How to Keep Network Traffic Secure with Security Validation
Network traffic validation is key for safeguarding against cyber threats. Network controls like Intrusion Detection Prevention Systems (IDPS) are just like other security controls that must be validated by offensive testing to detect drift, optimize security posture, and prove cyber resilience. For advanced controls testing, Cymulate Breach and Attack Simulation Advanced Scenarios include network traffic simulation via replay of Packet Captures (PCAPs). These advanced capabilities empower organizations to identify gaps, optimize security posture, and strengthen defenses against malicious traffic.
Network Traffic Validation Traditional Approach
A common network traffic validation tactic is to replay packet captures (PCAPs) of a network system, such as a firewall, which tracks and records all the network packages sent through it. Replaying PCAPs for validation purposes verifies if control modification for mitigation had the desired effect.
However, this traditional PCAP replay approach is both risky and complex.
- PCAP Risks: PCAPs replay of known threats can include “callback” traffic to command and control a threat actor. So, unwittingly replaying compromised PCAPs can result in the organization accidentally flagging itself to the threat actor. If the remediation did not work, replaying the compromised PCAP signals to the threat actor that their attack is still usable.
- PCAP Complexity: Modifying PCAP files to remove identified threats requires specialized skills beyond many security teams. This increases the odds of broadcasting remaining exposure. Creating PCAPs from scratch would eliminate that risk but can be even more complex.
How Cymulate Revolutionizes Network Traffic Validation
The Cymulate platform offers robust validation of network controls by identifying exploitable security gaps with safe, scalable simulations. Cymulate includes network control validation with capabilities that cover:
- Network segmentation
- North-south traffic gateways
- East-west internal traffic
Validating Network Segmentation
Network segmentation is key to preventing threat actors from propagating their attack within the network after gaining an initial foothold. Cymulate continuous automated red teaming (CART) provides agentless validation of network traffic flow resilience. The Cymulate Hopper capability challenges the resilience of internal network configuration and segmentation policies against advanced techniques and methods used by threat actors to propagate within the network and control additional systems.
Validating North-South Traffic
The web gateway filters network traffic that enters or exits an organization’s internal network. The Cymulate BAS web gateway capability launches attack simulations to identify the web gateway’s exposure to risk and provide actionable guidance on remediation steps.
Validating East-West Traffic
East-west traffic refers to the internal traffic flow between servers, endpoints, and other systems within an organization’s internal network. To assess controls for this internal lateral communication, Cymulate offers network traffic validation features as part of BAS Advanced Scenarios. Cymulate assessment templates allow safe PCAP replay and generate simulated internal traffic flow to validate controls.

Fig 1: Network traffic validation templates available in Cymulate BAS Advanced Scenarios
PCAP Replays in Cymulate BAS Advanced Scenarios
To validate IDPS, Cymulate BAS Advanced Scenarios now includes network traffic validation templates. Like all templates in Cymulate BAS Advanced Scenarios, the new traffic simulation templates provide security validation that is:
- Automated
- Production safe
- Scalable
- Customizable
- Prescriptive
Automation – The template comes with pre-built tools and resources for PCAP replay. This enables the automation of lateral movement testing without requiring specialized skills or effort from the security team. With a few clicks, existing teams can run continuous east-west traffic simulations without expanding the team.

Fig 2: Network traffic validation automation dashboard
Production Safe – The pre-built simulated PCAP traffic contains no live malware payloads or threat actor callbacks. This allows replay testing directly in the production environment without risk of accidental infection or drawing threat actors’ attention.
Scale – The template includes an extensive and expanding library of over 500 attack scenario templates specialized for lateral testing. Each covers common tactics like pass-the-hash, remote code execution, Golden Ticket attacks, etc. This breadth allows automation at scale rather than one-off PCAP analysis.
Custom Options – Pre-built organization-specific testing automation and support the creation of customized organization-specific PCAPs. This enables security teams to customize and tune assessments that focus on the most potentially impactful exposure risk susceptible to lateral attacks.

Fig 3: Cymulate advanced scenarios resources
Prescriptive – Simulation reports provide actionable remediation advice for identified security gaps. This includes specific guidance, such as specifying which IDS signatures to add, which firewall configuration to adjust, which segment needs better insulation, etc. This remediation guidance saves considerable time and resources.
