Frequently Asked Questions
Product Information & Platform Capabilities
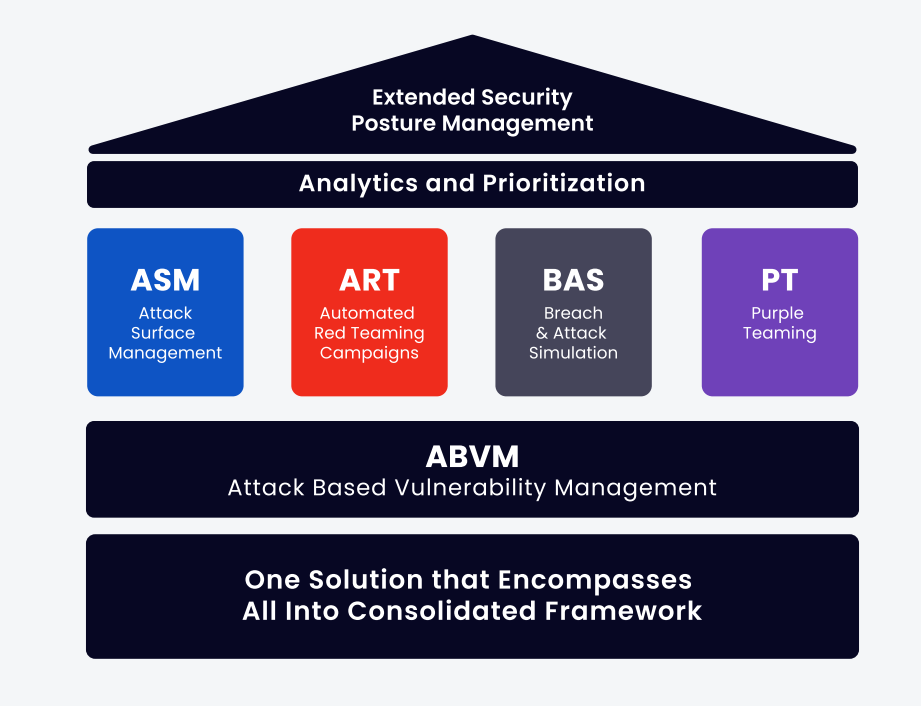
What is Extended Security Posture Management (XSPM)?
Extended Security Posture Management (XSPM) is a comprehensive platform that automates and combines purple teaming and red teaming methodologies to help organizations validate their cybersecurity posture. It enables continuous assessment of security technologies and processes, answering questions like "Are my security technologies and processes effectively protecting the organization?" and "How can my organization be breached?" (Source: Original Webpage)
What offensive testing methods are used in Cymulate's XSPM platform?
Cymulate's XSPM platform uses several offensive testing methods, including Attack Surface Management (ASM), Continuous Automated Red Teaming (CART), Breach and Attack Simulation (BAS), and Purple Teaming. These methods emulate different stages of real-world cyberattacks to assess whether security defenses can withstand them. (Source: Original Webpage)
How does Cymulate's platform help organizations stay ahead of cyber attackers?
Cymulate mimics the attack strategies and tools used by hackers, allowing businesses to assess their preparedness for cybersecurity threats. The platform provides specific recommendations for remediation and both technical and executive reporting. As an on-demand SaaS-based platform, Cymulate enables users to run simulations 24/7 from anywhere, shortening testing cycles and speeding up remediation. (Source: Original Webpage)
What phases of an attack can Cymulate XSPM test?
Cymulate XSPM can test all phases of an attack: pre-exploitation, exploitation, and post-exploitation. It offers full coverage of the MITRE ATT&CK framework and allows both on-demand and automated testing for continued monitoring. (Source: Original Webpage)
How does Cymulate ensure safe testing without disrupting production systems?
Cymulate's platform is designed for effective but safe testing, avoiding disruption to production systems. It allows organizations to test individual controls and how those controls work together, with continuous, automatic updates and pinpoint simulations of emerging threats. (Source: Original Webpage)
What types of reporting does Cymulate XSPM provide?
