Proactive Security
Proactive security is a preventive approach to protecting systems, data, and networks. Instead of waiting for threats to emerge, it anticipates and neutralizes risks before they cause harm. This strategy involves continuous monitoring, risk assessments, and implementing security measures before an attack happens.
Proactive vs. Reactive Security
The key difference between proactive and reactive security lies in timing and effectiveness:
- Proactive security focuses on incident prevention—identifying vulnerabilities, enforcing security policies, and using advanced threat detection.
- Reactive security responds after an attack, often leading to downtime, financial loss, and reputational damage.
With cyber threats being more sophisticated than ever, a proactive cybersecurity mindset is essential for ensuring a safer digital environment. Organizations must detect threats early with AI-driven monitoring, close security gaps before attackers exploit them, and educate employees to prevent human errors.
Core Components of Proactive Security
Proactive security requires a strategic approach that continuously strengthens defenses. The following components are essential to making security proactive, effective, and resilient.
Threat intelligence
Threat intelligence helps organizations anticipate attacks before they happen. By gathering and analyzing data on emerging threats, security teams can recognize patterns, understand attacker tactics, and prepare countermeasures. Key aspects of threat intelligence include:
- Data collection: Sources include open-source intelligence (OSINT), dark web monitoring, and internal security logs.
- Analysis: Identifying trends and indicators of compromise (IoCs) to predict future attacks.
- Actionable insights: Using intelligence to update security policies, patch vulnerabilities, and train employees on evolving threats.
By leveraging threat intelligence, organizations can shift from a reactive stance to a proactive security posture.
Continuous monitoring
24/7 monitoring is critical to detecting threats early. Cyberattacks often start with small, unnoticed activities that escalate over time. Continuous monitoring helps spot these signs before they become major breaches. Continuous monitoring includes:
- Real-time detection: Security tools analyze network traffic, user behavior, and system logs for anomalies.
- Automated alerts: Immediate notifications allow teams to respond quickly to suspicious activities.
- Behavioral analysis: Identifying unusual patterns that might indicate an insider threat or a compromised account.
By constantly scanning for threats, organizations can respond swiftly and prevent potential damage.
Vulnerability management
Cybercriminals exploit weaknesses in systems. Proactively identifying and fixing these vulnerabilities reduces the risk of an attack. Steps to effective vulnerability management:
- Regular assessments: Conduct frequent scans to find security gaps.
- Patch management: Apply updates to operating systems, applications, and hardware as soon as fixes become available.
- Penetration testing: Simulating attacks helps identify weak points before hackers do.
A strong vulnerability management program ensures systems remain secure against evolving threats.
Security control validation
Security control validation is not a tool or a framework, but rather the process of making sure that security controls such as firewalls, email gateways, data exfiltration, endpoint and cloud security etc., are correctly implemented, configured, and able to mitigate risks as expected. It’s an essential part of a proactive security strategy as it helps organizations identify potential problems with their security posture and mitigate potential vulnerabilities detected in the validation process. Ways to validate security controls:
- Red team exercises: Ethical hackers attempt to breach security to uncover weaknesses.
- Purple teaming: Collaboration between offensive (red) and defensive (blue) teams to strengthen defenses.
- Automated security validation: Regularly running scripts and tools to test firewalls, antivirus solutions, and endpoint protection.