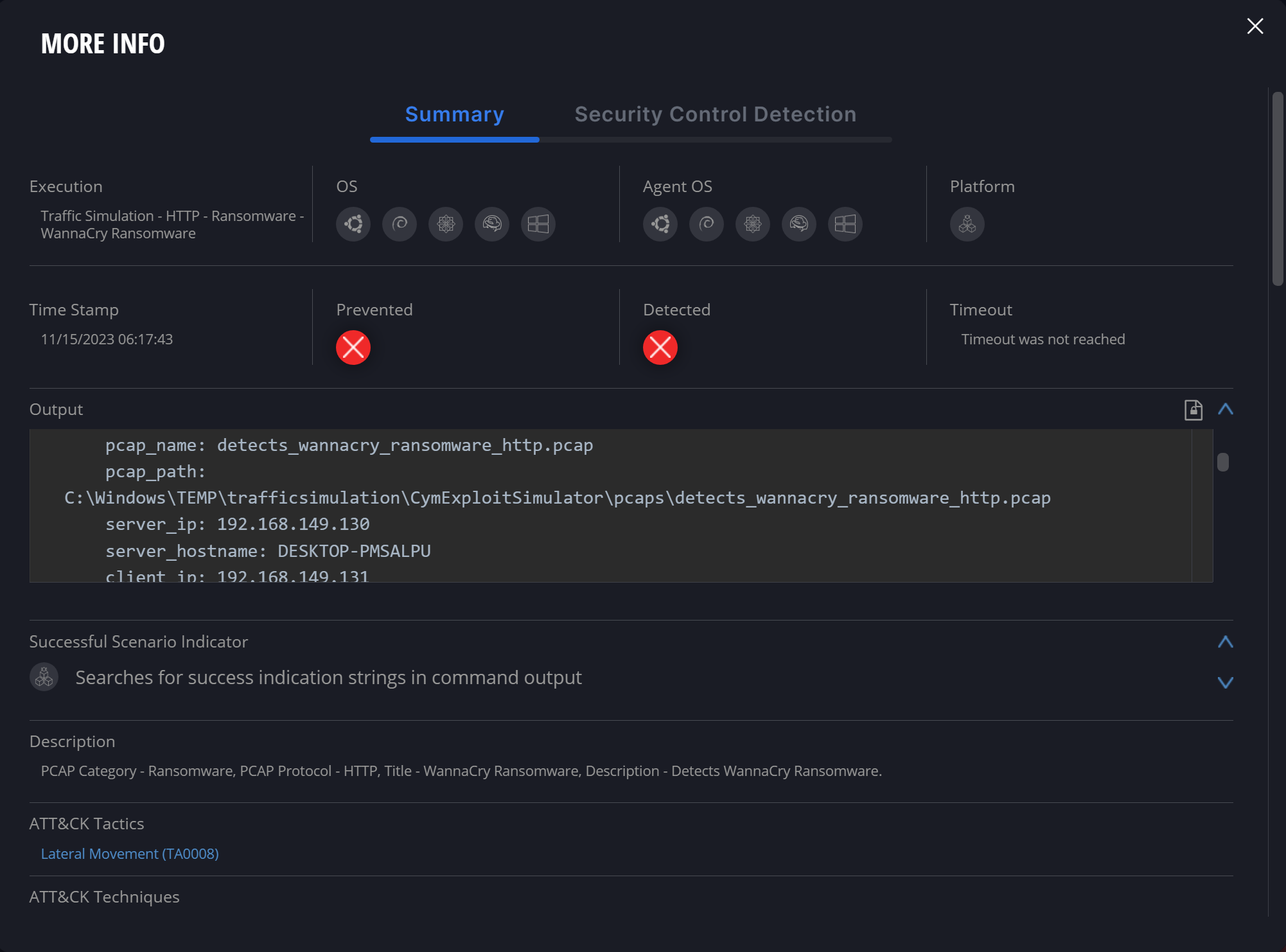
Fig 4: Detailed findings
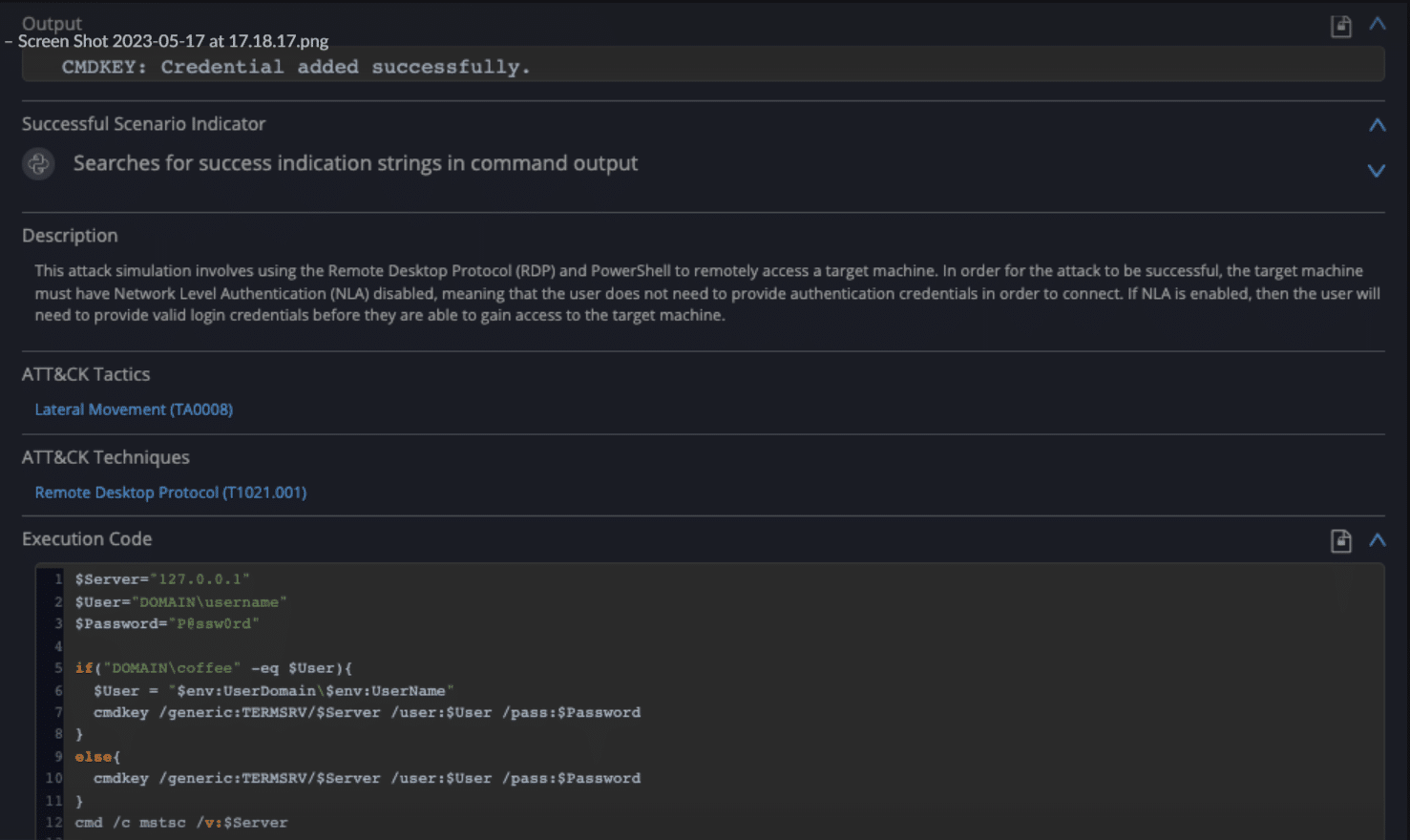
Fig 5: Remediation guidance
In conclusion, these purpose-built simulation templates remove traditional barriers of dangerous exposure, manual effort, and limited coverage during essential PCAP replay testing.
Key Takeaways
The network traffic validation template is only one of the many Cymulate Breach and Attack Simulation (BAS) Advanced Scenarios templates.
Cymulate BAS Advanced Scenarios is an open framework that enables the customization of chained cybersecurity assessments and automated testing for on-prem, cloud, and hybrid applications, environments, and infrastructure.
It includes a drag-and-drop wizard containing over two thousand customizable pre-encoded executions facilitating the creation of complex customized attack scenarios. That wizard also enables chaining with parameters from previous executions or external sources.