Risk-Based Vulnerability Management (RBVM)
Risk-based vulnerability management (RBVM) is a modern approach to handling security risks. Instead of treating all vulnerabilities equally, it prioritizes them based on the actual risk they pose to an organization. With RBVM, risk is determined by factors like exploitability, business impact, and threat intelligence.
Risk-Based Vulnerability Management vs. Traditional Vulnerability Management
Traditional vulnerability management (VM) aims to identify and patch every vulnerability, often leading to alert fatigue. Security teams struggle to keep up, and critical threats may go unnoticed.
RBVM takes a smarter approach, focusing on:
- Exploitability – Are attackers actively using this vulnerability?
- Asset criticality – Does it affect a key system?
- Threat intelligence – Is there a known attack method?
By prioritizing real-world risk, RBVM improves efficiency, reduces wasted effort, and strengthens defenses.
| Feature | Traditional VM | Risk-based VM |
| Approach | Patch all vulnerabilities | Prioritize based on risk |
| Decision factor | CVSS severity score | Exploitability, impact, and threats |
| Efficiency | Low—too many alerts | High—focus on real risks |
| Resource allocation | Wastes time on low-risk issues | Uses resources where needed most |
| Protection level | May leave critical gaps | Stronger, risk-driven security |
The Challenges with Traditional Vulnerability Management
Traditional vulnerability management struggles to keep up with today’s cybersecurity challenges. It often creates more work than security teams can handle, leading to inefficiency and missed threats. Data from security detections and alerts do not facilitate decision-making, as it is usually too late to prevent significant damage once an alert is triggered.Organizations that lack data-driven insights may waste resources on low-priority risks while leaving critical vulnerabilities unaddressed. Some of the most common struggles of a traditional vulnerability management program includes:
1. Volume overload
Security teams face thousands of vulnerabilities across their networks. Patching them all is impossible due to limited time and resources. This leads to:
- Alert fatigue – Too many vulnerabilities, not enough prioritization.
- Missed critical threats – Important risks get buried under low-impact issues.
- Inefficient patching – Teams waste time on vulnerabilities that pose little to no risk.
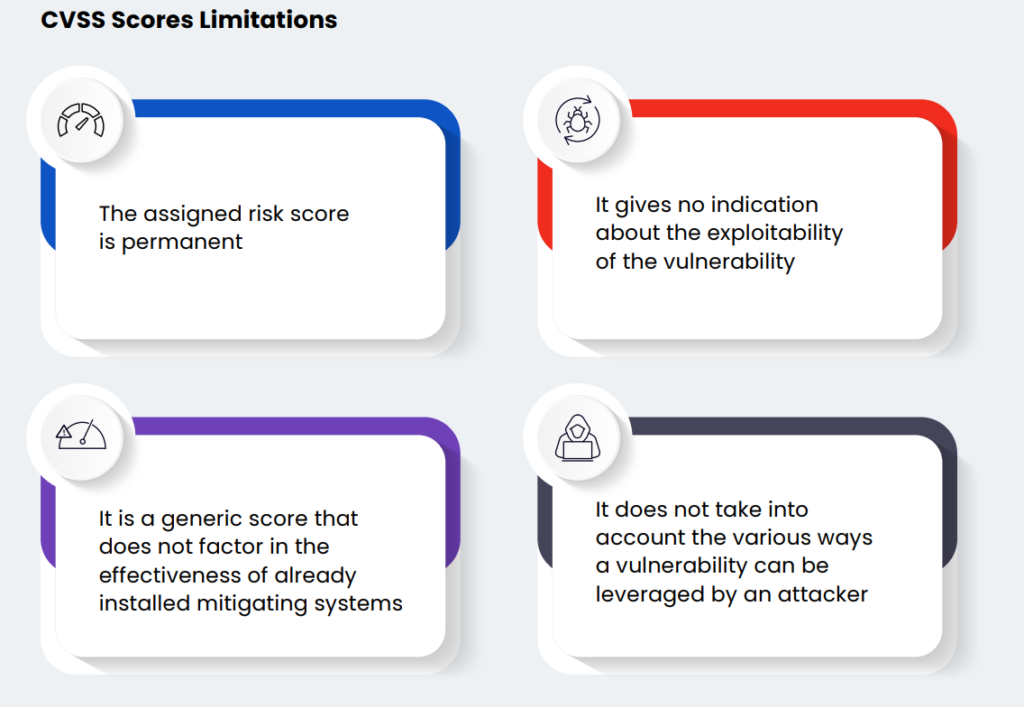
2. Common Vulnerability Scoring System (CVSS) score limitations
CVSS is useful but flawed. It ranks vulnerabilities based on severity, not real-world risk.
