Cloud Security Assessment Tools: How to Find the Right Fit
Too many cloud tools, not enough clarity. Sound familiar?
Between CSPM, CNAPP, CIEM, BAS and a dozen more acronyms, security teams end up with overlap, blind spots and mounting costs. However, all this does not mean cloud risk goes away.
It’s important to understand cloud security assessment tools and whether they can reduce your risk (and not just add dashboards).
In this guide, you’ll get plain-language definitions, a breakdown of how cloud security assessment tools work, the different categories to consider, a practical selection checklist and an at-a-glance FAQ.
Key highlights:
- Cloud security assessment is the process of identifying misconfigurations, vulnerabilities and risky permissions across multi-cloud environments, with fixes mapped to frameworks like CIS and NIST.
- Cloud security assessment tools include CSPM, CIEM, CWPP, CNAPP, SaaS posture, provider-native suites and advisory services, chosen based on coverage, IAM depth, validation and compliance needs.
- The Cymulate Exposure Management Platform goes further by continuously validating defenses, mapping attack paths and enabling evidence-based remediation aligned to CTEM.
What is cloud security assessment?
Cloud security assessment is a systematic evaluation of your cloud accounts, services, identities, data paths and controls to identify misconfigurations, exploitable vulnerabilities and policy gaps and to prioritize fixes by business risk. It spans IaaS, PaaS and often SaaS. It also accounts for shared responsibility models across AWS, Azure and Google Cloud.
Cloud security assessment is different from simple configuration scanning. It correlates findings across identity (IAM/CIEM), network exposure, encryption and key management, data access and workload hardening. A cloud security assessment also maps issues to frameworks like CIS Benchmarks and NIST to produce clear remediation paths and track posture improvement over time.
For a primer on program-level risk methods, see more on cloud risk assessment.
Benefits of automated cloud security validation
Unlike manual spot checks or static config scans, automated cloud security validation runs continuously, integrates with your CI/CD and ticketing stack and produces evidence instead of assumptions. Here are the key benefits of automated cloud security validation:
- Reduce detection time: Automation runs targeted tests in minutes, revealing exploitable paths (not just theoretical misconfigurations). That accelerates mean time to resolution (MTTR) and reduces “analysis paralysis.” IBM’s Cost of Data Breach report notes breach identification/containment mean time is 241 days on average; shortening this window directly cuts costs.
- Minimize manual effort: Pre-built test suites aligned to ATT&CK map to cloud-native services (IAM, KMS, S3/Blob/GCS, serverless, containers) so engineers spend time fixing, not crafting tests.
- Maintain continuous assurance of cloud security: Nightly/weekly runs become a guardrail for drift, IaC changes and new services. This is essential in a multi-cloud environment, where 89% of enterprises operate. (Flexera)
- Cut false positives and alert fatigue: Validated findings slash false positives. Instead of hundreds of “might be risky” alerts, teams get a short list of confirmed exploitable paths with step-by-step remediation.
- Support CTEM programs: Validation underpins Continuous threat exposure management (CTEM), closing the loop from discovery → validation → prioritized remediation → verification.
- Improve incident readiness: Running “controlled rehearsals” exposes detection gaps in your cloud security monitoring solutions before attackers do.
How does a cloud security assessment tool work?
