Pass-the-Ticket Attack
What is a Pass-the-Ticket Attack? How to Detect, Prevent and Stop Lateral Movement
A Pass-the-Ticket (PtT) attack is a credential theft technique where an attacker steals a valid Kerberos ticket – typically a Ticket Granting Ticket (TGT) – and uses it to impersonate a user without needing their password.
In a Windows Active Directory environment (which relies on Kerberos for authentication), this means the attacker can bypass normal authentication and gain illicit access to services and data using the stolen ticket.
Essentially, the attacker “passes” the stolen ticket to trick other systems into believing they are an authenticated user. This method is akin to the more widely known Pass-the-Hash attack (which abuses password hashes), but Pass-the-Ticket targets Kerberos – the default authentication protocol in modern Windows domains.
Kerberos Context
Kerberos uses tickets to authenticate users transparently after they log in. When a user enters credentials, the Key Distribution Center (KDC) on a domain controller issues a TGT (Ticket-Granting Ticket), which the user’s system then uses to request service tickets for specific resources. The TGT is like a master key that proves your identity to the KDC; with it, you can get access to other network services without re-entering your password.
In a Pass-the-Ticket attack, this trusted mechanism is abused – an attacker with a stolen TGT can obtain service tickets or directly access services as that user.
Because the ticket is a cryptographic token vouching for the user’s identity, any service that accepts Kerberos tickets will accept the attacker as the legitimate user if the ticket is valid.
In other words, once attackers have a foothold on one system, Pass-the-Ticket lets them pivot to other systems by reusing the stolen Kerberos tickets, all without triggering additional logon prompts or needing to crack passwords. This makes PtT a favored technique in many advanced intrusions, allowing attackers to escalate their access and roam the network as an authorized user – a nightmare scenario for defenders.
How a Pass-the-Ticket Attack Works
To understand how a Pass-the-Ticket attack unfolds, it’s important to grasp how Kerberos authentication works. Here is a step-by-step breakdown of a typical PtT attack, including the role of the TGT:
1. Initial compromise and ticket extraction
Attackers first gain access to a domain-connected machine, usually via phishing, malware, or exploiting vulnerabilities. After securing access, they escalate privileges—typically gaining local administrator rights—to read sensitive information stored in system memory. Active Kerberos tickets, including Ticket-Granting Tickets (TGTs), reside within the memory of the LSASS process when users are logged in.
Attackers use credential-dumping tools such as Mimikatz or Rubeus to extract these tickets directly from memory. The TGT is particularly valuable, as it can authenticate to any resource within the domain to which the user has access rights.
2. Ticket import/injection
After extracting the TGT from memory, attackers inject or import this ticket into another logon session or onto another machine they control.
Mimikatz offers specific functionality to inject the stolen Kerberos ticket into an attacker’s current session, effectively allowing the attacker to assume the identity of the victim user without ever needing the user’s password.
3. Requesting service tickets or accessing services
With the valid, stolen TGT now active in the attacker’s Kerberos cache, the attacker can request Ticket-Granting Service (TGS) tickets from the domain’s Key Distribution Center (KDC).
Because the TGT is legitimate, the KDC treats these requests as valid and issues service tickets accordingly.
The attacker uses these service tickets to access domain resources, such as file shares, databases, or even additional servers. Sometimes attackers directly reuse stolen service tickets without needing to interact further with the KDC. The receiving services see these tickets as legitimate since they are genuinely signed by the KDC.
4. Lateral movement and privilege abuse
Attackers exploit these valid Kerberos tickets to move laterally across the network, hopping from machine to machine. After gaining initial access to one server using stolen tickets, they often extract more tickets stored on that server—potentially tickets from accounts with elevated privileges, such as a domain administrator.