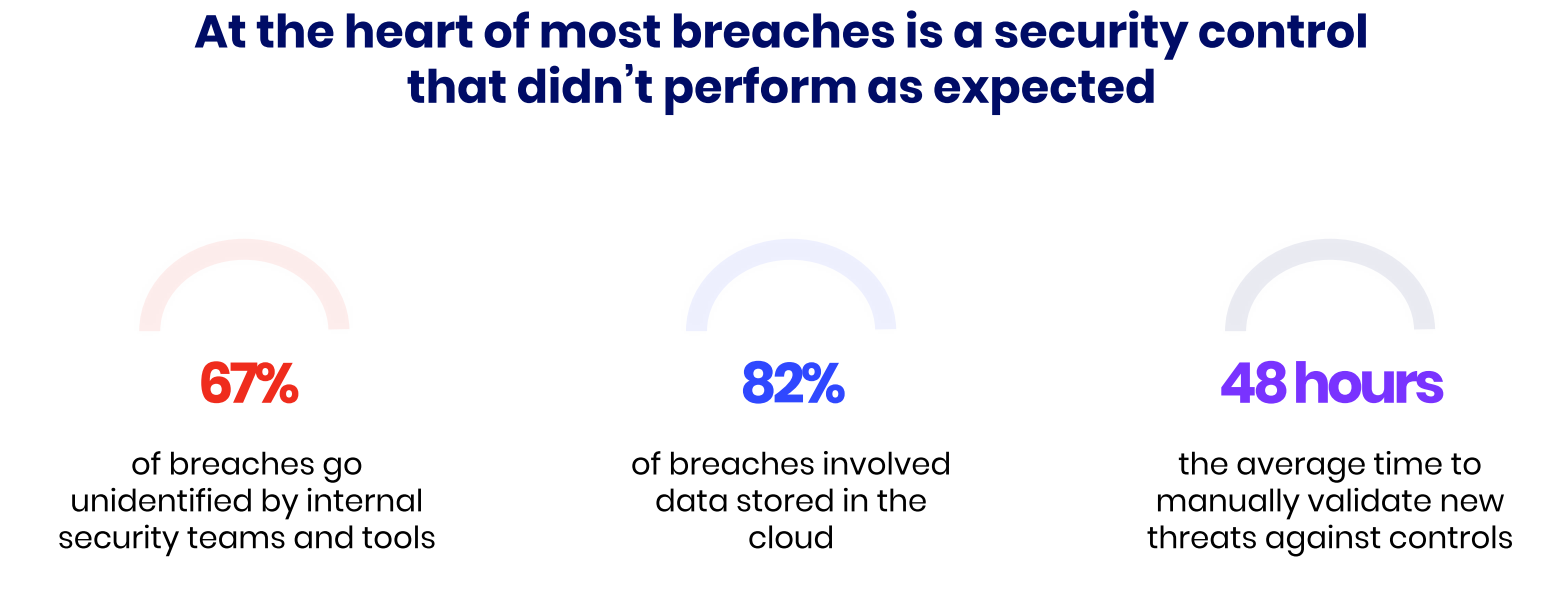
Incident readiness
No system is completely immune to attacks. Being prepared ensures a faster and more effective response when incidents occur. Key preparation steps:
- Tabletop exercises: Simulated attack scenarios help security teams practice their response plans.
- Incident response playbooks: Predefined steps for handling different types of threats.
- Regular training: Employees and IT teams must stay updated on response protocols. A well-prepared team can contain incidents quickly, minimizing damage and downtime.
Proactive Security Techniques and Tools
Proactive security, which is a proactive approach to cybersecurity safety, requires the right techniques and tools to detect, prevent, and mitigate cyber threats before they cause harm. Organizations can enhance their defenses by implementing structured strategies and leveraging advanced security technologies.
Below are some key techniques and tools that support a proactive security approach.
Red teaming and threat hunting
Red teaming and threat hunting help organizations uncover security gaps before attackers can exploit them.
- Red teaming: Ethical hackers simulate real-world attacks to test defenses. Red teams act like adversaries, using various tactics to penetrate security systems and expose weaknesses.
- Threat hunting: Security teams actively search for hidden threats within the network. They analyze unusual activity, identify indicators of compromise, and remove threats before they escalate.
Both techniques improve resilience by identifying vulnerabilities that automated tools might miss. Regular red team exercises and continuous threat hunting ensure stronger defenses.
