7 Essential Steps to Becoming Ransomware Resilient
According to The State of Ransomware 2025 by Sophos, ransomware remains one of the most pervasive threats to organizations worldwide, with exploited vulnerabilities accounting for 32% of all attacks and half of incidents resulting in data encryption. While the average ransom payment has dropped by 50% over the past year to $1 million, 49% of victims still end up paying, and nearly all report serious operational and human consequences, including stress, burnout, and leadership turnover.
These findings highlight that ransomware remains one of the most serious cyber threats. Attackers are constantly refining their techniques to exploit organizational weaknesses. While traditional defenses such as firewalls and antivirus software are still essential components of a layered cybersecurity strategy, true ransomware resilience requires more than prevention. True ransomware resilience demands the ability to prepare for, respond to, and recover from attacks effectively.
Key highlights
- Ransomware attacks are now among the fastest-growing cyber threats, with incidents expected every two seconds by 2031, no organization is immune.
- True resilience goes beyond prevention, combining strong defenses with the ability to detect, contain and recover quickly from attacks.
- Core resilience measures include least-privilege access, network segmentation, reliable offline backups and regular employee awareness training.
- Continuous validation and realistic attack simulations are essential to uncover hidden weaknesses before real attackers exploit them.
- The Cymulate security validation platform enables organizations to test against real ransomware tactics, close gaps fast and build measurable resilience.
What is ransomware resilience?
Ransomware resilience refers to an organization’s ability to prepare for, withstand, respond to and recover from a ransomware attack. In other words, it’s a proactive and holistic approach that goes beyond just blocking malware.
A ransomware-resilient organization assumes that breaches can happen, and builds robust systems and processes to minimize damage when they do. This includes strengthening defenses to make intrusions harder, but equally emphasizes incident response and recovery capabilities – such as maintaining viable backups and a practiced response plan.
Ransomware resilience is often described as moving “beyond prevention.” While traditional ransomware protection focuses on keeping attackers out, resilience recognizes no defense is 100% foolproof.
Instead of relying solely on prevention, resilience means also being ready to respond and quickly restore operations if ransomware hits.
A resilient company will have offline backups to restore data without paying a ransom, and a trained response team to contain an attack before it spreads. This comprehensive approach ensures that even if one layer of security fails, the organization can still limit the blast radius and recover its data and systems.
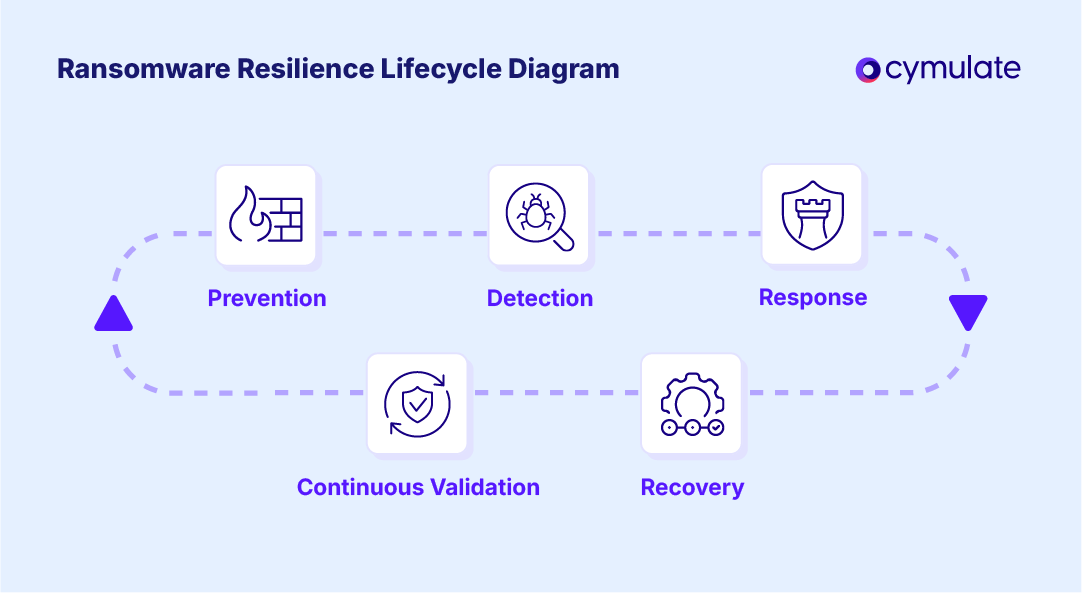
Key components of ransomware resilience
Building ransomware resilience means combining several defensive layers and ensuring fast recovery.