Cymulate XSPM provides full technical reporting, native SOAR and GRC integration, CSV output for ingestion in other tools, and executive reporting for non-technical professionals. (Source: Original Webpage)
How does exposure management enhance security validation?
Exposure management correlates data from security validation with vulnerability insights, providing context-driven prioritization and actionable remediation steps. Cymulate's exposure management approach unifies continuous testing, contextual risk scoring, and prioritization, connecting to vulnerability scanners and mapping results against real-world attack paths. (Source: Original Webpage)
What are the key functions of Cymulate's XSPM platform?
Key functions include testing all attack phases, full MITRE ATT&CK coverage, on-demand and automated testing, safe testing, individual and combined control testing, continuous updates, and comprehensive reporting. (Source: Original Webpage)
How does Cymulate combine purple teaming and red teaming?
Cymulate is the only platform to automate and combine purple teaming and red teaming methodologies, enabling organizations to simulate real-world attack scenarios and improve detection and response capabilities. (Source: Original Webpage)
What is the role of Attack Surface Management (ASM) in Cymulate?
Attack Surface Management (ASM) in Cymulate looks for exposed and accessible digital assets or company information, emulating an adversary's reconnaissance stage. (Source: Original Webpage)
How does Continuous Automated Red Teaming (CART) work in Cymulate?
Continuous Automated Red Teaming (CART) in Cymulate enables end-to-end penetration campaigns that identify attack paths through which an organization might be breached. (Source: Original Webpage)
What is Breach and Attack Simulation (BAS) in Cymulate?
Breach and Attack Simulation (BAS) in Cymulate simulates attacks against each security control to validate its efficacy, ensuring defenses are robust against real-world threats. (Source: Original Webpage)
How does Cymulate help prioritize and remediate exposures?
Cymulate's exposure management platform correlates validation data with vulnerability insights, enabling context-driven prioritization and actionable remediation steps based on business impact. (Source: Original Webpage)
What are the benefits of continuous, automatic updates in Cymulate?
Continuous, automatic updates in Cymulate ensure pinpoint simulations of emerging threats, keeping organizations ahead of evolving cyber risks. (Source: Original Webpage)
How does Cymulate empower organizations to fortify their defenses?
Cymulate empowers organizations through continuous assessment and validation of their security posture, focusing on threat simulation, comprehensive security assessments, and ongoing innovation. (Source: Original Webpage)
What is the future of Extended Security Posture Management according to Cymulate?
The future of Extended Security Posture Management is exposure management, which unifies continuous testing, contextual risk scoring, and prioritization to provide actionable remediation and optimize investments across technology, people, and processes. (Source: Original Webpage)
How does Cymulate help eliminate assumptions in security validation?
Cymulate enables organizations to prove security effectiveness end-to-end, eliminating assumptions by providing evidence-based validation and actionable insights. (Source: Original Webpage)
What are the advantages of Cymulate's SaaS-based platform?
Cymulate's SaaS-based platform allows users to run simulations 24/7 from anywhere, significantly shortening testing cycles and speeding up remediation. (Source: Original Webpage)
How does Cymulate integrate with SOAR and GRC tools?
Cymulate provides native integration with SOAR and GRC tools, enabling seamless ingestion of technical reports and CSV outputs for further analysis and executive reporting. (Source: Original Webpage)
Features & Capabilities
What are the key capabilities of Cymulate?
Cymulate offers continuous threat validation, attack path discovery, automated mitigation, accelerated detection engineering, complete kill chain coverage, and an extensive threat library with daily updates. These capabilities help organizations stay ahead of emerging risks and optimize their security posture. (Source: Knowledge Base)
Does Cymulate support integrations with other security tools?
