Cyber-attacks are making cyberspace an increasingly hostile environment for organizations. Without Breach and Attack Simulation capabilities, and despite having security solutions in place, defending against breaches is becoming more and more difficult, as recent cyber-attacks such as WannaCry have shown.
Between 2017 and 2023, global investments in cybersecurity saw a significant rise, nearly doubling from just under $100 billion in 2017 to close to $200 billion by 2023. The majority of this spending has been focused on security services, infrastructure protection, and network security tools. By 2024, expenditures on security services alone are projected to approach $90 billion.
Cybersecurity Investments Are Rising, But Are They Effective?
Selecting security products and services has become complicated, and it’s hard to assure their effectiveness. A deployed firewall, anti-malware platform, secure email gateway or other security solutions can be a valuable asset one day, and become a huge liability the next.
How effective they are being often a guessing game since little empirical evidence is available. This makes it hard for an organization to make informed decisions regarding its cybersecurity investments and risk management. Allocating resources for cybersecurity and ensuring their ROI has become a major challenge, especially since security products are often overlapping.
As Gartner points out, CIOs need to adapt a balanced approach that takes into account the security risks as well as business benefits by conducting continuous, objective, and non-invasive assessments of vulnerability threats.
Introducing Breach and Attack Simulation for Proactive Security
New services have emerged that help organizations do just that – assessing the effectiveness of security procedures, infrastructure, vulnerabilities, and techniques by using breach and attack simulation platforms. Such simulations test the vulnerability of your organization for e.g., ransomware attacks, (spear) phishing and whaling attacks, or clicking on malicious banners and links on websites.
Breach and attack simulation technologies help organizations prepare for attacks against their critical assets, as noted in Gartner’s Hype Cycle for Threat-Facing Technologies (image 1). “The ability to provide continuous testing at limited risk is the key advantage of Breach and Attach Simulation (BAS) technologies, which are used to alert IT and business stakeholders about existing gaps in the security posture, or validate that security infrastructure, configuration settings, and prevention technologies are operating as intended”.
Real-Time Cybersecurity Posture Monitoring with BAS
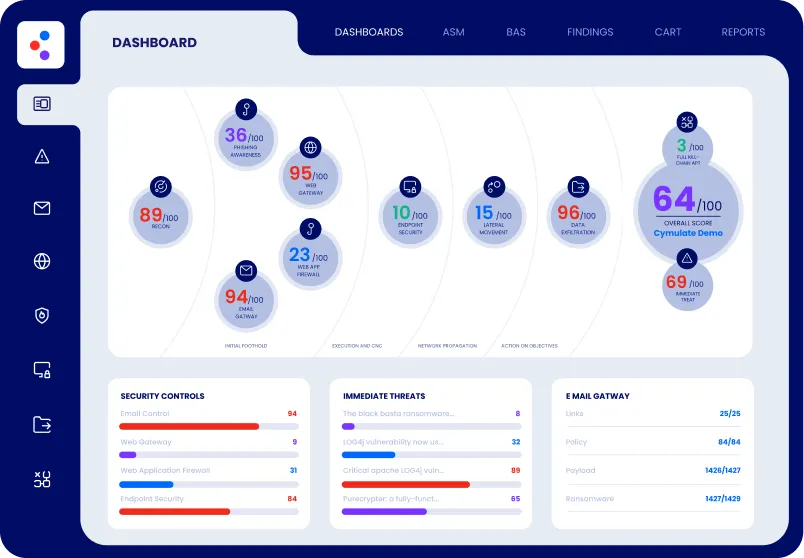
A proactive approach to cyber vulnerabilities consists of deploying a cyber simulation platform. This allows organizations to test their security assumptions, identify possible security gaps, and receive actionable insights to improve their security postures. Such a breach and attack simulation platform:
- Assists organizations to stay one step ahead of cyber-attacks with on-demand simulations delivering immediate results, providing a full picture of the company’s security posture 24/7. A simulation platform (such as Cymulate’s) shortens the usual testing cycle and speeds up the time to remediation, while the self-service model keeps the organization in full control of any vulnerability gaps that are detected.
- Helps organizations monitor the company’s cybersecurity on an ongoing basis by utilizing a platform that attacks the corporate network using multiple attack vectors (e.g., email, internet browsing, Web application vulnerabilities, social engineering) to detect the weak spots that could be exploited.
- Shows the organization’s management that the security programs are effective and justify the investments for achieving regulatory compliance, aligning the security with business objectives, reducing security events, incidents, and breaches, improving the risk profile, tracking improvements in responses, and maintaining the risk profile for optimal cyber insurance rates.
How Cymulate’s Platform Enhances Security Testing
The Cymulate platform allows organizations to run continuous, on-demand cybersecurity simulations at any time without affecting their systems. As a Software-as-a-Service (SaaS) breach and attack platform, it simulates multi-vector, internal or external attacks by targeting the latest vulnerabilities, including those that are in the wild. These simulated attacks expose vulnerability gaps which allow the organization to determine if its security architecture provides the right protection and if its configurations are properly implemented.
Overall, breach and attack simulation platforms such as Cymulate’s, have become a powerful tool in the arsenal of the organization’s security team.
Ready to strengthen your cybersecurity defenses? Book a demo with Cymulate today and see firsthand how continuous breach and attack simulations can safeguard your organization from evolving threats.
Don’t speculate, Cymulate