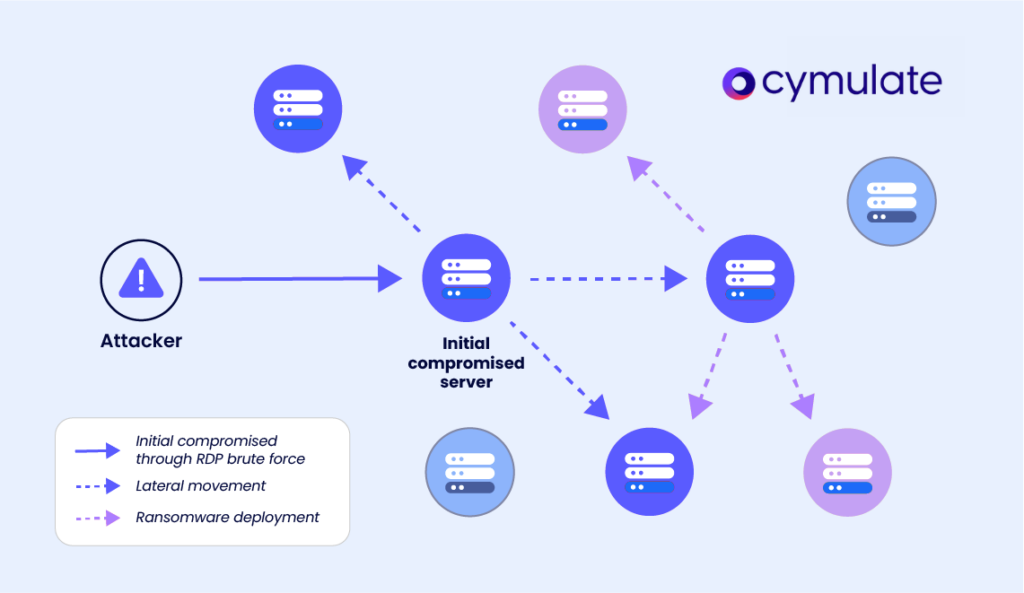
This allows attackers to escalate privileges rapidly and quietly across systems, progressively accessing more sensitive network resources. Because Pass-the-Ticket attacks reuse legitimate tickets, attackers can continuously bypass authentication mechanisms without triggering password-related alarms or account lockouts.
5. Maintaining access and persistence
Kerberos tickets have a default limited lifetime (typically about 10 hours). Within this timeframe, attackers can perform extensive reconnaissance or data exfiltration. To maintain long-term persistence, attackers may automate periodic ticket extraction or ticket renewal processes, ensuring continuous access.
In advanced scenarios, attackers may aim to compromise the Kerberos KDC itself by obtaining the KRBTGT account hash, enabling them to forge entirely new tickets—a more severe compromise known as a Golden Ticket attack. Even without forging new tickets, attackers might set backdoors or create new accounts to ensure continuous presence within the compromised environment.
The Critical Risks of Pass-the-Ticket Attacks
Pass-the-Ticket attacks are a serious threat to organizations because they combine stealth, persistence, and lateral movement in one technique. Here are the key reasons these attacks are particularly dangerous:
Stealthy and legitimate-looking access
Pass-the-Ticket (PtT) attacks exploit valid Kerberos tickets, making the attacker’s activities look like normal user behavior. Because these tickets are genuinely issued by the domain’s Key Distribution Center (KDC), attackers avoid typical detection methods that rely on spotting brute-force attempts, failed logins, or malware signatures.
Standard defenses like strong passwords and even multi-factor authentication (MFA) are ineffective once a ticket is stolen, as attackers reuse existing authenticated tokens without needing to trigger another login challenge.
Enables broad lateral movement
Once attackers have stolen a valid Kerberos ticket, they can move freely across the network—limited only by the permissions of the stolen ticket’s original user. Often, an attacker starts by compromising a regular user’s account, using that access to move deeper into the network by impersonating higher-privilege users.
This process enables attackers to escalate privileges, potentially reaching domain controllers or other sensitive systems, without exploiting additional vulnerabilities or cracking passwords. Essentially, PtT allows attackers to impersonate authorized users and quietly move throughout the network undetected.
Persistence and difficult remediation
Kerberos tickets typically remain valid even if a user’s password is changed or an account is disabled. Attackers leverage this by rapidly using stolen tickets and sometimes renewing them, ensuring continued access until the tickets naturally expire.
Incident response is challenging because there's no straightforward method to immediately invalidate active Kerberos tickets; even password resets or account disabling don't instantly terminate a ticket’s validity. The delay in revocation gives attackers ample time to maintain a foothold, carry out espionage, or establish persistent backdoors.
Credential reuse sidesteps many security controls
PtT represents a type of credential compromise that evades multiple layers of security. Password strength, lockout policies, or traditional intrusion detection methods become irrelevant because the attacker isn't performing actions that typically raise alerts.
Attackers favor this technique because it allows them to extend an initial breach into a complete compromise of the network without noisy activity. Combining PtT with tools like Mimikatz Kerberos modules can even automate the attack, making it more effective and harder to detect.
