Frequently Asked Questions
Defending Against SCATTERED SPIDER & Advanced Threats
What is SCATTERED SPIDER and why is it a significant threat?
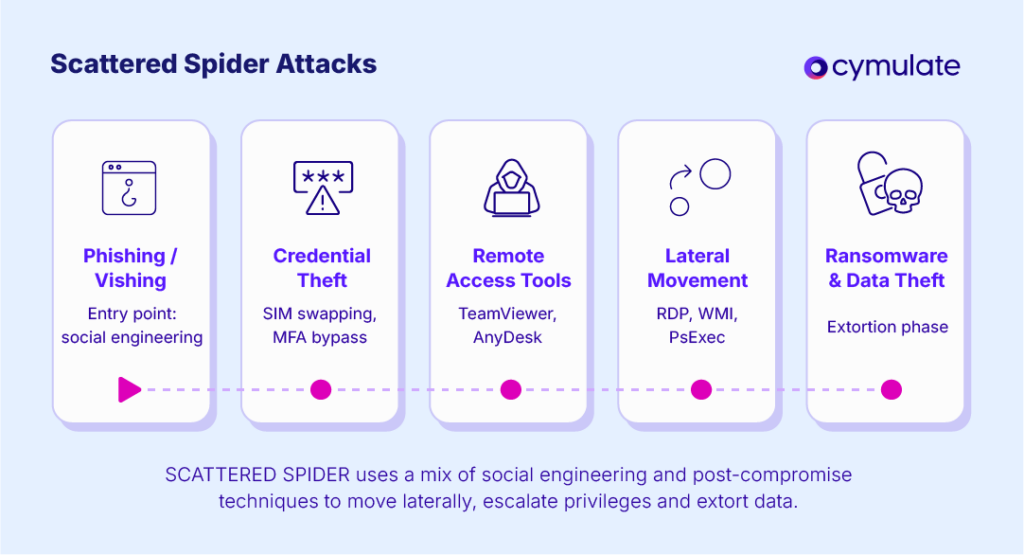
SCATTERED SPIDER is a prolific eCrime group, also known as Roasted 0ktapus, Octo Tempest, and Storm-0875. Since early 2022, they have conducted over 100 targeted attacks across industries such as telecommunications, finance, retail, and gaming. Their tactics include SIM swapping, MFA bypass, Active Directory abuse, credential harvesting, lateral movement, and ransomware deployment, making them a hybrid threat that requires advanced, continuous validation of security controls. Source
How does Cymulate help organizations defend against SCATTERED SPIDER attacks?
Cymulate enables organizations to automate breach and attack simulations that mimic SCATTERED SPIDER's real-world tactics, techniques, and procedures (TTPs). This includes credential dumping, lateral movement, privilege escalation, and social engineering scenarios. By running these simulations, organizations can validate their security controls, identify detection gaps, and receive actionable remediation guidance to strengthen their defenses. Source
What specific SCATTERED SPIDER techniques can Cymulate simulate?
Cymulate can simulate credential dumping (e.g., Mimikatz usage), lateral movement using tools like PsExec, RDP, or WMI, privilege escalation and persistence via registry modifications or scheduled tasks, and the use of legitimate IT tools (LOLBins). These scenarios are mapped to MITRE ATT&CK techniques for comprehensive coverage. Source
How does Cymulate test for phishing and social engineering resilience?
Cymulate's Email Gateway assessments and Employee Awareness simulation modules allow organizations to send realistic, customizable phishing emails, evaluate user susceptibility, track click-through rates, and identify gaps in email filtering and user awareness. This helps organizations assess and improve their defenses against social engineering attacks commonly used by SCATTERED SPIDER. Source
What kind of remediation guidance does Cymulate provide after simulations?
After running a simulation, Cymulate provides detailed risk scores, highlights configuration weaknesses, and offers specific detection rule enhancements such as Sigma rules or EDR tuning suggestions. This actionable guidance accelerates the hardening of defenses and helps organizations proactively address vulnerabilities. Source
How does Cymulate keep simulations up to date with the latest threats?
Cymulate regularly updates its threat intelligence feeds with the latest indicators of compromise (IOCs) and TTPs from groups like SCATTERED SPIDER. This ensures that simulations reflect current adversary behaviors, enabling real-time validation against emerging threats. Source
Can Cymulate help with lateral movement and privilege escalation testing?
