Attack Path Analysis (APA) Explained: How to Map, Detect and Prevent Breaches
Attack path analysis (APA) is a cybersecurity technique that helps security teams visualize and mitigate potential attack routes before adversaries can exploit them. Organizations can better understand how attackers navigate through networks to strengthen defenses, prioritize vulnerabilities and reduce overall exposure to threats.
APA is particularly critical in cloud environments, where attack paths are more dynamic due to constantly changing assets, misconfigurations and privilege escalation risks. With threat actors using lateral movement techniques, attack path analysis provides actionable insights to improve security controls and protect sensitive data.
Organizations with APA knowledge gain a more profound understanding of cyber risk management, ensuring they implement network segmentation, proactive threat modeling and zero-trust architectures.
Key highlights:
- Attack path analysis (APA) is a cybersecurity method that maps how attackers could move through an IT environment, highlighting vulnerabilities, misconfigurations and privilege escalation risks.
- Attack path analysis (APA) allows security teams to anticipate, visualize and mitigate attack routes before adversaries exploit them.
- You can automate APA to provide real-time risk assessment, AI-powered threat detection and integration with existing security tools.
- The Cymulate platform supports APA by continuously identifying, simulating and mitigating attack paths, improving security posture, compliance and resilience against breaches.
What is attack path analysis (APA)?
Attack path analysis (APA) is the process of identifying, mapping and analyzing potential attack routes within an IT environment. It helps security professionals anticipate how adversaries could move across systems, highlighting weaknesses before they can be exploited.
For example, attack path analysis can show when an attacker could exploit a vulnerable external server, use exposed credentials to move to an internal application server and then reach a critical database because segmentation controls are missing.
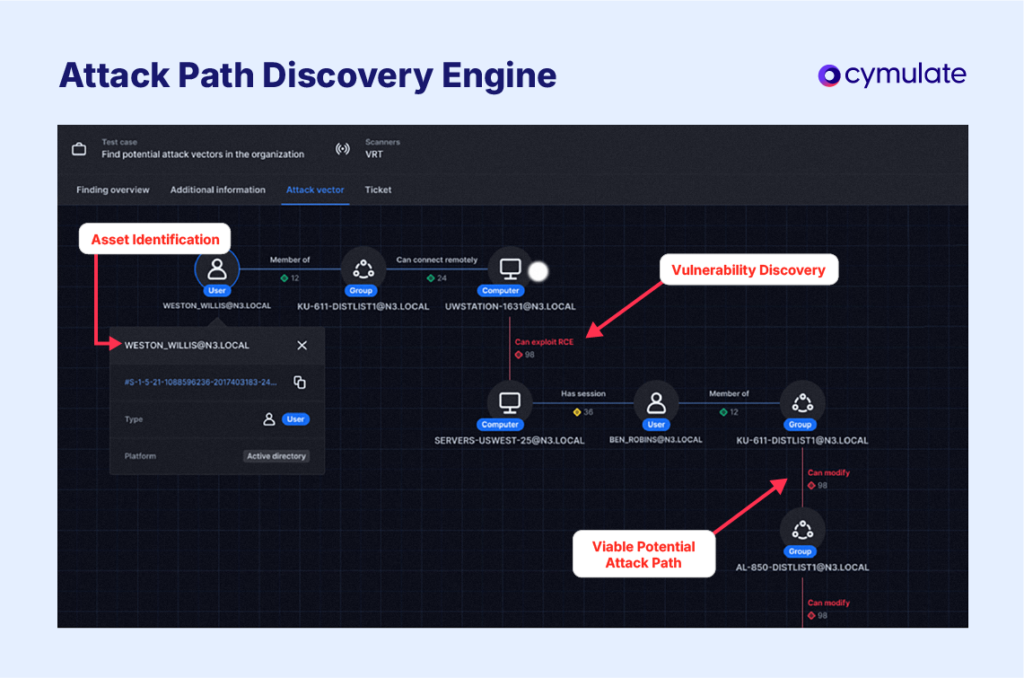
What are the benefits of attack path analysis?
APA enables SOC analysts, threat hunters and risk management teams to take active security measures and improve incident response. Furthermore, APA plays a much-needed role in threat exposure mapping as well. Key benefits of APA are:
- Visualize attack paths: Get a clear picture of how attackers can navigate through the network.
