Blue Teaming
What is a Blue Team in Cybersecurity?
In cybersecurity, a Blue Team is a group of security professionals tasked with defending an organization's assets against cyberattacks. The Blue Team uses various tools and techniques to identify, assess, and mitigate security risks.
Blue Teams often work in tandem with Red Teams, who act as ethical hackers to test the organization's defenses. By simulating real-world attack scenarios, Blue Teams can better understand an organization's security posture and identify areas for improvement.
What Does a Blue Team Do?
Blue Teams are composed of defensive security professionals, such as security analysts, incident responders, and network defenders, dedicated to protecting the organization from cyber threats.
While the tasks and responsibilities of a blue team can vary between organizations depending on their industry’s threat landscape, company size, and budget, the most common tasks performed by a blue team are:
- Monitoring and Detection: Blue Teams continuously monitor networks, systems, and applications for suspicious activities or anomalies. This involves analyzing logs, alerts, and data from security tools to detect potential threats in real-time.
- Incident Response: Blue Teams are responsible for responding when a security breach or incident occurs. The same goes for simulated attacks, where the Blue Teams are responsible for devising a defense strategy against the Red Teams' discoveries.
- Vulnerability Management: Blue Teams proactively identify and remediate vulnerabilities in systems, applications, and networks. This includes conducting regular vulnerability assessments and implementing patches or mitigation strategies.
- Security Control Validation: Ensuring that the organization’s security controls, such as firewalls, intrusion detection systems, and endpoint protection, are correctly configured and function as intended.
Methods and Tactics Used by Blue Teams
Blue Teams employ various methods and tactics to assess and optimize a robust cybersecurity posture. Their approach is often tailored to the threat landscape, scope, and specific needs of the organization. Standard techniques include continuous monitoring of network traffic and system logs to detect suspicious activity alongside Endpoint Detection and Response (EDR) tools that protect endpoints from advanced threats.
In addition to reactive strategies, Blue Teams often engage in proactive threat hunting, using behavioral analytics to spot anomalies that could indicate potential risks. They may also deploy deception technologies like honeypots to gather intelligence on attackers without exposing real systems.
To improve efficiency, Blue Teams can streamline tasks using security orchestration, automation, and response (SOAR) platforms, while AI and machine learning help detect subtle threats in real-time.
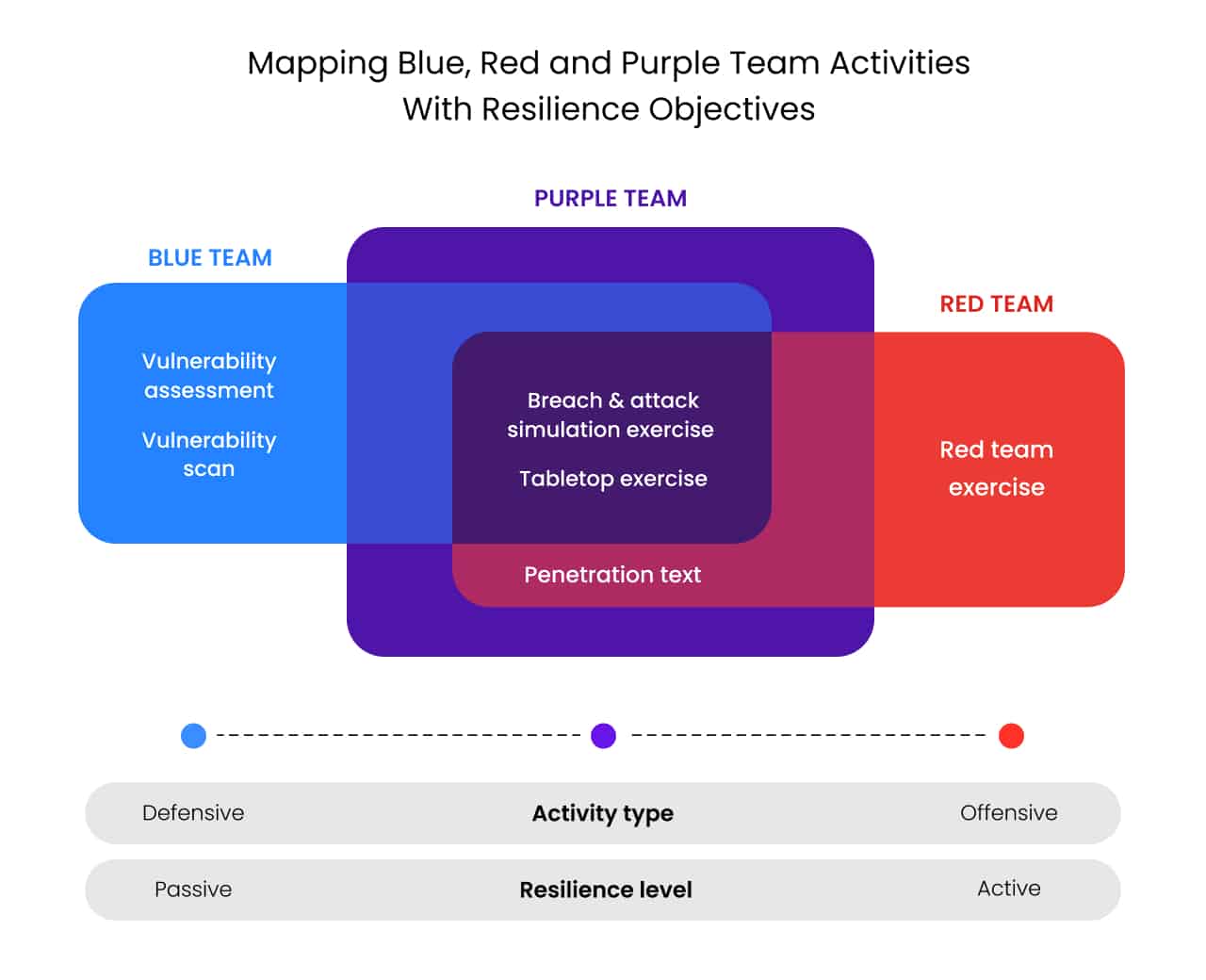
Blue Team vs Red Team and Purple Team
While the Red Team plays offense, the Blue Team plays defense, and the Purple Team combines offensive and defensive strategies. Blue Teams are often tasked with composing a mitigation and response strategy based on Red Teams’ findings.
