What is Breach and Attack Simulation (BAS)?

At its core, Breach and Attack Simulation (BAS) is exactly what it says on the tin - a platform that is designed to perform actions that closely mimic real threat actors breach attempts to determine if they are caught by your security measures.
The simulation can be anything from placing files that are indistinguishable from malware (but not actually dangerous to systems) onto a machine to see if the anti-malware tool catches them; to attempting to send data traffic through a firewall or malicious email through an email filter.
BAS Tools and Platforms
BAS tools and platforms are designed to run repeatedly; even automated to make the process of keeping security tight and up-to-date, making it easier for security teams to handle. The tests are designed not to interfere with production operations, working quietly behind the scenes so that users don’t even notice them running unless the vector is something like Phishing Awareness which tests employee vigilance.
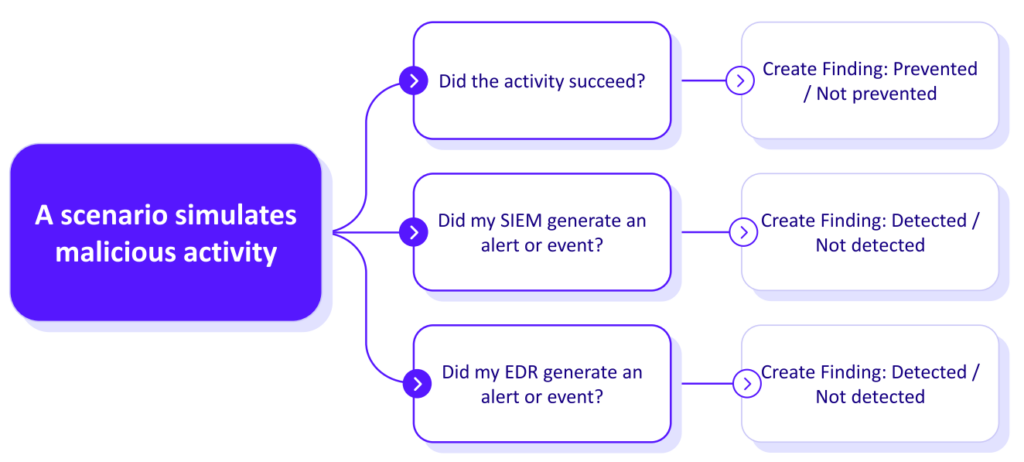
Breach and Attack Simulation uses a set of complex attack scenarios that attempt to bypass these control systems to reach a specific goal. If that goal can be reached (such as traffic making it through a firewall or an email being delivered to an end recipient), then the BAS platform has helped to uncover a flaw in that control that needs to be remediated.
Cymulate, for example, has multiple simulations designed to test a variety of vectors (potential attack paths that can be used to gain access to systems and resources). These simulations include:
- Email Gateway Simulation: Sends phishing emails designed to bypass security controls, ensuring spam filters effectively block malicious messages.
- Endpoint Simulation: Drops known malware files onto disks to test whether anti-malware tools detect and block them.
- Behavioral Detection Simulation: Executes test files in a controlled environment to assess whether behavioral-based detection systems recognize and respond to suspicious activity.
- Web Application Firewall (WAF) Simulation: Attempts to manipulate web servers into disclosing sensitive data or performing unauthorized actions, ensuring the web application firewall blocks such attempts before they reach the server.
How does BAS differ from other cybersecurity testing methods?
Penetration testing
Pen testing is conducted by human testers, also known as white-hackers, who attempt to evaluate the security of an organization’s infrastructure by safely exploiting potential vulnerabilities. Those security gaps may lie hidden in operating systems, services, or applications resulting from unpatched vulnerabilities, faulty configurations, or human error.
The corporate network, application, devices, and/or people are attacked to check whether a cyber attacker would be able to penetrate the organization. The tests reveal how deep an attacker could penetrate and if the attack payload could be executed, i.e., data exfiltration, file or system encryption, infrastructure disablement, or destruction.
Red teaming
Red teams use techniques such as pen testing, spear-phishing, and other social engineering techniques, multi-vector attack testing, vulnerability scanning, and cyber reconnaissance to find and expose weaknesses in the security measures and in the human element.
Red team exercises typically focus on just a few attack vectors - they don't test controls across the entire cyber kill chain. They typically use a limited number of attack techniques, unlike real-world malicious attackers who use more than 290 attack techniques, as listed in the MITRE ATT&CK™ framework.
Red team tools often lack the latest cyber threat intelligence, which means that they can only challenge controls against known threats, or else red team testers must perform some research in advance to ensure they are incorporating the latest threat intelligence in their testing. New malware variants emerge daily, which means you still must ensure that your controls can identify the newest attacks’ Indicators of Compromise (IoCs), stealth techniques, and behaviors.
Vulnerability scans
Performed by proprietary or open-source applications, vulnerability scans check the environment for potential vulnerabilities. However, their search capabilities are limited to vulnerabilities already known to vendors and the industry and limited to weaknesses already exploited by cyber attackers.
Vulnerability scanners typically scan networks and systems for thousands of security vulnerabilities of any variety, from software bugs and missing operating system patches to vulnerable services, insecure default configurations, and web application vulnerabilities. They then generate a report listing all the detected vulnerabilities, ideally affecting a risk score to each uncovered vulnerability.
These scores are typically based on CVSS scores. A patching schedule based on these scores and on defined risk tolerance baselines is then passed on to the IT team to apply the required patches.
The Benefits of Automated Breach and Attack Simulation
Automated BAS tools enable you to answer the question "How well do our controls and policies detect and stop attackers?" BAS tools model attacks, identify heat spots, and assess the risk of all security elements.
In addition, BAS enables continuous, comprehensive testing to challenge, measure, and optimize cyber defenses by:
- Simulating attacks without jeopardizing production environments.
- Simulating cyberattacks across the full kill chain against all threats, including the latest attacker TTPs.
- Testing continuously with flexibility to target specific vectors, infrastructure, and internal teams for awareness against the latest threats.
- Automating simulations for repeatability and consistency.
- Conducting testing at any time interval—hourly, daily, weekly, or ad hoc.
- Identifying gaps and evaluating controls against the MITRE ATT&CK framework.
- Remediating exposure using actionable insights.
With BAS, you can focus security control testing on techniques and potential attack paths that can be exploited by many different types of threat actors—without having to assemble teams of security experts. By utilizing technique-based frameworks such as MITRE ATT&CK, your organization can effectively test against and neutralize multiple types of attacks simultaneously for real security against real-world threats.

Breach and Attack Simulation Made Simple with Cymulate
The Cymulate Exposure Validation Platform applies breach and attack simulation to validate and optimize security controls with advanced testing and easy, repeatable automation in the industry’s most deployed solution for exposure validation that includes:
- Overview dashboards – Gain security posture insights and monitor for drift using risk scores, trends, prevention/detection ratios, top attack types and APT groups not prevented by your security controls.
- Assessment templates – Create your own assessment templates that validate your security posture and controls including dynamic smart templates that automatically include new attack scenarios at launch.
- Best practice assessments – Automated testing and validation of key security controls and threat scenarios using our best practice assessments and pre-built templates.
- Attack scenario workbench – Flexible workbench to create custom assessments for the threats that matter most to you, using a rich library of the latest attack scenarios and malicious behaviors.
- Daily threat feeds – Validate immediate threats using the latest emergent threats which are loaded into the Cymulate platform daily by our threat research team.
- Integrations and connectors – Integrate technologies from leading security vendors to optimize your investments in SIEM, SOAR, GRC, EDR, firewall and more via APIs to validate and improve detection and response capabilities.
- AI-powered attack planner – Privacy-focused artificial intelligence converts threat intel and plain language prompts into custom threat assessments and complex attack chains.
- Automated control updates – Integrate security controls and push new indicators of compromise (IOCs) to mitigate control gaps identified by the latest assessments.
- Mitigation guidance and detection rules – Remediation insights provide straightforward guidance to mitigate threats, fine tune controls and refine policies for better protection.
- Full MITRE ATT&CK coverage – Reports and findings are mapped to the MITRE ATT&CK® framework with heatmaps showing areas of strengths and weaknesses across the full range of MITRE tactics and techniques.
- Cross-platform solution – Extensive attack simulation and immediate threat testing across on-premises, cloud and hybrid environments for a wide variety of operating systems (Windows, Mac, Linux).
Key Takeaways
Breach and Attack Simulations test the effectiveness of security controls in your environment without impacting your end-users or requiring extensive cybersecurity knowledge.
- You can confirm that all of the security controls you put in place are working effectively and doing everything you expect them to be doing.
- You can quickly confirm that you are protected against the latest threats.
- You can test repeatedly - and whenever needed.
- If any weaknesses are discovered, you can use valuable insights to remediate the problem and close the gap quickly and completely.