Understanding the Ins and Outs of Cybersecurity Exposure Management

Exposure management takes a proactive approach to identify, validate, prioritize and mitigate the vulnerabilities, configurations, control gaps and other weaknesses that create exposure risk. It aims to answer the critical question: "How exposed are we to cyber threats and potential breaches?" By integrating different parts of the cybersecurity program, exposure management strengthens cyber resilience, focusing on the risks with the greatest potential impact on the organization.
Key takeaways:
- Cybersecurity exposure management is a proactive framework that empowers security teams to manage exposure by identifying and fixing network vulnerabilities.
- The cyber threat exposure management (CTEM) cycle ranks cyber risk exposure by business impact, ensuring that organizations address the most dangerous threats first.
- Effective management of exposure transcends basic scanning, demanding continuous discovery and validation to guarantee no digital asset remains unguarded.
- The Cymulate Exposure Management Platform consolidates an automated workflow, providing security leaders with a validated, real-time view of actual risk.
What is exposure management?
Cybersecurity exposure management is the ongoing process of identifying and fixing vulnerabilities in your digital defenses before criminals can exploit them. The method monitors your entire digital footprint—from cloud storage to employee passwords—to catch threats early.
When done successfully, exposure management helps security teams to:
- Understand where the weak points are.
- Check if security tools and safety plans actually work.
- Know precisely how networks, clouds and apps are set up so nothing is hidden.
Exposure management vs. vulnerability management: What's the difference?
While some see exposure management as the next logical step after vulnerability management, the Continuous Threat Exposure Management (CTEM) concept draws a clear line between them. Exposure management must look forward to potential threats and focus on preventing actual business disruption.
It goes far beyond standard vulnerability management by adding scoping, validation and mobilization. To do this, security teams must move away from the old "scan-and-patch" routine toward a more integrated risk management platform that should:
- Align directly with business priorities.
- Include offensive testing to validate if risks are real.
- Prioritize actions based on actual danger to the company.
- Treat mitigation as a strategic optimization, not just a quick fix.
How does management of exposure work?
Management of exposure works as an ongoing cycle of improvement. To stay ahead of attackers, security teams follow a five-stage process that repeats constantly. The process ensures that as your business changes—adding new software, clouds, or employees—your security adapts right along with it.
Here is how the exposure management five stages work in practice:
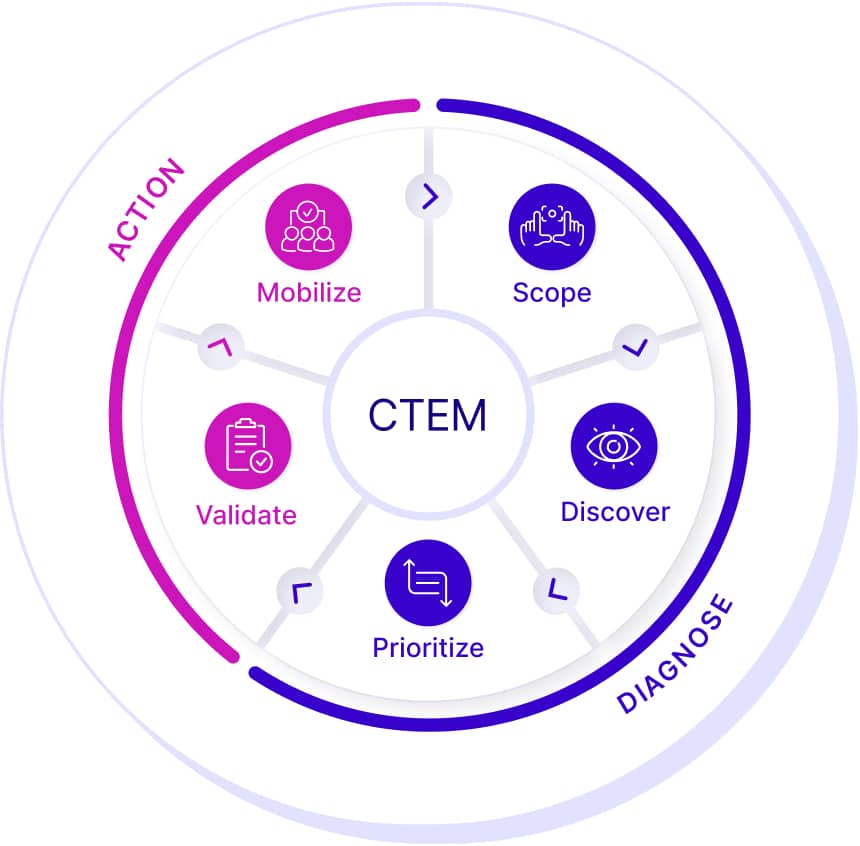
1. Scoping
Scoping lays the groundwork for effective exposure management programs by aligning the cybersecurity strategy with business risks, setting a clear focus and defining measurable goals and objectives. According to Gartner, continuous threat exposure management should operate in concurrent cycles of focus to enable iterative improvements.
