Securing and Accelerating Cybersecurity - Part 1
Why Purple Teaming?
Orlando’s FS- ISAC Americas Spring Summit was an exhilarating experience with too many great speakers to count. For those who could not attend, I decided to summarize my own presentation “Securing & Accelerating Cybersecurity with Purple Teaming” So, without further ado, here we go!What is the Ultimate Goal of Purple Teaming?
Purple teaming brings together two disparate teams into one.- Red teams are "attacking" pen testers looking for weaknesses, vulnerabilities, and gaps within your enterprise.
- Blue teams, "defenders" made up of security response SOC teams who need to see how effective they defend against threats.
More Generically, Why Purple Teaming?
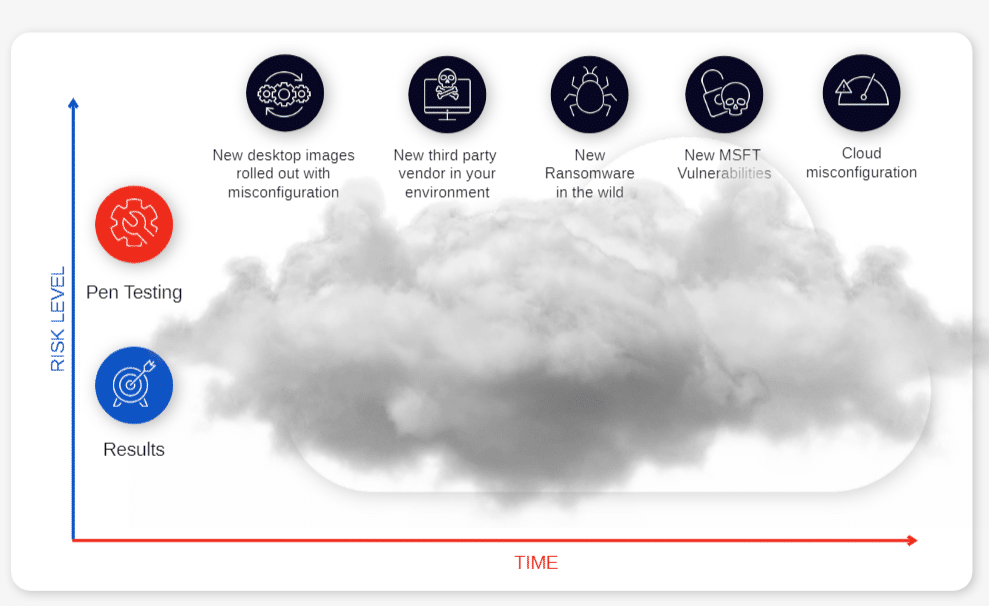
Purple teaming focuses on hardening the security posture far beyond the basic requirement of checking boxes for compliance purposes. At its core, the purple team is combining the traditional reactive defensive methods of a blue team with the insights gained from proactive offensive validation techniques typically used by penetration testers and red teams. The resulting assessments are far more thorough, and the blue and red team collaboration from the start promotes a smooth implementation of the uncovered required mitigations. When run in tandem with continuous security validation techniques, purple teaming integrated with day-to-day IT and DevOps deployments acts as an enabler by accelerating business goals while simultaneously reducing risk. To evaluate how relevant it would be for you to consider adding purple teaming capabilities, it might be useful to ask a few questions about the relevance of purple teaming for your organization, given your existing security infrastructure.Asking the Right Questions
So, let’s start by having a look at the questions that might justify opting for purple teaming when looking at the security validation options.Are you running red teaming or pen testing exercises because you must for compliance reasons, or because you want to improve your security?
Even if satisfying the regulators might limit the fines for non-compliance, it will not deter malicious actors from launching attacks, and, if successful, these attacks might carry heavy costs ranging from loss of IP to damages to users, and, of course, all the cost associated with business interruption, reputational damages, loss of clients, etc. If your goal is to improve security, then periodic pen testing or red teaming exercises will only go so far:- The combination of the frequent deployments inherent to agile development, each of which might introduce new security gaps, and the constant emergence of new vulnerabilities – and related exploits - and new threats render periodic validation exercises obsolete almost as soon as the report is handed in.
- The lack of built-in collaboration between your blue team and the in-house or outsourced validation teams is likely to create friction and result in siloed, potentially antagonistic teams.
Are you buying additional defensive solutions and technologies because you have the budget or because they add a significant delta to your security readiness?
As news of catastrophic breaches is becoming a staple of the regular newscast, awareness of the potential cost of such breaches resulted in a growth of the cybersecurity budget. The chronic shortage of skilled cybersecurity professionals is nowhere near being solved, it is tempting to rush to buy new tools, preferably with AI, ML, and lots of automation to shore up security. Yet, the problems with adding new tools are that:- Despite the vendor's marketing material, they are rarely truly plug-and-forget - Though some level of added security might be added using the tool as-is, each of these new tools needs to be configured individually and collectively to activate their full potential.
- Adding tools adds complexity – Each of these new tools produces data. Collating, organizing, and analyzing that data emanating from numerous sources and translating it into informative insights and actionable decisions become more complicated and less likely as the data mass grows. To add insult to injury, ill-configured tools with adjacent or overlapping capabilities sometimes generate contradictory results.
- More tools mean more alerts – Not only are additional tools adding to the complexity, they may also increase the number of alerts, hence alert fatigue, and the resulting risk of ignoring valid ones.
Can You Monitor and Pre-Empt Security Drift?