What is the SLAM Method in Cybersecurity? A Guide to Phishing Prevention
Phishing is one of the most prevalent cybersecurity threats today. It’s a key entry point for many cyberattacks, including ransomware, credential theft and data breaches. Despite continuous technological advancements, phishing remains highly effective because it exploits the human factor. Organizations have poured resources into developing training programs and technology defenses, but phishing attacks continue to evolve, and individuals remain vulnerable.
One practical and efficient way to help individuals and organizations combat phishing is the SLAM method—a simple, memorable approach to identifying suspicious emails before they cause harm.
What Does the SLAM Method Stand For?
SLAM is an acronym that highlights four critical aspects of an email that must be examined to determine whether it could be a phishing attempt. It stands for:
- Sender
- Links
- Attachments
- Message
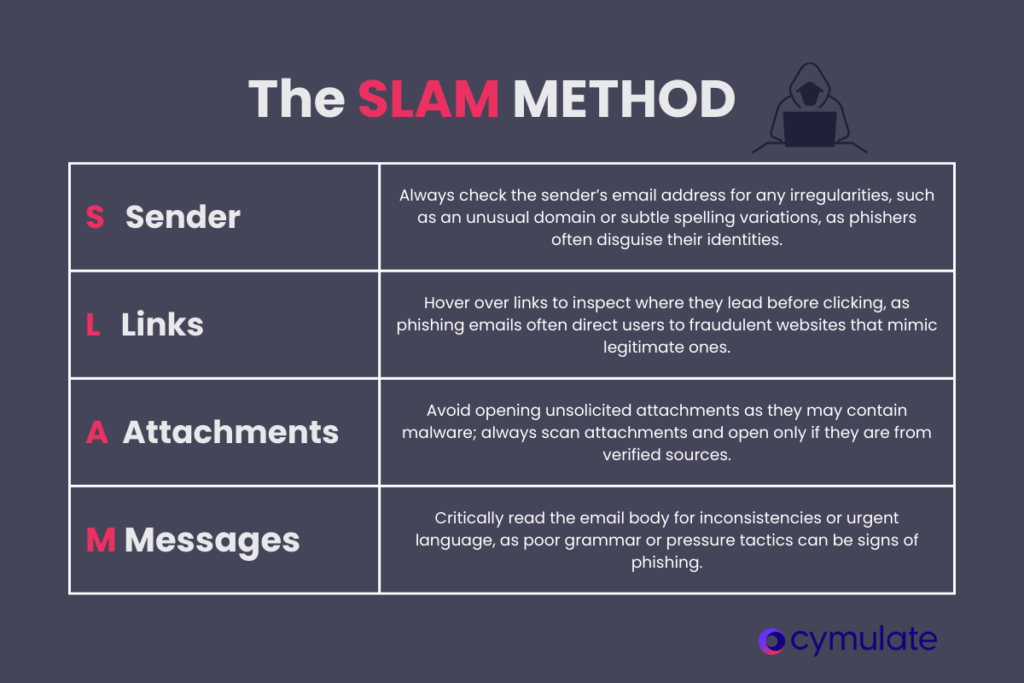
S – Sender: why checking the sender’s address is the first step
One of the first things anyone should do when receiving an email is to check the sender’s address. Phishers often manipulate email addresses to look like they come from legitimate sources, such as your bank or a trusted company. They might spoof the email domain or use slight variations of known addresses to trick recipients. For example, instead of an official domain like @bankofamerica.com, a phishing email might use @emcom.bankofamerica.com or another variation designed to deceive the reader.
Verifying the sender’s email address for irregularities, like an unfamiliar domain or unusual spelling, is critical. Any suspicious details here should prompt cautious engagement with the email.
L – Links: hover over links to see where they lead
Phishing emails frequently use malicious links to direct recipients to fraudulent websites where they might be asked to enter sensitive information, such as usernames, passwords, or payment details. These sites often look almost identical to legitimate ones but are controlled by attackers.
The SLAM method encourages users to hover over any links in an email before clicking them to see where they lead. If the link doesn’t match the sender’s known web address or appears suspicious, avoid clicking it. For example, a link labeled as “MyBank Login” might lead to phishy.com/login instead of a known domain.
A – Attachments: the danger of unsolicited attachments
Phishing emails often contain malicious attachments that, once opened, can install malware or ransomware onto a user’s system. These attachments may look harmless—a Word document, PDF, or spreadsheet—but can hide harmful scripts.
