In the Attacker’s Sights, Healthcare Must Ready their Defenses & Recovery Processes
As threat actors continue to target the healthcare providers, cyber leaders in the industry face heightened urgency to harden their defenses ahead of the next attack while preparing their response and recovery capabilities for the potentially inevitable breach.
Healthcare data has long been a valuable target because of its very personal nature that demands the highest level of sensitivity and the fact that it includes minors who have a more limited digital footprint. Recent research indicates that medical records sell for an average of $60 apiece on the dark web as compared to social security numbers at $15 and credit card numbers at $3.
Beyond the value of the data, the very critical nature of healthcare services makes the industry a prime target for ransomware attacks. While the ultimate nightmare scenario would involve hospital operational technologies (OT and IoT), and other systems that regulate and manage medical devices for the delivery of life supporting services, the recent attacks against Change Healthcare and Ascension highlight the impact of disrupting both healthcare services and business operations.
Double Extortion
By cutting off access to electronic health records, ordering systems, and claims/payment processing, these attacks demonstrate the damage of not having robust business continuity plans (or paying an immediate ransom). Of course, paying that ransom only entices the attacker to strike again. After restoring operations, the attackers will then demand another ransom for the data exfiltrated in the attack.
With the healthcare industry in the attacker’s sights, security leaders can take practical steps to validate their defenses to prevent a breach, build detection and response capabilities to contain a breach, and implement strong backup and recovery processes that allow for a fast return to normal operations.
Test & Validate Defenses
In the cybersecurity breach at Change Healthcare, attackers successfully infiltrated critical systems, caused significant damage, and exfiltrated data without timely detection. This demonstrates a crucial gap in the security-in-depth strategy. This incident highlights not just the need for robust security policies and solutions, but also the vital importance of regularly verifying their effectiveness.
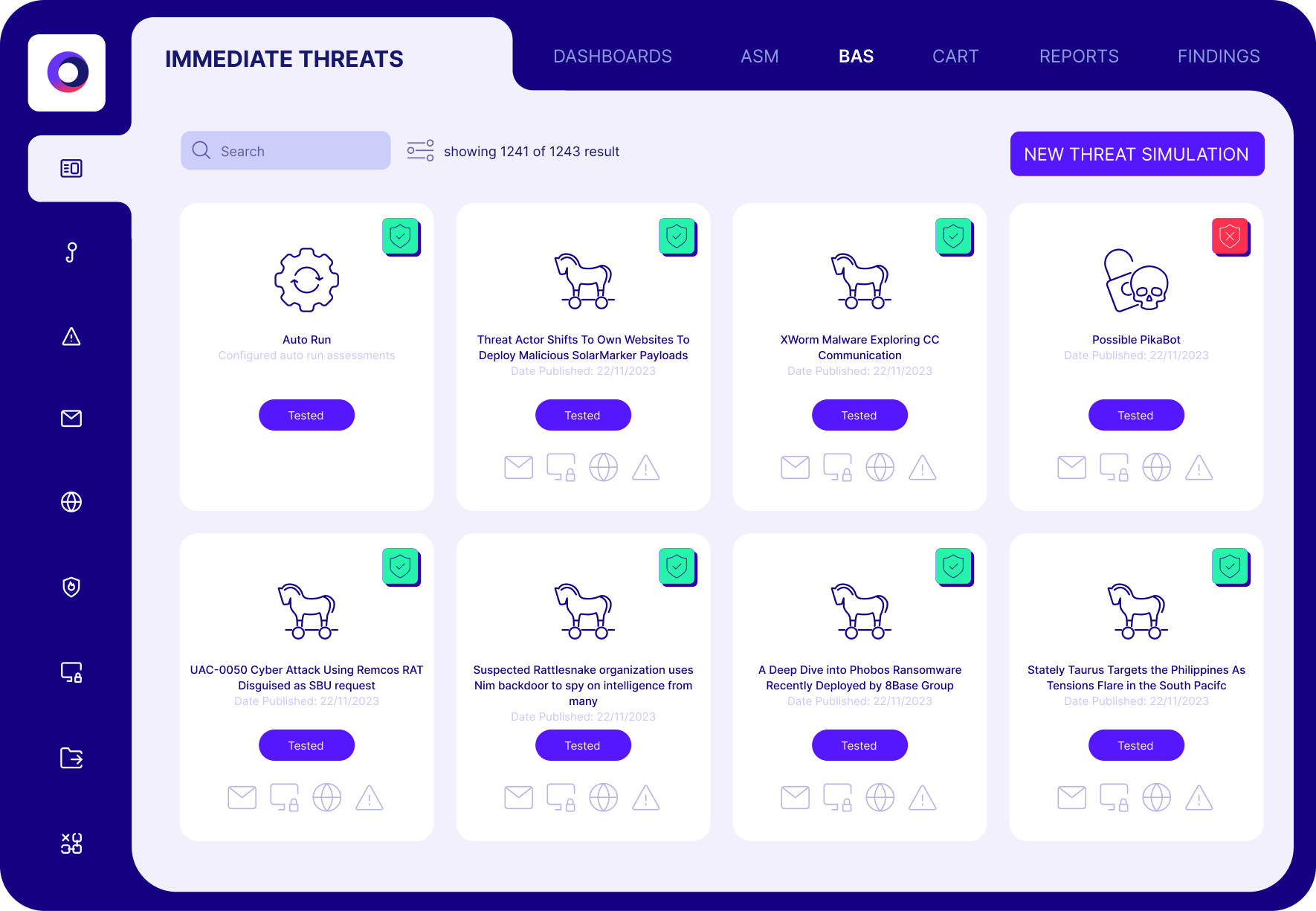
For example, healthcare organizations could significantly benefit from implementing continuous security validation with breach and attack simulation (BAS) technologies. BAS systematically challenges existing defenses by simulating a wide range of realistic attack scenarios, allowing organizations to test and validate the effectiveness of their security measures continuously.
Security control and threat validation help identify whether defensive measures are properly configured to mitigate threat campaigns across the cyber kill chain. In another incident involving a major hospital network, the attack led to a significant data breach despite having advanced malware protection. Attackers compromised their systems by targeting improperly configured firewalls.