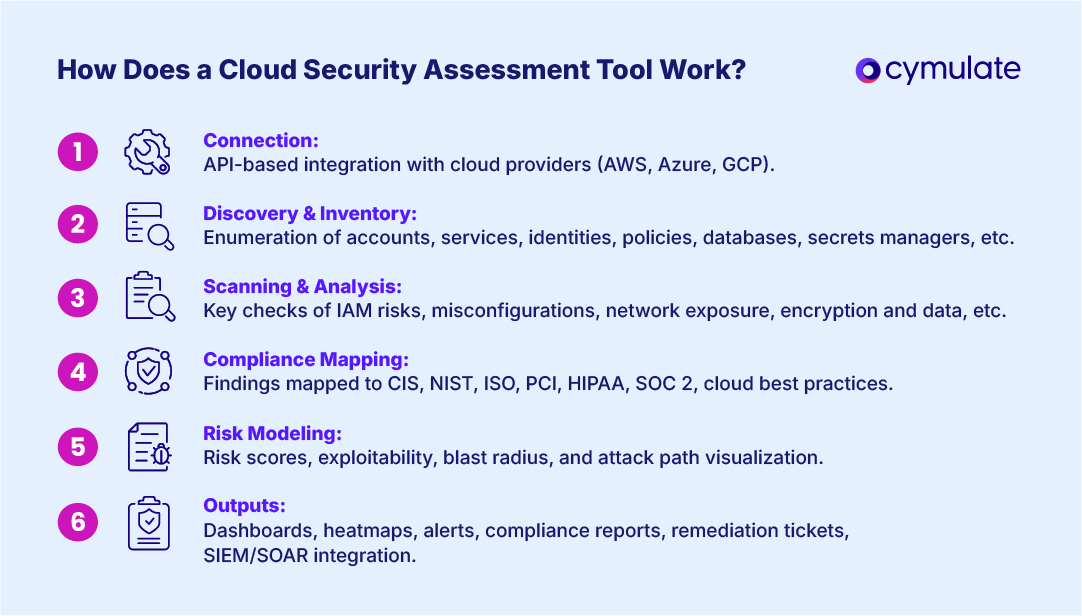
From connection to reporting, here’s the common flow of a cloud security assessment:
Step 1: API-based connections. Tools use read-only API integration (and sometimes lightweight agents) to connect to AWS organizations, Azure subscriptions and GCP projects/folders.
Step 2: Discovery and inventory. Enumerate accounts, services, identities, roles, policies, storage, databases, network egress, serverless, containers and secrets managers.
Step 3: Vulnerability scanning and analysis. These tools scan for areas that could pose cyber risk for an organization, including these areas:
- Misconfigurations: Public buckets, wide-open security groups, unmanaged keys, weak TLS, overly permissive roles.
- IAM risk: Toxic permission combos, dormant high-privilege roles, cross-account trust abuse (CIEM).
- Network exposure: Routable paths from the internet to crown-jewel assets; egress risks.
- Encryption and data: Unencrypted storage, exposed secrets, data residency violations.
- Workload posture: Container/image vulnerabilities, runtime drifts, serverless permissions.
Step 4: Compliance mapping. Map findings to CIS Benchmarks, NIST 800-53/CSF, ISO 27001, PCI DSS, HIPAA, SOC 2 and cloud provider best practices.
Step 5: Risk modeling. Adopt a risk-based vulnerability management approach and assign risk scores by exploitability and blast radius; visualize attack paths across identities, networks and data stores.
Step 6: Outputs. Dynamic dashboards, risk heatmaps, policy drift alerts, compliance reports and ticket-ready remediation steps. Many integrate with SIEM/SOAR to enrich detections from your cloud security monitoring solutions.
Types of cloud security assessment tools
If you’re considering a tool for cloud security assessments, there is no shortage of options. Here are options you can consider and what they might be able to provide your organization:
- CSPM (Cloud Security Posture Management): Continuous config/compliance monitoring for IaaS/PaaS services.
- CIEM (Cloud Infrastructure Entitlement Management): Deep IAM/permissions analysis to reduce over-privilege and lateral-movement risk.
- CWPP (Cloud Workload Protection Platform): Image scanning, runtime protection for VMs/containers/serverless.
- CNAPP (Cloud-Native Application Protection Platform): Unified platform combining CSPM + CIEM + CWPP + IaC scanning and more.
- CASB / SSPM (SaaS posture): Assess and enforce security for SaaS apps and their data sharing.
- Cloud provider–native suites: AWS Security Hub, Microsoft Defender for Cloud and Google Security Command Center. These are foundation controls that third-party tools often enrich.
- Cloud assessment and advisory services: Outside experts to run a cloud security review or program-level cloud security risk assessment, which is useful for baselines.
| Cloud security assessment category | Primary focus | Typical outcomes | Common integrations |
| CSPM | Config and compliance | Misconfig fix lists, compliance reports | Ticketing, SIEM, IaC |
| CIEM | Identity and permissions | Least-privilege plans, toxic combo reduction | IAM, SSO, PAM |
| CWPP | Workload/runtime | Vulnerability and runtime hardening | Container registries, EDR/XDR |
| CNAPP | Unified cloud app protection | Cross-layer risk views, dev-to-prod guardrails | CI/CD, IaC, SIEM |
| Provider-native | Baseline guardrails | Quick wins, account hygiene | Native logging/monitoring |
| Advisory services | Security strategy and audits | Roadmaps, program design | Exec reporting, GRC tools |
How to conduct a cloud security assessment
The key to conducting these assessments is consistency; keep it lean and repeatable. Here is what you need to know:
- Define scope: Accounts/subscriptions, regions, data classifications and critical apps (include cloud application security assessment needs).
