Cybersecurity Reconnaissance
Cybersecurity reconnaissance is the first phase of a cyberattack, where attackers gather intelligence about a target’s systems, networks, and vulnerabilities. The objective is to build a detailed profile of the target, identifying network architecture, open ports, technologies in use, and potential weaknesses—all while staying undetected.
Attackers use public sources like company websites, DNS records, social media, and leaked credentials, alongside technical scanning of networks and applications. This reconnaissance phase informs later attack stages, such as exploitation and intrusion, making it a critical part of the cyber attack lifecycle.
For defenders, understanding reconnaissance is essential—it allows security teams to identify and mitigate exposures before attackers exploit them. While reconnaissance itself does not cause damage, it is a key adversarial tactic recognized in security frameworks like MITRE ATT&CK. In short, reconnaissance sets the stage for an attack, making proactive defense crucial.
Types of Cyber Reconnaissance: Passive vs. Active
Reconnaissance techniques fall into two broad categories: passive reconnaissance and active reconnaissance.
These approaches differ in how attackers gather information and the risk of detection associated with each. Both play a role in adversarial reconnaissance (and in red teaming strategies used by ethical hackers), but they involve distinct tactics.
Passive Reconnaissance
Passive reconnaissance involves covert information gathering without directly interacting with the target. Attackers collect data from publicly available sources without sending any requests to the target's infrastructure. Key characteristics of passive reconnaissance:
- Relies on publicly available data – OSINT (Open Source Intelligence), company websites, search engines, social media, and Shodan searches.
- Stealthy – Difficult for the target to detect since there is no direct interaction.
- Limited technical details – Passive recon can identify broad details but lacks in-depth insights into network configuration or vulnerabilities.
Passive reconnaissance involves gathering information about a target without directly engaging with it. Examples include OSINT techniques such as Google dorking, WHOIS lookups, and analyzing certificate transparency logs to uncover publicly available data. Corporate research can provide valuable insights by examining job postings, company press releases, and discussions on public forums.
Attackers using passive reconnaissance operate like digital eavesdroppers, gathering information quietly from search engines, social media, and leaked databases. For example, they may scrape LinkedIn profiles to identify IT staff or use WHOIS queries to find IP ranges associated with a company.
Since passive reconnaissance does not trigger security logs or alerts, it is difficult to detect. However, its limitation is that attackers cannot see hidden configurations or internal vulnerabilities without directly probing the target.
Active Reconnaissance
Active reconnaissance involves direct interaction with the target system to extract detailed technical information. Attackers probe networks, scan for open ports, and interact with services to identify security weaknesses. Key characteristics of active reconnaissance:
- Engages with the target infrastructure – Sends queries, scans, or probes to collect data.
- Intrusive and detectable – Leaves logs and may trigger security alerts.
- Reveals deep system details – Can uncover running services, software versions, and misconfigurations.
Active reconnaissance involves directly interacting with a target system to gather information. This includes network scanning with tools like Nmap to identify active hosts and open ports, as well as port scanning to determine running services.
Unlike passive methods, active reconnaissance interacts with the target directly. This can include performing ping sweeps to identify live hosts, scanning for open ports and services, or using traceroute to analyze network paths. Because these actions involve sending requests, they are more likely to be noticed by intrusion detection systems (IDS) or firewalls.
Attackers try to minimize detection by using slow, distributed scanning techniques, but active recon always carries the risk of exposure. The benefit, however, is much richer data – attackers can determine exact software versions, operating systems, and potential exploits for identified vulnerabilities.
