Firewall Testing: Ensuring Your Firewall Functions Properly

Firewalls are foundational to network security, serving as the first line of defense by regulating and monitoring traffic between trusted internal networks and external sources. However, firewalls alone cannot provide complete protection. Regular firewall testing ensures they are correctly configured and functioning optimally. This article provides a comprehensive, actionable guide to firewall testing, covering best practices and tools, including how Cymulate supports continuous firewall security validation.
What is a Firewall?
A firewall is a network security device or software solution that monitors and controls incoming and outgoing network traffic based on pre-configured security rules. Acting as a barrier, a firewall helps protect an internal network by only permitting approved traffic. There are several types of firewalls, each with a distinct role in network security.
- Network firewalls: Network firewalls monitor traffic at the perimeter, using rules based on IP addresses, ports, and protocols. They can be hardware-based, software-based, or a hybrid solution. Network firewalls form a critical part of firewall security for most organizations.
- Web application firewalls (WAF): WAFs protect web applications by filtering and monitoring HTTP requests, helping to prevent web-based attacks like SQL injection and cross-site scripting (XSS).
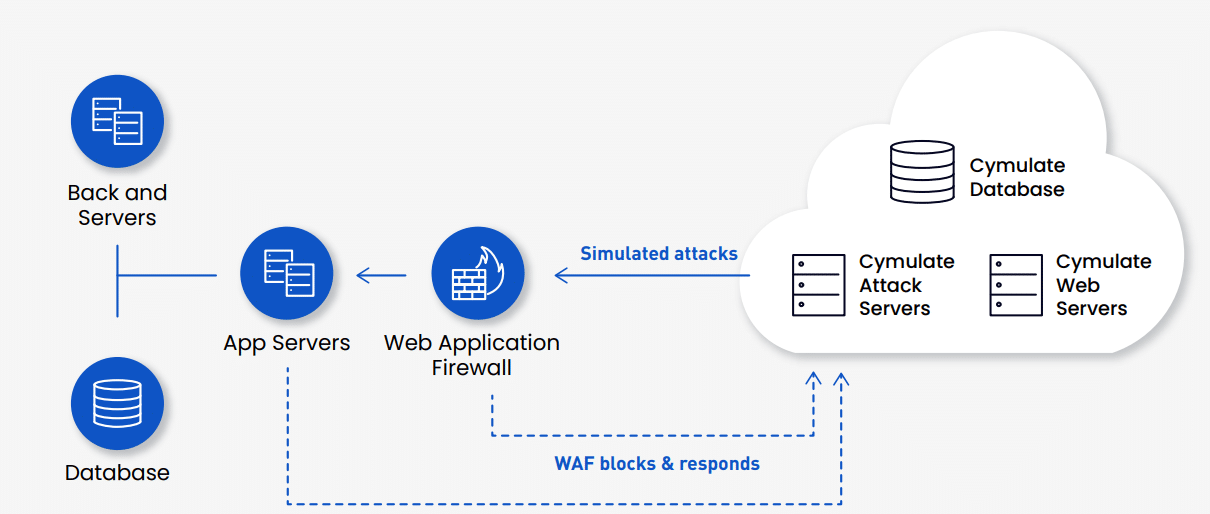
- Next-generation firewalls (NGFWs): NGFWs go beyond standard filtering, providing advanced features like application awareness, intrusion prevention, and deep packet inspection to more effectively address modern, complex threats.
Each type of firewall offers distinct capabilities, so organizations must select the right solution based on their specific network security requirements.
The Primary Purpose of a Firewall
Firewalls protect network security by enforcing policies, blocking unauthorized access, and segmenting networks.
- Enforcing security policies: Firewalls are vital for enforcing network security policies. By controlling traffic based on rules, firewalls ensure that only authorized users and activities can access sensitive resources. This makes firewall rules a cornerstone of secure network operations.
- Blocking unauthorized access: At their core, firewalls block unauthorized access, helping protect internal systems from potential breaches. By filtering out potentially harmful traffic, firewalls reduce the risk of malware infections, data breaches, and unauthorized access attempts.
- Maintaining network segmentation: Firewalls support network segmentation by creating isolated zones. This segmentation helps contain any security incidents in a specific area, preventing attackers from easily moving laterally across the network. Effective segmentation protects sensitive data and limits damage during a breach.
In summary, firewalls enforce rules that allow only trusted traffic into the network, providing a structured approach to protect sensitive assets and support robust network security.
Why You Need to Test Your Firewalls
Testing a firewall ensures it is configured correctly and can withstand evolving threats. Here’s why regular firewall testing is essential:
Identify misconfigurations: Misconfigurations are common and can create significant vulnerabilities. For example, a minor error in access control lists (ACLs) or firewall rules could permit unauthorized traffic. Firewall testing helps uncover and address these misconfigurations before they lead to security incidents.