- Preventive security controls: Deploy next-generation firewalls, endpoint protection (EPP/EDR), email filters, web gateways and anti-malware tools to block threats early. Strong vulnerability management and patching close software flaws that ransomware often exploits.
- Access management & least privilege: Use least privilege access so users only get the minimum rights they need. Enforce Multi-Factor Authentication (MFA) and adopt Zero Trust to restrict lateral movement if attackers gain entry.
- Detection & response: Implement SIEM validation, intrusion detection and endpoint monitoring to spot suspicious activity quickly. Maintain a tested incident response plan to isolate and contain attacks, reducing dwell time and limiting damage.
- Data backups & recovery: Keep regular, protected backups stored offline or in immutable storage. Follow the 3-2-1 rule (3 copies, 2 media types, 1 offsite) and test restoration to ensure data can be recovered without paying ransom.
- Employee awareness & training: Train staff to detect phishing and other social engineering attempts. Run phishing simulations and encourage quick reporting of suspicious activity to prevent human-enabled breaches.
- Advanced threat protection: Defend against tactics like BYOVD (Bring Your Own Vulnerable Driver) with behavior-based detection, network segmentation and application allow-listing to stop unauthorized programs.
- Continuous validation & testing: Conduct regular breach and attack simulations, red-team exercises and penetration tests to identify gaps and verify that defenses remain effective.
Ransomware resilience relies on preventive controls, tight access management, rapid detection/response, secure backups, employee vigilance, advanced defenses and continuous testing to withstand and recover from attacks.
Why ransomware resilience matters
Ransomware attacks now go far beyond simple data encryption. They cause business disruption, financial loss, regulatory fines, and lasting reputational damage.
Recovery costs can reach millions of dollars, healthcare breaches average $10 million per incident. Attackers bypass defenses by disabling endpoint agents, using stolen credentials and even destroying backups, so relying only on antivirus or firewalls is not enough. Resilience accepts that some attacks will succeed and ensures you can respond and recover quickly.
Key business benefits
A resilient organization can detect intrusions early, restore from protected backups and recover systems without paying ransom. This prevents long outages and breaks the cycle of repeated ransomware attacks.
Strong resilience also improves cyber-insurance eligibility, lowers premiums and supports regulatory compliance (MFA, EDR, incident response plans, NIST standards).
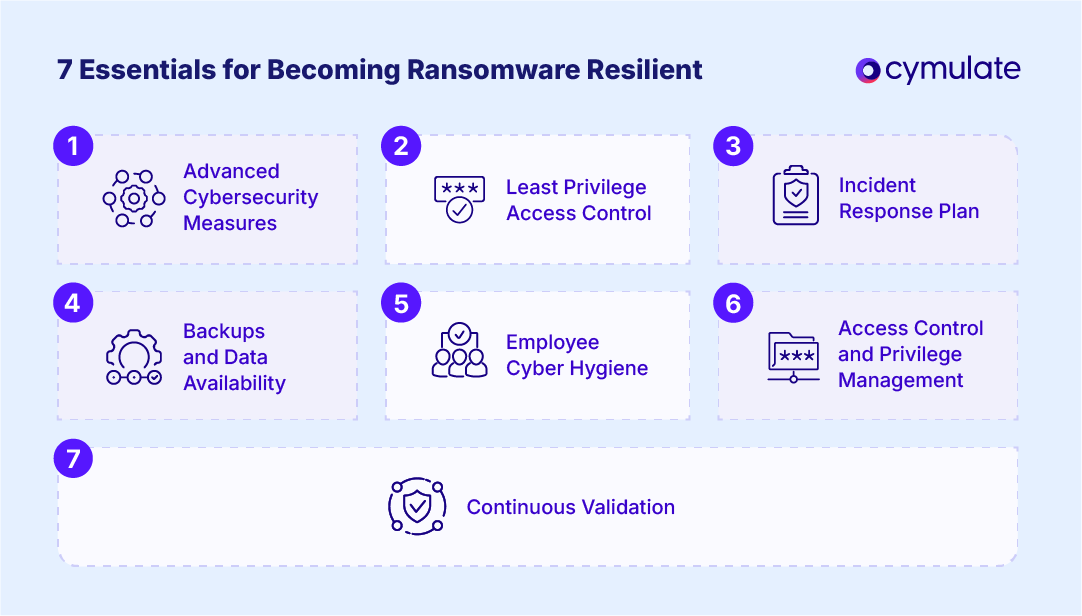
How to become ransomware resilient: 7 key steps
Becoming ransomware resilient requires a proactive approach to cybersecurity, a blend of prevention, detection and recovery strategies all working in concert.