Proactive assessments with automated offensive security testing are imperative not just to ensure that security solutions are functioning as intended but also to guarantee they are effectively integrated without leaving any coverage gaps. Only through such rigorous, proactive testing can organizations truly validate their cybersecurity posture and safeguard against sophisticated cyber threats.
Assume Breach with Detection & Response
While prevention is always better than detection, history shows us that breaches happen. Strong detection and response mitigates potential damage by detecting and disrupting the attack before the threat actor achieves their ultimate objective. While red teaming and detection engineering are typically limited to the most mature cyber programs, they are becoming a must-have in the healthcare industry.
With a focused detection engineering practice, security teams proactively design and build their capabilities for visibility, analysis, and response to specific threats, known campaigns, and potential attacks against known weaknesses. In essence, healthcare cyber teams must start thinking like an attacker to build essential cyber resilience into their program.
And like the preventive controls, detection and response capabilities must be tested to:
- Validate visibility to logs and proper collection of data
- Validate threat analysis and ability to trigger the appropriate alert for analysis
- Validate analysts and automated responses to triage, investigate, and contain the threat.
Continuous security validation from BAS and automated red teaming can provide the production-safe automation to validate visibility, threat analysis, and response.
Back Up & Recovery
In the event of a successful ransomware incident, cyber resilience must also include robust back up and recovery systems and processes to restore critical operations with minimal disruption. Critical elements of this strategy include maintaining regularly scheduled backups that are not connected to the network—often referred to as air-gapped—and using diverse formats such as cloud storage and physical drives to ensure redundancy.
These backups should encompass all critical data, applications, and system configurations, organized in a way that prioritizes quick restoration of the most essential services first.
Just like controls testing, regular testing of the backup integrity and the recovery process is crucial, ensuring that the system can be brought online swiftly and efficiently after an attack. Clear, step-by-step recovery procedures should be documented and accessible, with roles and responsibilities well-defined to avoid confusion during what is often a high-pressure situation.
Cymulate Can Help
Healthcare organizations like Assuta Medical Center, Elara Caring, and Nemours know they must be prepared for the next attack, so they use Cymulate to continuously validate their cyber security controls and test their defensive posture.
The Cymulate security and exposure validation platform automates advanced offensive testing with the latest threat activity facing the healthcare industry. Each assessment includes remediation guidance with specific steps to update configurations and tune controls.
To learn more about how Cymulate helps healthcare organizations validate security and optimize defenses, check out this case study for Nemours Children’s Health System, a nonprofit children’s health organization that cares for 500,000 children every year.