Validate rule effectiveness: Regular testing validates that each firewall rule functions as intended and aligns with organizational security policies. For instance, a rule designed to block traffic from certain IP ranges should be rigorously tested to confirm its effectiveness. This ensures that the firewall is enforcing rules properly and safeguarding network security.
Enhance compliance: Many regulatory standards, including PCI DSS and HIPAA, mandate regular firewall testing as part of compliance. Organizations meet these compliance requirements by scheduling and documenting firewall testing and demonstrating a proactive approach to network security.
Improve incident response: Understanding how a firewall responds under various conditions enhances a security team’s ability to respond effectively to incidents. Regular testing provides insights into firewall behavior during attacks, leading to faster, more effective incident response.
How to Test Firewalls
Firewall testing involves various methods to assess the firewall’s functionality, rule configurations, and attack resistance.
Firewall Auditing
Firewall auditing is the first step in assessing firewall configuration and security. This process involves reviewing access control lists (ACLs), firewall rules, and configuration logs to ensure they align with security policies. For example, an audit might reveal unused or overly permissive rules that open pathways for unauthorized access. Regular auditing helps optimize firewall rules and align with organizational security policies, making it a foundational part of firewall security.
Primary Methods for Firewall Testing
- Rule-based testing: Rule-based testing evaluates specific firewall rules and policies to ensure they meet security objectives. For instance, rule-based testing confirms that these IP addresses are effectively blocked if an organization restricts access from specific IP ranges.
- Network scanning: Network scanning tools like Nmap can identify open ports, services, and configuration weaknesses that could expose the network. Scanning the network to detect open or misconfigured ports allows administrators to close unused or vulnerable ports, preventing unauthorized access points.
- Traffic simulation: Simulating legitimate and malicious traffic tests the firewall’s ability to distinguish between safe and harmful connections. For example, using tools like TCPreplay to simulate normal and attack traffic helps assess how the firewall processes and blocks suspicious patterns.
- Vulnerability scanning: Regular vulnerability scans detect any weak points in firewall software or firmware configurations. Tools like Nessus can identify vulnerabilities and ensure the firewall is up-to-date. Regular vulnerability scanning is essential for identifying exploitable weaknesses before attackers can target them.
Patching
Regularly updating the firewall’s firmware is critical, as updates frequently address security vulnerabilities. Hackers often exploit outdated firewall software, so timely patching ensures the firewall has the latest protections. Firmware updates should be a part of any firewall testing plan, as they are a fundamental component of ongoing firewall configuration and security management.
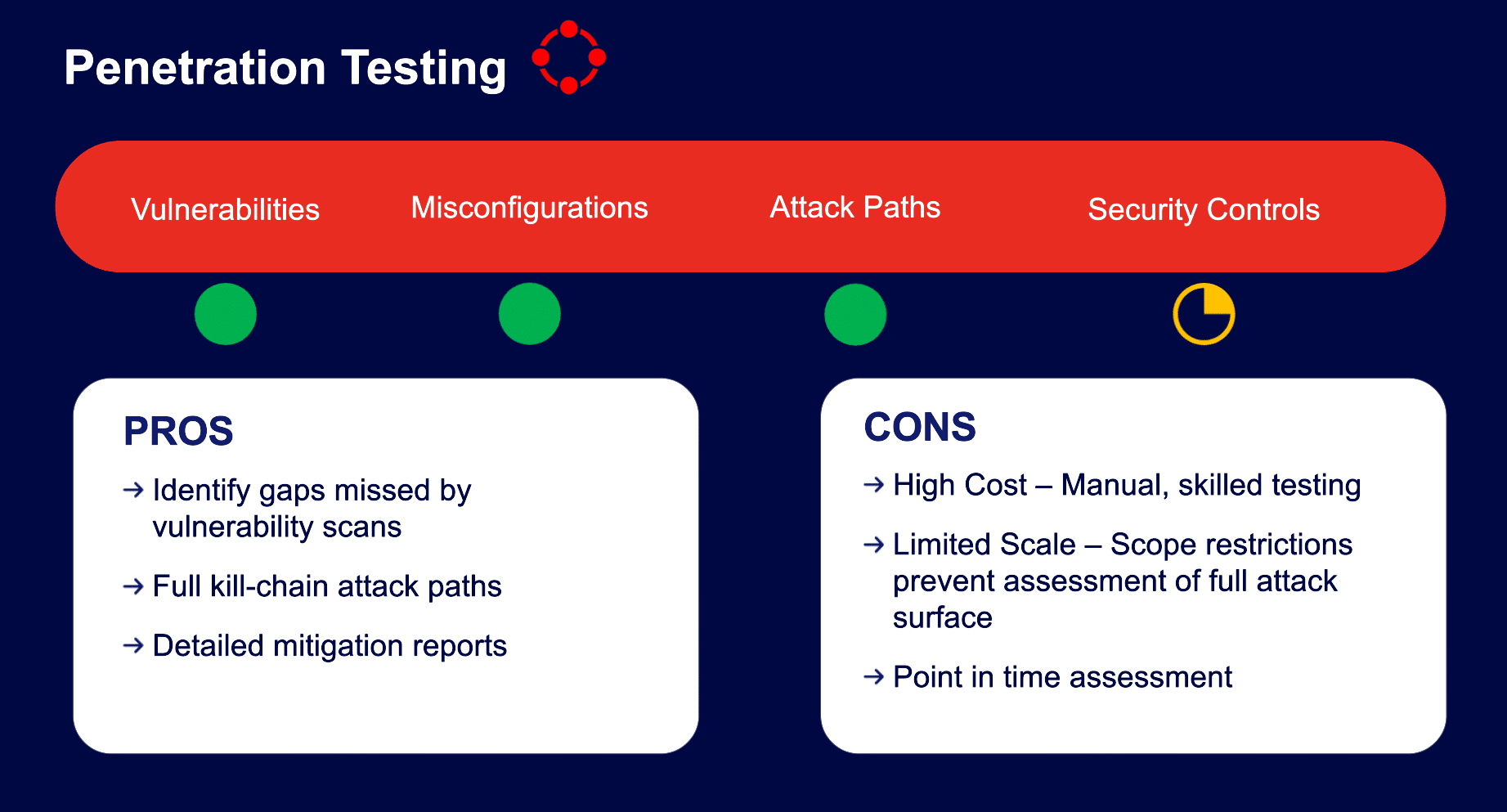
Penetration Testing for Firewalls
Penetration testing for firewalls is an advanced technique that simulates real-world attacks to assess the firewall’s resilience. Penetration testing identifies weak points by mimicking tactics that attackers would use to infiltrate the network.
Types of Penetration Testing for Firewalls
- External penetration testing: External testing evaluates firewall security outside the network, focusing on how well the firewall protects against external threats. This type of testing is crucial for understanding how the firewall prevents unauthorized access attempts.