The SLAM method reminds individuals to treat all unexpected attachments with suspicion, especially from unknown senders. Avoid opening attachments unless they are expected and verified. Even when attachments seem safe, scanning them with antivirus software before opening them is a good practice.
M – Messages: spotting inconsistencies or suspicious messages
The body of a phishing email often contains subtle signs that something is off. These could include poor grammar, spelling mistakes, or awkward phrasing. Another common trick phishers use is creating a sense of urgency, pushing the recipient to act quickly—such as “Your account will be suspended unless you act now.”
Critically reading the message for inconsistencies or suspicious language is essential. Signs of urgency or pressure are often red flags that warrant further scrutiny.
Using the SLAM Method to Help Prevent Phishing Attacks
The SLAM method is a quick and practical checklist to guide individuals through evaluating email security. By training yourself or your team to use SLAM every time an email seems suspicious, you can prevent phishing attacks before they even begin. The method is straightforward, easy to remember, and ensures that each potential phishing email is scrutinized based on its most common elements—sender, links, attachments, and message.
Moreover, the SLAM method can be integrated seamlessly into any organization’s security awareness program. It encourages users to pause and evaluate emails thoughtfully, helping them make smarter decisions when confronted with suspicious communications.
Recognizing a Phishing Email
While the SLAM method offers a targeted approach, phishing emails often exhibit other telltale signs that extend beyond the SLAM acronym. These signs include:
- Poor grammar and spelling: Many phishing emails contain grammatical errors or awkward wording. This could be because non-native speakers or automated bots conduct many phishing attacks.
- Urgent requests: Phishing emails often attempt to create a sense of urgency, urging recipients to act immediately, threatening consequences such as account suspension or financial loss.
- Strange-looking URLs: Even if you hover over a link, it’s worth paying attention to the structure of the URL. Phishers often create URLs that appear legitimate at first glance but include slight variations to deceive users.
What to Do When You Detect a Phishing Attack
If you suspect that you’ve received a phishing email, it’s essential to follow a clear set of steps to mitigate the risk:
- Do not engage with the email: Avoid clicking on links, downloading attachments, or replying.
- Report the email: Most organizations have procedures for reporting suspected phishing emails. Alerting your IT or security team is essential to prevent the attack from spreading.
- Flag the email: Mark the email as spam or phishing in your email client to help prevent future similar attacks.
- Involve your cybersecurity point of contact (IT/CISCO): IT and security teams should be informed as quickly as possible if you suspect a phishing attempt. They may need to take additional steps to protect the organization’s systems.
Employee Awareness Training: Integrating SLAM into Organizational Cybersecurity
Cybersecurity awareness training is crucial in preventing phishing attacks. While organizations invest in advanced email filtering solutions, no technology is perfect, and phishing emails will inevitably slip through the cracks. This is where human intervention becomes critical.
The SLAM method can be a powerful tool for teaching employees during security awareness training sessions. By providing them with a simple, memorable framework, employees are better equipped to identify phishing attempts quickly and effectively. The more intuitive the process, the more likely employees will adopt it in their daily routines.
How Cymulate Can Help Prevent Breaches from Phishing Attacks
As part of the Cymulate Red Teaming Solution, organizations can strengthen their defenses by leveraging the Cymulate platform to simulate realistic phishing attacks and enhance employee readiness. This capability provides an automated and continuous way to evaluate and improve resilience against phishing threats, helping organizations proactively identify weaknesses and build a more cyber-aware workforce.
Using the Cymulate intuitive drag-and-drop interface, security teams can design phishing campaigns that mirror real-world attack tactics. These simulations help employees practice identifying phishing emails and reinforce SLAM principles. Additionally, they provide security teams with insights into risky behaviors.
Key Takeaways
Phishing continues to be one of the most significant threats facing organizations today. Threat actors constantly refine their techniques, making suspicious emails harder to identify. The SLAM method offers a simple yet effective strategy for combating phishing by encouraging users to scrutinize emails for common red flags—sender, links, attachments, and messages.
While no single method can eliminate the risk from phishing campaigns, combining SLAM with a solution, like Cymulate, significantly reduces an organization’s exposure to these threats. Training employees with SLAM and using phishing simulations empowers the human element of cybersecurity, helping individuals make smarter choices when engaging with email.