For instance, a Red Team attack might include a simulated phishing campaign targeting employees to gain unauthorized access to sensitive information. After identifying which employees clicked on malicious links or opened phishing emails, the Blue Team would develop a mitigation strategy that includes refining email filtering rules, strengthening authentication measures, and singling out staff that require additional training on recognizing phishing attempts.
On the other hand, a Purple Team takes a more collaborative approach, combining the Red Team's offensive insights with the Blue Team's defensive strategies in real-time.
For example, instead of waiting for the Red Team’s report after a phishing simulation, the Purple Team would work alongside both teams throughout the process. As the Red Team launches their simulated attacks, the Purple Team helps the Blue Team improve detection and response strategies on the fly. This leads to faster adjustments, such as real-time refinement of security controls and enhanced awareness training.
Blue Teams’ Challenges
Having a professional and seasoned Blue Team as part of your cybersecurity department can significantly benefit any organization. However, Blue Teams face the challenge of staying ahead of the constantly evolving threat landscape, as attackers are always developing new techniques to take down even the strongest cyber defense. Therefore, Blue Teams must regularly update threat intelligence, detection rules, and security tools to remain effective.
This can be a tall order even for the most seasoned Blue Teams. Resource limitations, such as budget constraints and a lack of personnel, make staying ahead of the evolving threat landscape even more difficult. The Blue Team also depends on strong collaboration with Red Teams and other departments to ensure the implementation of their strategies.
Exposure Management to Help Prioritize Risks
The biggest hurdle for Blue Teams is the sheer volume of data they must analyze, as continuous monitoring of networks, systems, and endpoints generates vast amounts of logs and alerts. This can lead to alert fatigue, where critical threats may be overlooked. Additionally, new threats that emerge daily can overwhelm security teams and make it difficult to determine which are the most dangerous threats to their organizations.
Exposure management provides a framework for Blue Teams to view their cyber assets and support processes from the attacker’s view of the organization. With this approach, Blue Teams can identify the biggest gaps and prioritize appropriate remediation. By prioritizing the most critical threats, Blue Teams can focus on addressing the most significant vulnerabilities and potential attack vectors, reducing the likelihood of missing high-priority incidents.
Exposure management helps Blue Teams streamline their efforts, ensuring they can respond swiftly and effectively to the most dangerous threats rather than being overwhelmed by lower-risk alerts.

How Cymulate Helps Blue Teams
Cymulate provides the essential technologies, workflows, and metrics to help Blue Teams drive exposure management. Cymulate's platform combines full visibility of the attack surface with business context and the most advanced security validation to focus remediation and prove cyber resilience.
Through the automation of exposure discovery, security validation, and actionable remediation plans, Cymulate provides Blue Teams continuous assessments that transform one-off exercises into a repeatable program to strengthen security posture before the next attack.