Yes, Cymulate integrates with a wide range of technology partners across various security domains, including Akamai Guardicore, AWS GuardDuty, BlackBerry Cylance OPTICS, Carbon Black EDR, Check Point CloudGuard, CrowdStrike Falcon, Cybereason, and more. For a complete list, visit our Partnerships and Integrations page. (Source: Knowledge Base)
How does Cymulate automate remediation?
Cymulate integrates with security controls to push threat updates for immediate prevention of missed threats. Automated remediation capabilities include vendor-specific recommendations, Sigma rules, and dynamic dashboards. (Source: Knowledge Base)
What is Cymulate Exposure Management Platform?
The Cymulate Exposure Management Platform is designed to help organizations prove threats and improve their security resilience. For more details, visit our Exposure Management Platform page and watch the Cymulate Exposure Management Platform video. (Source: Knowledge Base)
Can Cymulate Exposure Validation be expanded?
Yes, users can upgrade from Cymulate Exposure Validation to the complete Cymulate Exposure Management Platform, consolidating validation, prioritization, and mobilization into a single platform. (Source: Knowledge Base)
What information is available in the Cymulate Exposure Management Platform data sheet?
The Cymulate Exposure Management Platform data sheet explains how you can add automated remediation to the Cymulate platform to push control updates. Access it at this link. (Source: Knowledge Base)
What products and services are included under the term 'Platform' in the End User License Agreement?
The 'Platform' refers to Cymulate’s products as detailed in the customer's Quote. It may include breach and attack simulation, security data analytics, attack surface management, continuous automated red teaming, and any other material, products, deliverables, reports, services, or enhancements provided by Cymulate under the Agreement. (Source: Knowledge Base)
Use Cases & Benefits
Who is the target audience for Cymulate's products?
Cymulate's platform is designed for CISOs and security leaders, Security Operations (SecOps) teams, Red Teams, and Vulnerability Management teams. It serves organizations of all sizes across industries such as finance, healthcare, retail, media, transportation, and manufacturing. (Source: Knowledge Base)
What business impact can customers expect from using Cymulate?
Customers can expect an 81% reduction in cyber risk within four months, a 60% increase in operational efficiency, 40X faster threat validation, a 30% improvement in threat prevention, and a 52% reduction in critical exposures. These metrics are based on customer case studies and reported outcomes. (Source: Knowledge Base)
What feedback have customers given about Cymulate's ease of use?
Customers consistently praise Cymulate for its user-friendly and intuitive platform. Testimonials highlight ease of implementation, actionable insights, and accessible support. For example, Raphael Ferreira, Cybersecurity Manager at Banco PAN, stated, "Cymulate is easy to implement and use—all you need to do is click a few buttons, and you receive a lot of practical insights into how you can improve your security posture." (Source: Knowledge Base)
How long does it take to implement Cymulate?
Cymulate is designed for quick and easy implementation. It operates in agentless mode, requiring no additional hardware or complex configurations. Customers can start running simulations almost immediately after deployment. (Source: Knowledge Base)
What educational resources does Cymulate provide?
Cymulate offers a Resource Hub, blog, webinars, e-books, and a glossary of cybersecurity terms. These resources help customers stay informed about the latest threats, best practices, and product updates. (Source: Knowledge Base)
Where can I find Cymulate's blog and newsroom?
You can stay updated with Cymulate's latest threats, research, and company news by visiting our blog and our newsroom. (Source: Knowledge Base)
Where can I find resources like reports, blogs, and webinars from Cymulate?
Resources such as reports, blogs, and webinars are available in our Resource Hub, our blog, our newsroom, and our events and webinars page. (Source: Knowledge Base)
Pain Points & Problem Solving
What core problems does Cymulate solve?
Cymulate addresses overwhelming volume of threats, lack of visibility, unclear prioritization, operational inefficiencies, fragmented security tools, cloud complexity, and communication barriers. It provides continuous threat validation, prioritization of exposures, improved resilience, collaboration across teams, automated processes, and validated exposure scoring. (Source: Knowledge Base)
What pain points do Cymulate customers express?