Below, we detail seven essential steps to help your organization build a strong, multi-layered defense against ransomware. Following these steps will significantly improve your ability to resist ransomware attacks and minimize damage if one occurs.
1: Implement advanced cybersecurity measures (including a ransomware assessment)
The first step to ransomware resilience is to harden your environment with advanced security controls and to assess your vulnerabilities before attackers do. This often starts with a comprehensive ransomware resilience assessment to identify gaps in your defenses.
Consider leveraging frameworks or tools (for example, CISA’s Ransomware Readiness Assessment) to evaluate how prepared you are to prevent and handle ransomware (cisa.gov). By knowing your weak points, you can prioritize improvements to stop ransomware in its tracks.
Key measures and tactics include:
- Identify vulnerabilities using multiple methods: Thoroughly scan your network and systems for weaknesses. Deploy solutions like endpoint security validation, strong network configurations and rigorous access controls that provide real-time monitoring and automated threat response. The goal is to catch and neutralize malware early. These tools can flag suspicious behavior (such as a process starting to encrypt files) and shut it down immediately.
Network segmentation: Segment your organization’s network to limit how far ransomware can spread if it gets in. By creating isolated network zones (for example, separating critical servers from user workstations), you prevent an infection on one node from easily propagating enterprise-wide. This is a critical containment strategy, if an attacker compromises a less-privileged segment, network segmentation will isolate vital systems and prevent the attack from affecting the entire organization. - Breach and Attack Simulation (BAS): Deploy BAS tools to simulate real-world attack scenarios in a safe manner. BAS platforms, such as the Cymulate Breach and Attack Simulation module, allow you to test how your current security controls stand up to ransomware tactics without the risk of actual damage. A BAS exercise might simulate a phishing email with ransomware payload or an attacker moving laterally across the network.
2: Implement least privilege access control
Even if malware infiltrates your network, following the principle of least privilege will drastically limit what it can do. This step focuses on tightening access controls so that users and systems have only the minimum permissions necessary, reducing the potential blast radius of an attack.
In a ransomware context, if an employee’s account is compromised, least privilege ensures the ransomware can only access that user’s files, not the entire network.
Key sub-strategies include:
- Role-based access control (RBAC): Restrict access to sensitive systems and data based on each user’s role. Every employee, application, or service account should only be able to reach the resources essential for their job. For instance, an HR employee should not have access to the finance department’s file shares, and vice versa. By compartmentalizing access this way, you minimize the chances of a ransomware infection reaching critical resources.
- Zero zrust principles: Adopt a Zero Trust security model for access, meaning never trust and always verify every access request, whether it originates from inside your network or outside. In practice, Zero Trust involves continuously authenticating and authorizing users and devices, and evaluating context (like device security posture) before granting access to resources.