- Connect via API: Read-only access for discovery; decide where agents add value.
- Run baseline scans: Misconfigs, IAM, network, encryption, secrets, workload posture.
- Map to frameworks: CIS, NIST, ISO, PCI/HIPAA as needed.
- Prioritize by exploitability and blast radius: Not by alert volume.
- Validate cloud security controls: Use safe simulations to prove detections/blocks across key attack paths.
- Remediate and verify: Automate fixes where safe; re-run to confirm.
- Operationalize: Integrate with SIEM/SOAR/ticketing; schedule continuous runs for cloud security automation.
How to choose the right cloud security assessment tool
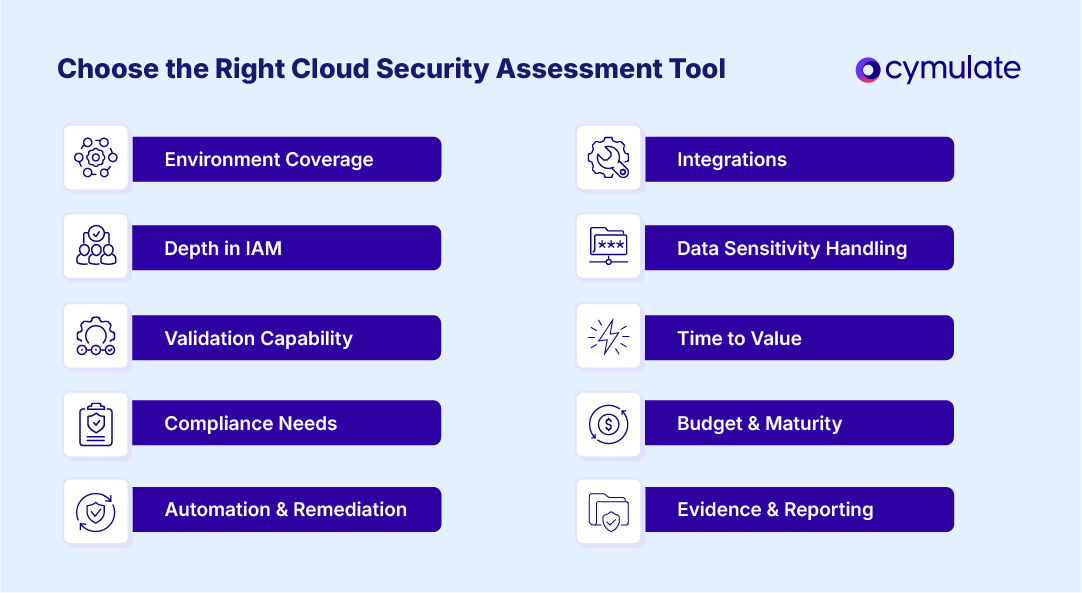
There’s no single winner. The fit for a cloud security assessment tool depends on your stack, team and goals. Use this checklist:
- Environment coverage: Single cloud vs multi/hybrid; support for your PaaS/services and Kubernetes flavor.
- Depth in IAM: Rich experience for CIEM analytics, toxic combo detection, cross-account trust analysis.
- Validation capability: Built-in cloud security validation to prove detections; support for attack path discovery and safe simulations.
- Compliance needs: HIPAA, PCI DSS, ISO 27001, SOC 2; evidence exports for auditors. This is a clear focus for Cloud Security Posture Management (CSPM).
- Automation and remediation: Auto-fixes or guided wizards; drift prevention; robust APIs.
- Integrations: SIEM/SOAR, EDR/XDR, ITSM, CSP-native logs and findings.
- Data sensitivity handling: Evidence redaction, data residency and least-privilege connectors.
- Time to value: Agentless start; quick baselines; clear ROI reporting.
- Budget and maturity: Start with CSPM if you’re early; add validation/CNAPP as you scale.
- Evidence and reporting: Risk scoring, business impact mapping, exec-ready views.