Detection Indicators of Pass-the-Ticket Activity
Detecting Pass-the-Ticket (PtT) attacks requires close monitoring of authentication logs for subtle anomalies. Key indicators include:
Unusual logon patterns (Event ID 4624, type 3)
A Pass-the-Ticket attack often creates unexpected network logons (Event ID 4624, Type 3) from machines that a user wouldn't typically access.
For instance, a sudden Kerberos network logon by a regular user on a critical server (rather than their usual workstation) could signal ticket reuse. Security teams should configure their SIEM systems to highlight logins that deviate from normal user behavior.
Logon events with missing or anomalous fields
Attackers using stolen or forged Kerberos tickets might generate Windows Event logs (4624 or 4672) containing irregularities, such as blank "account domain" or "Logon GUID" fields.
While normal logons populate these fields, attackers' activities—particularly with Golden Tickets—can leave these suspiciously empty, indicating ticket forgery or reuse.
Kerberos ticket request anomalies (Event IDs 4768/4769)
Under normal circumstances, obtaining a service ticket (Event ID 4769) follows shortly after a Ticket-Granting Ticket (TGT) request (Event ID 4768).
In Pass-the-Ticket attacks, however, service tickets may be requested without corresponding recent TGT requests from the same system or user, indicating ticket reuse or forgery. Additionally, tickets with unusually long or future expiration dates strongly suggest malicious activity.
Multiple systems using identical tickets or unexpected ticket use
Monitoring for identical Ticket IDs appearing across multiple hosts is another strong indicator, as a single TGT should only be used by the original requesting system. Furthermore, if regular users suddenly access sensitive resources like Active Directory or executive file shares using Kerberos tickets, it can indicate stolen tickets being leveraged for unauthorized access.
Monitoring tools and anomalous behavior analytics (Ueba)
Organizations should enable comprehensive Kerberos audit logging across domain controllers and critical servers.
Behavioral analytics tools (UEBA) help detect anomalies like unusual login times or abnormal user activities. Additionally, security solutions may flag indirect indicators, such as Mimikatz triggering security alerts or antivirus detections when injecting tickets into memory.
Network traffic anomalies
Network Detection and Response (NDR) tools can detect irregular Kerberos traffic patterns (e.g., unexpected KRB_TGS_REQ/KRB_AS_REQ messages or tickets with abnormal timestamps or ciphers). Combining network-level monitoring with host-based logs significantly improves the chances of detecting stealthy Pass-the-Ticket activity.
Prevention and Mitigation Strategies
Preventing Pass-the-Ticket attacks involves securing systems to limit ticket theft opportunities and restricting attackers' capabilities if tickets are compromised. Key strategies include:
- Enable credential guard: Microsoft’s Credential Guard protects sensitive credentials (like Kerberos TGTs and NTLM hashes) by storing them securely in a virtualization-based container, preventing attackers from extracting them—even with tools like Mimikatz. Deploy Credential Guard on all supported Windows endpoints and servers, particularly privileged systems.
- Limit kerberos ticket lifetimes: Reduce the default Kerberos Ticket-Granting Ticket (TGT) lifetime (usually 10 hours) to shorter intervals (e.g., 4-6 hours). Shorter lifetimes shrink the window attackers have to misuse stolen tickets. Monitor for unusually aged tickets, as they often indicate malicious activity.
- Apply least privilege and account tiering: Restrict user privileges to minimize damage if credentials are stolen. Limit the use of administrative accounts, avoid shared local admin credentials, and enforce privileged account tiering. Tools like LAPS (Local Administrator Password Solution) help randomize local admin passwords, further hindering lateral movement.
- Harden and monitor privileged sessions: Leverage security features like Restricted Admin Mode for RDP to avoid credential exposure. Regularly purge idle Kerberos tickets (using commands like klist purge) to prevent lingering credentials. Segment your network to block lateral movements from compromised machines.
- Frequent credential rotation & rapid response: Regularly rotate privileged account passwords, including the critical KRBTGT account, to minimize attackers’ persistence opportunities. Implement rapid response protocols (such as "Credential DoubleTap")—quickly resetting compromised passwords twice to invalidate stolen tickets and clearing cached credentials from memory.
- Use multi-factor authentication (MFA) wisely: While MFA doesn't stop an attacker reusing stolen tickets, it significantly raises the bar for the initial compromise. Enforce MFA for remote and privileged logins, and consider smartcards or certificate-based Kerberos authentication (PKINIT) to prevent easy ticket theft.
