Red Team vs Blue Team vs Purple Team in Cybersecurity

The cyber industry has adopted red, blue, and purple to distinguish between the different responsibilities that contribute to an organization’s cyber resilience. Cybersecurity departments rely on their Red, Blue, and Purple Teams to work in unison to identify vulnerabilities and security gaps, defend against attacks, and optimize security measures.
Overview and Breakdown of Each Team
Each team has its area of responsibility and main tasks that it is expected to accomplish.
| Team | Main Purpose | Main Tasks |
| Blue Team | Defenders who detect and respond to cyberattacks | Monitoring, incident response, threat hunting |
| Red Team | Ethical hackers who simulate cyberattacks to test an organization’s resilience and find weaknesses | Ethical hacking, penetration testing, exploit discovery |
| Purple Team | Integrate Red and Blue team activities | Combine offensive and defensive strategies for continuous improvement |
Blue Team
Blue Teams are composed of defensive security professionals, such as security analysts, incident responders, and network defenders, dedicated to protecting the organization from cyber threats.
The Blue Team protects data and internal systems, detects and responds to incidents, and strengthens an organization’s security posture.
Blue Teams implement, validate, and fine-tune their organizations’ security controls and SIEM (security information and event management) and improve their detection and response capabilities.
The Blue Team focuses on defensive strategies and real-time threat mitigation by monitoring threats and detecting anomalies.
Red Team
While Blue Teams play defense, Red Teams play offense. Red Teams are comprised of offensive security experts, such as ethical hackers, penetration testers, and security researchers, who simulate real-world cyberattacks to identify vulnerabilities before malicious actors can exploit them.
The Red Team’s main objective is to uncover security weaknesses, test incident response, and provide the Blue Team with actionable insights for improvements.
To test an organization’s defenses comprehensively, the Red Team adopts the mindset of attackers, using similar tactics like social engineering, phishing, network infiltration, and exploitation of known vulnerabilities.
Purple Team
Purple Teams bridge the gap between Red and Blue Teams, facilitating opportunities for collaboration to optimize security efforts.
This team is not formal but more of an integration of Blue and Red Teams during exercises to combine offensive and defensive strategies.
For this reason, it’s been said that Blue and Red Teams are nouns while Purple Team is verb – as in Purple Teaming is what Blue and Red Teams do when they collaborate on Purple Team exercises.
Purple Team activities aim to improve overall security posture, enhance collaboration, and ensure continuous improvement. They are an excellent way for organizations to take a more proactive approach to security and bulk up defenses before an attack occurs.
Shared Challenges of Red Teams, Blue Teams and Purple Teams
While each team has its own responsibilities, some of their challenges overlap.
1. Limited resources
Security teams are often understaffed and struggle to keep up with specific responsibilities. Blue Teams that are insufficiently staffed struggle to keep up with the volume of alerts and incidents, and Red Teams that don’t have enough manpower will be limited in the scope and depth of their testing. If Blue and Red Teams are understaffed, their limitations will also impact how much time they can invest in Purple Team activities.
2. Rapidly evolving threat landscape
Many organizations use threat feeds so that Red, Blue, and Purple Teams can stay on top of emergent threats to fulfill their different responsibilities. However, due to information overload, security teams often can’t determine the most dangerous threats to their organization, putting them at risk.
3. Communication gaps
Blue and Red Teams need effective communication to improve defenses, but because each team has different objectives, this can lead to conflicting priorities. For example, Red Teams may create extensive reports detailing security weaknesses, while Blue Teams require clear, actionable items to reduce risk. Typically, Purple Teams would bridge this communication gap by aligning both teams' goals.
A Shared Solution: Breach and Attack Simulation
Because the Blue, Red, and Purple Teams share challenges, they can also find value in the same solution, such as Breach and Attack Simulation (BAS). BAS continuously tests the effectiveness of an organization's security posture by simulating real-world cyberattacks. It helps organizations take the attacker’s perspective by identifying vulnerabilities and gaps, validating security controls, and ensuring their defenses can withstand real threats.
Blue, Red, and Purple Teams can all benefit from BAS, which provides solutions to the challenges outlined above.
1. Limited resources --> Automation
BAS provides the automation that significantly benefits understaffed Red, Blue, and Purple Teams by enhancing their productivity, efficiency, and effectiveness in testing and validating security measures.
With an extensive library of threat-intelligence-led risk assessments, BAS reduces Red Teams’ manual effort in creating and running these tests. Automation enables Red Teams to scale their testing across IT environments with detail into different layers of each control.
Blue Teams can independently run customized assessments to validate security controls against emergent threats, confirm remediations, and prepare for audits without needing Red Teams to re-run tests. BAS also provides Blue Teams with immediate feedback on the effectiveness of security controls and offers practical remediation guidance, helping to address vulnerabilities quickly.
BAS empowers Purple Teams by enabling Red and Blue Teams to collaborate more effectively by providing a unified platform where both Teams can run and analyze simulations, share insights, and improve overall security posture.
2. Rapidly evolving threat landscape --> Immediate Threats Intelligence
BAS platforms should have threat research groups who update the platform daily with attack simulations of these latest threats that require urgent attention and action. These assessments test security controls against new and emerging threats observed in the wild. Each assessment uses the exact IOCs and TTPs of that threat. Threat and simulation updates include insights into threat actors, attack vectors, techniques mapped to MITRE ATT&CK, and indicators of compromise.