Comparison Table: Passive vs. Active Reconnaissance
| Passive Reconnaissance | Active Reconnaissance |
|---|---|
| Covert information gathering with no direct interaction with the target. | Overt information gathering that directly engages the target’s systems. |
| Relies on publicly available data and observation (e.g., OSINT, social media, search engine dorking) | Involves probing the target’s infrastructure (e.g., network scanning, DNS enumeration, vulnerability scanning). |
| Stealthy – Difficult for the target to detect since there’s no direct contact. | Intrusive – More likely to trigger logs or alerts on the target’s systems (higher risk of detection). |
| Limited technical details (cannot enumerate everything without touching the system). | Can reveal detailed system information (running services, software versions, configurations). |
| Examples: OSINT research, WHOIS lookups, metadata analysis, social engineering. | Examples: Nmap port scans, banner grabbing, DNS brute-force, vulnerability scanning. |
In real-world cybersecurity reconnaissance, attackers often combine passive and active recon to maximize their intelligence gathering.
- Passive recon is used first – Attackers gather general information using OSINT and other indirect techniques.
- Active recon follows – Once they have a basic understanding, they engage in network scanning, service enumeration, and probing vulnerabilities.
This blended approach ensures attackers get both broad contextual awareness and detailed system-level insights. Similarly, penetration testers and red teams use the same methodology when assessing an organization’s security posture.
Network Reconnaissance: A Critical Subset
Network reconnaissance is a crucial aspect of cybersecurity reconnaissance, focusing on mapping an organization's network topology, assets, and vulnerabilities. Attackers analyze the technical footprint of a target, identifying IP addresses, hostnames, open ports, running services, and operating system types. The goal is to uncover exploitable weaknesses that can serve as entry points for further attacks.
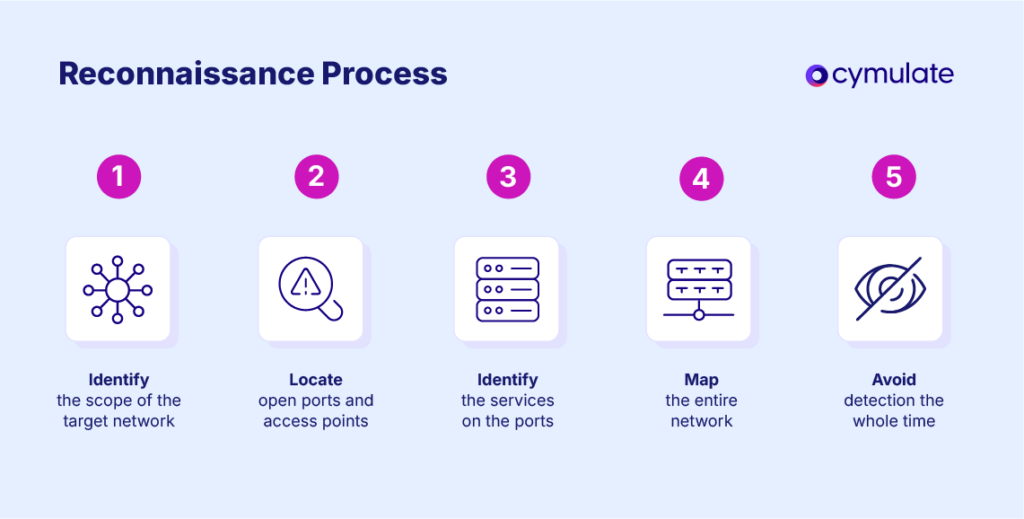
This process involves both external and internal reconnaissance. External network reconnaissance focuses on internet-facing systems, such as cloud assets, VPN gateways, and exposed IoT devices.
Internal reconnaissance, on the other hand, occurs after an attacker has gained a foothold inside the network, allowing them to map subnets, user accounts, and trust relationships.
How do attackers use network reconnaissance?
For attackers, network reconnaissance provides a strategic advantage, allowing them to identify active hosts, scan for open services, and analyze security gaps.
By understanding how different systems interact and where defenses are weak, they can develop an effective attack strategy while minimizing the risk of detection. For instance, they may locate an open database port or an outdated web server, both of which could be exploited for unauthorized access.
Once inside a network, attackers shift their focus to mapping internal structures by enumerating subnets, querying directory services, and identifying high-value assets. Commands like nslookup, net view, and PowerShell scripts help attackers navigate and expand their reach within the system. This phase is a key component of lateral movement, where attackers attempt to escalate privileges and move deeper into the network.
Tools and Techniques Used in Cybersecurity Reconnaissance
Cyber reconnaissance involves a mix of manual research and automated scanning techniques, helping attackers gather intelligence about a target's infrastructure, vulnerabilities, and personnel.
Security professionals, including penetration testers and red teams, often use the same methods for ethical hacking and security assessments. Below are some of the most common reconnaissance techniques.
1. Open Source Intelligence (OSINT)
OSINT involves collecting publicly available information without directly interacting with the target. Attackers use search engines, corporate websites, social media, DNS lookups, and dark web forums to gather intelligence.
Tools like Shodan help identify exposed IoT devices and servers, while Maltego maps relationships between domains, employees, and infrastructure. OSINT is a low-risk, high-value method for reconnaissance as it leaves no digital footprint.
2. Network scanning and enumeration
Active scanning tools like Nmap allow attackers to identify live hosts, open ports, and running services on a network. Ping sweeps determine which devices are active, while OS fingerprinting analyzes network responses to infer operating system details.
Advanced tools like Nessus and OpenVAS perform vulnerability scanning, probing systems for weaknesses that can be exploited later. These techniques provide deeper insights but carry a higher risk of detection.
3. DNS and domain reconnaissance
By analyzing DNS records, attackers can uncover subdomains, mail servers, and infrastructure details.
Tools like FindSubDomains and dnsdumpster help enumerate hidden subdomains, which may lead to forgotten or unprotected assets. Attackers may also perform brute-force DNS enumeration to uncover additional entry points that standard scans might miss.
4. Packet sniffing and traffic analysis
If an attacker can intercept network traffic (such as on public Wi-Fi or through a compromised device), they can use tools like Wireshark to capture and analyze unencrypted data packets.
This may reveal internal IP addresses, communication protocols, and even plaintext credentials. Passive sniffing techniques make it difficult for defenders to detect, making it a valuable method for extracting sensitive network details.
5. Social engineering and human intelligence
Not all reconnaissance is technical. Social engineering techniques, such as phishing emails, pretext phone calls, and tailgating, trick individuals into revealing sensitive information.
An attacker posing as IT support might call an employee to learn about VPN configurations or software versions. Even traditional methods like dumpster diving (searching trash for documents) or shoulder surfing (watching over someone’s screen) can yield useful intelligence.
6. Automated reconnaissance tools
Advanced adversaries automate reconnaissance using tools like Recon-ng and theHarvester, which systematically collect OSINT data.
Some cybercriminals leverage dark web monitoring platforms to check if a target’s credentials or sensitive data have already been exposed. Ethical hackers and red teams also use automation to speed up reconnaissance in security testing and penetration exercises.
The dual use of reconnaissance tools
Many reconnaissance tools are used by both attackers and security professionals. Penetration testers employ Nmap, OSINT tools, and vulnerability scanners to identify security gaps before malicious actors can exploit them.
The key difference is intent—security teams use these tools to strengthen defenses, while attackers use them to exploit weaknesses. Understanding these techniques allows defenders to better anticipate and counteract potential threats.
Defending Against Cybersecurity Reconnaissance
Defending against reconnaissance is challenging because attackers often blend their activities with normal traffic or use publicly available data.
However, organizations can take proactive steps to reduce their exposure and detect recon attempts early. Below are key strategies for strengthening cybersecurity against reconnaissance attacks.
1. Know your own attack surface
One of the best defenses is to conduct reconnaissance on yourself before attackers do. Organizations should regularly assess their attack surface by scanning for exposed assets, cloud services, and leaked credentials.