A high severity of common vulnerabilities and exposures (CVEs) isn’t always dangerous—some are hard to exploit or irrelevant in certain environments. Meanwhile, lower-severity vulnerabilities can pose major threats, especially if attackers actively exploit them.
CVSS limitations are that the scores are static and lack context, ignoring whether a vulnerability is being used in real attacks. Security teams need a smarter approach that prioritizes risk, not just scores.
3. Lack of threat context
Traditional VM doesn’t account for how attackers operate or which systems matter most. This leads to:
- Blind spots – Some vulnerabilities pose higher risks due to their location in critical systems.
- Ineffective defense – Fixing vulnerabilities without knowing how attackers use them leaves gaps.
- Wasted resources – Effort goes into patching issues that don’t impact security.
Without real-world threat intelligence, traditional VM falls short. Organizations need a smarter approach—one that prioritizes risk and focuses on what truly matters.
4. Lack of business context
As cyber risks become business risks, data-driven exposure insights are vital to integrate risk in the operational decisions-making process. To assess the risk impact of business planned actions, executives need to communicate effectively with security teams. Understanding security strategy and translating it into meaningful risk metrics can be challenging for non-technical audiences.
Why a Risk-Based Vulnerability Management Program is Essential in a Modern Cybersecurity Strategy
Cyber threats are evolving fast, and traditional vulnerability management can’t keep up. Organizations need a smarter approach—RBVM. It helps security teams focus on real threats, not just high-severity scores.
1. Prioritization of exploitable vulnerabilities
RBVM ensures security teams focus on exploitable threats by considering:
- Active exploitation – Are attackers currently using this vulnerability?
- Ease of exploitation – How difficult is it for a hacker to take advantage of it?
- Impact on systems – Would exploitation cause serious damage?
2. Integration with threat intelligence
Attackers constantly evolve, so a static approach to vulnerabilities fails.
RBVM integrates real-time threat intelligence to keep organizations ahead. It:
- Enhances decision-making by providing better risk insights—teams prioritize vulnerabilities based on exploitability and business impact, not just severity scores.
- Tracks emerging attack trends, helping security teams respond faster.
- Identifies vulnerabilities linked to active threats, ensuring the most dangerous issues get fixed first.
3. Better resource allocation
Security teams have limited time and resources. RBVM helps them work smarter by focusing on real threats. It prioritizes high-risk vulnerabilities in critical systems, ensuring the most dangerous issues get fixed first. It eliminates wasted effort on low-risk or non-exploitable vulnerabilities.
4. Improved security posture
By addressing the most dangerous vulnerabilities first, RBVM strengthens overall security. It helps organizations:
- Reduce attack surfaces before hackers can exploit them.
- Minimize business disruption by securing critical systems.
- Improve compliance with security frameworks and regulations.

Key Components of an Effective Risk-Based Vulnerability Management Program
A robust Risk-Based Vulnerability Management (RBVM) program goes beyond traditional vulnerability scanning and patching. It prioritizes vulnerabilities based on real-world risks by integrating the following components:
1. Asset Criticality and Business Context
Not all assets carry the same level of risk. RBVM prioritizes vulnerabilities by assessing:
- Business impact – How essential is the system to operations?
- Data sensitivity – Does it store or process confidential information?
- Exposure level – Is it accessible from the internet or restricted to internal use?
By focusing on high-value assets, organizations can mitigate the most significant risks first.
2. Threat Intelligence and Exploitability
Understanding how attackers operate is crucial. RBVM integrates threat intelligence to determine:
- Are attackers actively exploiting this vulnerability?
- Which adversary tactics, techniques, and procedures (TTPs) are associated with it?
- Is there a publicly available exploit or proof-of-concept?
By prioritizing vulnerabilities based on real-world threats, organizations can stay ahead of attackers.
3. Security Control Validation
Patching alone isn't enough—organizations must test their security controls to ensure they can detect and prevent exploitation. Key security controls to validate include:
- Web Application Firewall (WAF) – Can it block exploit attempts?
- Endpoint Detection & Response (EDR) – Can it detect and stop attacks?
- Security Information & Event Management (SIEM) – Is it generating useful alerts?
Validating security controls ensures that vulnerabilities cannot be easily exploited, even if patches are delayed.
4. Automated Risk Scoring
AI and machine learning enhance RBVM by dynamically ranking vulnerabilities based on:
- Real-time exploitability
- Asset value and business impact
- Security gaps and defense readiness
This approach enables organizations to focus on the most pressing threats.
5. Continuous Validation and Exposure Management
Instead of relying on periodic scans, RBVM continuously monitors for:
- Emerging vulnerabilities and threats
- Changes in asset exposure
- Weaknesses in security defenses
This ongoing validation ensures that security measures remain effective against evolving threats.
Challenges in Implementing Risk-Based Vulnerability Management
Implementing RBVM comes with obstacles. Overcoming them makes security stronger and more efficient.
