Gartner has released its annual Hype Cycle™️ for Security Operations 2022 report with many great insights on the emerging technologies, solutions, and approaches security practitioners should consider adopting.
With all due respect to technologies that are over the hill, I’d like to focus on the left side of the illustration and discuss what’s on the rise, and why it’s so exciting.
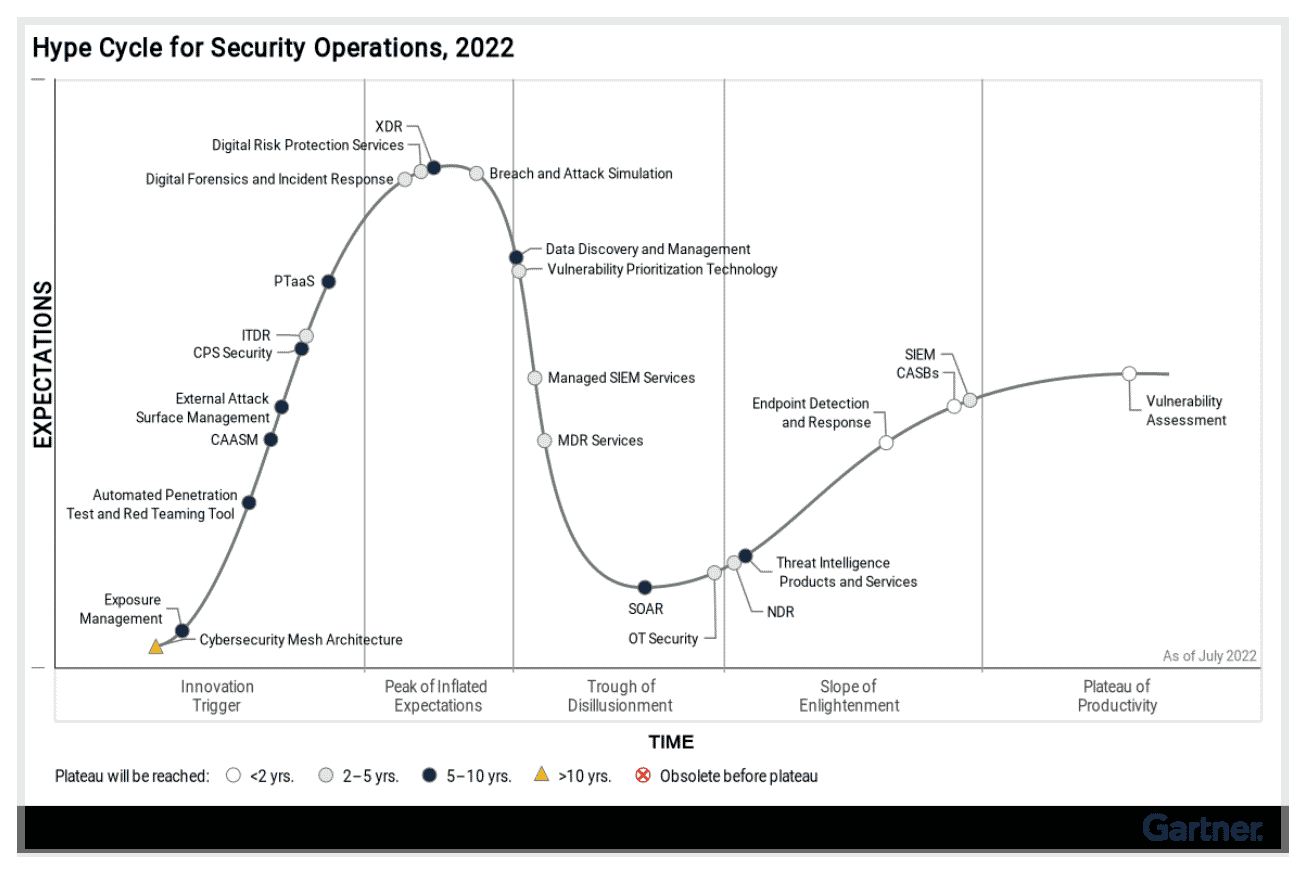
1. The Bottom Left Corner – Exposure Management
Looking at Gartner Hype Cycle for Security Operations 2022, every new-tech geek would first look at what’s new. There we find “Exposure Management”, a program that combines different technologies and tools (such as breach and attack simulation, attack surface management, and automated penetration testing /red-teaming) to eventually reduce the overall risk of cyberattacks.
In essence, Exposure Management is a five-stage program that allows organizations to stay on top of security gaps in their security posture, and continuously work to take corrective measures in a timely manner. It dictates better collaboration between enterprise security and risk management teams to maintain a tolerable level of risk in the long run. EM also mandates a combination of tools and approaches to identify the likelihood of successful attacks and exploits in advance, understand the context and prioritize based on the potential business impact.
2. Look Closer – Into the Mesh
Other than the program, this corner also features cybersecurity mesh architecture. It emerges due to the overcomplexity of cybersecurity defense strategies, that involve many distributed detection and enforcement points and everchanging dataflows. Putting order to all this will take a while, and the prediction is that we’re ten years away from mass adaption.
Why mesh architecture, then?
The consolidation of inputs from the different security solutions and rearranging the data into buckets of real-time dashboards, threat intelligence, and policy management – all in the context of identity and entitlement – allows organizations to take educated decisions that eventually impact their level of risk. Gaining visibility prompts a better reaction.
So now that we know which program to roll out and which architecture to design (and why), let’s look at the different technologies and solutions:
3. At the Peak – Breach and Attack Simulation
Labeled “high benefit” by Gartner Hype Cycle for Security Operations 2022, breach and attack simulation technologies are becoming more and more common. Organizations are looking to use simulated attacks as a production-safe method to continuously test their security controls and improve their performance. BAS tools also allow running SOC tabletop and incident response exercises and provide actionable, prioritized, and prescriptive remediation guidance.
As BAS tools expand their capabilities (such as ASM, VPT, or red team automation) to cover more use cases, they are becoming the foundation of the aforementioned Exposure Management programs
4. Buzzword of the Year – Attack Surface Management
ASM is all the rage in 2022, yet its level of benefit is ranked ‘moderate’.
Split into two approaches – external attack surface management and cyber-asset attack surface management, organizations are becoming aware of the importance of keeping an eye on their digital footprint and the risk exposure associated with it.
CAASM is designed to improve security hygiene and control shadow IT by providing visibility into vulnerabilities of various assets (usually using API) and aggregating the data collected from the different endpoints, servers, and applications.
External Attack Surface Management helps identify exposed assets that are either internet-facing or can be accessed by adversaries who begin their reconnaissance in order to get an initial foothold. Good EASM tools also provide some context and prioritization around discovered vulnerabilities.
5. Automated Red Teaming Tools
This technology is also considered emerging, with only a moderate benefit level. Such tools automate random penetration audits and activities. Not every organization has or uses red teams and penetration tests, and while focusing on automated campaigns, this approach lacks the extensive validation of security controls performance like BAS tools do. However, it makes red teaming activities more accessible and more affordable, minimizing the dependency on annual or semi-annual pen-testing exercises.
All in all, the message of this year’s hype cycle edition is clear – BE PROACTIVE!
A large portion of the security solutions that are emerging and, on the rise, (left side of the hype-cycle chart) are tools used to assess and validate current protections, in different forms. Using such tools changes the fundamental unwritten law of cybersecurity which is that defenders are always a step behind. Automated and Continuous Security Validation technologies allow for establishing a baseline of the security program effectiveness and working towards better cyber resilience while minimizing risk exposure.
Read the full Gartner® Hype Cycle™️ report here.