For ransomware defense, Zero Trust can prevent an attacker who compromises one account or endpoint from freely roaming your internal network. Even if they get in, every lateral movement they attempt triggers fresh authentication and policy checks. This helps prevent or slow down lateral movement, a common technique ransomware uses to escalate an initial foothold into a domain-wide compromise. - Minimize privileged accounts: Drastically limit the number of accounts with administrative or other high-level privileges. Domain admins, for example, should be very few in number and used sparingly. Since privileged accounts are a favorite target for ransomware operators (because they can do the most damage), having fewer of them reduces your risk exposure. Use just-in-time access and privilege elevation tools to grant admin rights only when needed and automatically revoke them after.
3: Develop a comprehensive incident response plan
This step is about being prepared to react swiftly and effectively when an attack is detected, to contain the damage and facilitate rapid recovery.
A well-crafted and rehearsed ransomware IR plan can make the difference between a minor security incident and a full-blown crisis.
Key elements of a ransomware-focused IR plan include:
- Establish clear protocols: Create a detailed, step-by-step incident response playbook that covers ransomware scenarios. This plan should outline exactly what to do when ransomware is suspected or confirmed, from detection through containment, eradication, recovery, and post-incident analysis. Important aspects include isolating infected systems (e.g. removing them from the network), notifying stakeholders (internal leadership, IT teams, communications, legal, etc., as well as external partners or law enforcement as appropriate), and initiating recovery procedures (like starting data restore from backups).
- Simulate ransomware attacks: An IR plan is only as good as your team’s ability to execute it. Conduct regular tabletop exercises and simulations to practice the ransomware response. This could involve a scheduled drill where a ransomware outbreak is mimicked (without actual malware), requiring teams to walk through their actions: from detecting the threat, “locking down” the affected machines, coordinating with backups team for restores, etc. You might also use technical simulation tools.
Additionally, your IR plan should include post-incident review procedures. After containing and recovering from any ransomware attack (or completing a drill), convene the team to analyze what went well and what didn’t. Update the plan accordingly. Ransomware tactics evolve quickly, so keep the IR plan current with the latest threat intelligence.
4: Conduct regular backups and ensure data availability
Maintaining reliable data backups is often called the single most important defense against ransomware. If you can restore your data from uncompromised backups, you can deny attackers the leverage they seek. This step emphasizes establishing a rigorous backup strategy and testing it regularly so that your data remains available and recoverable no matter what.
Key practices for resilient backups include:
- Frequent, offline backups: Ensure all critical data is backed up on a frequent schedule (daily or even hourly for mission-critical systems). More importantly, store backups in an offline or air-gapped environment that ransomware cannot reach. This could mean keeping copies on external drives that are disconnected when not in use, using offline tape backups, or leveraging cloud backups with robust access controls/immutable storage. The idea is that even if your production network is compromised, the backups remain untouched. Many ransomware strains actively try to find and encrypt or delete any connected backups, including network shares or attached storage.
- Backup testing and restoration drills: A backup that can’t be restored is no backup at all. Regularly test your backups by actually restoring some data and verifying its integrity. At least annually (if not more often), perform full restore tests for key systems to simulate a recovery from scratch. This ensures your backup files aren’t corrupted and that your team knows the restore process.
Pay attention to how long restoration takes, this defines your Recovery Time Objective (RTO) and determines how much downtime you might face in a real incident. It’s better to discover in a test that a backup was misconfigured than during an actual crisis.
Companies that have beaten ransomware attacks often cite their investment in backups as the reason. It’s important to view backups as a dynamic, actively managed defense: keep them current, secure and test their effectiveness. In doing so, you ensure that your organization can bounce back from ransomware with minimal disruption.
5: Train employees on cyber hygiene and ransomware awareness
Human error is a leading cause of ransomware incidents, which means that educating your workforce is an essential step toward resilience. Your employees and contractors should be a strong first line of defense, not a weak link. This involves instilling good cyber hygiene habits and awareness of ransomware tactics through ongoing training and a supportive security culture.
