SIEM Correlation Rules
How Correlation Rules Reduce False Positives in SIEM Detection
SIEM correlation rules are the logic that ties together separate security events to spot threats. A correlation rule defines a pattern or sequence of events that, when observed together, indicate malicious activity.
A simple rule might look for “five failed logins followed by a successful login” from the same user or machine. By linking these separate events, the SIEM can generate an alert only when the combined pattern appears.
The purpose of correlation rules is to connect the dots across disparate logs. Rather than treating each event in isolation, a correlation rule captures a meaningful series of events.
Put another way, correlation rules help the SIEM answer: “If Event A happens and then Event B happens shortly after, should this be a problem?” If yes, the rule fires an alert.
Most major SIEM platforms, like Splunk, IBM QRadar, ArcSight, Microsoft Sentinel and others support correlation rules.
Each system may call them slightly different things (e.g. Splunk “correlation searches,” QRadar “custom rules”), but the goal is the same: link multiple security events to reveal attack patterns that individual events would miss.
How SIEM Correlation Works
At its core, SIEM correlation means looking for event patterns over time. The SIEM continuously ingests logs (from endpoints, servers, network devices, etc.) and checks them against its collection of correlation rules. A rule might specify something like: Event X occurs, then within Y minutes, Event Z occurs. When both conditions are met in the right order, the rule “matches” and triggers an alert.
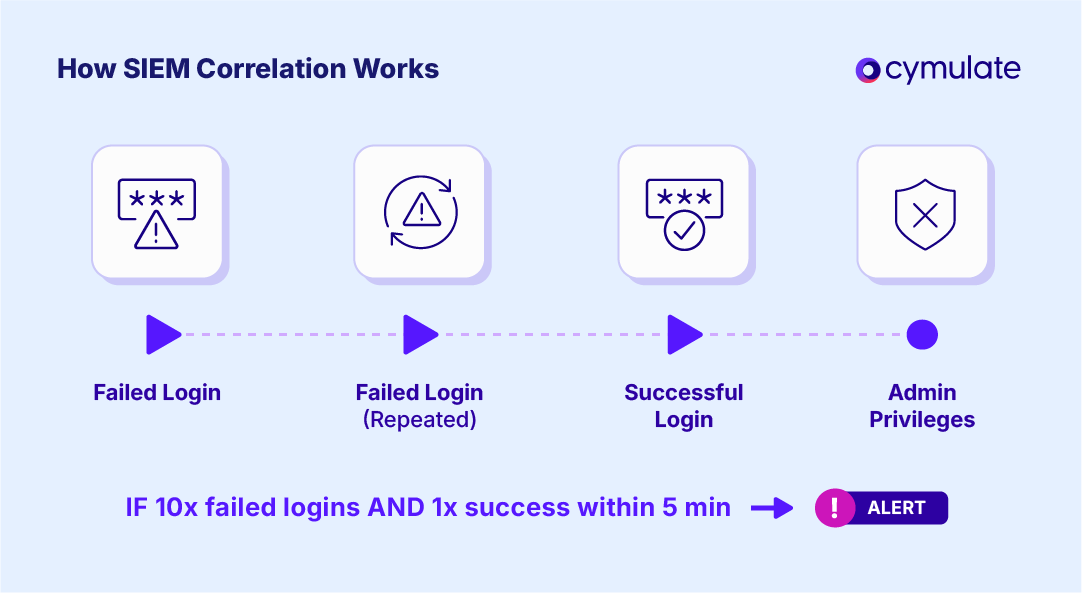
Imagine a rule that says “if 10 failed login attempts occur within 5 minutes, and then an administrative account login succeeds, generate an alert.” The SIEM’s correlation engine will monitor all login events. Whenever someone logs in (successful or failed), the engine checks: has this sequence happened?
If a user indeed hits 10 failures and then a success in that time window, the engine links those events and raises the alert. Alone, the failed logins might be assumed harmless (perhaps someone forgot their password), but the sequence with a successful login is a red flag.
Correlation rules rely on evaluating time, sequence and logic:
- Time windows: Rules often include a time frame. For example, “five failed logins within one hour followed by success.” The SIEM must keep track of events and forget old ones once the time window expires.
- Sequence/order: Many rules depend on a specific order of events. In our example above, the success must follow the failures. If the order is reversed (success then failures), the rule doesn’t match.
- Logical conditions: Rules combine conditions (AND/OR logic). For instance, a rule might require both an event in the firewall log and an event in the DNS log involving the same IP.
Under the hood, correlation requires normalized data. Logs come in from many sources and formats. To make rules reliable, the SIEM often normalizes log data into a common schema or format. Consistent timestamps, IP address formats, user IDs and event types ensure that disparate logs can be compared.