In each cycle, scoping helps the organization determine what will be reviewed, narrowing the scope to reduce variables. It also establishes the business context and sets the criteria for success. This stage includes:
- Identify business operation risks: While the scope of exposure management may be technical (cloud, data, SaaS, etc.) or focused on a critical organization function, the scope must always consider potential impact to business operations.
- Baseline security posture: To deliver measurable results, exposure management must start with an understanding of where you are today. The baseline considers the full attack surface in scope (such as assets, clouds, systems, etc.) and correlates it with business risks.
- Define Risk Tolerance: Exposure management programs recognize that many vulnerabilities cannot be patched and remediation often involves business disruption. Aligning with the business on risk tolerance establishes the criteria and foundation for mitigation actions and determines the acceptability of disruption or risk.
2. Discovery
While scoping defines the business process itself, discovery identifies the systems, applications, and other resources that support that scope—even when those resources may not initially appear to fall within the scope. This constitutes the attack surface. The discovery phase creates a risk-profiled asset inventory of both the internal and external attack surface by identifying assets, classifying their business context and assessing their potential cyber risks. This stage includes:
- External discovery: Exposure management applies the attacker’s view to understand how the organization appears to the threat actor. This requires a comprehensive scan and discovery of the external attack surface, including web domains, IP addresses, web applications, databases supporting web applications and asset libraries or other code components visible to the outside world.
- Dark web discovery: Discovery also includes monitoring the dark web to find stolen data, confidential business information, sensitive personal details, or counterfeit products.
- Internal discovery: The goal of internal discovery is to uncover vulnerabilities and exploitable assets that contribute to exposure risk. This involves scanning the internal attack surface to identify assets an adversary could use to move from an initial foothold to critical assets or "crown jewels."
- Identify vulnerabilities and misconfigurations: Discovery should also focus on identifying vulnerabilities and misconfigurations across both external and internal systems that could expose the organization to attacks.
- Identify control weaknesses: Control weaknesses and gaps can be just as harmful as unpatched common vulnerabilities and exposures (CVE). Security programs that already incorporate control testing and validation should include these findings during the discovery phase of exposure management.
- Map attack paths: Attack path analyses map potential lateral movement paths across external and internal environments, highlighting risks from the chained exploitation of individual vulnerabilities.
- Consolidate exposures and create a risk-profiled asset inventory: Discovery should aggregate and analyze all findings into a unified view of exposure risk. Using this consolidated view of assets and exposures, organizations can create risk-profiled asset inventories that factor in the business context of each asset.