Yes, Cymulate offers Lateral Movement and Privilege Escalation scenarios that safely test whether attackers could move laterally within your network, mimicking how SCATTERED SPIDER operates post-compromise. These simulations help assess segmentation policies, privilege abuse detection, and SOC response effectiveness. Source
How does Cymulate support continuous validation of security controls?
Cymulate enables organizations to continuously test, measure, and strengthen their defenses by automating production-safe breach and attack simulations. This ongoing validation ensures that security controls remain effective against evolving threats like SCATTERED SPIDER. Source
What customer feedback is available regarding Cymulate's effectiveness against advanced threats?
Jason Barford, Senior Manager, Governance Risk & Compliance at Domino's Pizza UK, stated: “Cymulate enables me to present our cybersecurity posture in terms of an attacker's journey. It came to life with our senior stakeholders when we were able to demonstrate our capability against the Scattered Spider attacks. The team has been quick to work with us on improvements.” Source
How does Cymulate help organizations move from reactive to proactive security?
Cymulate empowers security teams to proactively validate their defenses, identify vulnerabilities, and optimize their security posture. By simulating real-world threats and providing actionable insights, organizations can shift from reactive incident response to proactive risk management. Source
What is the Cymulate Exposure Validation Platform?
The Cymulate Exposure Validation Platform is a solution that automates production-safe breach and attack simulations, allowing organizations to validate their security controls against the latest threat tactics and real-world attack techniques. It is designed to be fast, easy to use, and effective for building custom attack chains. Learn more
How does Cymulate integrate with MITRE ATT&CK?
Cymulate's attack scenarios and simulations are mapped to MITRE ATT&CK techniques, ensuring comprehensive coverage of adversary behaviors and enabling organizations to validate their defenses against tactics used by groups like SCATTERED SPIDER. Learn more
What is lateral movement and how does Cymulate help prevent it?
Lateral movement refers to an attacker's ability to move within a network after initial compromise. Cymulate helps prevent lateral movement by simulating these attack paths, testing segmentation policies, and providing actionable insights to strengthen internal defenses. Read more
How does Cymulate's Email Gateway assessment work?
Cymulate's Email Gateway assessment sends realistic, customizable phishing emails to test user awareness and the effectiveness of email filtering solutions. It tracks user interactions and identifies vulnerabilities in email security controls. Learn more
What is privilege escalation and how does Cymulate test for it?
Privilege escalation is when an attacker gains higher-level permissions within a system. Cymulate tests for privilege escalation by simulating common techniques such as registry modifications or scheduled tasks, helping organizations identify and remediate weaknesses in access controls. Glossary
How does Cymulate help organizations respond to ransomware threats?
Cymulate simulates ransomware deployment and data exfiltration techniques, allowing organizations to test their detection and response capabilities. The platform provides actionable guidance to close gaps and improve resilience against ransomware attacks. Glossary
What is the benefit of continuous threat intelligence integration in Cymulate?
Continuous threat intelligence integration ensures that Cymulate's simulations are always aligned with the latest adversary tactics, enabling organizations to validate their defenses against current and emerging threats in real time. Source
How does Cymulate help organizations measure their security posture?
Cymulate provides detailed risk scores and executive-level reporting that demonstrate an organization's security posture in terms of an attacker's journey. This helps communicate risk and improvement areas to stakeholders. Source
What is the role of user awareness in defending against SCATTERED SPIDER?
User awareness is critical because SCATTERED SPIDER often uses social engineering and phishing to gain initial access. Cymulate's Employee Awareness modules help organizations test and improve user resilience to these tactics. Source
How does Cymulate's platform support executive reporting?
Cymulate provides executive-level reporting that visualizes the organization's security posture and demonstrates improvements over time, making it easier for senior stakeholders to understand and act on cyber risk data. Source
Features & Capabilities
What are the key features of Cymulate's platform?
Cymulate offers continuous threat validation, a unified platform combining Breach and Attack Simulation (BAS), Continuous Automated Red Teaming (CART), and Exposure Analytics, attack path discovery, automated mitigation, AI-powered optimization, complete kill chain coverage, ease of use, and an extensive threat library with over 100,000 attack actions updated daily. Learn more
How does Cymulate's exposure validation reduce cyber risk?
