Phishing Awareness Training: Building a Human Firewall Against Phishing Attacks
As phishing attacks become increasingly sophisticated and evasive, technology solutions alone cannot thwart every threat. The human element remains the most vulnerable target. That is why comprehensive security awareness training, testing, and improvement programs are essential to equip employees with effective methods to recognize and respond properly to phishing attempts.
When implemented effectively, human phishing prevention initiatives can significantly boost organizational resilience against phishing.
Training Employees to Spot Phishing Attempts
The foundation of any phishing prevention program is security awareness training to help employees identify common phishing techniques and respond appropriately. Training should aim to be engaging, practical, and refreshed regularly. Avoid using harsh or deceptive tactics, such as the controversial GoDaddy campaign, which used a fake bonus email as a test. Such approaches can harm trust and undermine the program's effectiveness.
Phishing awareness training best practices
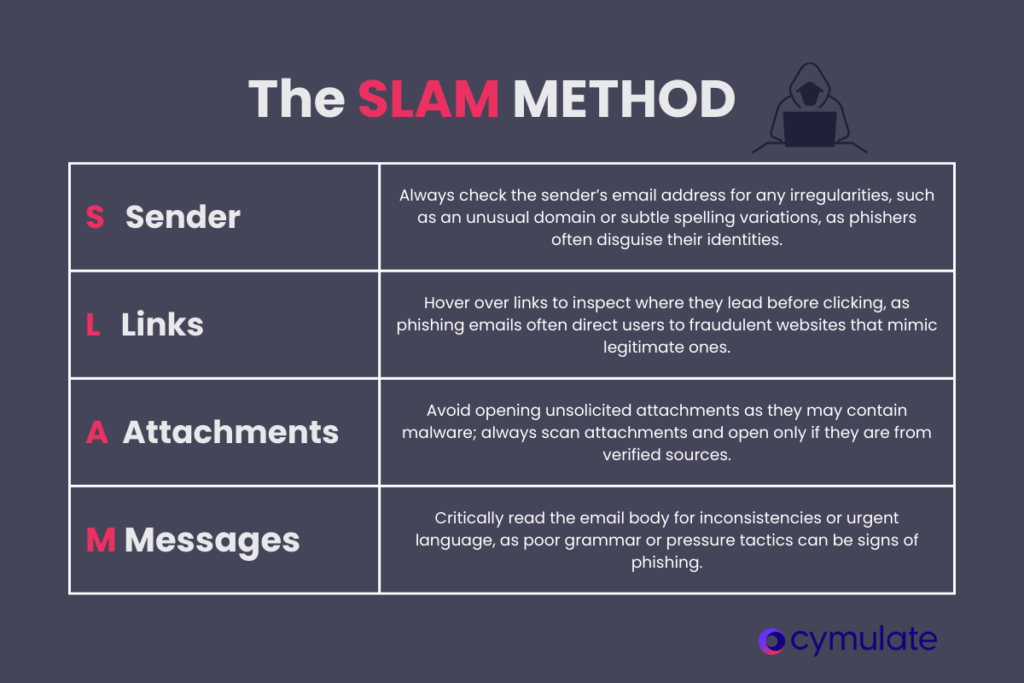
Engaging training sessions bring phishing to life through interactive demonstrations of actual tactics used by hackers. Adding the SLAM method—focusing on evaluating Sender, Links, Attachments, and Message—helps employees systematically assess emails for red flags, reinforcing key skills for spotting phishing attempts.
Employees are more likely to retain the content if sessions incorporate:
- Quizzes and roleplaying scenarios to apply concepts
- Real examples of phishing emails, voicemails, texts, QR codes and malicious sites
- “Phishing labs” where employees identify fraudulent messages
- Gamification through phishing simulations and competitions
- Reward programs for reporting phishing and attending training
Making training fun, interesting, and rewarding helps to fix the material in trainees' memory and build appropriate behavior. Sessions should also provide easily digestible information that employees can apply daily, rather than overwhelming staff with complex technical concepts.
Along with engaging delivery, training content should cover:
- Red flags like urgency, threats, odd links, and spelling errors
- Safe protocols for reporting suspicious messages
- The dangers of clicking links or opening attachments
- Secure password practices
- Social engineering and impersonation techniques
- Current phishing trends and case studies
Cybercriminals rapidly adjust their techniques, so training must stay ahead of emerging trends. Periodic Phishing awareness training content should be updated frequently to address new phishing tactics and the new techniques included in controlled phishing simulations.
The ideal frequency for phishing awareness training varies based on organization size and risk levels but, at minimum, should occur yearly. Combining initial onboarding training with regular refresher courses maintains employees' ability to effectively filter out suspicious incoming messages.
Testing Employees with Simulated Phishing Exercises
Classroom-style awareness training provides a strong foundation. However, the next step of any phishing prevention program should be simulated phishing campaigns that put skills into practice.
These controlled test "phishing" emails allow organizations to safely mimic real-world attacks by sending messages with typical phishing lures. Employee interactions reveal who takes the bait so you can identify high-risk individuals in need of additional coaching.
Requirements for phishing simulation technology
Phishing simulation technology, whether dedicated platforms or capability included in more inclusive platforms, makes it easy to launch simulated campaigns and track detailed results. Features like automated reporting provide analytics on:
- Click rates for links and attachments
- Credential entry rates on fake login pages
- Response rates by department
- Repeat offenders or chronic report skippers
Based on the results, you can double down on training for susceptible departments or high-risk employees. Identifying trends in tactics that evade detection from controlled phishing awareness campaigns assists in identifying knowledge gaps.
For optimal impact, phishing simulations should be ongoing with new campaign scenarios regularly. Start with a baseline assessment, then track improvement over time as training and testing heighten human awareness and resilience.
Improving Defense Against Phishing
An effective phishing awareness training program requires continuously improving over time by learning from metrics, coaching employees, and enhancing content.
Analyze phishing report data will spot areas providing improvement opportunities such as:
- Departments in need of supplemental training
- Phishing tactics with a high success rate
- Failure to report potential threats
With these insights, you can:
- Target awareness gaps with customized content and coaching.
- Identify repeat victims of simulated phishing and have one-on-one talks to understand their challenges
- Require additional training
- Configure additional controls

Continuous phishing awareness training content recommendations
The variety of phishing techniques will continue to grow, so training must always stay one step ahead. Maintaining an adaptive, ever-improving training curriculum is crucial for sharpening human phishing detection skills.
Best practices include:
- Seek direct feedback through surveys and focus groups will provide further visibility into the awareness program blind spots. Opting to encourage openness about clicking or failing to report real phishing attempts has better results than penalizing employees with deficient records.
- Keep training content fresh and relevant by promptly incorporating examples of new phishing methods observed internally or making the rounds externally.
- Localize material to resonate across geographic regions and cultures throughout global organizations.
In the ongoing battle against increasingly convincing phishing scams, combining interactive and engaging training, ongoing testing through simulated campaigns, metrics-driven enhancement of content, and coaching for high-risk individuals are all necessary steps to increase resilience to phishing attempts.
An informed and alert workforce remains the most effective first line of defense. For an advanced, proactive approach to phishing prevention and resilience building, book a demo today and see how continuous security validation can empower your organization against emerging threats.