- Prioritize security improvements: Focus on mitigating the most critical risks first.
- Reduce threat exposure: Address security weak points before attackers exploit them.
- Improve incident response: Enable security teams to act quickly and decisively during a breach scenario.
- Validate security: Simulate attack paths to proactively test security controls against the cyber kill chain.
Attack vector vs. attack surface vs. attack path: Key differences
The difference among attack vector, attack surface and attack path is that:
- An attack vector is the method by which an adversary can gain entry.
- The attack surface represents all potential vulnerabilities in a system.
- The attack path outlines the specific routes an intruder might follow once inside.
| Concept | Definition | Example |
| Attack path | The route an attacker takes to move through a system or network. | A hacker exploits an unpatched vulnerability in a web server, then moves laterally to access critical databases. |
| Attack vector | The specific method or technique used to exploit a system. | Phishing emails, malware infections and brute-force attacks. |
| Attack surface | The total number of exploitable points in a system. | Public-facing applications, open ports and misconfigured cloud storage. |
With an increased understanding of these concepts, security teams can easily prioritize remediation efforts, patching high-risk attack paths before a breach occurs.
How attack path analysis works: 5 key steps of the process
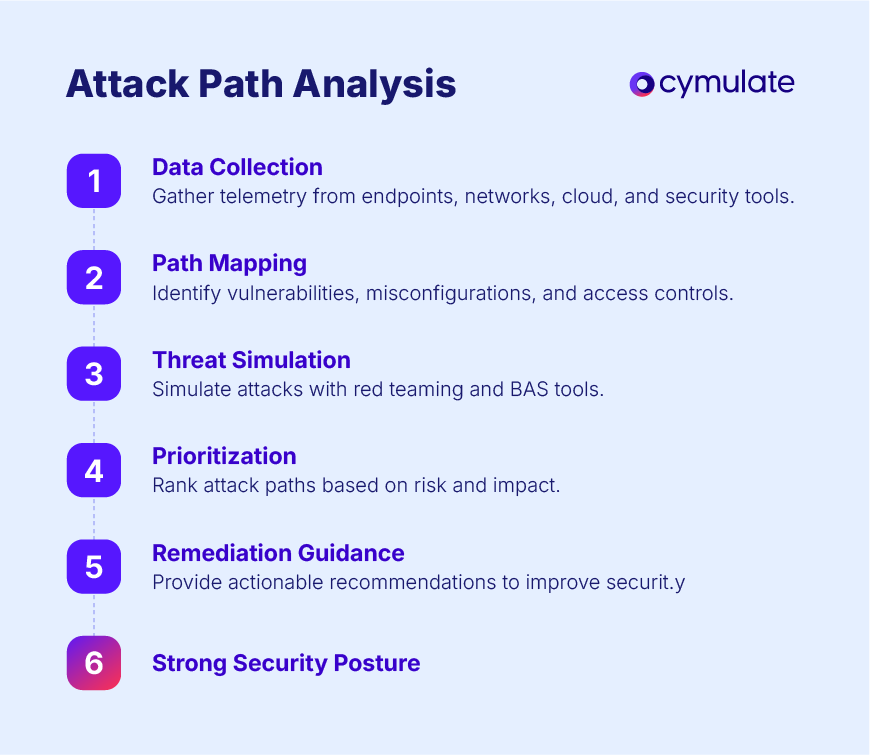
APA follows a structured five-step process to identify, analyze and mitigate security risks:
Step 1: Data collection
The first step in attack path analysis is data collection. Security telemetry is gathered from various sources, including endpoints, networks, cloud environments and security tools.
This step ensures that organizations have a comprehensive view of their IT infrastructure, identifying weaknesses and vulnerabilities that attackers could exploit.
2. Attack path mapping
Once data is collected, potential attack paths mapping is completed based on detected vulnerabilities, misconfigurations and access controls.
Security teams use attack graph visualization to analyze how adversaries could traverse the system. Attack path mapping helps organizations pinpoint high-risk entry points and lateral movement routes.
3. Threat simulation
In this phase, attack scenarios are simulated to assess real-world risks. Red teaming and breach and attack simulation (BAS) tools test security controls by mimicking adversarial behaviors.