Exposure validation identifies and closes security gaps before adversaries can exploit them. By validating exposures across endpoints, identities, networks, and configurations, Cymulate helps teams prioritize and remediate critical weaknesses, minimizing the attack surface and lowering breach risk. Learn more
What integrations does Cymulate support?
Cymulate integrates with a wide range of security technologies, including Akamai Guardicore, AWS GuardDuty, BlackBerry Cylance OPTICS, Carbon Black EDR, Check Point CloudGuard, Cisco Secure Endpoint, CrowdStrike Falcon, Wiz, SentinelOne, and more. For a full list, visit the Partnerships and Integrations page.
How easy is Cymulate to implement and use?
Cymulate is designed for quick, agentless deployment with no need for additional hardware or complex configurations. Customers can start running simulations almost immediately, and the platform is praised for its intuitive interface and actionable insights. Schedule a demo
What feedback do customers give about Cymulate's ease of use?
Customers consistently praise Cymulate for its ease of use, intuitive dashboard, and accessible support. For example, Raphael Ferreira, Cybersecurity Manager, said, “Cymulate is easy to implement and use—all you need to do is click a few buttons, and you receive a lot of practical insights into how you can improve your security posture.” Read more testimonials
What security and compliance certifications does Cymulate hold?
Cymulate holds SOC2 Type II, ISO 27001:2013, ISO 27701, ISO 27017, and CSA STAR Level 1 certifications, demonstrating robust security, privacy, and cloud compliance practices. Learn more
How does Cymulate ensure data security and privacy?
Cymulate uses encryption for data in transit (TLS 1.2+) and at rest (AES-256), hosts data in secure AWS data centers, and follows a strict Secure Development Lifecycle (SDLC) with regular vulnerability scanning and third-party penetration testing. The platform is GDPR-compliant and includes mandatory 2FA, RBAC, and IP restrictions. Learn more
What is Cymulate's pricing model?
Cymulate uses a subscription-based pricing model tailored to each organization's needs. Pricing depends on the chosen package, number of assets, and selected scenarios. For a personalized quote, schedule a demo.
What are the measurable benefits of using Cymulate?
Organizations using Cymulate have reported up to a 52% reduction in critical exposures, a 60% increase in team efficiency, and an 81% reduction in cyber risk within four months. Read the Hertz Israel case study
How does Cymulate compare to other security validation platforms?
Cymulate stands out with its unified platform combining BAS, CART, and Exposure Analytics, continuous 24/7 validation, AI-powered optimization, and an extensive, frequently updated threat library. It is recognized for ease of use and measurable outcomes, such as significant reductions in cyber risk and improved operational efficiency. See comparisons
Who can benefit from using Cymulate?
Cymulate is designed for CISOs, security leaders, SecOps teams, red teams, and vulnerability management teams in organizations of all sizes and industries, including finance, healthcare, retail, media, transportation, and manufacturing. Learn more
What educational resources does Cymulate provide?
Cymulate offers a Resource Hub with whitepapers, product info, and thought leadership, a blog for the latest threats and research, a glossary of cybersecurity terms, and webinars and events for ongoing education. Resource Hub
Where can I find Cymulate's latest news, research, and events?
You can stay updated through Cymulate's blog, newsroom, and events page. These resources cover the latest threats, research, media mentions, and upcoming webinars. Blog | Newsroom | Events
How does Cymulate address the needs of different security roles?
Cymulate tailors its solutions for CISOs (providing metrics and risk prioritization), SecOps teams (automating processes and improving efficiency), red teams (offensive testing with a large attack library), and vulnerability management teams (automated validation and prioritization). Learn more
What is Cymulate's mission and vision?
Cymulate's mission is to transform cybersecurity by enabling organizations to proactively validate defenses, identify vulnerabilities, and optimize their security posture. The vision is to create a collaborative environment for lasting improvements in cybersecurity strategies. About Us
Where can I find case studies and customer success stories for Cymulate?
Cymulate features a variety of case studies across industries, such as Hertz Israel's 81% cyber risk reduction and a credit union's improved threat prevention. Explore more at the Case Studies page.