How Cymulate - Splunk Integration Makes Validating SIEM a Snap
The Cymulate Exposure Management and Security Validation platform supports integration with Splunk. When using the Cymulate platform with Splunk, SIEM administrators and SOC analysts can:
- Validate their detection rules
- Increase their efficiency
- Build new rules based on the latest threat actor behaviors and techniques
- Train and prepare their colleagues for actual incident detection and response
Cymulate provides the ability to safely simulate real attacks targeting production security controls, to understand and enhance how your security team detects and handles incidents. Cymulate’s ease of use, customizable dashboards and reports, and comprehensive set of out-of-the-box and custom assessments enable security organizations to supercharge their detection and reporting capabilities.
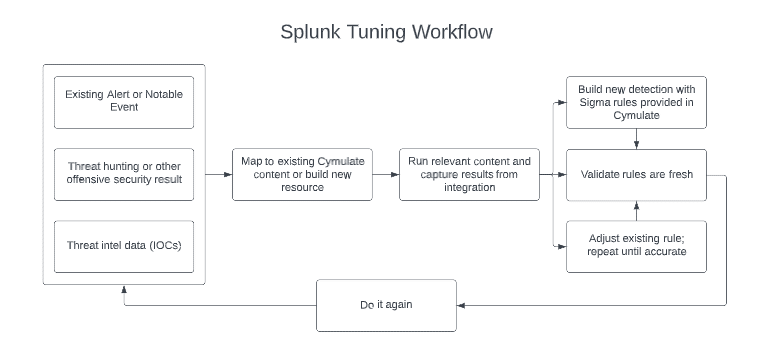
How Cymulate Helps Tune Splunk
Adapting security to constantly changing technology and infrastructure is a complex task. Without tuning rules and alerts, a team might miss important information that helps them detect and respond to emerging threats.
In addition, the threat landscape is constantly changing. Security teams are expected to generate new and innovative detection capabilities to identify new attack techniques. Unfortunately, even the most highly resourced and capable teams struggle to keep pace with new threat actors, campaigns, and groundbreaking attacker techniques.
Given the above, it is no surprise that detection rules configuration lags. Outdated or inadequate configurations can jeopardize your organization’s infrastructure in two ways:
- An unnecessarily high number of alerts and false positives leading to alert fatigue – Alerts that were once vital might have lost their relevancy, tools with redundant capabilities might raise alerts twice for the same event, and evolution in the organization’s risk appetite might not have been reflected in the configuration of trigger levels. As alerts increase, they should be checked for their value and risk-rated based on the monitoring of their behaviors and actions.
- Recently added devices, tools, infrastructure modifications, or other changes might not be considered. In the era of rapid infrastructure evolution and increased reliance on the supply chain, a delay in adequately configuring security controls in time may open hidden security gaps.
This simultaneous combination of factors makes it hard for SOC teams to keep up. Considering that this needs to be done continuously to ensure security technology detects suspicious activities and alerts are firing as intended, it is easy to see how a team can be overwhelmed managing SIEM solutions.
How does Cymulate - Splunk Integration Make Life Easier?
1. Ensure logs are being ingested
No matter how strong your team and your use cases are, if logs are not being sent to and ingested by Splunk correctly, nobody will ever see them. As a result, configurations inevitably break or are broken by changes. Cymulate helps identify issues with receiving logs. When integrated with Splunk, Cymulate queries to see if an event was detected within Splunk after each assessment; there might be a log delivery issue if no event was detected where events should be easily identified. Setting up a scheduled routine assessment in Cymulate makes this an easy check.
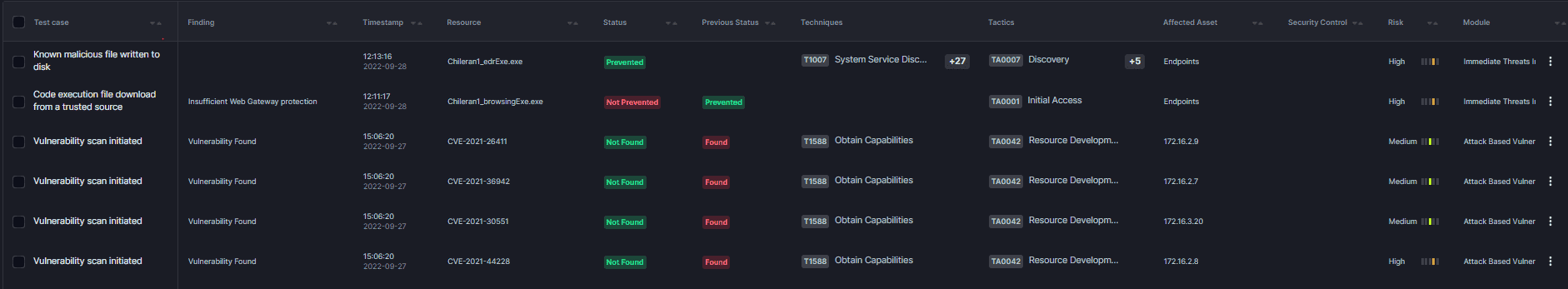
2. Validate detection rules and alerts
Detection rules and new alerts should be created regularly by the SOC team. Old rules should be retired, and new ones should be developed, tested, and implemented based on emerging threats. What better way to test a new rule than executing an attack or using IOCs that should trigger it? Cymulate allows you to use pre-built attack templates or customize your own to ensure your detection and alerting mechanisms are working as intended. Taking this a step further, Cymulate provides built-in detection and mitigation recommendations for each assessment to make life even easier.