- Internal penetration testing: Internal testing assesses firewall security from within the network, focusing on insider threats and configuration weaknesses. By evaluating how well internal security controls are enforced, organizations can ensure that sensitive data remains protected.
Common Firewall Penetration Testing Techniques
- Port scanning: Port scanning identifies open ports that attackers could exploit. Tools like Nmap and Netcat help detect open ports and verify whether firewall rules block access to vulnerable services effectively.
- Protocol and traffic anomalies: Testing the firewall’s response to abnormal traffic patterns, such as malformed packets or protocol-specific attacks, provides insight into how well it handles unexpected activity. This can identify weak points in protocol handling.
- Bypassing rules: Attempting to bypass firewall rules by exploiting misconfigurations reveals potential entry points. Weak access control lists may allow specific types of traffic to slip through undetected, which can be mitigated through regular testing.
Tools
Several tools support effective firewall penetration testing:
- Nmap: Useful for scanning open ports and identifying accessible services, helping to close potential access points.
- Metasploit: Provides a range of testing techniques to simulate different attack scenarios against firewall rules, assessing resilience.
- Netcat: Known as the “Swiss Army knife” of networking tools, Netcat facilitates testing by creating open connections to test ports and configurations.
Reporting and Remediation After Penetration Testing
Effective penetration testing requires thorough documentation and prioritized remediation steps. Reporting findings and planning remediation enables teams to address vulnerabilities and optimize firewall configuration, strengthening network firewall security.
How Cymulate Can Help
Cymulate provides a comprehensive exposure management platform for continuous security validation, supporting firewall testing, and helping organizations strengthen firewall security:
- Continuous security validation: Cymulate enables organizations to validate firewall configurations continuously, ensuring that firewall rules align with security policies and network security requirements.
- Automated testing: Cymulate automated testing allows security teams to conduct regular simulations to assess firewall performance and configuration. Automation minimizes manual intervention, allowing for consistent firewall testing.
- Real-time reporting and recommendations: Cymulate generates real-time reports that deliver actionable insights into firewall rules, configuration, and potential vulnerabilities. These reports provide prioritized recommendations, enabling teams to address issues efficiently and enhance firewall security.
Key Takeaways
Firewalls are essential to network security, but their effectiveness depends on regular testing and maintenance. By adhering to best practices and leveraging advanced tools, organizations can ensure their firewalls remain robust against evolving threats while aligning with compliance requirements and supporting incident readiness.
- Testing and maintenance: Routine testing helps uncover misconfigurations, validate rules, and maintain optimal performance. Regular updates to firewall firmware and rules are critical for addressing emerging threats.
- Best practices for security: Periodically review and document firewall configurations while enabling logging and monitoring to identify unusual traffic and troubleshoot effectively.
- Comprehensive testing methods: Employ a combination of rule-based testing, traffic simulations, and penetration testing to gain a full understanding of your firewall's capabilities and vulnerabilities.
- Cymulate role in validation: Cymulate enhances firewall security through continuous validation, automated testing, and actionable insights, helping organizations strengthen defenses and respond proactively to potential threats.