Credential Compromise
Credential compromise is one of the biggest cybersecurity threats today. Hackers use stolen usernames and passwords to break into accounts, steal data, and launch further attacks. Once inside, they can access sensitive information, install malware, or even take over entire systems.
Attackers commonly use phishing, data breaches, credential stuffing, and brute force attacks to steal login credentials. A single exposed password can open the door to widespread damage, from financial loss to operational disruption. Strong authentication, regular password updates, and employee awareness are critical for preventing a credential compromise attack.
What is Credential Compromise?
Credential compromise happens when hackers gain unauthorized access to authentication credentials. These include usernames, passwords, API keys, and other login details. Once stolen, attackers can use these credentials to access larger systems, steal data, or escalate their credential validation attacks.
Stolen credentials are often a gateway to a large-scale cyber-attack. Attackers use them to:
Steal sensitive data – customer records, financial details, and intellectual property.
- Deploy ransomware – locking critical systems until a ransom is paid.
- Commit fraud – making unauthorized transactions or impersonating employees.
- Damage reputations – losing customer trust and facing legal consequences.
The impact of compromised credentials goes beyond unauthorized access—real-world breaches have shown how a single stolen password can lead to widespread disruption and financial loss.
In 2021, Colonial Pipeline suffered a massive ransomware attack because of a single compromised password. Hackers used stolen credentials to access the company’s network. Once inside, they deployed ransomware that shut down fuel supplies along the U.S. East Coast for days. The company had to pay a multi-million dollar ransom to regain control. This attack exposed how weak credential security can lead to large-scale consequences.
In 2022, Uber faced a serious security breach when an attacker purchased stolen credentials online. Using these login details, they gained access to internal systems, including company tools and sensitive data.
The breach exposed critical vulnerabilities in Uber’s security controls. It proved that even a single leaked password, if not properly protected, can lead to a major cybersecurity incident.
How Do Credentials Become Compromised?
Hackers use various methods to compromise credentials:
- Phishing attacks: Attackers trick users into revealing their login details by sending fraudulent emails, texts (smishing), or website links that appear legitimate. When users enter their credentials, hackers steal them. Phishing credentials are one of the most common and effective credential theft methods.
- Social Engineering: Attackers manipulate their targets to reveal their credentials either by phone, in-person or through other means
- Brute-force attacks: Hackers use automated tools to guess weak passwords (also known as password spraying). They try millions of combinations until they find the right one. Short or simple passwords are easy targets.
- Credential stuffing: Despite warnings, many people still reuse passwords across multiple sites. When hackers steal login details from one breach, they will commonly test them on other accounts. If users repeat passwords, attackers can gain easy access to a number of their platforms.
- Man-in-the-middle (MitM) attacks: Hackers intercept login credentials during transmission. This often happens over unsecured Wi-Fi or compromised networks. Attackers eavesdrop on login sessions and steal usernames and passwords.
- Malware & keyloggers: Malware infects devices and records keystrokes. Keyloggers silently capture login details and send them to hackers. These threats often come from malicious email attachments or fake software downloads.
- Dark web credential dumps: Hackers may sell stolen credentials on the dark web. Cybercriminals buy these login details and use them for additional attacks.
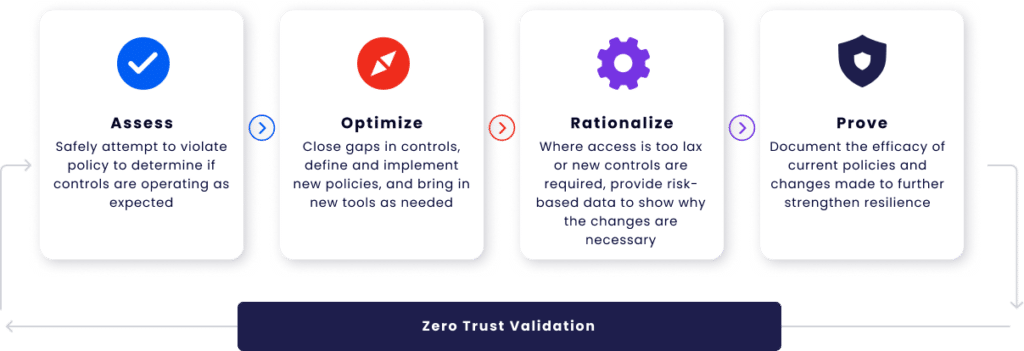
The Role of Zero Trust in Preventing Credential Compromise
The zero-trust security model operates under the assumption that no user, device, or system can be trusted by default. It requires continuous verification of identities, devices, communications, and transactions. Adopting a zero-trust mindset is crucial for any organization who wants to prevent credential compromise attacks.
Key zero trust principles are:
- Never trust, always verify – Every login and request must be authenticated.
- Least privilege access – Users only get access to what they need.
- Micro-segmentation – Limits how far attackers can move if they break in.
Zero trust relies on adaptive authentication, which analyzes real-time risk factors before granting access. It looks at:
- User location and device
- Login behavior patterns
- Access history and anomalies
If anything appears to be suspicious—like a login from a new country or an unusual IP address—the system asks for extra verification, such as multi-factor authentication (MFA). Continuous monitoring ensures threats don’t slip through. Security tools detect unusual activity, flag compromised credentials and block unauthorized access automatically.
7 Rules for Avoiding Compromised Credentials Attacks
By implementing a combination of strong authentication, proactive monitoring, and security best practices, it’s possible to significantly reduce the risk of credential compromise:
1. Use multi-factor authentication (MFA)
Even if hackers steal a password, they can’t access accounts without the second factor, like a one-time code or biometric verification. However, some attackers attempt MFA bypass techniques, such as phishing, SIM swapping, or exploiting misconfigured authentication systems. This makes it crucial to use strong, phishing-resistant MFA methods like hardware tokens or Fast IDentity Online 2 (FIDO2) authentication.