Incorporating exposure validation helps ensure that identified risks are exploitable in practice, not just in theory. By validating exposures through continuous testing, organizations can prioritize real threats, eliminate unnecessary attack paths, and reduce the likelihood of a successful breach.
2. Minimize digital footprint exposure
Reducing the amount of public information available to attackers is crucial. Organizations should avoid exposing software versions, network diagrams, or sensitive technical details on websites or documents.
Old or forgotten assets, such as demo sites or outdated databases, should be taken offline. Regularly checking DNS records, GitHub repositories, and cloud storage configurations prevents accidental data leaks. The less attackers can gather through passive reconnaissance, the better.
3. Strengthen external network defenses
Since attackers frequently use scanning and probing techniques, network defenses should be configured to detect and block reconnaissance activities.
Firewalls and Intrusion Detection/Prevention Systems (IDS/IPS) should be set up to monitor for port scans, unusual DNS queries, or rapid requests from unknown IPs. Limiting publicly exposed services and implementing network segmentation can also make it more difficult for attackers to map an organization’s internal structure.
4. Continuous vulnerability scanning and patching
Routine vulnerability scanning helps organizations identify and remediate weaknesses before attackers do. Security teams should regularly scan networks, web applications, and databases for known vulnerabilities and misconfigurations.
Keeping software updated and patching critical flaws reduces the likelihood of attackers finding exploitable entry points. Cyber threat intelligence feeds can further help identify emerging vulnerabilities that require immediate attention.
5. Monitoring and anomaly detection
Despite strong preventive measures, some reconnaissance attempts will still occur. SIEM (Security Information and Event Management) systems and network traffic monitoring tools can detect suspicious activity such as sequential port scanning, spikes in DNS queries, or unauthorized crawling of web pages. Behavior analytics tools can help flag subtle anomalies that indicate reconnaissance efforts, allowing security teams to respond proactively.
6. Deploy deception technologies
Deception strategies can be an effective way to detect and mislead attackers. Organizations can deploy honeypots (decoy servers), honeytokens (fake credentials), and alerting canaries (fake services designed to trigger alerts when accessed).
These techniques help security teams identify reconnaissance attempts early and waste an attacker’s time by feeding them misleading information.
How Cymulate Helps Protect Against Cybersecurity Reconnaissance
The Cymulate Exposure Management Platform empowers organizations to proactively identify and mitigate reconnaissance-driven threats. By simulating real-world reconnaissance techniques, security teams can uncover vulnerabilities and enhance their defenses.
- Breach and Attack Simulation (BAS): BAS mimics reconnaissance techniques like network scanning and LDAP enumeration to test firewalls, SIEM, and intrusion detection systems. Security teams can identify blind spots and improve threat detection before real attackers strike.
- Continuous Automated Red Teaming (CART): CART automates multi-stage attack simulations, starting from reconnaissance and moving through exploitation. By continuously testing defenses, it ensures early detection and mitigation of attack pathways.
By integrating BAS and CART, Cymulate enables organizations to simulate, detect, and defend against reconnaissance tactics, turning an attacker’s advantage into a proactive security strategy.
Key Takeaways
- Reconnaissance is the first step of a cyber attack. Attackers gather intelligence to identify vulnerabilities, network structures, and entry points. Recognizing this phase is crucial for proactive defense.
- Passive vs. Active Reconnaissance. Passive recon uses indirect methods like OSINT, while active recon involves direct probing and scanning, increasing the risk of detection. Attackers often use both approaches.
- Network Reconnaissance is a major threat. Attackers map networks to find open ports, weak points, and hidden assets. Reducing attack surface exposure helps limit their insights.
- Strong defenses can disrupt reconnaissance. Regular security assessments, network monitoring, deception tactics, and employee awareness make it harder for attackers to gather useful information.
- Cymulate enhances proactive security. With BAS and CART, organizations can simulate reconnaissance techniques, detect exposures, and improve defenses before real threats emerge.