- Lack of visibility – Organizations struggle to track all assets and vulnerabilities, especially in cloud and hybrid environments. Without full visibility, critical risks go unnoticed.
- Data overload – Security teams receive too much data from scanners, threat intelligence, and security tools. Sorting through it all is overwhelming. Without automation, important threats may be missed.
- Balancing security and operations – Patching high-risk vulnerabilities can disrupt business. Teams must fix threats without causing downtime or slowing productivity.
- Measuring effectiveness – Tracking RBVM success is tough. Organizations need clear KPIs that go beyond patch counts, showing real risk reduction and security improvements.
How Cymulate Helps with Risk-Based Vulnerability Management
The Cymulate platform provides data-driven insights based on simulated attacks. These insights proactively highlight high-risk security deficiencies and quantify risk. This provides organizations the ability to reduce risk exposure by prioritizing vulnerabilities and finding misconfigurations that could be exploited by attackers.
Additionally, executive reporting translates technical findings so business leaders can track cybersecurity performance and risk management. This way, executives can make informed decisions and ensure that their strategy remains relevant and effective over time.
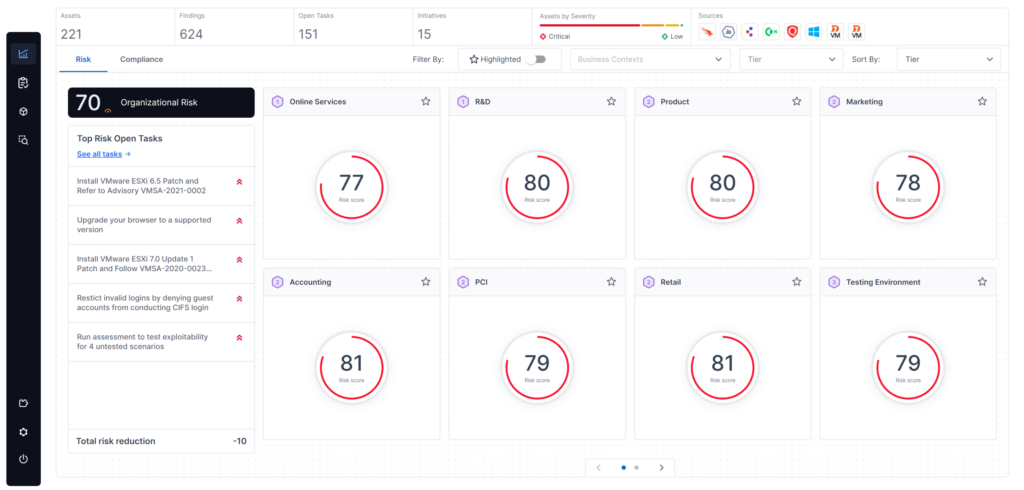
- Attack-based vulnerability prioritization: The Cymulate Platform focuses on vulnerabilities that adversaries are actively exploiting. By simulating real-world attack scenarios, it identifies which vulnerabilities are most likely to be targeted, allowing organizations to prioritize remediation efforts where they matter most.
- Continuous security validation: Through Breach and Attack Simulation (BAS), Cymulate continuously tests the effectiveness of security controls against evolving threats. This proactive approach ensures defenses remain effective and adapt to new attack techniques, providing real-time insights into security gaps.
- Exposure management and real-time risk assessment: Cymulate Exposure Analytics gives organizations a clear view of security risks by:
- Aggregating data from risk assessment vulnerability scanners and security controls.
- Providing real-time visibility into exploitable vulnerabilities across cloud, hybrid, and on-prem environments.
- Enabling informed decision-making to prioritize and effectively implement risk mitigation strategies.
- Actionable remediation recommendations: The platform delivers clear, step-by-step guidance to address high-risk vulnerabilities. By correlating vulnerability findings with business context and security control effectiveness, Cymulate ensures that remediation efforts are both efficient and aligned with organizational priorities.
Cymulate's integrated approach to RBVM empowers organizations to proactively manage vulnerabilities by focusing on real threats, validating security measures continuously, understanding their exposure comprehensively, and implementing targeted remediation strategies.
Key Takeaways
A risk-based approach to security is essential for effective vulnerability management. Traditional vulnerability management methods often create too much noise, overwhelming security teams with endless alerts.
Rrisk-based vulnerability mangement solves this by focusing on the threats that matter most. It prioritizes exploitable vulnerabilities, aligns security with business goals, and ensures smarter decision-making.
RBVM reduces risk exposure by addressing real-world threats before attackers can exploit them. It improves security resilience by integrating threat intelligence, validating security controls, and continuously monitoring vulnerabilities.
Instead of reacting to every issue, organizations can proactively defend their critical assets.