In practice, the SIEM might parse syslogs, Windows Event Logs, or network device logs into standardized fields so that the correlation engine can treat them uniformly. In other words, “normalizing log data” is crucial so the SIEM can easily match events across different sources.
Why Correlation Rules Matter for Threat Detection
Correlation rules power smarter detection and help SOC teams cut through noise. By design, they reduce alert fatigue. Instead of firing an alert on every failed login, or every port scan, a well-tuned correlation rule only alerts when a pattern of concern emerges.
This means fewer low-fidelity alerts and fewer wasted investigations. In fact, unrefined correlation rules are often a major source of false alarms; research notes that “excess false positives can come from unrefined correlation rules or unfiltered logs,” and tuning is needed to avoid turning analysts off.
Good correlation rules, on the other hand, prioritize the right signals, making alerts more meaningful.
Catching What Single-Rule Alerts Miss
Correlation rules also detect advanced attack behaviors that single-rule alerts miss. Consider lateral movement or privilege escalation. Each step of these attacks might look benign by itself.
An attacker might successfully log in as a low-priv user (normal event) and then, a while later, escalate to an admin account (possibly normal as well). But if you correlate “user login” with “admin process spawn,” the SIEM can spot this lateral movement.
Cymulate’s SIEM logging guide notes that, “a SIEM may detect lateral movement by correlating a Windows login log with an EDR process spawn.” A similar approach catches privilege escalation: linking a regular shell with a sudden change to SYSTEM privileges, for instance, would trigger an alert only when the sequence happens together.
Revealing Multi-Stage Attacks Through Correlation
Perhaps most importantly, correlation rules reveal multi-stage attacks. Modern attacks often involve a chain of steps (reconnaissance, initial compromise, escalation, etc.).
Individually, each step might blend into normal activity. But when you correlate across the chain, the attack lights up. Event correlation is “crucial for detecting multi-stage attacks or identifying patterns” across logs.
Combining a suspicious login event with a spike in data exfiltration can expose an attacker who might otherwise slip through. In short, correlation rules allow SIEMs to catch stealthy threats by linking event sequences that follow known attack patterns.
Types of SIEM Correlation Rules
Not all correlation rules work the same way. Broadly, they fall into a few categories:
Rule-based (static) correlation
These are the classic correlation rules built by analysts. They use fixed thresholds or patterns. For example, “Alert if 10 failed logins occur within 15 minutes” is a static rule.
Another might be: “If a USB device is inserted and then a sensitive file is accessed in the next 5 minutes, alert.” These rules rely on set values (counts, time windows) and do not adapt on their own. They’re straightforward to understand and write but often require manual tuning to avoid false positives.
Behavioral (anomaly) correlation
Instead of fixed thresholds, behavioral rules use baselines or machine learning to spot anomalies. The SIEM learns normal patterns (like a user’s typical login times or a server’s usual network traffic) and flags deviations.
This type of detection is often called anomaly detection or user/entity behavior analytics (UEBA). It’s especially useful for finding subtle or evolving threats, because it looks for anything “outside the norm” rather than matching a predefined sequence. (That said, true anomaly correlation usually falls under advanced analytics in modern SIEMs, and may be combined with other rules.)
Time-based and sequence-based correlation
These focus explicitly on event order and timing. A sequence rule triggers only if Event A happens followed by Event B (and possibly others) in a specific order. For example, multiple failed logins followed by a privilege escalation command (e.g. sudo or net user /add) is a classic sequence-based rule.
A time-window rule might not care about strict order, just co-occurrence within a time frame. For instance, “Alert if a file deletion and a database access happen within 30 seconds of each other,” regardless of which came first. Time-based rules are often combined with sequence rules (the above login example implicitly has a time window).
SIEMs can catch a wide range of tactics by mixing and matching these types (e.g. a static rule that also checks a time window). Crafting good examples and thresholds typically requires knowledge of both the network environment and adversary behaviors.

Challenges in SIEM Correlation
Correlation rules are powerful, but writing them effectively is challenging.
The False Positives
Correlation rules are powerful, but writing them effectively is challenging. One common issue is false positives. If rules are too broad or thresholds too low, normal activities will trigger alerts. For example, a poorly tuned rule might fire every time a contractor logs in (creating the same pattern as an attacker).
Analysts can suffer alert fatigue when faced with floods of benign alerts. Studies note that “too many low-fidelity alerts” from unrefined rules can cause SOC teams to “tune out.” On the flip side, being too strict or filtering aggressively can lead to missed detections – the exact situations we wanted to catch are quietly ignored.