2. Enforce strong password policies
Weak and reused passwords are easy targets. Organizations should:
- Require long, complex passwords.
- Ban commonly used passwords.
- Prevent credential reuse across accounts.
- Use automated tools to enforce these rules.
3. Implement least privilege access
Limit the number of people who have access to sensitive systems. Give employees only the access they need to do their jobs. This reduces the damage an attacker can do with stolen credentials through privilege escalation.
4. Regularly rotate passwords and credentials
Frequent password changes help prevent long-term exposure. If credentials are leaked, rotation ensures they become useless to attackers. Set expiration policies for passwords, API keys, and privileged accounts.
5. Use password managers
Password managers store and generate strong, unique passwords for each account. Employees don’t have to remember complex passwords, reducing the risk of weak or reused credentials.
6. Monitor for credential leaks
Use dark web monitoring to detect if company credentials have been exposed. Security validation tools can also check for compromised accounts and force password resets before hackers exploit them.
7. Train employees on phishing awareness
The ever-present phishing threat continues to be a major breach entry point, even with significant investments in email security. Employees are the first line of defense against such attacks, making it crucial to regularly test their alertness and awareness of emerging phishing techniques through efficient pre-emptive measures. Employees should learn to:
- Identify suspicious emails and links.
- Avoid entering credentials into unverified sites.
- Report phishing attempts immediately.
Preventing Credential Compromise with Cymulate
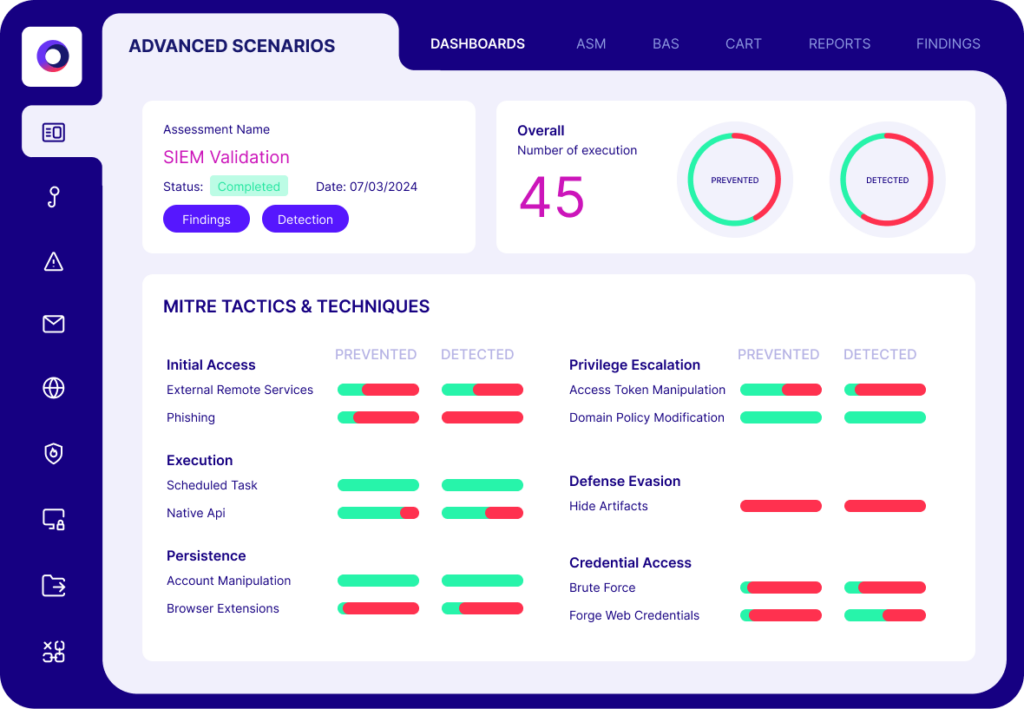
The Cymulate Security Validation and Exposure Management Platform simulates thousands upon thousands of cyber-attacks to verify that zero trust segmentation functions as intended. It continuously assesses segmentation from multiple perspectives and provides actionable insights to strengthen security postures. Key capabilities include:
Comprehensive segmentation validation, covering:
- User access control
- Attack path mapping
- Data protection
Customizable attack simulation templates to match unique security needs
Automated reporting with:
- In-depth analysis of security gaps
- Actionable mitigation guidance for faster remediation
Schedulable and repeatable attack templates to support continuous zero trust validation
Integration with SIEM and SOAR solutions
Cymulate integrates seamlessly with security information and event management (SIEM) and security orchestration, automation, and response (SOAR) systems. This integration automates the detection and response to credential threats, ensuring swift action to neutralize potential compromises.
By automating these processes, organizations can maintain a robust security posture with reduced manual intervention. Incorporating Cymulate into your security strategy provides a proactive approach to identifying and mitigating credential-based threats. By leveraging its comprehensive features, organizations can strengthen their defenses and reduce the risk of credential compromise.
Key Takeaways
Credential compromise, by definition, is one of the biggest cybersecurity threats today. Stolen credentials give attackers an easy way into critical systems, leading to data breaches, ransomware attacks, and financial loss. Organizations can’t afford to rely on passwords alone. To stay protected, organizations must:
- Enforce multi-factor authentication to block unauthorized access.
- Use strong password policies to prevent weak or reused passwords.
- Limit access with least privilege principles.
- Monitor for credential leaks
- Train employees to spot phishing attacks and social engineering scams