For context on identity-driven risk, the Cloud Security Alliance found most cloud breaches tie back to insecure identities, making CIEM depth and validation especially critical.
Cymulate: Exposure management beyond cloud security assessment
Choosing the right cloud security assessment tools comes down to two truths: multi-cloud complexity is here to stay and posture without validation is table stakes. Prioritize platforms that continuously discover, prioritize and prove your defenses so you can show real, sustained risk reduction.
Cymulate goes beyond posture snapshots. Its Exposure Management Platform includes:
- Cloud security validation solution to continuously tests your defenses with safe, production-friendly simulations
- Attack path discovery solution to expose how identities, misconfigurations and network exposures chain together
You get prioritized, evidence-backed findings as well as guided remediation that you can verify with one click. Because the platform unifies breach and attack simulation (BAS), validation and analytics across cloud, network and endpoint layers, security teams can align with CTEM, reduce alert fatigue and prove risk reduction to leadership.
With Cymulate, you solve the core problems through exposure management with this approach:
- Prove the threat: Cymulate can simulate the latest threats to test and validate how your cyber defenses prevent, detect and respond across your IT environments (cloud, on prem, applications, etc.).
- Improve resilience: Cymulate gives security teams the tools and automation to build threat resilience with control updates for missed threats, custom detection rules and an action plan to optimize prevention and detection.
- Prioritize exposure: Cymulate can prioritize threat exposures by validating exploitability in your environment and stack ranking them based on your proven prevention and detection of exploits, business context and threat intel.
- Collaborate across teams: Cymulate provides the insights and action plans for security operations, red teams and vulnerability management to collaborate and focus on what’s exploitable in each environment. This is continuous threat exposure management (CTEM).
Request a demo to see how Cymulate can help you beyond cloud security validation.
Frequently asked questions
What is the difference between cloud security assessments and traditional penetration tests?
The differences between cloud security assessments and traditional penetration tests come down to scope, frequency and outcomes. Assessments emphasize continuous posture, identity and control validation across cloud services; pen tests focus on point-in-time exploitation within a scoped target.
| Feature | Cloud security assessment | Traditional penetration test |
| Scope | Broad (accounts, services, IAM, data paths, workloads) | Narrow, predefined targets/applications |
| Frequency | Continuous or scheduled (monthly/quarterly) | Point-in-time (annual or ad-hoc) |
| Methods | API discovery, config/IAM analysis, safe simulations/validation | Manual exploitation, custom attack paths |
| Output | Risk scores, compliance mapping, validated controls, remediation tickets | Exploit proof-of-concept, prioritized findings |
| Goal | Reduce exploitable attack paths and prove defenses work | Demonstrate vulnerabilities under test conditions |
| Fit | Ongoing cloud programs and CTEM | Assurance for compliance or targeted systems |
How can I maximize the benefits of my cloud security assessment?
To maximize the benefits of cloud security assessment:
- Scope your critical data and business processes
- Align tool outputs to measurable outcomes (blocked attack paths, reduced mean time to remediate, fewer critical misconfigs)
- Automate evidence capture, push fixes directly to owners via ticketing and rerun validation after every change
- Treat assessments as a continuous guardrail for IaC and DevOps, not an annual event to do occasionally
- Tie KPIs to breach likelihood and impact (for example, reducing public exposure of sensitive storage)
How do I assess cloud security vulnerabilities effectively?
Cloud security vulnerabilities demand a deliberate, step-by-step approach to assess:
- Asset discovery and inventory: Enumerate accounts, services, identities, storage, and internet-exposed endpoints
- Scan smart: Use a cloud security assessment tool to detect misconfigurations, exposed services, weak encryption and IAM risks across AWS/Azure/GCP.
- Prioritize by exploitability and impact: Weigh reachable data paths, privilege escalation potential and blast radius as opposed to not raw alert counts.
- Validate exposures: Use safe, simulate exploitation (exfil from a misconfigured bucket, assume-role abuse) with Cymulate to verify that detections fire and controls block.
- Assign owners and remediate: Route tickets with clear “how-to-fix” steps; enable auto-remediation where low risk.
- Re-check and document: Re-run scans and validation post-fix to confirm closure and update compliance evidence.
- Monitor continuously: Feed validated signals into your cloud security monitoring solutions and SOAR playbooks to prevent regressions.
For threats to watch, review cloud security threats.