With BAS, Red Teams can automate the platform to run simulations of the latest threats as soon as they emerge, relieving them of a time-consuming and labor-intensive task. The Immediate Threats Intelligence report allows Blue Teams to understand assessment results easily. If a threat penetrates the organization, Blue Teams can focus their efforts and follow easy-to-digest remediation guidance to optimize controls. Blue Teams can then independently re-run the assessment to ensure protection. This reinforces collaboration between Blue and Red Teams, helping them reach the stature of a Purple Team.
3. Communication gaps --> Reporting and remediation guidance
BAS platforms include reporting and remediation guidance to significantly enhance communication and collaboration between Red, Blue, and Purple Teams by providing clear, actionable insights and fostering a unified understanding of security posture and remediation priorities. Data-driven insights allow for fact-based discussions about security improvements so all teams can be on the same page.
Take a Proactive Approach to Cybersecurity with Cymulate BAS
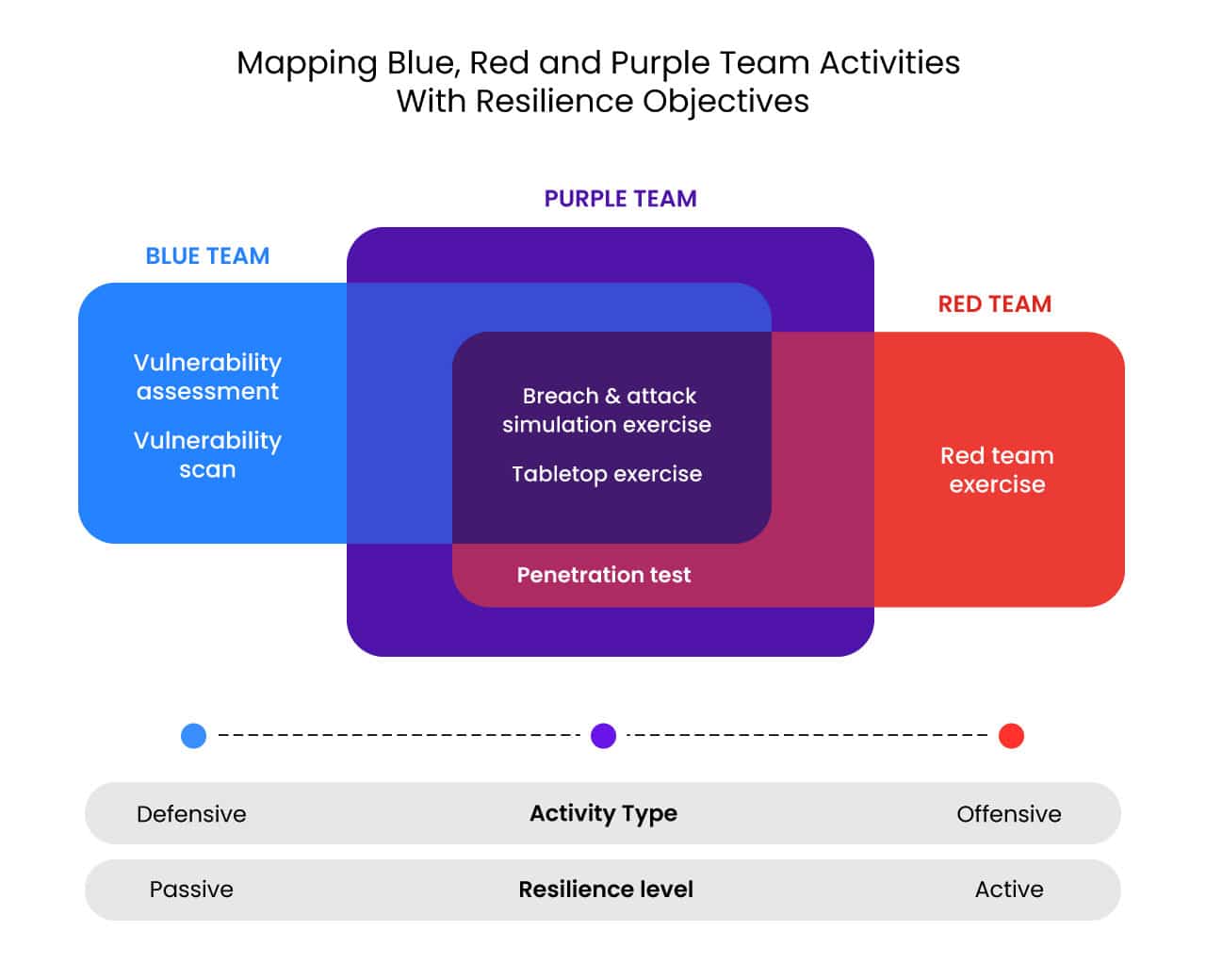
Cymulate Breach and Attack Simulation provides the automation, immediate threat intelligence, and reporting mentioned above. It is simple to deploy and use, offers comprehensive coverage, and is highly customizable. Cymulate BAS enables Blue and Red Teams to work together and integrate offensive and defensive security measures, essentially creating a Purple Team function. Continuous security validation encourages organizations to take a more proactive approach to security to provide better resilience, as depicted in the diagram below from the Gartner Report Quick Answer: Key Objectives of Blue, Red and Purple Teams.
If you are interested in seeing how Cymulate BAS can help your Red, Blue, and Purple Teams increase collaboration and take a proactive approach to cybersecurity, you can schedule a demo here: