to fine-tuning the attack simulations to maximize the value of attack path mapping, lateral movement, network pen testing, and other related capabilities.
This can be done in parallel with mapping assets to their respective business context and beginning to correlate those with collected data through an exposure analytics solution.
Once the assets’ business value is established and the selection of environment-relevant attack simulations is stable, it is time to automate.
Automating translates into scheduling attack simulations at appropriate intervals and replacing the legacy vulnerability prioritization technology with exposure analytics to create risk-based exposure management.
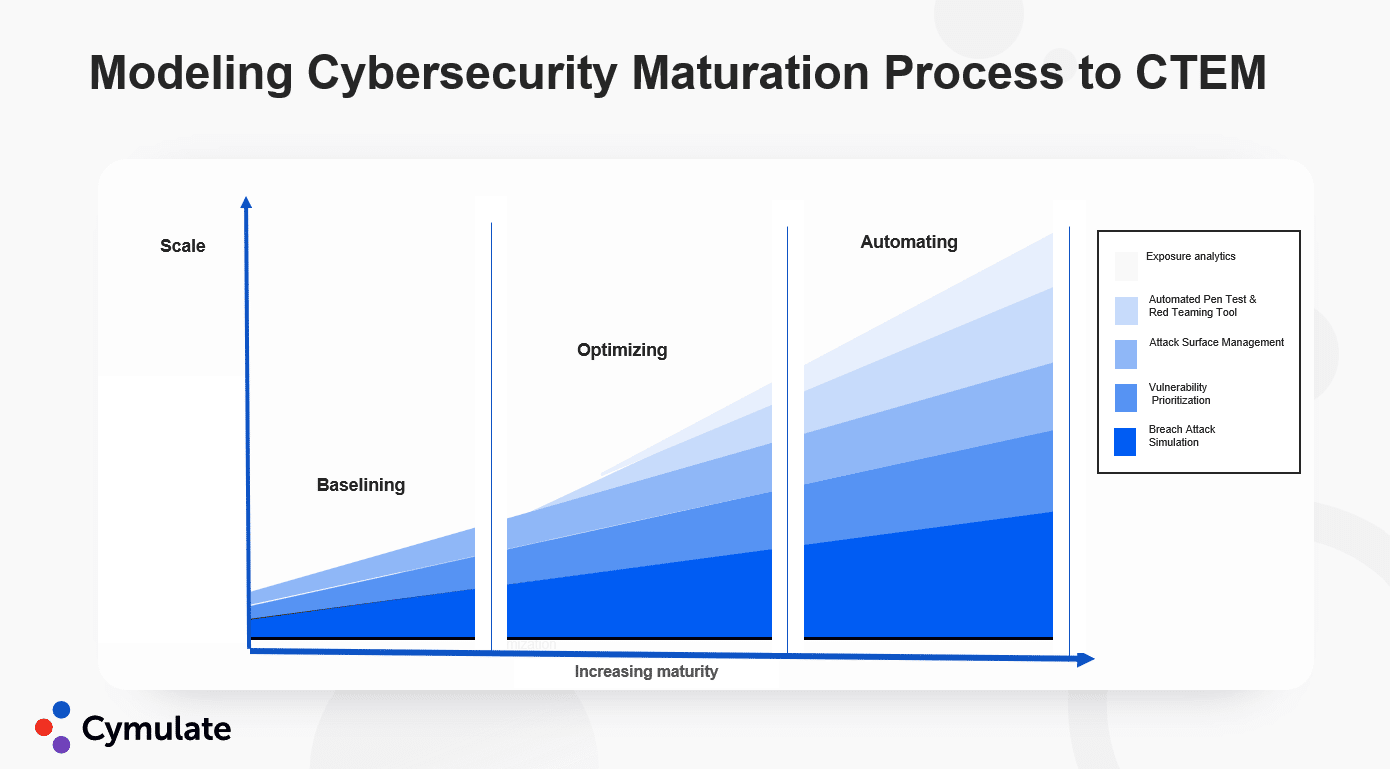
Reaching the automation stage enables focusing the attention of defenders on continuously refining their processes instead of performing routine repetitive tasks that may miss critical contextual information. As it also considerably reduces the number of alerts, both false positive and negative, it reduces burnout and churn within the cybersecurity workforce, allowing you to keep and grow the individuals on the team instead of searching for talent from the currently restrictive hiring pool.
Baselining, optimizing, and automating reflect the different cybersecurity maturity level of an organization adopting a CTEM approach, the most comprehensive model of integrating an attacker’s view into a cybersecurity strategy.