- System hardening and regular updates: Keep systems, especially domain controllers, fully patched to benefit from Kerberos-related security improvements. Disable legacy protocols like NTLM where possible, and adhere to recommended Microsoft Active Directory security baselines.
- Continuous monitoring and testing: Consistently monitor Active Directory and Kerberos activity for anomalies and regularly train security analysts on attack patterns. Use specialized tools to detect unusual AD changes and perform ongoing testing of defenses to promptly detect and respond to incidents.
Implementing these layered security practices significantly reduces the likelihood and impact of Pass-the-Ticket attacks, ensuring attackers must resort to riskier or noisier techniques, thus enhancing your ability to detect and neutralize threats quickly.
Related Attacks: Pass-the-Hash, Golden Ticket, and Silver Ticket
Pass-the-Ticket (PtT) is related to several credential theft techniques:
- Pass-the-Hash (PtH): Targets NTLM authentication. Attackers steal and reuse password hashes (without cracking passwords) to access resources. It's similar to PtT but involves NTLM hashes instead of Kerberos tickets.
- Golden Ticket: Attackers steal the KRBTGT account hash from the Kerberos Key Distribution Center (KDC), enabling them to forge powerful, unrestricted TGTs with custom privileges and long lifetimes. Golden Tickets grant persistent domain-wide access, making them extremely dangerous and difficult to detect without careful monitoring.
- Silver Ticket: Attackers forge Kerberos service tickets (TGS) for individual services after compromising a service account’s password hash. Unlike Golden Tickets, Silver Tickets don't involve the KDC directly at authentication time, making detection more challenging. Protecting service accounts with strong, rotated passwords and enabling PAC signature validation helps prevent this attack.
- Kerberoasting: Attackers request service tickets for user-operated service accounts, then crack these tickets offline to obtain plaintext passwords. While not directly a ticket-reuse attack, Kerberoasting often precedes PtT, Silver, or Golden Ticket attacks by giving attackers credentials needed for these techniques. Defenses include using strong passwords and managed service accounts.
Defenders should be aware of all these, as attackers might chain techniques together. For instance, a common attack path in a network is: phishing -> dump hashes -> PtH to move laterally -> find service account -> Kerberoast -> crack password -> Silver Ticket or PtT -> get domain admin -> Golden Ticket for persistence. Understanding the differences helps in deploying the right mitigations and detections at each stage.
Simulating and Preventing Lateral Movement with Cymulate
The Cymulate Breach and Attack Simulation (BAS) and security posture management platform helps organizations proactively test and strengthen defenses against lateral movement attacks like Pass-the-Ticket.
By safely simulating real-world attack scenarios—including credential compromise (using tools like Mimikatz), Pass-the-Ticket, and other lateral movement techniques—Cymulate assesses your detection and response capabilities in a controlled environment.

The platform includes modules such as Continuous Automated Red Teaming (CART) to perform realistic, multi-stage attack simulations. These simulations validate your SIEM correlation rules, EDR effectiveness, and overall security configuration, identifying visibility gaps before attackers exploit them.
Cymulate enables continuous validation, verifying defensive improvements after implementing mitigations like Credential Guard, Kerberos hardening, or MFA. Regular simulations serve as security "fire-drills," ensuring SOC readiness and enhancing compliance reporting.
Ultimately, Cymulate ensures your organization stays ahead by converting theoretical security measures into tested, practical defenses against sophisticated lateral movement threats like Pass-the-Ticket.
Key Takeaways
- Pass-the-Ticket (PtT) attacks leverage stolen Kerberos tickets to bypass normal authentication, allowing attackers to impersonate legitimate users without passwords. Protecting credentials stored in memory (such as TGTs) is essential.
- PtT attacks enable stealthy lateral movement and privilege escalation, helping attackers deepen their foothold in networks. Defenses such as network segmentation and user behavior monitoring are crucial.
- Effective detection involves monitoring for anomalies in authentication logs (e.g., event IDs 4624, 4768, 4769). No single indicator is definitive, but correlation and behavioral analytics are key.
- Prevention focuses on credential hardening (e.g., using Credential Guard), account hygiene, and layered defenses. Assume attackers will bypass individual measures; implement multiple overlapping controls.
- Understanding related attacks (Pass-the-Hash, Golden Ticket, Silver Ticket, Kerberoasting) is vital for creating holistic defenses, ensuring no gaps remain for attackers to exploit.