3. Prioritization
Prioritization in the management of exposure focuses on addressing the most likely threats. Unlike traditional vulnerability management, which relies on external factors such as CVSS scores and threat intelligence, it also considers internal factors such as compensating controls, business context and available mitigation options. This stage includes:
- Stack rank exposures: Effective prioritization involves ranking all exposures based on key factors such as risk, potential impact on business operations and threat intelligence related to active campaigns and targeted industries. While prioritization has traditionally been a challenge for vulnerability management, applying risk-based vulnerability management principles to all exposures becomes feasible when organizations start with a consolidated list and a risk-profiled asset inventory.
4. Validation
Validation is a key advantage of exposure management over traditional programs such as vulnerability management. It confirms exposure risk by evaluating the likelihood of an attack's success and its potential impact. While some argue that prioritization isn’t effective without validation, Gartner analyst Pete Shoard differentiates the two: prioritization acts as the “sort” function, while validation serves as the “filter.”
This validated risk filter enables security teams to focus remediation efforts on the exposures that pose the greatest risk. Legacy validation methods, such as periodic penetration tests and red team exercises, are limited. Exposure management emphasizes the need for continuous assessment, requiring automated technologies that provide broad coverage across the attack surface.
- Validate controls and response: Validating controls and optimizing responses are key ways exposure management improves security posture over time. For exposure risks, validation tests whether existing controls can mitigate attacks targeting those vulnerabilities. If a threat cannot be mitigated, assessments evaluate response processes and the ability to contain the threat. Exposures mitigated through compensating controls carry significantly lower risk.
- Validate threats: The disclosure of new high-severity vulnerabilities or the report of new exploits or active campaigns from threat actors often requires urgent testing to validate the risk to the organization.
- Validate attack paths: Attack path validation demonstrates how exposures and vulnerabilities can be exploited and the potential consequences of a compromised asset, such as lateral movement and privilege escalation. By validating these paths, security teams can confirm the viability of attacks and understand the overall potential damage a successful attack could cause.
5. Mobilization
The mobilization phase is the action-driven step of an exposure management program. It involves taking concrete actions to reduce organizational risk and strengthen security posture based on insights gathered during the process. Once fixes are implemented, their effectiveness should be validated to ensure they achieve the intended reduction in exposure and to identify any remaining security gaps.
- Plan remediation: Effective response is often not straightforward, especially for complex remediations that require collaboration and alignment across teams. A successful remediation plan should take into account the business impact of an exploited threat, the tradeoffs between remediation and mitigation along with available options, the potential disruptions caused by remediation efforts and the technical requirements of the proposed actions.
- Automate configuration updates: Whenever possible, automated remediation and mitigation through configuration and control updates offer a quick and efficient response. This approach frees up valuable human resources to concentrate on more complex remediation processes.
- Managing the remediation process: The final step involves creating and assigning specific remediation tasks to designated owners, ensuring accountability to drive execution. Tracking task completion through metrics and dashboards is essential for monitoring progress and confirming that risk reduction goals are achieved.
Key solutions for online exposure management
Exposure management differs from traditional vulnerability management by incorporating the attacker's perspective of an organization's assets—something traditionally provided by penetration tests. Now, advanced tools can automate this offensive security mindset, delivering automation, analytics and actionable insights to help organizations manage exposure effectively.
Breach and attack simulation (BAS)
BAS tools answer the question: "How well are my security controls and processes performing?" They launch simulated attacks and correlate the findings with security controls (email and web gateways, WAF, endpoints and others) to provide mitigation guidance. BAS solutions are instrumental during the prioritization and validation stages.
Continuous automated red teaming (CART)
Continuous automated red teaming (CART) goes beyond the ASM reconnaissance phase to answer the question: "How can an adversary breach my defenses and internal segmentation?" CART tools simulate an end-to-end campaign attempting to penetrate the organization by analyzing exposed vulnerabilities and autonomously deploying attack techniques that penetrate the network. CART solutions are instrumental during the prioritization and validation stages.
Exposure analytics
Exposure analytics tools automate the data collection, aggregation and exposure intelligence across enterprise IT, clouds and the security stack. The platform aggregates intelligence from vulnerability management systems, asset inventories, clouds and security controls across the IT infrastructure.