Automated testing and validation
Automated security testing helps organizations continuously validate their security measures without manual effort. Tools like Cymulate Exposure Validation Platform simulate attacks to assess how well security controls perform.
Continuous testing allows automated tools to scan for vulnerabilities, misconfigurations, and security gaps, ensuring ongoing protection. The results provide immediate feedback, helping teams quickly address issues and reinforce security policies.
By reducing manual effort, automation saves time and ensures that security systems remain effective and resilient.
Security information and event management (SIEM)
SIEM solutions centralize security data, providing real-time insights into potential threats.
- Data collection: SIEM tools aggregate logs from various sources, including firewalls, servers, and endpoints.
- Threat detection: AI-driven analytics help identify suspicious patterns and anomalies.
- Incident response: Security teams receive alerts on potential threats, allowing for rapid investigation and response.
By consolidating security events, SIEM enables organizations to detect and respond to threats more efficiently.
Endpoint detection and response (EDR)
Endpoints—such as laptops, desktops, and mobile devices—are common targets for cyberattacks. EDR tools provide proactive protection by detecting and responding to threats at these entry points.
- Real-time monitoring: EDR solutions track endpoint activity and identify suspicious behavior.
- Threat containment: If an attack is detected, EDR isolates compromised devices to prevent further spread.
- Detailed forensics: Security teams can analyze incidents, understand attack methods, and strengthen defenses.
By using EDR, organizations can stop threats before they compromise the entire network.
4 Key Benefits of Proactive Security
Proactive security prevents threats before they cause damage. It strengthens defenses, reduces risks, and ensures long-term stability.
1. Early threat detection
Detecting threats early stops attacks before they escalate. Continuous monitoring, threat intelligence, and red teaming help identify suspicious activities.
By analyzing network behavior and hunting threats actively, security teams can block cybercriminals before they strike.
2. Reduced incident costs
Preventing attacks costs less than recovering from them. Breaches cause downtime, legal fees, and reputational damage. Automated testing, vulnerability management, and endpoint protection reduce risks.
Fewer incidents mean lower recovery costs and stronger business continuity.
3. Improved security posture
Proactive security strengthens defenses through regular testing and continuous improvement. Best practices like zero-trust architecture and security validation create a resilient environment. Stronger security makes it harder for attackers to succeed.
4. Regulatory compliance
Many industries require strict cybersecurity compliance. Proactive security ensures policies, controls, and monitoring align with regulations.
Risk assessments and audits prevent violations, protect sensitive data, and build trust with customers.
Challenges and Considerations
Proactive security has challenges. Organizations must allocate resources wisely, maintain continuous efforts, and balance proactive and reactive strategies.
Resource allocation
Proactive security requires investment in technology and skilled personnel. Organizations need tools like threat intelligence platforms and automated testing solutions. Cybersecurity professionals must analyze data and manage security operations.
Hiring and retaining talent is difficult, so businesses should prioritize spending and consider automation.
Continuous effort required
Proactive security is ongoing. Regular proactive security monitoring, vulnerability assessments, and security updates are essential. Teams must stay informed about new threats, apply patches quickly, and refine security policies.
Frequent training and simulations keep employees prepared. Without consistent effort, defenses weaken over time.
Balancing proactive and reactive measures
Proactive security is crucial, but reactive measures are also necessary. Even the best-prepared organizations face incidents. An incident response plan ensures quick containment and recovery.
Combining threat hunting and red teaming with forensic analysis and resolution strengthens overall security. A balanced approach prevents most threats and responds effectively to breaches.
How Cymulate Supports Proactive Security
The Cymulate Exposure Validation Platform enhances proactive security through continuous testing and validation. It provides actionable insights and supports various environments, including hybrid, on-premises, and cloud infrastructures. The platform enables organizations to assess and strengthen their security measures proactively. Key features include:
Breach and Attack Simulation (BAS)
Cymulate uses breach and attack simulation technology to create real-world attack scenarios that are executed in a production-safe mode to test and validate your security controls against the latest emergent threats and threat actors.