This allows organizations to identify security validation gaps and understand which attack vectors could be used in an actual breach.
4. Vulnerability prioritization
Not all attack paths present the same level of risk. Security teams prioritize vulnerabilities and critical attack paths based on their potential impact.
This step involves assessing the exploitability of vulnerabilities, the value of targeted assets and the likelihood of a successful attack. By ranking risks, organizations can focus on remediating the most pressing threats first.
5. Remediation guidance
Based on the findings, actionable recommendations are provided to harden security controls, patch vulnerabilities and improve network defenses. This step often includes strengthening identity and access management (IAM), enforcing network segmentation and improving endpoint security policies.
5 cloud security challenges in attack path analysis
Cloud security introduces more challenges due to its distributed nature and changing attack paths. APA plays a considerable role in securing cloud environments by identifying misconfigurations, weak IAM policies and hybrid attack paths. The following challenges occur during attack path analysis for cloud environments:
1. Dynamic attack paths
The flexibility of cloud environments, including autoscaling and ephemeral workloads, makes it challenging to maintain a static security posture.
Attackers exploit these rapid changes to find weaknesses in configurations, permissions and exposed endpoints.
2. IAM-Based attack paths
Weak identity and access management (IAM) configurations can allow attackers to escalate privileges and gain unauthorized access.
Misconfigured permissions, excessive privileges and weak authentication mechanisms create entry points that attackers can exploit to move laterally and compromise cloud workloads.
3. Data exfiltration risks
Improperly configured cloud storage services, such as publicly accessible S3 buckets or misconfigured blob storage, expose sensitive data to cybercriminals.
Attackers use multiple data exfiltration techniques, looking for open cloud storage locations to extract critical business data, leading to compliance violations and data breaches.
4. Multi-cloud complexity
Organizations using multiple cloud providers, such as AWS, Azure and Google Cloud, must address cross-cloud attack paths.
The complexity of managing security policies across different environments creates blind spots, making it easier for attackers to exploit gaps between disparate cloud security configurations.
5. API security threats
APIs are widely used for cloud service automation and integration, but poor API security practices often expose organizations to cyber threats. Attackers can exploit insecure APIs to bypass authentication mechanisms, extract data or manipulate cloud workloads, making API security a critical component of attack path analysis.
APA helps with real-time cloud security validation for organizations to continuously monitor and remediate risks. With attack path mapping tools, security teams gain better visibility into potential risks within hybrid and multi-cloud architectures.
Use cases of attack path analysis: When can you use the method
Organizations can leverage APA in various security scenarios, including:
- Red teaming exercises: Simulate real-world attack scenarios to test security defenses.
- Post-breach forensic analysis: Identify how attackers infiltrated and moved laterally within networks.
- Security control validation: Ensure network segmentation and security controls are effective against advanced threats.
- Regulatory compliance: Meet cyber risk assessment requirements for frameworks like DORA, NIST and ISO 27001.
- Cloud security assessment and audits: Assess whether cloud environments are secure from misconfigurations and lateral movement threats.
Why is automating attack path detection important
As organizations grow, so does their attack surface. Manually tracking attack paths across thousands of endpoints, cloud assets and networks is impossible. With automation, security teams gain confidence in their ability to detect and remediate threats before they escalate into breaches. Automating APA gives you easier:
- Scalability: Automated APA scales effortlessly, mapping millions of attack paths in large environments and identifying complex multi-stage attack chains. This scalability is crucial for enterprises managing hybrid cloud architectures and multi-cloud security strategies.
- Compliance: Automated APA helps security teams to mitigate risks before attackers can exploit them. With real-time attack path insights, automation helps organizations validate security controls, enforce compliance with cybersecurity frameworks (such as NIST, ISO 27001 and DORA) and improve cloud security posture.
How to automate attack path analysis
With large, complex environments, manual attack path mapping becomes inefficient and difficult to manage. Attackers continuously adapt their techniques, making real-time monitoring a necessity. Automation significantly enhances attack path analysis (APA) by streamlining detection, monitoring and response efforts.
Real-time risk assessments
One of the biggest advantages of automating attack path analysis is continuous risk assessment. Traditional risk assessments are periodic and may leave gaps where new vulnerabilities emerge undetected.