Data are aggregated to contextualize information, facilitate risk assessment, prioritize remediation and measure and optimize cyber resilience. Exposure analytics solutions are instrumental during the scoping, discovery, prioritization and mobilization stages.
The benefits of cyber threat exposure management
Implementing an exposure management cybersecurity program within an organization offers numerous benefits:
- Reduced risk of data breaches: By proactively identifying and addressing vulnerabilities, organizations can significantly reduce the risk of successful cyberattacks, safeguard sensitive data and protect their reputation. Exposure management allows organizations to stay ahead of emerging threats and continuously improve their security posture.
- Improved compliance with security regulations: Addressing exposure in risk management helps organizations ensure compliance with industry-specific security regulations and standards. This avoids legal consequences and builds trust with customers and stakeholders. Compliance with security regulations is critical for organizations operating in highly regulated industries, such as finance, healthcare and government.
- Improved cyber insurance conditions: The ability to document efforts to reduce exposure and proactively remediate security gaps is instrumental in facilitating negotiations with cyber insurance underwriters, potentially resulting in lower premiums and expanded coverage.
- Increased efficiency in security operations: Focusing on the most critical security gaps, risk exposure management enables organizations to allocate resources effectively, streamline security operations and optimize their overall cybersecurity strategy.
- Improved decision-making about security investments: Insights into organizations’ security posture help them make informed decisions regarding security investments, ensuring resources are allocated where they are most needed.
- Increased involvement of all stakeholders: Cymulate's Data Breach Survey indicated that regular meetings between executives and cybersecurity teams reduce the risk of a breach. Integrating exposure analytics directly ties cybersecurity with the non-IT executive-level stakeholders and increases their involvement in shoring up security.
Common challenges in implementing exposure management
While the benefits are clear, actually building an exposure management cybersecurity program can be difficult. Organizations often face specific challenges:
- Siloed teams: Security, IT and development teams often work in isolation. Without a unified platform, departments struggle to share data, leading to slow response times and missed risks.
- Data overload: Scanners generate thousands of alerts every day. Without automated prioritization, analysts quickly become overwhelmed by "alert fatigue" and may miss critical threats amid the noise.
- Fragmented tools: Companies often use separate tools for cloud security, vulnerability scanning and red teaming. The fragmentation of the tools forces the team to manually piece together reports, creating blind spots in the security posture.
- Lack of visibility: Modern networks change constantly. Security leaders often struggle to maintain an up-to-date inventory of all assets, especially "shadow IT" or unauthorized cloud instances that employees spin up.
Get the best Exposure Management Platform with Cymulate
Cymulate understands the importance of integrating siloed SecOps functions with supporting technologies to drive exposure management from scoping to mobilization. To assist security teams on their journey, the Cymulate Exposure Management Platform unites essential technologies, including:
- Breach and attack simulation (BAS)
- Automated red teaming (CART)
- Exposure analytics
- Security control validation
Take the next step and stop guessing where your risks are. Book a demo and discover how the Cymulate Exposure Management Platform works.
Frequently asked questions
Most platforms focus on isolated silos, such as vulnerability management or cloud security dashboards. While these platforms provide specific data, they often leave CISOs with a fragmented view of risk.
Cymulate solves this challenge with a unified exposure management dashboard. By integrating scoping, discovery and validation into a single interface, our platform provides leaders with a complete, validated view of their security posture, enabling them to prioritize remediation based on actual business impact rather than isolated data points.
In cybersecurity, exposure refers to the total attack surface available to a threat actor. While a vulnerability is a specific flaw (a software bug), exposure encompasses the broader context, such as misconfigured cloud settings, exposed identity credentials or open ports, that allows an adversary utilizing a specific attack model to reach and exploit that flaw. Managing exposure means looking beyond the bug itself to identify and close the open doors across the entire IT environment before an attack occurs.