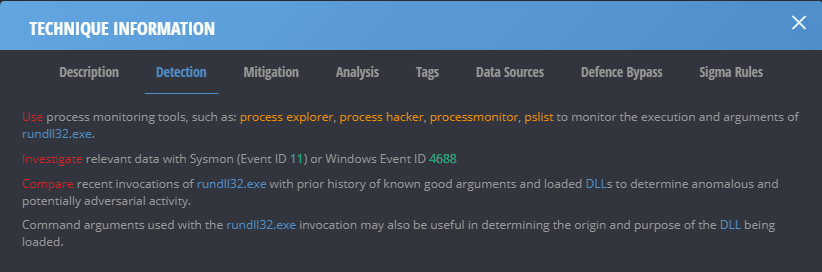
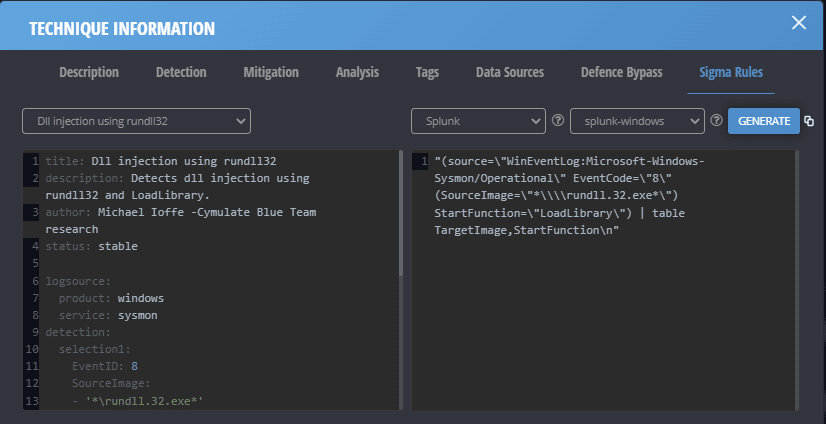
3. Reduce the team’s level of effort
Cymulate simplifies and accelerates the SIEM detection use case development process. Many modules within Cymulate provide mitigation recommendations within the assessment reports. In addition, Cymulate delivers a mechanism to generate Sigma rules based on the specific attack techniques used in an assessment. This functionality accelerates analysts' ability to create meaningful rules or alerts within Splunk or other products.
4. Train and measure the security team
Cymulate enhances a SOC team’s skills and readiness. An organization can use Cymulate to conduct tabletop exercises, test new or senior staff's response time, and to ensure that processes are working within pre-defined timelines or Service Level Agreements (SLAs). An assessment can be started to see how quickly an event is detected in Splunk. After detection, the downstream processes can be evaluated to determine if the response time is within acceptable bounds. Where deficiencies exist, processes could be changed, or teams could be educated to identify better and triage the attack behaviors.
Integrating Splunk with Cymulate allows your team to safely simulate malicious behaviors, home in on activities that bypass your security controls and fine-tune your SIEM for optimal results. Moving from a reactive detection and response approach toward a proactive, continuous enhancement approach results in more effective and efficient people, processes, and technology.
Benefits
Cymulate equips security teams with greatly enhanced visibility into an organization’s security posture, streamlines the ability to detect and respond, and enables SOC teams to be more efficient and effective. Running simulated attacks on the production network with the Splunk integration:
- Gives richer context to findings
- Enables security controls fine-tuning
- Reduces workload related to vulnerability management
- optimizes change management through integrated ticketing
- Provides a modular, customizable dynamic dashboard for instantaneous in-depth analysis
Cymulate’s integration with Splunk is available for Immediate Threats, Endpoint Detection and Response (EDR), and Advanced Scenarios.
How to Integrate Cymulate with Splunk
Setting up the integration between Splunk and Cymulate is easy.
- Sign in to the Cymulate platform.
a. Click on the user button.
b. Click ‘Integrations’. - Scroll to the Splunk integration and select ‘Edit’.
- Provide the username, password, and URL for your Splunk instance. Select the time zone for the Splunk deployment and enter any desired delay for Cymulate to wait before querying for events after executing simulated attacks.
Note: This requires setting up an integration user within Splunk. For more information on how to do this, please read the following Splunk article. - Click ‘Submit’.
- Cymulate will validate the connection.
Once the integration is established, it is available directly from any supported modules within the platform. You can safely run attacks and see if the resulting logs that Splunk is ingesting contain relevant identifiers associated with Cymulate actions. Cymulate will display the query sent to Splunk and the detailed Splunk response, verifying if Splunk detected relevant events and triggered alerts.
We encourage you to book a demo to understand better the power of Cymulate and the benefits it brings to your security team.



