Offensive Testing Roadmap: Moving from Annual Pen tests to Continuous Control Validation
With cyber threats being more creative and sophisticated than ever, offensive security testing is now a critical component of an organization’s overall cybersecurity strategy. The evolution of offensive security testing methodologies, from manual pen testing to breach and attack simulation (BAS), tell an important storied timeline of how these technologies have been adapted over time to meet the constantly changing threat landscape.
Testing the Limits of Vulnerability Assessments and Pen Tests
Pen tests date back to the late 1960’s and early 1970’s, primarily being used within military and academic institutions. Early pen tests were focused on identifying basic vulnerabilities in systems and often conducted in-house. With an approach drawing on so much history, it’s easy to see why there are limitations.
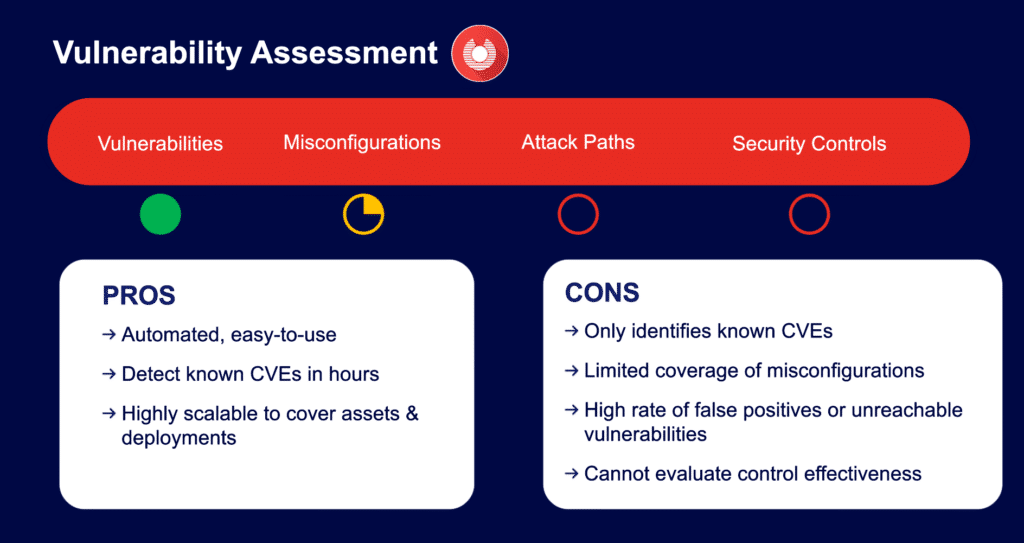
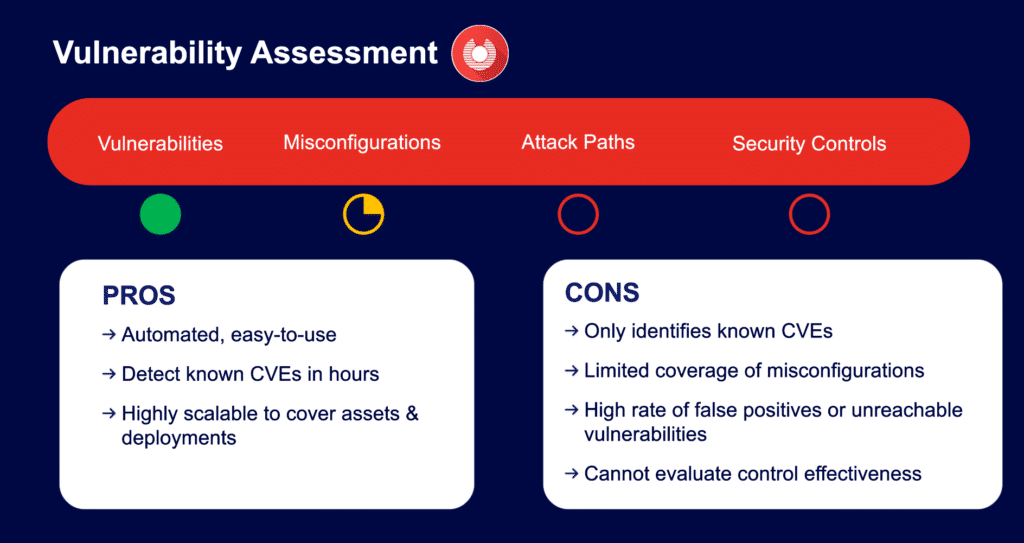
Traditional vulnerability assessments and pen tests often provide only a snapshot of security at a specific moment. Once the test is completed, new vulnerabilities can emerge, leaving an organization exposed until a new assessment is done. These approaches also have limited scopes to specific systems and applications that can lead to blind spots.
Vulnerability assessments can generate false positives, meaning it would be incorrectly identifying a vulnerability or a false negative, and failing to identify an existing vulnerability. This can lead to wasted resources, time and money, while leaving the organization still exposed.
How BAS Automates and Enhances Security Testing
With breach and attack simulation, security teams can implement real-world attack simulations in a controlled environment, offering a significantly more effective security testing approach. This is also where security control validation comes into play with automated, continuous testing and validation, comprehensive coverage, reduced resources needed and easy security tools integration.
BAS allows organizations to assess their security posture in real-time, helping to identify new vulnerabilities as they arise. Organizations can use BAS to easily simulate things like phishing, ransomware and lateral movement. This comprehensive coverage helps organizations identify weaknesses across their environment, including networks, applications, clouds and endpoints.
Every organization looks for ways to spend less, and by automating the testing process, BAS can reduce the need for extensive manual intervention, allowing security teams to focus on higher-priority tasks. This makes security testing more efficient and cost-effective. Many BAS solutions integrate with existing security tools, such as security information and event management (SIEM) systems and vulnerability management platforms. This integration allows organizations to streamline their security processes and gain a more holistic view of their security posture.
5 Best Practices for Implementing Continuous Security Validation
Implementing continuous security validation requires a proactive, integrated approach that involves people, processes and technology. It is essential for maintaining a holistic and strengthened cybersecurity posture in today’s dynamic threat landscapes.
Here are five best practices for implementing continuous security validation:
- Use comprehensive tools – Implement BAS to continuously simulate real-world attacks, assess security controls and use automated vulnerability scanning to identify and remediate vulnerabilities regularly.
- Integrate with DevSecOps – Incorporate security into the software development lifecycle (SDLC) by embedding security practices early in development and use automated security testing tools within CI/CD pipelines to ensure security checks are part of every deployment.
- Adopt a risk-based approach – Prioritize and identify critical assets based on their value and potential impact on the organization. Conduct threat modeling to understand potential threats and vulnerabilities specific to your environment.
- Implement security monitoring – Set-up continuous monitoring of network traffic, endpoints and cloud environments to detect suspicious activities and use SIEM systems to analyze logs for unusual behavior or potential breaches.
- Foster a security culture – Conduct regular training sessions for employees on security best practices and phishing awareness while creating an environment where employees feel comfortable reporting suspicious activities or potential security threats.
Key Takeaways
The evolution of offensive security testing methodologies reflects the dynamic nature of cyber threats. From the early days of basic pen testing to the more advanced approaches of today, there is no doubt that an organization’s security posture or any decision-maker aiming to optimize security investments must take a hard look at their testing methodologies to ensure their defenses remain resilient.
If you missed the live webinar in action, watch the replay to learn how Cymulate can help put your security team on the offensive.