Key focus areas for employee-centric resilience:
- Phishing awareness training: Because many ransomware attacks begin with a simple phishing email, it’s critical to train staff to recognize and avoid phishing attempts. Conduct regular training sessions (e.g. quarterly) that teach employees how to spot common signs of phishing – suspicious sender addresses, misspellings, unexpected attachments or links, urgent scare tactics, etc. Supplement these with simulated phishing campaigns: send fake phishing emails to employees (in a controlled test) to see who clicks, then use that as a coaching opportunity.
- Create a security-centric culture: Fostering a workplace culture that emphasizes the importance of cybersecurity will reinforce training and make employees active participants in resilience. This means encouraging employees to report suspicious activity or potential security incidents immediately, without fear of blame. When employees feel responsible for the organization’s security, they become more cautious and engaged.
6: Strengthen access control and privilege management
This step is about fortifying account security and anticipating advanced attack techniques that target authentication and system controls.
While Step 2 addressed least privilege at a high level, here we dive deeper into specific identity and access management enhancements and discuss emerging attacker tactics so you can counter them.
Important measures include:
- Use the Principle of Least Privilege (PoLP) consistently: We mentioned least privilege earlier, but it bears repeating and reinforcing across all systems. Review not just user accounts, but also service accounts, API keys, and any account that could be leveraged by an attacker. Ensure every account has only the privileges absolutely required.
- Multi-Factor Authentication (MFA) everywhere: Enforce MFA across all critical systems and accounts, including remote access, VPNs, email, privileged accounts and ideally for all user logins in general. MFA adds a significant hurdle for attackers, even if credentials are stolen via phishing or a data breach, the attacker generally cannot get in without the second factor. Many real-world ransomware incidents could have been prevented if MFA had been in place on admin accounts or VPN access.
- Be aware of advanced tactics like BYOVD and others: As mentioned, threat actors continuously evolve their techniques. One notable example is Bring Your Own Vulnerable Driver (BYOVD) attacks, where attackers exploit legitimate but vulnerable kernel drivers. By installing an older, known-vulnerable driver on a system, the attacker can run code with kernel-level privileges, effectively bypassing standard protections and disabling security tools.
7: Continuously validate security controls
The final essential step for resilience is to institute a process of continuous validation of your security controls and posture.
In practical terms, this means regularly testing, measuring, and improving your defenses so that you maintain a strong security posture over time, even as new threats emerge.
Key activities in continuous validation include:
- Regular security assessments and penetration testing: Rather than doing security assessments once a year (or only after an incident), shift to a continuous assessment mindset. Utilize automated scanning tools frequently to catch new vulnerabilities or misconfigurations. Schedule professional penetration tests periodically and whenever you make significant changes to your environment.
- Exposure management and real-time monitoring: Leverage exposure management tools and practices to keep an up-to-date view of your risk surface. Exposure management (also related to concepts like Attack Surface Management) involves identifying all your IT assets – including shadow IT, cloud services, partner connections – and assessing them for vulnerabilities or misconfigurations on an ongoing basis. Many breaches happen because something was forgotten or left unmonitored.
After implementing these seven steps, your organization will have significantly bolstered its ransomware defenses. However, resilience is an ongoing journey.
How to measure ransomware resilience
To ensure your ransomware resilience efforts are effective, you should track certain metrics and indicators that collectively gauge your ability to prevent, withstand and recover from attacks. Measuring ransomware resilience involves looking at both technical performance and process maturity.
Here are some key ways to measure how resilient you are:
Incident detection and response times
Monitor metrics like Mean Time to Detect (MTTD) and Mean Time to Respond/Recover (MTTR) for security incidents. MTTD is the average time it takes to discover a threat, and MTTR covers containment and restoration. In a resilient organization, these numbers should be as low as possible.
Backup recovery performance
Another vital measure is how quickly and successfully you can restore from backups (and how much data loss, if any, you’d incur).
Conduct periodic restore tests and record the Recovery Time Objective (RTO), the time it takes to get critical systems back up and Recovery Point Objective (RPO), how recent the restored data is (e.g. last nightly backup vs. real-time mirroring). If your current RTO for a full restore is, say, 48 hours, you might work to bring that down to 24 or 12 hours for greater resilience.