The attack scenario workbench provides a quick and easy way to create fully automated assessments from a rich library of attack scenarios. Security teams can use the workbench to compose attack simulations by selecting from the list of security controls, threats, platforms, and operating systems that matter to them the most.
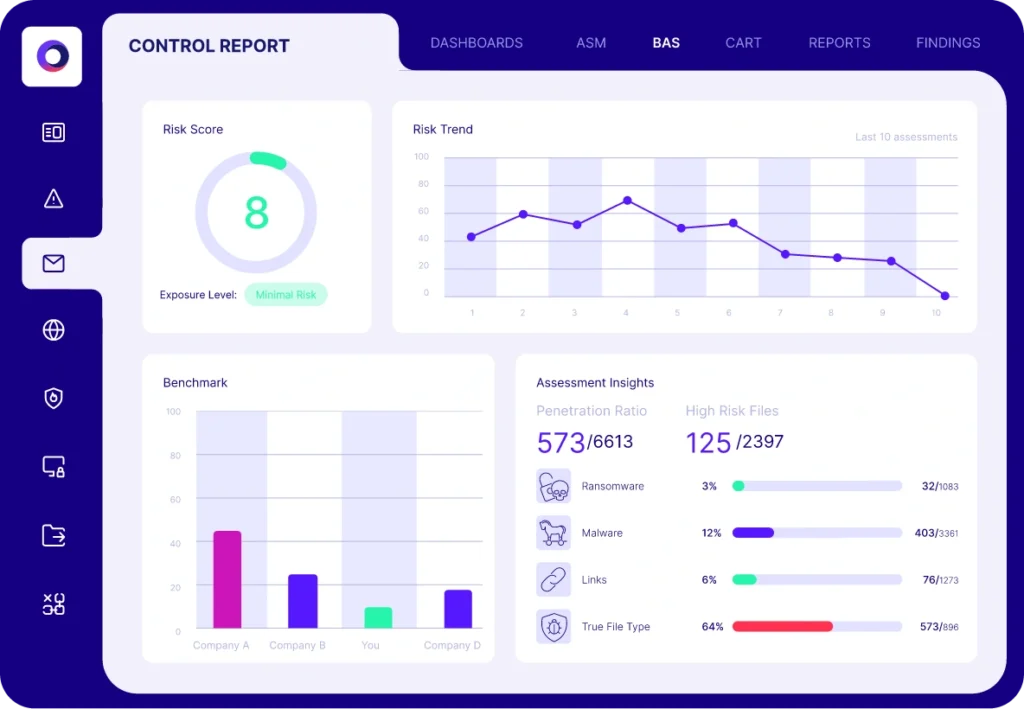
Continuous Automated Red Teaming (CART)
Cymulate Continuous Automated Red Teaming (CART) provides the automation and scale for ongoing security validation with advanced testing for active campaigns and custom threats that target users, systems, and networks.
The implementation is easy, and the assessments can test any technique at any stage of the attack kill chain independently or as part of complex attack chains. Cymulate CART simulates attacks that propagate within the network in search of critical information or assets.
The solution is cloud-based and easily deploys with minimal installation and maintenance. Installing one lightweight agent per environment facilitates seamless communication between customer devices and the Cymulate platform, ensuring timely updates and efficient transfer of operational data.
Key Takeaways
Proactive security is essential for organizations aiming to reduce risk and stay ahead of evolving cyber threats. By anticipating and addressing vulnerabilities before they can be exploited, businesses can significantly lower the likelihood of successful attacks.
Implementing proactive security measures safeguards critical assets and enhances an organization's overall security posture. This approach fosters resilience and ensures compliance with industry regulations and standards.
Adopting proactive security practices is a strategic move toward building a robust cybersecurity framework. Organizations are encouraged to integrate these measures into their operations to effectively mitigate risks and protect their digital environment.