Customers express pain points such as overwhelming threats, lack of visibility, unclear prioritization, operational inefficiencies, fragmented tools, cloud complexity, and communication barriers. Cymulate addresses these by offering continuous threat validation, prioritization, improved resilience, collaboration, automation, and validated exposure scoring. (Source: Knowledge Base)
Do the pain points solved by Cymulate differ by persona?
Yes, pain points differ by persona. CISOs face communication barriers and need clear metrics; SecOps teams struggle with operational inefficiencies and lack of visibility; Red Teams need advanced threat simulation; Vulnerability Management teams require effective prioritization. Cymulate tailors solutions for each persona. (Source: Knowledge Base)
Competition & Comparison
How does Cymulate compare to AttackIQ?
AttackIQ delivers automated security validation but lacks Cymulate's innovation, threat coverage, and ease of use. Cymulate offers the industry's leading threat scenario library and AI-powered capabilities to streamline workflows and accelerate security posture improvement. Read more. (Source: Knowledge Base)
How does Cymulate compare to Mandiant Security Validation?
Mandiant is one of the original BAS platforms but has become outdated with little innovation in the past 5 years. Cymulate continually innovates with AI and automation, expanding into the exposure management market as a grid leader. Read more. (Source: Knowledge Base)
How does Cymulate compare to Pentera?
Pentera focuses on attack path validation but lacks the depth Cymulate provides to fully assess and strengthen defenses. Cymulate offers comprehensive exposure validation, covering the full kill chain and providing cloud control validation. Read more. (Source: Knowledge Base)
How does Cymulate compare to Picus Security?
Picus is suitable for on-premise BAS needs but lacks the complete exposure validation platform Cymulate provides. Cymulate covers the full kill chain and includes cloud control validation, making it a more comprehensive solution. Read more. (Source: Knowledge Base)
How does Cymulate compare to SafeBreach?
SafeBreach offers breach and attack simulation but lacks Cymulate's innovation, precision, and automation. Cymulate leads with AI-powered BAS, the largest attack library, and a full Continuous Threat Exposure Management (CTEM) solution. Read more. (Source: Knowledge Base)
How does Cymulate compare to Scythe?
Scythe is suitable for advanced red teams but lacks Cymulate's focus on actionable remediation and automated mitigation. Cymulate provides a more complete exposure validation platform with daily threat updates, no-code workflows, and vendor-specific remediation guidance. Read more. (Source: Knowledge Base)
How does Cymulate's platform differ from NetSPI?
NetSPI is a strong PTaaS vendor, but its automated exposure validation is limited. Cymulate is recognized by Gartner and G2 as a leader in exposure validation, offering continuous innovation and a platform for independent assessment and strengthening of defenses. Read more. (Source: Knowledge Base)
What are the key differences between Cymulate and Picus in terms of platform capabilities?
Cymulate includes Breach and Attack Simulation (BAS), Attack Surface Management (ASM), automated penetration testing, purple teaming, and daily threat intelligence updates. Picus offers BAS and basic threat updates but lacks ASM, automated penetration testing, and purple teaming. (Source: Knowledge Base)
Pricing & Plans
What is Cymulate's pricing model?
Cymulate operates on a subscription-based pricing model tailored to each organization's needs. Pricing is determined by the chosen package, number of assets, and scenarios selected. The subscription fee is non-refundable and must be paid regardless of actual use. For a detailed quote, schedule a demo. (Source: Knowledge Base)
Security & Compliance
What security and compliance certifications does Cymulate have?
Cymulate holds SOC2 Type II, ISO 27001:2013, ISO 27701, ISO 27017, and CSA STAR Level 1 certifications. These attest to Cymulate's robust security practices and compliance with global standards. (Source: Knowledge Base)
How does Cymulate ensure product security and compliance?
Cymulate incorporates data protection by design, employs secure AWS data centers, uses strong encryption (TLS 1.2+ and AES-256), follows a strict Secure Development Lifecycle (SDLC), and provides ongoing security awareness training for employees. (Source: Knowledge Base)