Phishing test success rates
To measure the human factor, use your phishing simulation campaign results. Track the percentage of users who fall for test phishing emails (click links or enter credentials). As resilience improves through training, you should see this click rate decrease over time.
Frequency of security assessments and findings closed
Another meta-metric is how proactively you’re testing yourself. A resilient org will be running regular BAS exercises, vulnerability scans and red team tests.
You can measure resilience by the scope and severity of issues uncovered in these tests, and how quickly you remediate them.
Cyber insurance readiness
If you apply for cyber insurance or undergo security audits, note the feedback. Many insurers now provide questionnaires or scans that effectively measure your controls (MFA everywhere, backups in place, etc.). Passing those with minimal exceptions is a form of measuring resilience.
Measuring ransomware resilience involves a combination of technical metrics (time-based and success rates) and qualitative assessments (like readiness checklists and external audits).
It’s beneficial to define a set of Key Performance Indicators (KPIs) for your security program focused on resilience. Common metrics include those around detection/response times, backup RTO/RPO, patching cadence, user awareness and assessment results.
Managed ransomware resilience: When to consider external support
All organizations, regardless of size or sector, are vulnerable to ransomware attacks. While companies can and should implement preventive measures such as security controls, software updates, multi-factor authentication, employee training, and incident response planning, these steps alone may not be enough.
Because it is nearly impossible to validate the effectiveness of these defenses until an actual attack occurs, many organizations reach a point where external support becomes critical. Managed ransomware resilience services provide expertise, continuous testing, and independent validation to help close security gaps before attackers can exploit them. By leveraging external support, companies strengthen preparedness, reduce recovery time, and improve their chances of withstanding even the most sophisticated ransomware campaigns.
Cymulate offers a powerful and comprehensive approach to enhancing ransomware resilience through its proactive security validation platform. By simulating real-world ransomware attacks, Cymulate can help organizations identify weaknesses in real-time, improve their defenses and strengthen their overall security posture.
Through the breach and attack simulation solution (BAS), Cymulate can:
- Replicate ransomware attacks and other malicious activities to help security teams assess how their defenses would perform under real-life attack conditions
- Pinpoint vulnerabilities
- Prioritize areas of improvement
A critical factor of being ransomware resilient is continuously scanning and assessing your environment for risks. Our platform provides real-time security gap reports of your organization’s potential risk exposure, allowing you to measure the effectiveness of your defenses and make prioritized remediations.
Build ransomware resilience with Cymulate
Building ransomware resilience isn't a one-time task — it's an ongoing process that involves preparation, detection and quick recovery. By following these seven essential steps, organizations can minimize the damage caused by ransomware attacks, reduce downtime and safeguard critical data. As ransomware tactics evolve, maintaining a flexible, multi-layered defense is the key to staying resilient in the face of increasing cyber threats.
Cymulate AI-powered platform offers faster, more accurate and efficient results, making it a world-class cybersecurity provider to help you become ransomware resilient.
Request a demo to see how Cymulate can enable you to build your ransomware resilience.
Frequently asked questions
Strong cyber resilience prepares you to respond and recover fast if a ransomware attack lands. With rehearsed IR playbooks, protected backups, and clear roles, you limit spread and downtime and avoid paying ransom.
Ransomware protection focuses on blocking attacks (AV, EDR, email filtering). Ransomware resilience includes protection plus recovery and continuity, segmentation, offline backups and practiced response, so one missed alert doesn’t become a crisis.
Yes. Insurers increasingly require controls like MFA, EDR and tested backups; strong resilience lowers risk, improves eligibility and can lead to better terms and pricing.
All sectors do, healthcare, finance, government, education, manufacturing, legal, SMBs. Any organization that relies on data or 24/7 services needs layered defenses and rapid recovery to keep operations running.
Usually no. You tighten configurations, close gaps (MFA, segmentation, offline backups) and add complementary testing/validation rather than rip-and-replace.
Run breach and attack simulations, tabletop exercises, and periodic red-team engagements; verify backup restores on a schedule. Track MTTD/MTTR and fix gaps, then retest to confirm improvements.