Complexity and Tuning Overhead
Another challenge is rule complexity and tuning. Large organizations may have hundreds or thousands of correlation rules. Each rule needs the right data sources, correct field mappings, and constant tweaking as the network and threats change.
Time windows, IP address scopes, user groups, all may need adjustment. Keeping rules up-to-date is a tedious task. It often turns into a manual grind of writing a rule, testing it with historical logs (to see if it would have caught real incidents), then tweaking it again. This complexity means valuable rule-writing resources are stretched thin.
Static Rules vs Evolving Techniques
A related problem is over-reliance on static rules. Static rules catch only what they were explicitly written to detect. Attackers constantly evolve their techniques, so static correlation logic can quickly become outdated.
A rule that once detected lateral movement might miss a new variant of the same technique. In fact, research shows that default SIEM rule sets often cover only a small fraction of known attacks: one source cites only ~19% of MITRE ATT&CK techniques are covered on average. Anything outside those hard-coded patterns will slip through.
Enhancing Correlation Rules Through Detection Engineering
Given these challenges, modern SOCs treat correlation rule development as a form of detection engineering. Detection engineers play a critical role: they take threat intelligence and creative scenarios to refine rules and fill gaps.
This involves writing new rules, tweaking logic and testing them against known attack data. Rather than hoping a rule works in production, engineers use controlled tests and simulations to confirm effectiveness.
Cymulate can automatically analyze your existing SIEM rules and match them to real-world attack techniques. If a gap is found, Cymulate even suggests Sigma rules to cover it. (Sigma rules are an open, SIEM-neutral format for writing detection logic in YAML.)
In practice, this means SOCs don’t have to start from scratch. Cymulate provides off-the-shelf Sigma rule templates for common attacks, which can be directly applied to your SIEM. According to Cymulate, Sigma rules “greatly accelerate SOC engineers’ work” by reducing routine tasks.
Detection engineering refines correlation logic. Engineers might craft a more granular rule after seeing too many false positives, or split a monolithic rule into parts. They also test rules by replaying historical attack data or simulations
As one customer puts it, if a SIEM rule can’t be validated with logs, they use Cymulate to “generate the appropriate events and see if the rule was successful,” providing immediate feedback for fine-tuning.
Validating Correlation Rules with Cymulate
Writing correlation rules is only half the battle – you must also validate that they work as intended. The Cymulate platform specializes in safe, automated SIEM rule validation.
The idea is simple: use controlled attack simulations to test each rule. In practice, Cymulate connects to your SIEM, pulls in all your existing rules and then runs breach-and-attack simulations to trigger those rules.
These simulations cover a variety of tactics (endpoint compromise, privilege escalation, cloud attacks, etc.) so you see which rules catch them and which do not.

Identifying Missed Detections and Fine-Tuning Logic
This approach has concrete benefits. First, it identifies missed detections. If an attack simulation (say, a known malware execution) fails to generate an alert, Cymulate flags that gap.
You then know a new or adjusted correlation rule is needed. Second, it helps tune logic. Perhaps a rule only fires when all conditions are met exactly. By seeing the rule’s behavior on test data, engineers can loosen or tighten thresholds to reduce noise.
Reducing False Positives Through Realistic Testing
A key result is fewer false positives. Because you can replay both malicious and benign scenarios, you’ll quickly see if a rule is firing too often on normal activity.
The solution can tune SIEM detection rules and reduce false positives through validation. In other words, simulated validation gives you confidence that an alert is meaningful.
Real-World Impact of Continuous Validation
Finally, there are measurable improvements. Cymulate reports that organizations running exposure validation regularly have 20% fewer breaches (since problems get caught earlier). In their Threat Exposure Validation Impact Report 2025, 47% of surveyed security leaders said that exposure validation improved their mean time-to-detection, and 40% reported greater threat resilience.
This demonstrates that validating correlation logic against real attack data isn’t just theory – it delivers real-world gains.
Smarter Detection Through Smarter Correlation
SIEM correlation rules are a linchpin of effective threat detection, but only when they’re well-engineered and continuously refined. The smartest SOCs treat correlation rules as living logic: they proactively validate and tune them rather than “set and forget.”
With detection engineering (writing and adjusting Sigma rules) and automated validation (simulating attacks to test rules), teams turn raw log data into precise detection logic. This threat-informed correlation cuts alert noise and uncovers stealthy multi-stage attacks faster.
Modern tools like Cymulate make this process far easier. They automate the grind of mapping rules to attacks, running simulations, and even generating rule suggestions.
The result is continuous improvement: rules evolve alongside threats, and detection quality improves over time. In short, better correlation means smarter alerts. When SOCs adopt a proactive validation mindset (as our guide on SIEM rule validation emphasizes), they stay ahead of attackers rather than chasing them.