Automated APA provides real-time visibility into evolving threats by continuously analyzing attack paths, identifying misconfigurations and assessing security weaknesses.
AI-powered threat detection
Sophisticated cyber threats often use hidden attack paths that traditional security tools may not detect. AI-driven APA solutions use machine learning to recognize patterns of lateral movement, privilege escalation and anomaly-based indicators of compromise. By analyzing large datasets and recognizing attack trends, AI-powered APA enhances proactive threat detection and reduces response times.
Integration with security tools
Automated APA seamlessly integrates with Security Information and Event Management (SIEM), Extended Detection and Response (XDR) and exposure management platforms.
This integration ensures that APA findings are correlated with broader security insights, allowing teams to prioritize remediation efforts based on actual attack feasibility rather than just theoretical vulnerabilities.
Linking APA insights with existing security workflows could help organizations can reduce alert fatigue and improve efficiency.
How Cymulate helps with attack path analysis
The Cymulate security validation platform enables organizations to identify, visualize and mitigate attack paths before they are exploited. With comprehensive exposure management and attack simulation, Cymulate provides:
- Proactive attack path discovery and mapping: Identify vulnerabilities before they become threats.
- Lateral movement testing: Ensure security controls block unauthorized movement.
- Security posture assessments: Meet compliance and regulatory requirements.
- Actionable threat intelligence: Improve threat resilience with detailed remediation guidance for security teams.
- Integration with cybersecurity ecosystems: Work alongside leading threat exposure management and BAS (breach and attack simulation) platforms.
Request a demo to see how Cymulate's continuous security validation contributes to the development of resilient cybersecurity programs.
Frequently asked questions
An attack graph is a visual or logical representation of all possible paths an attacker could take to move through an IT environment. It’s the key output of attack path modeling, mapping vulnerabilities, misconfigurations and exposures to critical assets.
You can group attack path analysis into six categories, depending on the way attackers move through an environment:
- Privilege escalation paths: Track how attackers gain higher access by exploiting weak passwords, over-permissioned accounts or stolen credentials.
- Lateral movement paths: Show how attackers navigate between systems after initial access, using misconfigured network settings, weak policies or exploitable protocols.
- Vulnerability-based paths: Identify how unpatched software or system flaws can be leveraged to gain access, execute malicious code or move laterally.
- Network and configuration paths: Highlight risks from open ports, exposed admin interfaces or weak trust relationships that can provide footholds for attackers.
- Domain compromise paths: Reveal techniques attackers use to take control of directory services or authentication mechanisms, allowing persistent access across the network.
- Cloud and hybrid paths: Map potential attacks across cloud environments, misconfigured access policies or hybrid AD setups, showing how attackers could move between cloud and on-prem systems.
Attack path management (APM) is the ongoing process of monitoring, assessing and remediating potential attack paths in your environment. It extends attack path analysis by continuously tracking exposures, validating security controls and ensuring that fixes actually break exploit chains before attackers can leverage them.
Attack path analysis (APA) and the MITRE ATT&CK framework are closely related because APA can use ATT&CK to map attacker behavior along identified paths. Together, they give security teams a clearer view of both the path and the methods an attacker might use. Here’s how:
- APA identifies how an attacker could move through an environment
- ATT&CK provides a structured library of tactics, techniques and procedures (TTPs) to classify and contextualize each step.
Threat modeling is a proactive exercise that identifies potential threats and designs defenses at a conceptual level, often during the design phase of a system. Attack path analysis, by contrast, examines the actual environment to map real exploitable paths, showing how an attacker could move through existing systems and misconfigurations.
Attack path analysis should be performed continuously or at least regularly, such as after significant infrastructure changes, new deployments or critical vulnerability disclosures. Continuous testing identifies new exposures or misconfigurations quickly before they can be exploited.
Vulnerability scans and assessments focus on identifying individual vulnerabilities and attack path analysis looks at how those vulnerabilities could be combined to reach critical assets:
- Vulnerability scan: Automated check to identify known vulnerabilities in systems or applications.
- Vulnerability assessment: Deeper review that validates scan results, prioritizes risks and may recommend remediation.
Attack path analysis: Further mapping of how multiple vulnerabilities and misconfigurations can be chained to reach high-value assets.


